IPM_E_17.3.12
•
0 likes•172 views
Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences: Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, workflow, and schedule managers. Knowledge IT's software-as-a-service applications can be tailored to business needs and integrate with third-party software.
Report
Share
Report
Share
Recommended
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, education, and oil/energy. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, and workflow managers. Knowledge IT's software-as-a-service applications can be tailored to fit the needs of individual users, small businesses, or large enterprises through access privileges and integrated third-party software.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include modules for IP management, HR strategy, incident response, and corporate governance management. Knowledge IT's software products are role-based and include object manager, forensic manager, review manager, workflow manager, and other modules to manage projects, schedules, resources, and more.
IPM_E_19.3.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality. Security and access controls allow documents and folders to be viewed according to user privileges.
IPM_E_23.4.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its document management solutions in 3 sentences:
Knowledge IT offers a variety of secure document and folder management software as a service applications for organizations of all sizes. The applications allow users to add, modify, search, and comment on documents with role-based access control and automatic email notifications. Customers can integrate these applications and select only the necessary functions to meet their business needs.
IPM_E_7.4.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality.
IPM

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for organizations of different sizes, from individuals and small businesses to large enterprises. Key features include role-based access control, document management and sharing capabilities, and automated email notifications.
HSM_E_19.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their customizable applications include features for HR management, intellectual property management, incident response management, and corporate governance management. Knowledge IT's solutions are designed to increase effectiveness and reduce expenses for businesses of all sizes.
IPM_E_10.2.12

1) Knowledge IT offers a variety of software as a service (SaaS) applications for different industries and business needs without requiring upfront investment or installation.
2) Their applications include solutions for intellectual property management, human resources, incident response, and corporate governance that can be used individually or together.
3) Knowledge IT's SaaS model allows customers to pay for only the specific functions they need within each application.
Recommended
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, education, and oil/energy. Their solutions include applications for IP management, HR strategy, incident response, corporate governance, and customized project, review, and workflow managers. Knowledge IT's software-as-a-service applications can be tailored to fit the needs of individual users, small businesses, or large enterprises through access privileges and integrated third-party software.
IPM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its industry-specific solutions in 3 sentences:
Knowledge IT offers customized software solutions for various industries including patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, electronics, franchising, construction, and government. Their solutions include modules for IP management, HR strategy, incident response, and corporate governance management. Knowledge IT's software products are role-based and include object manager, forensic manager, review manager, workflow manager, and other modules to manage projects, schedules, resources, and more.
IPM_E_19.3.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality. Security and access controls allow documents and folders to be viewed according to user privileges.
IPM_E_23.4.12

Quick Solution Delivery Offered by Knowledge IT provides concise summaries of its document management solutions in 3 sentences:
Knowledge IT offers a variety of secure document and folder management software as a service applications for organizations of all sizes. The applications allow users to add, modify, search, and comment on documents with role-based access control and automatic email notifications. Customers can integrate these applications and select only the necessary functions to meet their business needs.
IPM_E_7.4.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for different business sizes, from individual professionals to large enterprises, with customizable access and functionality.
IPM

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support organizations across different industries. Their applications include tools for human resource strategy management, intellectual property management, incident response management, and corporate governance management. The document discusses Knowledge IT's product offerings and how they are tailored for organizations of different sizes, from individuals and small businesses to large enterprises. Key features include role-based access control, document management and sharing capabilities, and automated email notifications.
HSM_E_19.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their customizable applications include features for HR management, intellectual property management, incident response management, and corporate governance management. Knowledge IT's solutions are designed to increase effectiveness and reduce expenses for businesses of all sizes.
IPM_E_10.2.12

1) Knowledge IT offers a variety of software as a service (SaaS) applications for different industries and business needs without requiring upfront investment or installation.
2) Their applications include solutions for intellectual property management, human resources, incident response, and corporate governance that can be used individually or together.
3) Knowledge IT's SaaS model allows customers to pay for only the specific functions they need within each application.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer customizable software products that include modules for functions like IP management, HR strategy, and corporate governance. Customers can choose which modules they need rather than being required to use all functions of an application.
IPM_E_3.2.12

