IRM_E_14.3.12
•
0 likes•182 views
The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users, analysts, and managers to view, assign, update, and close incidents through an online portal. It also enables escalation of incidents by email if response criteria are not met.
Report
Share
Report
Share
Recommended
IRM_E_14.03.2012

The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users to search, view assigned incidents, add follow-ups, and close incidents. It also enables escalating unresolved incidents through automated emails.
IRM_E_15.3.12

The document describes Knowledge IT's incident management software solutions. It offers products for professional, business, enterprise, and ultimate users. The software allows users to search, register, and track incidents. Analysts can view assigned incidents, add follow-ups, and modify incidents. Users can view their incident list, follow-ups from analysts, and acknowledge when incidents are resolved. The software also enables copying incidents and on-demand escalation through email.
IRM_E_17.03.2012

The document describes an incident management software solution offered by Knowledge IT Corporation. It includes the following key capabilities:
1. Incident registration, assignment to analysts, and tracking of status and resolution through a web interface.
2. Communication features like follow ups, notifications, and feedback between users and analysts to resolve incidents.
3. Flexible configuration options for organizations of different sizes, including user roles and access privileges.
4. Automated escalation workflows that notify managers when incidents meet defined response time thresholds.
IRM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides industry-specific solutions for patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, and other industries. It offers 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. Key features include incident management, folder organization, user login and access controls, and notification escalation.
IRM_E_7.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and copy incidents to reuse resolved issues. The software provides role-based access and integrates with third party tools.
IRM_E_19.3.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, view incident history, and integrate with other third-party software. The software is offered in various tiers to suit organizations of different sizes, from individual use to enterprise-level systems managing hundreds of users.
IRM_E_1.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and escalate incidents that meet certain criteria. The software provides role-based access and is available in various tiers to suit organizations of different sizes.
IRM_E_12.03.12

Knowledge IT is a technology solutions provider that offers various SaaS applications for different industries and business needs. Their applications include modules for IP management, HR strategy, CRM, emergency management, and corporate governance. The document highlights Knowledge IT's product categories including professional, business, enterprise, and ultimate applications. It provides examples of how the applications can be used for incident search, registration, follow up, and modification.
Recommended
IRM_E_14.03.2012

The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users to search, view assigned incidents, add follow-ups, and close incidents. It also enables escalating unresolved incidents through automated emails.
IRM_E_15.3.12

The document describes Knowledge IT's incident management software solutions. It offers products for professional, business, enterprise, and ultimate users. The software allows users to search, register, and track incidents. Analysts can view assigned incidents, add follow-ups, and modify incidents. Users can view their incident list, follow-ups from analysts, and acknowledge when incidents are resolved. The software also enables copying incidents and on-demand escalation through email.
IRM_E_17.03.2012

The document describes an incident management software solution offered by Knowledge IT Corporation. It includes the following key capabilities:
1. Incident registration, assignment to analysts, and tracking of status and resolution through a web interface.
2. Communication features like follow ups, notifications, and feedback between users and analysts to resolve incidents.
3. Flexible configuration options for organizations of different sizes, including user roles and access privileges.
4. Automated escalation workflows that notify managers when incidents meet defined response time thresholds.
IRM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides industry-specific solutions for patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, and other industries. It offers 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. Key features include incident management, folder organization, user login and access controls, and notification escalation.
IRM_E_7.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and copy incidents to reuse resolved issues. The software provides role-based access and integrates with third party tools.
IRM_E_19.3.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, view incident history, and integrate with other third-party software. The software is offered in various tiers to suit organizations of different sizes, from individual use to enterprise-level systems managing hundreds of users.
IRM_E_1.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and escalate incidents that meet certain criteria. The software provides role-based access and is available in various tiers to suit organizations of different sizes.
IRM_E_12.03.12

