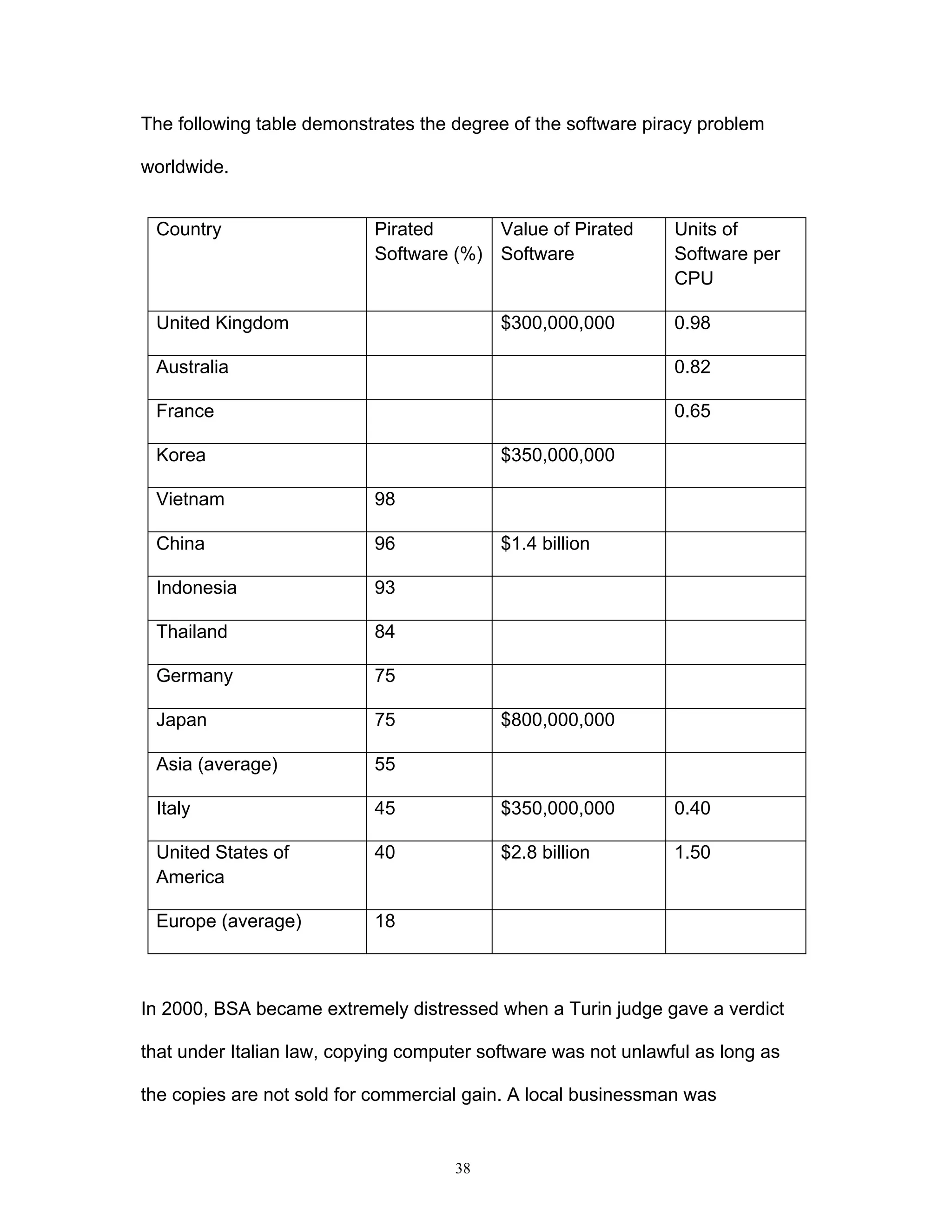
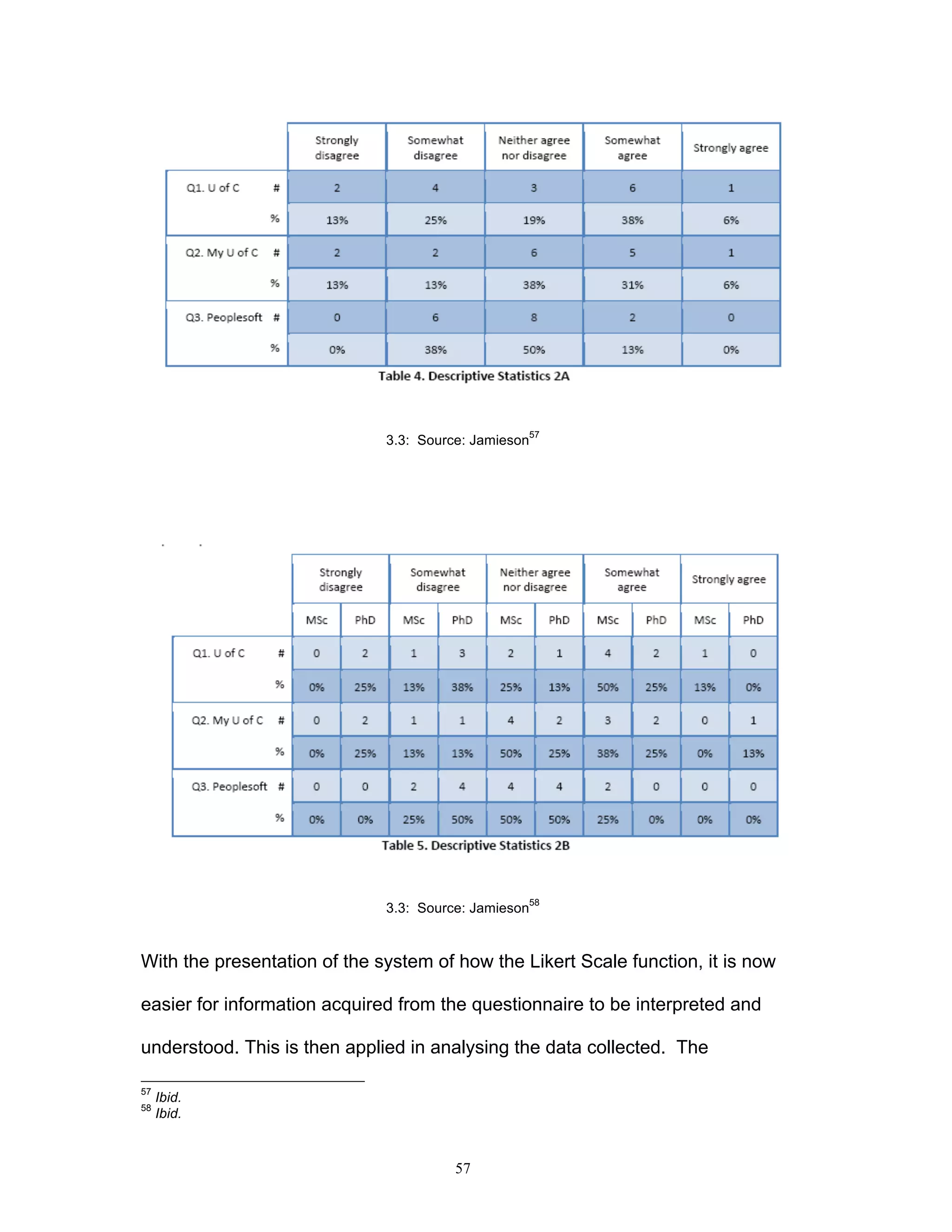
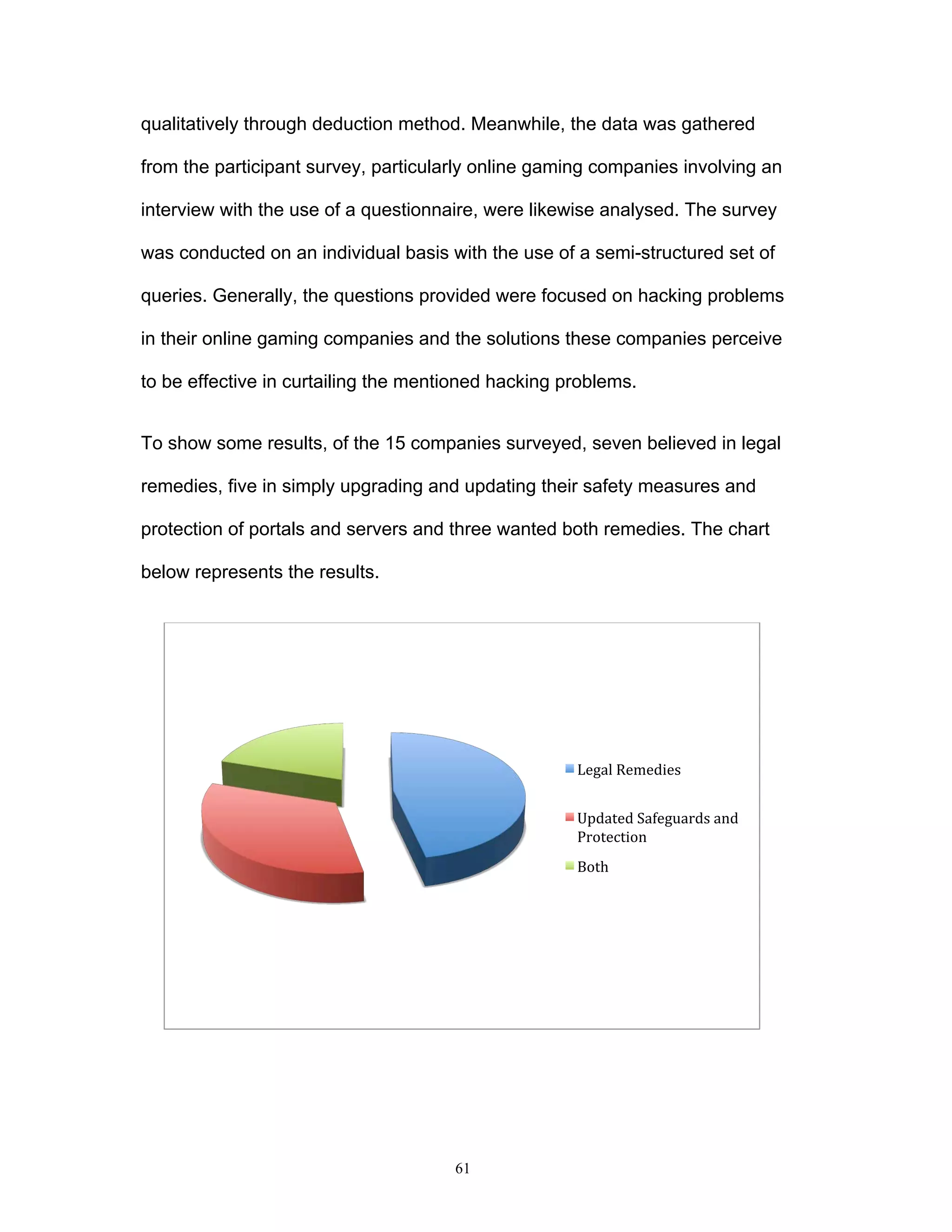
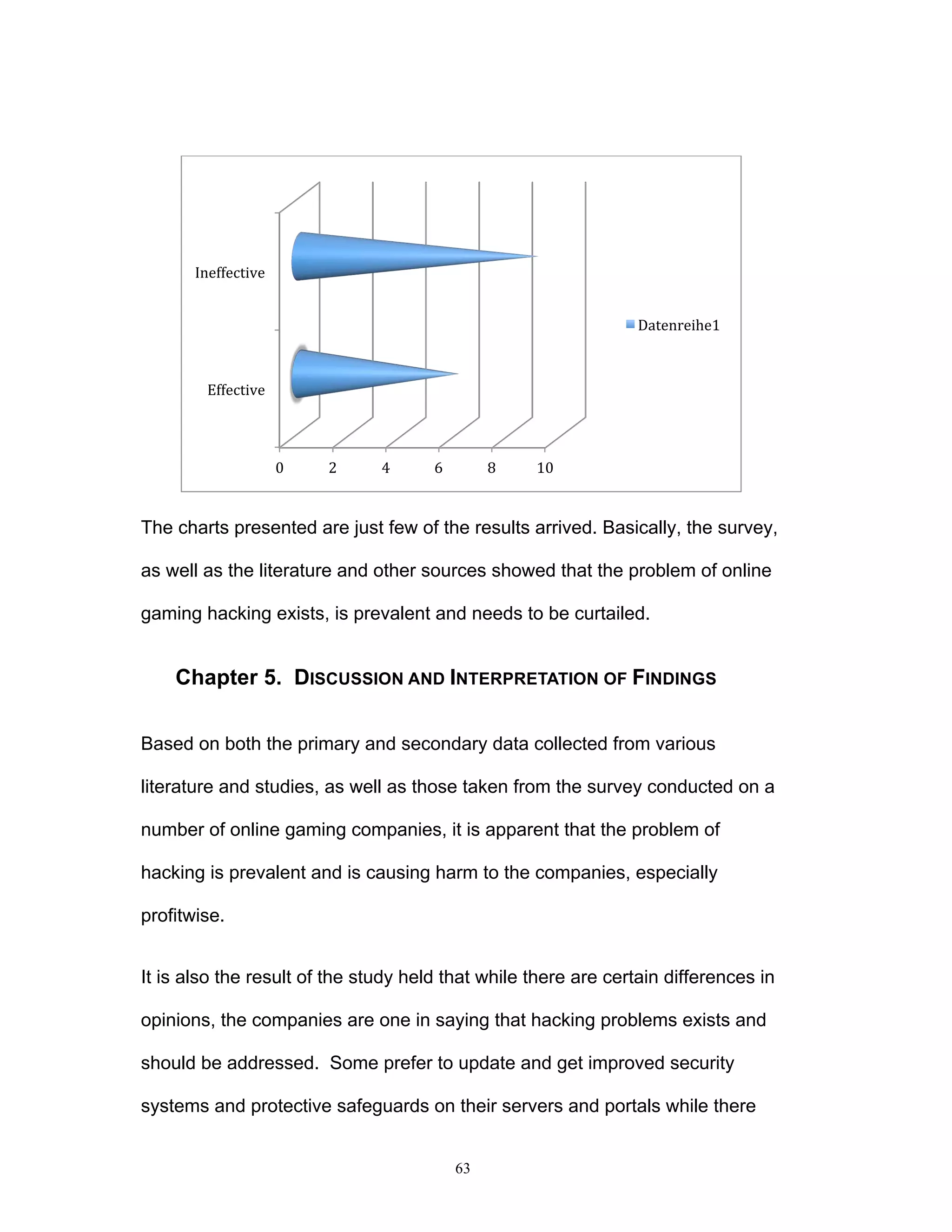
This document discusses the impact of online game hacking on the gaming industry and explores how intellectual property law can be used to combat this issue. It analyzes various laws and methodologies, focusing on the legal strategies that can be adopted to bring hackers to justice while assessing the implications of hacking on profits and business operations. The research aims to provide online gaming companies with practical legal frameworks to deter hacking through existing intellectual property laws and other relevant regulations.