The document describes Knowledge IT's solutions and products for intellectual property management. It lists various industry verticals Knowledge IT serves and its key solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It then lists Knowledge IT's products which include tools like Object Manager, Administration Manager, Review Manager, and Project Manager. The document explains Knowledge IT offers applications tailored for different organization sizes from professional to ultimate. It provides examples of folder registration and access management, annotation/comment features, and escalation emails for document operations.
HSM_E_7.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their applications include HR strategy, intellectual property, incident response, and corporate governance management and can be customized using only required functions. Knowledge IT aims to offer easy-to-deploy software services at competitive pricing to help small and large businesses improve efficiency and reduce costs.
IRM_E_24.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support different business needs across industries. Their applications include modules for intellectual property management, human resources strategy, customer relationship management, emergency management, and corporate governance management. The applications allow users to access only required functions and integrate with third-party software. Knowledge IT's applications are available at different tiers - Professional, Business, Enterprise, and Ultimate - tailored for organizations of various sizes from sole proprietors to large enterprises.
HSM_E_23.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different industries and business needs. Their applications include tools for intellectual property management, human resources strategy, customer relationship management, emergency incident management, and corporate governance management. The applications are role-based and allow customization so users only access needed functions. Knowledge IT's solutions range from individual professional plans to enterprise-level offerings for large organizations. They allow easy third-party integration and data migration management between different application modules. The platforms also include features for annotations, escalation workflows, and automated email notifications.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to business needs from individual use to large enterprises. Knowledge IT's products include features like IP management, HR strategy management, incidence response management, and more that can be customized and integrated with third party software.
IEM_E_13.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different types of organizations and industries. Their applications include modules for intellectual property management, human resources, emergency response, and corporate governance. The applications allow customers to use only the necessary functions and integrate with third-party software. Knowledge IT's applications are available at different tiers to suit organizations of various sizes, from individual users to large enterprises.
IRM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides industry-specific solutions for patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, and other industries. It offers 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. Key features include incident management, folder organization, user login and access controls, and notification escalation.
IRM_E_19.3.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, view incident history, and integrate with other third-party software. The software is offered in various tiers to suit organizations of different sizes, from individual use to enterprise-level systems managing hundreds of users.
IPM_E_8.2.2012

This document discusses Knowledge IT's quick solution delivery offerings across various industries. It provides an overview of 5 solutions - IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It also describes Knowledge IT's product suite which includes tools like Object Manager, Administration Manager, Review Manager, and others. Finally, it discusses Knowledge IT's 4 types of applications - Professional, Business, Enterprise, and Ultimate - which are tailored for customers based on needs and user demand.
IPM_E_8.2.2012

This document summarizes the services offered by Knowledge IT, including industry-specific solutions and products for intellectual property management, HR management, emergency management, and other functions. It describes Knowledge IT's SaaS application offerings for professional, business, enterprise, and ultimate users. Key capabilities highlighted include document management with folder structure and security, annotation and search features, and automated email notifications.
IPM_E_8.2.2012

Quick Solution delivery offered by Knowledge IT provides industry-specific solutions including patent & intellectual property, manufacturing, medical & health care, beauty & care, education, oil and energy, and government. It offers 5 solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It also provides various productivity applications that can be customized for professional, business, enterprise, and ultimate users.
IRM_E_7.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and copy incidents to reuse resolved issues. The software provides role-based access and integrates with third party tools.
HRCM_E_2FEB2012

The document describes Knowledge IT's software-as-a-service (SaaS) applications for various industries. It offers 6 main applications for intellectual property management, HR management, incident response management, and more. It also lists related products including object, review, and schedule managers. The applications are available at different tiers for individual, small/medium business, enterprise, and ultimate users. Features include search, data import/export, and alert/escalation messages.
IRM_E_15.3.12