Knowledge IT is a technology solutions provider that offers various SaaS applications for different industries and business needs. Their applications include modules for IP management, HR strategy, CRM, emergency management, and corporate governance. The document highlights Knowledge IT's product categories including professional, business, enterprise, and ultimate applications. It provides examples of how the applications can be used for incident search, registration, follow up, and modification.
IRM_E_13.03.2012

Knowledge IT is a company that offers various IT solutions and products for different industries. It provides solutions for intellectual property management, HR strategy, and incident response management. Its products include modules for object management, forensic management, review management, and others. Knowledge IT also offers different types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. The document provides details on Knowledge IT's solutions, products, application types and incident management workflow.
HSM_E_19.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their customizable applications include features for HR management, intellectual property management, incident response management, and corporate governance management. Knowledge IT's solutions are designed to increase effectiveness and reduce expenses for businesses of all sizes.
IRM_E_25.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different business needs. Their applications include modules for intellectual property management, HR strategy, CRM incident management, emergency incidence management, and corporate governance management. They provide applications tailored for professional individual/small business use, business use, enterprise use, and ultimate/large company use. Their applications integrate easily with third-party software and allow customizing the functions used.
IRM_E_24.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support different business needs across industries. Their applications include modules for intellectual property management, human resources strategy, customer relationship management, emergency management, and corporate governance management. The applications allow users to access only required functions and integrate with third-party software. Knowledge IT's applications are available at different tiers - Professional, Business, Enterprise, and Ultimate - tailored for organizations of various sizes from sole proprietors to large enterprises.
HSM_E_7.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their applications include HR strategy, intellectual property, incident response, and corporate governance management and can be customized using only required functions. Knowledge IT aims to offer easy-to-deploy software services at competitive pricing to help small and large businesses improve efficiency and reduce costs.
IPM_E_10.2.12

1) Knowledge IT offers a variety of software as a service (SaaS) applications for different industries and business needs without requiring upfront investment or installation.
2) Their applications include solutions for intellectual property management, human resources, incident response, and corporate governance that can be used individually or together.
3) Knowledge IT's SaaS model allows customers to pay for only the specific functions they need within each application.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer customizable software products that include modules for functions like IP management, HR strategy, and corporate governance. Customers can choose which modules they need rather than being required to use all functions of an application.
IEM_E_13.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different types of organizations and industries. Their applications include modules for intellectual property management, human resources, emergency response, and corporate governance. The applications allow customers to use only the necessary functions and integrate with third-party software. Knowledge IT's applications are available at different tiers to suit organizations of various sizes, from individual users to large enterprises.
IPM_E_3.2.12

The document describes Knowledge IT's solutions and products for intellectual property management. It lists various industry verticals Knowledge IT serves and its key solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It then lists Knowledge IT's products which include tools like Object Manager, Administration Manager, Review Manager, and Project Manager. The document explains Knowledge IT offers applications tailored for different organization sizes from professional to ultimate. It provides examples of folder registration and access management, annotation/comment features, and escalation emails for document operations.
CIM_E_24.2.12

Knowledge IT is a software company that offers various SaaS applications for different industries and business needs. Their solutions include products for intellectual property management, HR strategy, CRM, emergency management, and corporate governance. Their applications can be used by individuals, small businesses, or large enterprises. Knowledge IT's document highlights some of their incident management software, including features for adding and viewing incidents, registering incidents, responding to incidents, categorizing incidents in folders, searching incidents, and escalating incidents via email notifications.
HSM_E_23.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different industries and business needs. Their applications include tools for intellectual property management, human resources strategy, customer relationship management, emergency incident management, and corporate governance management. The applications are role-based and allow customization so users only access needed functions. Knowledge IT's solutions range from individual professional plans to enterprise-level offerings for large organizations. They allow easy third-party integration and data migration management between different application modules. The platforms also include features for annotations, escalation workflows, and automated email notifications.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include modules for IP management, HR strategy, incident response, and corporate governance management. Knowledge IT's software products are role-based and include object manager, forensic manager, review manager, workflow manager, and other modules to manage projects, schedules, resources, and more.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to business needs from individual use to large enterprises. Knowledge IT's products include features like IP management, HR strategy management, incidence response management, and more that can be customized and integrated with third party software.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, workflow, and schedule managers. Knowledge IT's software-as-a-service applications can be tailored to business needs and integrate with third-party software.
HSM_E_21.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions and products for functions like HR, intellectual property management, and incident response. Their software-as-a-service applications can be used by small businesses, large corporations, and governments and require no upfront installation. Knowledge IT's applications support configurable search forms, data migration management, annotation capabilities, and automated escalation emails.
IPM

