This document discusses online game security and preventing game bots. It covers several topics:
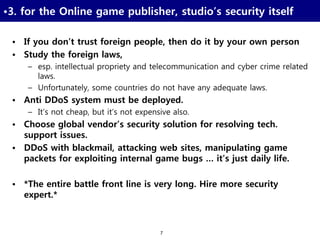
1. Online game security for publishers, including securing servers and networks, detecting private servers, and protecting users' computers.
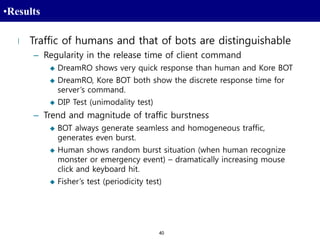
2. Methods for preventing game bots, including technical approaches like encryption, legal approaches, and game design approaches.
3. An academic paper on identifying MMORPG bots through traffic analysis, focusing on the popular game Ragnarok Online.









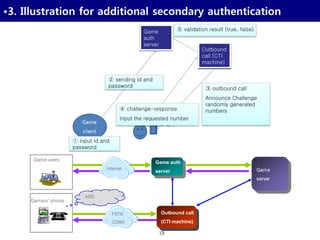
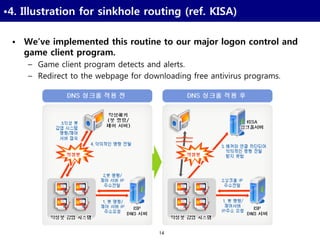










![26
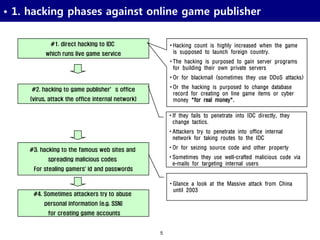
•2. Why BOT program is evil?
1. General theory
Destruction of in game balance.
Increase non-BOT users’ claim
Increase game development cost for prevention BOT module.
Increase game development cost because game BOT consume in-game
contents very speedily
Increase monitoring costs – hire more game master personnel, increase
a lot of costs regarding customer satisfaction.
When BOT fails to update game protocol, that program repeatedly
sends old protocol packets it’s kind of DDoS theoretically.
2. [이데일리] 환치기•명의도용…게임산업 좀먹는 `오토`
– http://www.edaily.co.kr/news/stock/newsRead.asp?sub_cd=DB41&newsid
=01079126586634584&clkcode=&DirCode=0030503&OutLnkChk=Y
3. The truth?
– It’s for money.](https://image.slidesharecdn.com/session2-2codegate2hkkim-130517025514-phpapp01/85/Session2-2-codegate2-hkkim-26-320.jpg)








![37
•Paper 1
Identifying MMORPG Bots: A Traffic Analysis
Approach
[ Chen, Jiang, Huang, Chu, Lei & Chen]
ACM International Conference Proceeding Series, Vol.
2006](https://image.slidesharecdn.com/session2-2codegate2hkkim-130517025514-phpapp01/85/Session2-2-codegate2-hkkim-37-320.jpg)

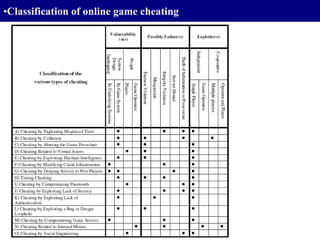
![42
•Paper 2
A systematic classification of cheating in online
games
[ Jeff Yan & Brian Randell]
Proc. Of 4th ACM SIGCOMM workshop on Network and
system support for games](https://image.slidesharecdn.com/session2-2codegate2hkkim-130517025514-phpapp01/85/Session2-2-codegate2-hkkim-42-320.jpg)