The document describes Knowledge IT's incident management software solutions. It offers products for professional, business, enterprise, and ultimate users. The software allows users to search, register, and track incidents. Analysts can view assigned incidents, add follow-ups, and modify incidents. Users can view their incident list, follow-ups from analysts, and acknowledge when incidents are resolved. The software also enables copying incidents and on-demand escalation through email.
IRM_E_17.03.2012

The document describes an incident management software solution offered by Knowledge IT Corporation. It includes the following key capabilities:
1. Incident registration, assignment to analysts, and tracking of status and resolution through a web interface.
2. Communication features like follow ups, notifications, and feedback between users and analysts to resolve incidents.
3. Flexible configuration options for organizations of different sizes, including user roles and access privileges.
4. Automated escalation workflows that notify managers when incidents meet defined response time thresholds.
IRM_E_25.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different business needs. Their applications include modules for intellectual property management, HR strategy, CRM incident management, emergency incidence management, and corporate governance management. They provide applications tailored for professional individual/small business use, business use, enterprise use, and ultimate/large company use. Their applications integrate easily with third-party software and allow customizing the functions used.
IRM_E_12.03.12

Knowledge IT is a technology solutions provider that offers various SaaS applications for different industries and business needs. Their applications include modules for IP management, HR strategy, CRM, emergency management, and corporate governance. The document highlights Knowledge IT's product categories including professional, business, enterprise, and ultimate applications. It provides examples of how the applications can be used for incident search, registration, follow up, and modification.
IRM_E_14.3.12

The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users, analysts, and managers to view, assign, update, and close incidents through an online portal. It also enables escalation of incidents by email if response criteria are not met.
IRM_E_14.03.2012

The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users to search, view assigned incidents, add follow-ups, and close incidents. It also enables escalating unresolved incidents through automated emails.
Is “Freedom to Operate” Mission Impossible? | OCTANe Event

Is “Freedom to Operate” Mission Impossible? | OCTANe EventKnobbe Martens - Intellectual Property Law
A panel of experts discussed the concept of “freedom to operate” in the context of evaluating and mitigating third party patent infringement risk at a recent OCTANe OC event. The discussion focused on startup companies, and the topics included: How to analyze the third party patent landscape; How to set an appropriate budget based on the company’s objectives and milestones; Understanding the impact of litigation on the company; What to do if the company is sued. Ensuring freedom to operate: IP inventory and FTO analysis

Presented by Linda Opati at the First Bio-Innovate Regional Scientific Conference, Addis Ababa, Ethiopia, 25-27 February 2013
More Related Content
What's hot
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer customizable software products that include modules for functions like IP management, HR strategy, and corporate governance. Customers can choose which modules they need rather than being required to use all functions of an application.
IPM_E_3.2.12

The document describes Knowledge IT's solutions and products for intellectual property management. It lists various industry verticals Knowledge IT serves and its key solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It then lists Knowledge IT's products which include tools like Object Manager, Administration Manager, Review Manager, and Project Manager. The document explains Knowledge IT offers applications tailored for different organization sizes from professional to ultimate. It provides examples of folder registration and access management, annotation/comment features, and escalation emails for document operations.
HSM_E_7.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides a variety of industry-specific and functional SaaS solutions to meet different business needs. Their applications include HR strategy, intellectual property, incident response, and corporate governance management and can be customized using only required functions. Knowledge IT aims to offer easy-to-deploy software services at competitive pricing to help small and large businesses improve efficiency and reduce costs.
IRM_E_24.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications to support different business needs across industries. Their applications include modules for intellectual property management, human resources strategy, customer relationship management, emergency management, and corporate governance management. The applications allow users to access only required functions and integrate with third-party software. Knowledge IT's applications are available at different tiers - Professional, Business, Enterprise, and Ultimate - tailored for organizations of various sizes from sole proprietors to large enterprises.
HSM_E_23.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different industries and business needs. Their applications include tools for intellectual property management, human resources strategy, customer relationship management, emergency incident management, and corporate governance management. The applications are role-based and allow customization so users only access needed functions. Knowledge IT's solutions range from individual professional plans to enterprise-level offerings for large organizations. They allow easy third-party integration and data migration management between different application modules. The platforms also include features for annotations, escalation workflows, and automated email notifications.
HSM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions across various industries including manufacturing, healthcare, education, and energy. They offer 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to business needs from individual use to large enterprises. Knowledge IT's products include features like IP management, HR strategy management, incidence response management, and more that can be customized and integrated with third party software.
IEM_E_13.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different types of organizations and industries. Their applications include modules for intellectual property management, human resources, emergency response, and corporate governance. The applications allow customers to use only the necessary functions and integrate with third-party software. Knowledge IT's applications are available at different tiers to suit organizations of various sizes, from individual users to large enterprises.
IRM_E_17.3.12