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for organizations of different sizes, from individuals and small businesses to large enterprises. Key features include role-based access control, document management and sharing capabilities, and automated email notifications.
HRCM_E_2FEB2012

The document describes Knowledge IT's software-as-a-service (SaaS) applications for various industries. It offers 6 main applications for intellectual property management, HR management, incident response management, and more. It also lists related products including object, review, and schedule managers. The applications are available at different tiers for individual, small/medium business, enterprise, and ultimate users. Features include search, data import/export, and alert/escalation messages.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, education, and oil/energy. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, and workflow managers. Knowledge IT's software-as-a-service applications can be tailored to fit the needs of individual users, small businesses, or large enterprises through access privileges and integrated third-party software.
IPM_E_23.4.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its document management solutions in 3 sentences:
Knowledge IT offers a variety of secure document and folder management software as a service applications for organizations of all sizes. The applications allow users to add, modify, search, and comment on documents with role-based access control and automatic email notifications. Customers can integrate these applications and select only the necessary functions to meet their business needs.
IPM_E_7.4.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality.
More Related Content
What's hot
IRM_E_13.03.2012

Knowledge IT is a company that offers various IT solutions and products for different industries. It provides solutions for intellectual property management, HR strategy, and incident response management. Its products include modules for object management, forensic management, review management, and others. Knowledge IT also offers different types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. The document provides details on Knowledge IT's solutions, products, application types and incident management workflow.
HSM_E_19.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their customizable applications include features for HR management, intellectual property management, incident response management, and corporate governance management. Knowledge IT's solutions are designed to increase effectiveness and reduce expenses for businesses of all sizes.
IRM_E_25.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different business needs. Their applications include modules for intellectual property management, HR strategy, CRM incident management, emergency incidence management, and corporate governance management. They provide applications tailored for professional individual/small business use, business use, enterprise use, and ultimate/large company use. Their applications integrate easily with third-party software and allow customizing the functions used.
IRM_E_24.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support different business needs across industries. Their applications include modules for intellectual property management, human resources strategy, customer relationship management, emergency management, and corporate governance management. The applications allow users to access only required functions and integrate with third-party software. Knowledge IT's applications are available at different tiers - Professional, Business, Enterprise, and Ultimate - tailored for organizations of various sizes from sole proprietors to large enterprises.
HSM_E_7.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their applications include HR strategy, intellectual property, incident response, and corporate governance management and can be customized using only required functions. Knowledge IT aims to offer easy-to-deploy software services at competitive pricing to help small and large businesses improve efficiency and reduce costs.
IPM_E_10.2.12

1) Knowledge IT offers a variety of software as a service (SaaS) applications for different industries and business needs without requiring upfront investment or installation.
2) Their applications include solutions for intellectual property management, human resources, incident response, and corporate governance that can be used individually or together.
3) Knowledge IT's SaaS model allows customers to pay for only the specific functions they need within each application.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer customizable software products that include modules for functions like IP management, HR strategy, and corporate governance. Customers can choose which modules they need rather than being required to use all functions of an application.
IEM_E_13.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different types of organizations and industries. Their applications include modules for intellectual property management, human resources, emergency response, and corporate governance. The applications allow customers to use only the necessary functions and integrate with third-party software. Knowledge IT's applications are available at different tiers to suit organizations of various sizes, from individual users to large enterprises.
IPM_E_3.2.12

