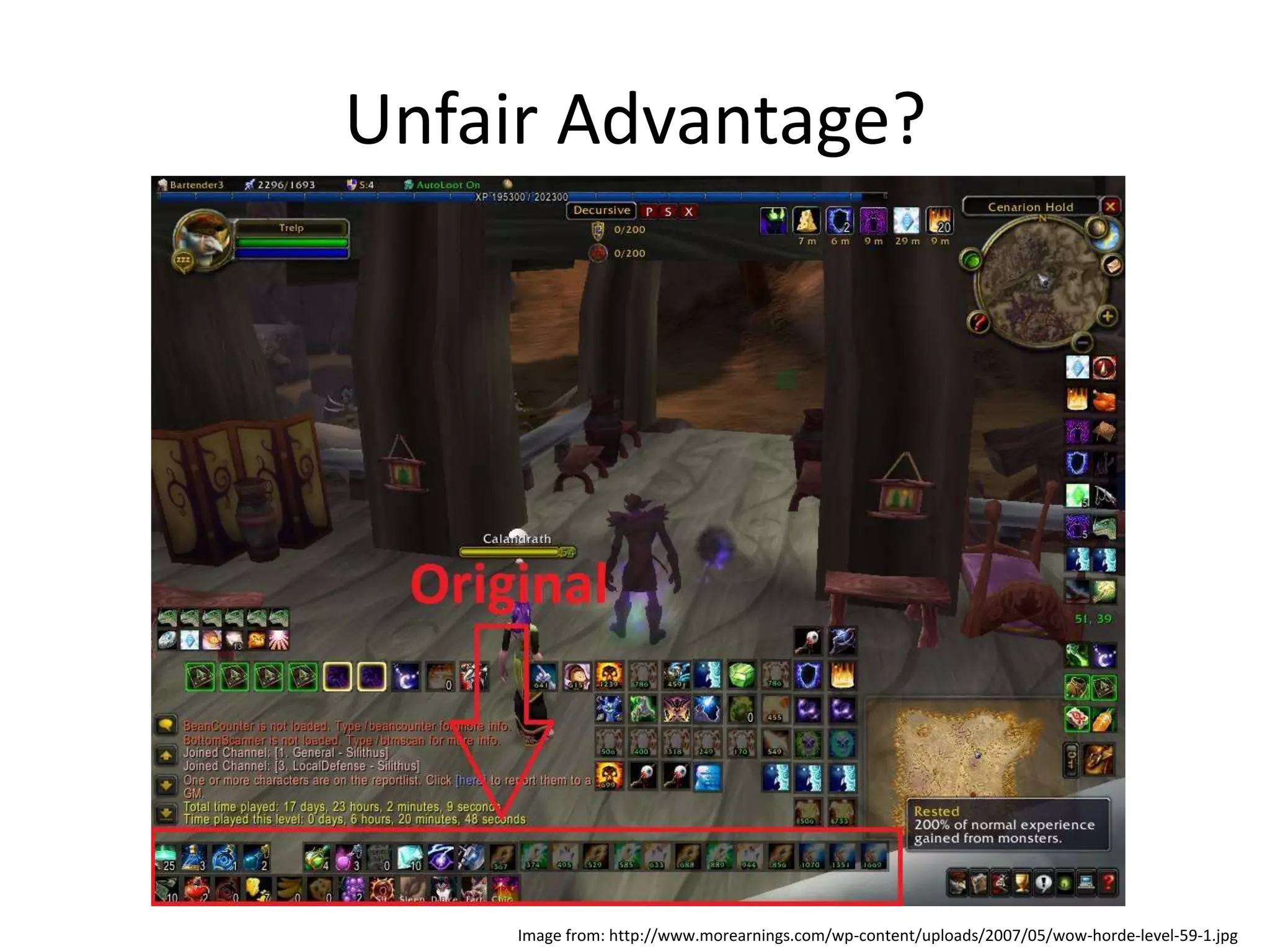
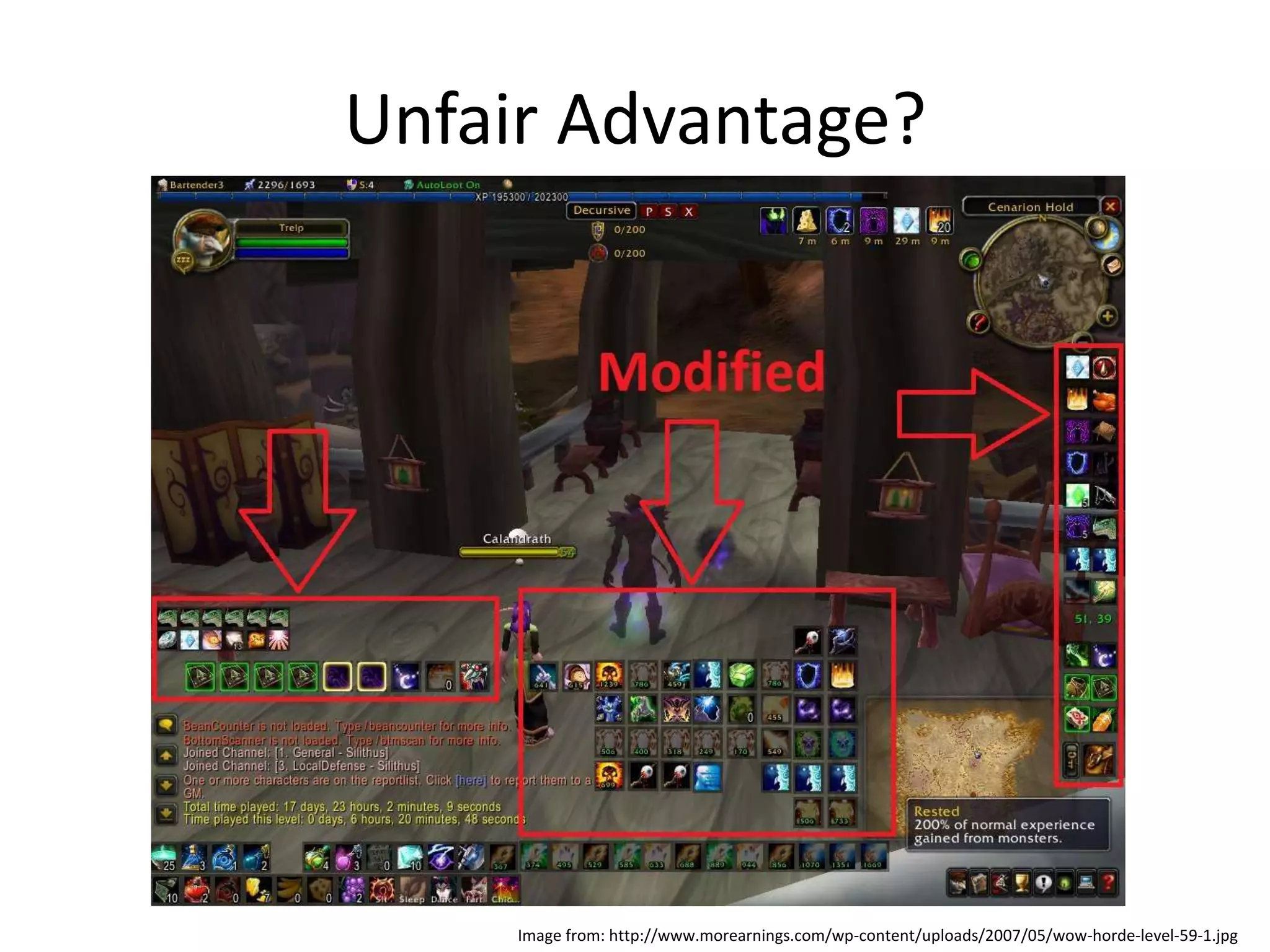
This document discusses cheating and exploits in online games. It begins by providing background on the gaming industry and types of games. It then describes two main types of cheating: exploiting game play mechanics and modifying game data. Exploits of game play include lag switching and stacking abilities. Modifying game data involves hacking for speed or aiming advantages. Cheating provides an unfair advantage and is motivated by the real-world value of in-game wealth or competitive prizes. Game developers try to prevent cheating through detection, patching vulnerabilities, and monitoring games. Overall, online game security faces similar challenges to other systems in identifying and addressing threats.