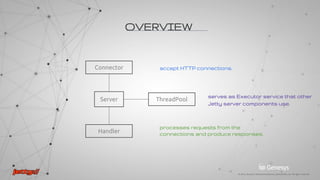
This document provides an overview of the Jetty web server and servlet container. It discusses:
- Jetty's ability to function as an HTTP server, HTTP client, and servlet container. It is open source and embeddable with a small memory footprint.
- The asynchronous nature of Jetty which never blocks for I/O activity.
- Supported Java versions for different Jetty versions ranging from Java 1.6 to 1.8.
- Information on configuration files, modules, and commands for starting Jetty.



![RUNNING
To start Jetty from $JETTY_HOME, run:
java -jar start.jar
Usage: java -jar start.jar [options] [properties] [configs]
java -jar start.jar --module=logging -Dorg.eclipse.jetty.server.LEVEL=ALL --list-config
java -jar start.jar --add-to-start=logging
start.ini
etcXML
libmod
Configuration Files](https://image.slidesharecdn.com/660bca36-4956-4a74-b563-eb3b43d77a70-151104232733-lva1-app6891/85/Jetty-TLS-troubleshooting-5-320.jpg)


![LOGGING
Jetty's internal org.eclipse.jetty.util.log.StdErrLog implementation:
java -jar /opt/jetty/start.jar --module=logging
yyyy_mm_dd.stderrout.log:
2015-10-14 03:23:29.726:INFO:oejs.ServerConnector:main: Started
ServerConnector@24a67{HTTP/1.1,[http/1.1]}{0.0.0.0:8080}
2015-10-14 03:30:46.580:INFO:oejs.ServerConnector:Thread-1: Stopped
ServerConnector@24a67{HTTP/1.1,[http/1.1]}{0.0.0.0:8080}
ALL
DEBUG
INFO
WARN
IGNORE
Logging Levels](https://image.slidesharecdn.com/660bca36-4956-4a74-b563-eb3b43d77a70-151104232733-lva1-app6891/85/Jetty-TLS-troubleshooting-8-320.jpg)












![***
found key for : jetty
Subject: CN=ua-rteresch-dt, OU=Jetty, O=Jetty, L=Kiev, ST=Kiev, C=UA
Issuer: CN=Symantec Trial Secure Server CA - G3
Multiple certificates may be linked in a certificate chain. First one chain [0] always sender’s certificate.
*** Certificate chain
chain [1] = [ chain [2] = [
Subject: CN=Symantec Trial Secure Server CA - G3 Subject: CN=VeriSign Trial Secure Server Root CA
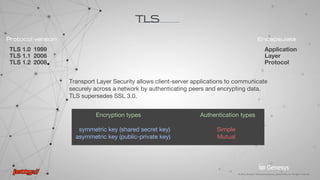
Troubleshooting
TLS debugging
-Djavax.net.debug=ssl
handshake
trustmanager
SunJSSE has a built-in debug facility activated by system property
javax.net.debug
Options:
***
Search criteria](https://image.slidesharecdn.com/660bca36-4956-4a74-b563-eb3b43d77a70-151104232733-lva1-app6891/85/Jetty-TLS-troubleshooting-22-320.jpg)