The document describes Knowledge IT's solutions and products for intellectual property management. It lists various industry verticals Knowledge IT serves and its key solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It then lists Knowledge IT's products which include tools like Object Manager, Administration Manager, Review Manager, and Project Manager. The document explains Knowledge IT offers applications tailored for different organization sizes from professional to ultimate. It provides examples of folder registration and access management, annotation/comment features, and escalation emails for document operations.
CIM_E_24.2.12

Knowledge IT is a software company that offers various SaaS applications for different industries and business needs. Their solutions include products for intellectual property management, HR strategy, CRM, emergency management, and corporate governance. Their applications can be used by individuals, small businesses, or large enterprises. Knowledge IT's document highlights some of their incident management software, including features for adding and viewing incidents, registering incidents, responding to incidents, categorizing incidents in folders, searching incidents, and escalating incidents via email notifications.
HSM_E_23.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different industries and business needs. Their applications include tools for intellectual property management, human resources strategy, customer relationship management, emergency incident management, and corporate governance management. The applications are role-based and allow customization so users only access needed functions. Knowledge IT's solutions range from individual professional plans to enterprise-level offerings for large organizations. They allow easy third-party integration and data migration management between different application modules. The platforms also include features for annotations, escalation workflows, and automated email notifications.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include modules for IP management, HR strategy, incident response, and corporate governance management. Knowledge IT's software products are role-based and include object manager, forensic manager, review manager, workflow manager, and other modules to manage projects, schedules, resources, and more.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to business needs from individual use to large enterprises. Knowledge IT's products include features like IP management, HR strategy management, incidence response management, and more that can be customized and integrated with third party software.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, workflow, and schedule managers. Knowledge IT's software-as-a-service applications can be tailored to business needs and integrate with third-party software.
HSM_E_21.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions and products for functions like HR, intellectual property management, and incident response. Their software-as-a-service applications can be used by small businesses, large corporations, and governments and require no upfront installation. Knowledge IT's applications support configurable search forms, data migration management, annotation capabilities, and automated escalation emails.
IPM

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for organizations of different sizes, from individuals and small businesses to large enterprises. Key features include role-based access control, document management and sharing capabilities, and automated email notifications.
HRCM_E_2FEB2012

The document describes Knowledge IT's software-as-a-service (SaaS) applications for various industries. It offers 6 main applications for intellectual property management, HR management, incident response management, and more. It also lists related products including object, review, and schedule managers. The applications are available at different tiers for individual, small/medium business, enterprise, and ultimate users. Features include search, data import/export, and alert/escalation messages.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, education, and oil/energy. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, and workflow managers. Knowledge IT's software-as-a-service applications can be tailored to fit the needs of individual users, small businesses, or large enterprises through access privileges and integrated third-party software.
IPM_E_23.4.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its document management solutions in 3 sentences:
Knowledge IT offers a variety of secure document and folder management software as a service applications for organizations of all sizes. The applications allow users to add, modify, search, and comment on documents with role-based access control and automatic email notifications. Customers can integrate these applications and select only the necessary functions to meet their business needs.
IPM_E_7.4.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality.
What's hot (20)
Viewers also liked
CGS_E_23.4.12

Knowledge IT offers industry-specific solutions using their SaaS products which only utilize necessary functions. Their applications support various organization sizes from individuals to large corporations. The document describes their 4 types of applications - Professional, Business, Enterprise, and Ultimate - which differ based on needs, users, and control offered. It also outlines some key features including customer search, registration, mail escalation, and follow up functions.
IRM_E_12.03.12

The document outlines the incident management workflow within a customer service system. It shows the various user logins and screens involved in registering an incident, receiving notifications, adding follow ups, searching and finding incidents, modifying incidents, and escalating incidents by email. The full workflow allows customers and analysts to log issues, provide updates, and ensure issues are properly tracked and resolved.
Viewers also liked (14)
Similar to IRM_E_14.3.12
CMS_01.03.12