Quick Solution Delivery Offered by Knowledge IT provides industry-specific solutions for patent/intellectual property, manufacturing, healthcare, beauty/care, education, oil/energy, and other industries. It offers 4 types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. Key features include incident management, folder organization, user login and access controls, and notification escalation.
IRM_E_19.3.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, view incident history, and integrate with other third-party software. The software is offered in various tiers to suit organizations of different sizes, from individual use to enterprise-level systems managing hundreds of users.
IPM_E_8.2.2012

This document discusses Knowledge IT's quick solution delivery offerings across various industries. It provides an overview of 5 solutions - IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It also describes Knowledge IT's product suite which includes tools like Object Manager, Administration Manager, Review Manager, and others. Finally, it discusses Knowledge IT's 4 types of applications - Professional, Business, Enterprise, and Ultimate - which are tailored for customers based on needs and user demand.
IPM_E_8.2.2012

This document summarizes the services offered by Knowledge IT, including industry-specific solutions and products for intellectual property management, HR management, emergency management, and other functions. It describes Knowledge IT's SaaS application offerings for professional, business, enterprise, and ultimate users. Key capabilities highlighted include document management with folder structure and security, annotation and search features, and automated email notifications.
IPM_E_8.2.2012

Quick Solution delivery offered by Knowledge IT provides industry-specific solutions including patent & intellectual property, manufacturing, medical & health care, beauty & care, education, oil and energy, and government. It offers 5 solutions: IP Management, HR Collaborative Management, Incidence Response Management, Incidence & Emergency Management, and Corporate Governance Management. It also provides various productivity applications that can be customized for professional, business, enterprise, and ultimate users.
IRM_E_7.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and copy incidents to reuse resolved issues. The software provides role-based access and integrates with third party tools.
HRCM_E_2FEB2012

The document describes Knowledge IT's software-as-a-service (SaaS) applications for various industries. It offers 6 main applications for intellectual property management, HR management, incident response management, and more. It also lists related products including object, review, and schedule managers. The applications are available at different tiers for individual, small/medium business, enterprise, and ultimate users. Features include search, data import/export, and alert/escalation messages.
IRM_E_15.3.12

The document describes Knowledge IT's incident management software solutions. It offers products for professional, business, enterprise, and ultimate users. The software allows users to search, register, and track incidents. Analysts can view assigned incidents, add follow-ups, and modify incidents. Users can view their incident list, follow-ups from analysts, and acknowledge when incidents are resolved. The software also enables copying incidents and on-demand escalation through email.
IRM_E_17.03.2012

The document describes an incident management software solution offered by Knowledge IT Corporation. It includes the following key capabilities:
1. Incident registration, assignment to analysts, and tracking of status and resolution through a web interface.
2. Communication features like follow ups, notifications, and feedback between users and analysts to resolve incidents.
3. Flexible configuration options for organizations of different sizes, including user roles and access privileges.
4. Automated escalation workflows that notify managers when incidents meet defined response time thresholds.
IRM_E_25.2.12

Knowledge IT offers a variety of software-as-a-service (SaaS) applications for different business needs. Their applications include modules for intellectual property management, HR strategy, CRM incident management, emergency incidence management, and corporate governance management. They provide applications tailored for professional individual/small business use, business use, enterprise use, and ultimate/large company use. Their applications integrate easily with third-party software and allow customizing the functions used.
IRM_E_12.03.12