Quick Solution Delivery Offered by Knowledge IT
Knowledge IT offers a variety of software as a service (SaaS) applications across different industries including manufacturing, healthcare, education, and government. Their applications include intellectual property management, HR strategy management, CRM incident response management, emergency incident management, and corporate governance management. Knowledge IT's products are modular and allow customers to use only the necessary functions, avoiding overuse of applications. Their applications are available at competitive prices without upfront costs and can support organizations of all sizes.
IPM_E_8.2.2012

This document summarizes the services offered by Knowledge IT, including industry-specific solutions and products for intellectual property management, HR management, emergency management, and other functions. It describes Knowledge IT's SaaS application offerings for professional, business, enterprise, and ultimate users. Key capabilities highlighted include document management with folder structure and security, annotation and search features, and automated email notifications.
IPM_E_8.2.2012

Quick Solution delivery offered by Knowledge IT provides industry-specific solutions including patent & intellectual property, manufacturing, medical & health care, beauty & care, education, oil and energy, and government. It offers 5 solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It also provides various productivity applications that can be customized for professional, business, enterprise, and ultimate users.
IPM_E_8.2.2012

This document discusses Knowledge IT's quick solution delivery offerings across various industries. It provides an overview of 5 solutions - IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It also describes Knowledge IT's product suite which includes tools like Object Manager, Administration Manager, Review Manager, and others. Finally, it discusses Knowledge IT's 4 types of applications - Professional, Business, Enterprise, and Ultimate - which are tailored for customers based on needs and user demand.
CGM_E_8.2.2012

Knowledge IT is a software company that offers industry-specific solutions including intellectual property management, HR management, and emergency response management. It provides 5 main products: Object Manager, Administration Manager, Review Manager, Schedule Manager, and Corporate Manager. These products each have additional modules like Forensic Manager, Workflow Manager, and Billing Manager. Knowledge IT takes a software-as-a-service approach, allowing customers to use only the necessary functions. It offers 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored for organizations of different sizes. The document provides examples of login screens, data import/export, and escalation mail views within Knowledge IT's software products.
CGS_E_1.3.12

Quick Solution Delivery Offered by Knowledge IT
Knowledge IT offers a variety of software as a service (SaaS) applications to meet different business needs. Their applications include tools for intellectual property management, human resources, customer relationship management, and more. Customers only need to use the specific functions relevant to their business. Knowledge IT also makes it easy to integrate their applications with third party software. They provide applications tailored for individuals, small and medium businesses, large enterprises, and customized solutions for very large companies.
CGS_E_1.4.12

Knowledge IT offers a variety of solutions and products for different industries including patent & intellectual property, manufacturing, medical & health care, beauty & care, education, oil and energy, electronics, franchising, construction, and government. Their solutions include HR strategy management, intellectual property management, incident response management, and corporate governance management. Their products include object manager, forensic manager, review manager, workflow manager, human resource manager, administration manager, project manager, discovery manager, and schedule manager. Knowledge IT provides applications tailored to professional, business, enterprise, and ultimate users with flexible integration and customization options.
CGS_E_7.4.12

Knowledge IT offers a variety of software solutions tailored for different industries and business needs. Their products include applications for HR strategy management, intellectual property management, incident response management, and corporate governance management. The document then describes their customizable software products which include object manager, forensic manager, review manager, and others. It explains that their applications are cloud-based and users only access the specific functions they require. Knowledge IT provides solutions for organizations of all sizes, from individuals and small businesses to large enterprises.
IPM_E_19.3.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality. Security and access controls allow documents and folders to be viewed according to user privileges.
HSM_E_1.4.12

Quick Solution Delivery Offered by Knowledge IT
Knowledge IT offers a variety of software-as-a-service (SaaS) applications across multiple industries that provide quick solutions without requiring initial investment or complex installation. Their applications support small and large businesses and can increase effectiveness while reducing expenses. Key features include customizable search forms, data migration management tools, annotation capabilities, and automatic escalation and email notifications.
Similar to IRM_E_14.3.12 (10)
More from Hemant_Kumar_Setya
More from Hemant_Kumar_Setya (17)
Recently uploaded
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
20 Comprehensive Checklist of Designing and Developing a Website

Dive into the world of Website Designing and Developing with Pixlogix! Looking to create a stunning online presence? Look no further! Our comprehensive checklist covers everything you need to know to craft a website that stands out. From user-friendly design to seamless functionality, we've got you covered. Don't miss out on this invaluable resource! Check out our checklist now at Pixlogix and start your journey towards a captivating online presence today.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
How to Get CNIC Information System with Paksim Ga.pptx

Pakdata Cf is a groundbreaking system designed to streamline and facilitate access to CNIC information. This innovative platform leverages advanced technology to provide users with efficient and secure access to their CNIC details.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
“I’m still / I’m still / Chaining from the Block”

“An Outlook of the Ongoing and Future Relationship between Blockchain Technologies and Process-aware Information Systems.” Invited talk at the joint workshop on Blockchain for Information Systems (BC4IS) and Blockchain for Trusted Data Sharing (B4TDS), co-located with with the 36th International Conference on Advanced Information Systems Engineering (CAiSE), 3 June 2024, Limassol, Cyprus.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Join us to introduce Milvus Lite, a vector database that can run on notebooks and laptops, share the same API with Milvus, and integrate with every popular GenAI framework. This webinar is perfect for developers seeking easy-to-use, well-integrated vector databases for their GenAI apps.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Building RAG with self-deployed Milvus vector database and Snowpark Container...

This talk will give hands-on advice on building RAG applications with an open-source Milvus database deployed as a docker container. We will also introduce the integration of Milvus with Snowpark Container Services.
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
Full-RAG: A modern architecture for hyper-personalization

Mike Del Balso, CEO & Co-Founder at Tecton, presents "Full RAG," a novel approach to AI recommendation systems, aiming to push beyond the limitations of traditional models through a deep integration of contextual insights and real-time data, leveraging the Retrieval-Augmented Generation architecture. This talk will outline Full RAG's potential to significantly enhance personalization, address engineering challenges such as data management and model training, and introduce data enrichment with reranking as a key solution. Attendees will gain crucial insights into the importance of hyperpersonalization in AI, the capabilities of Full RAG for advanced personalization, and strategies for managing complex data integrations for deploying cutting-edge AI solutions.
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
Recently uploaded (20)
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
20 Comprehensive Checklist of Designing and Developing a Website

20 Comprehensive Checklist of Designing and Developing a Website
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
How to Get CNIC Information System with Paksim Ga.pptx

How to Get CNIC Information System with Paksim Ga.pptx
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...
Building RAG with self-deployed Milvus vector database and Snowpark Container...

Building RAG with self-deployed Milvus vector database and Snowpark Container...
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
Full-RAG: A modern architecture for hyper-personalization

Full-RAG: A modern architecture for hyper-personalization
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
IRM_E_14.3.12
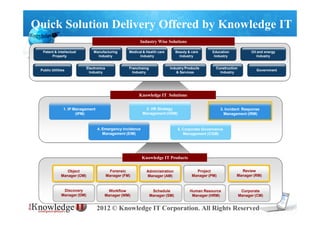
- 1. Quick Solution Delivery Offered by Knowledge IT Industry Wise Solutions Patent & Intellectual Manufacturing Medical & Health care Beauty & care Education Oil and energy Property Industry Industry Industry Industry Industry Electronics Franchising Industry Products Construction Public Utilities Government Industry Industry & Services Industry Knowledge IT Solutions 1. IP Management 2. HR Strategy 3. Incident Response (IPM) Management (HSM) Management (IRM) 4. Emergency Incidence 5. Corporate Governance Management (EIM) Management (CGM) Knowledge IT Products Object Forensic Administration Project Review Manager (OM) Manager (FM) Manager (AM) Manager (PM) Manager (RM) Discovery Workflow Schedule Human Resource Corporate Manager (DM) Manager (WM) Manager (SM) Manager (HRM) Manager (CM) 2012 © Knowledge IT Corporation. All Rights Reserved
- 2. Pick and Use Functions that you Need With any application, you effectively use only 10% of the application. But with Knowledge IT’s SaaS applications, you use only those functions that you need. The Knowledge IT Products Object Forensic Manager (OM) Manager (FM) Review Workflow Manager (RM) Manager (WM) Project Administration Manager (PM) Manager (AM) Human Resource Discovery (RM) Manager (HRM) Manager (DM) Corporate Schedule Manager (CM) Manager (SM) Easy Third Party Software Integration 2012 © Knowledge IT Corporation. All Rights Reserved
- 3. Knowledge IT’s 4 Types of Application Based on Needs & User Demand Knowledge IT offers a variety of SaaS applications which do not require initial investment and installation effort, by providing easy-to-deploy software services at competitive pricing. The applications supports small businesses and large corporations, contributing to increasing effectiveness and reducing expenses. Professional Business Enterprise Ultimate Individuals・SOHO Small and Medium Small and Medium For large companies Personal Offices enterprises or Enterprises or looking for full control or Small Offices Shop owners Enterprise Subcontractors and autonomy Best for individual Suitable for system ranging Ideal for organizations and Highly specialized set of use and smaller from two to multiple users. businesses with large groups. administration tools in an businesses Data access for packaged Security, access privileges as application is ideal for large groups predetermined privilege based. well as functions can be of people in an organization. This Users: 1-5 Secure user access. determined by the customer and Ultimate set comes with the freedom Size: 1-5 Users Users: 2-1000 set/added per category of users to build a solution view and dig- Size: 30 and above from Packaged Solution. down feature according to each Users: 100-1000 customer’s need. Role based as well Size: 50 and above as privilege based access control can be set by the Business and above. Users: 100 and above Size: 100 and above 2012 © Knowledge IT Corporation. All Rights Reserved
- 4. Incident Search of Different Types Analyst Login User Login Incident Search Result 2012 © Knowledge IT Corporation. All Rights Reserved.
- 5. Incident Registration User Login 2012 © Knowledge IT Corporation. All Rights Reserved.
- 6. Incident Occurrence Notification Help Desk Manager Login Help Desk manager receive the incident registration alert mail He may also reply along and will assign it to the with any feedback or concerned analyst. suggestion. 2012 © Knowledge IT Corporation. All Rights Reserved.
- 7. Incident List Analyst Login Analyst finds an incident assigned to him 2012 © Knowledge IT Corporation. All Rights Reserved.
- 8. Add Follow Up Analyst Login Analyst can add follow up if required, to convey his message, to user regarding an incident. Different Index Description Form 2012 © Knowledge IT Corporation. All Rights Reserved.
- 9. User Incident List User Login Icon of follow up added by analyst. User finds follow up which was added by analyst. 2012 © Knowledge IT Corporation. All Rights Reserved.
- 10. Incident Closure & Notification User Login Analyst Login User may report or give his acknowledgement on incident being resolved or follow up added by analyst. Analyst will find notification of user feedback on follow up via mail. 2012 © Knowledge IT Corporation. All Rights Reserved.
- 11. Incident Modify Analyst Login Lock during modify by any user or analyst. 2012 © Knowledge IT Corporation. All Rights Reserved.
- 12. Incident Copy User Login If the problem occurs again user may copy selected incident to required folder. 2012 © Knowledge IT Corporation. All Rights Reserved.
- 13. On Demand Escalation Multiple escalations with various KPI’s can be set for multiple user. Mail escalated when pre-defined criteria meets. 2012 © Knowledge IT Corporation. All Rights Reserved.