Knowledge IT is a technology solutions provider that offers various SaaS applications for different industries and business needs. Their applications include modules for IP management, HR strategy, CRM, emergency management, and corporate governance. The document highlights Knowledge IT's product categories including professional, business, enterprise, and ultimate applications. It provides examples of how the applications can be used for incident search, registration, follow up, and modification.
IRM_E_14.3.12

The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users, analysts, and managers to view, assign, update, and close incidents through an online portal. It also enables escalation of incidents by email if response criteria are not met.
IRM_E_14.03.2012

The document describes Knowledge IT's incident management software. It offers solutions for various industries and functions for managing incidents from registration through resolution. The software allows users to search, view assigned incidents, add follow-ups, and close incidents. It also enables escalating unresolved incidents through automated emails.
What's hot (20)
Viewers also liked
Is “Freedom to Operate” Mission Impossible? | OCTANe Event

Is “Freedom to Operate” Mission Impossible? | OCTANe EventKnobbe Martens - Intellectual Property Law
A panel of experts discussed the concept of “freedom to operate” in the context of evaluating and mitigating third party patent infringement risk at a recent OCTANe OC event. The discussion focused on startup companies, and the topics included: How to analyze the third party patent landscape; How to set an appropriate budget based on the company’s objectives and milestones; Understanding the impact of litigation on the company; What to do if the company is sued. Ensuring freedom to operate: IP inventory and FTO analysis

Presented by Linda Opati at the First Bio-Innovate Regional Scientific Conference, Addis Ababa, Ethiopia, 25-27 February 2013
Freedom To Operate

This document discusses freedom to operate (FTO) analysis, which provides a legal opinion on potential patent infringement for a new product. It outlines approaches to FTO including analysis of a product's components against third party intellectual property, and drafting an opinion on infringement likelihood. The document then discusses various strategies to obtain FTO, including licensing needed patents, modifying the product design, abandoning the project, or merging with other companies. It notes challenges for public sector institutions in planning early for FTO due to different priorities than private companies.
Freedom to Operate FTO

This document discusses Freedom to Operate (FTO) analysis, which assesses the intellectual property rights and tangible property rights of others that may be relevant to a new product or process in development. It describes the FTO principles, preparations, procedures, perspectives, options for obtaining FTO status, and strategies. The key aspects are performing an FTO analysis by dissecting the new technology, searching patent and scientific databases iteratively, drafting an FTO opinion on infringement risk, determining an FTO status, and formulating an FTO strategy based on that status. The FTO analysis is most effective when conducted early in product development before significant resources are invested.
Methods to improve Freedom to Operate analysis

This document discusses improving freedom to operate (FTO) analysis through comprehensive risk assessment and targeted patent searching. It provides an overview of patent filing trends, litigation statistics in key regions like the US and Europe, and a business case study on conducting an FTO analysis for a proposed fuel tank product. New semantic search technologies available in tools like PatentOptimizer can help enable more precise and recall patent searches to better inform FTO evaluations.
RD FTO 2016_F

The document discusses freedom to operate (FTO) in intellectual property. It defines FTO as the ability to capitalize on an invention without challenges from other patent holders. The author cautions that during research and development, one must carefully record all materials, tools, and processes used and identify any existing exclusivity claims. Several strategies are discussed for circumventing or removing obstacles to FTO, such as paying to license a patent, exchanging technologies, inventing around a patent, or sharing patents or confidential information. The document provides an example of FTO considerations for biopharmaceutical research and development and discusses a technology using deuterium to extend drug effects. It concludes with discussing concepts and strategies for searching patents.
Collection Secrets Presentation

The document provides tips and strategies for effective accounts receivable management and debt collection. It recommends verifying customer information, having clear terms of sale, following up with customers systematically, using positive communication, and educating oneself on best practices. It also lists sample forms that can be used and provides resources for additional information on credit and collections.
Viewers also liked (7)
Is “Freedom to Operate” Mission Impossible? | OCTANe Event

Is “Freedom to Operate” Mission Impossible? | OCTANe Event
Ensuring freedom to operate: IP inventory and FTO analysis

Ensuring freedom to operate: IP inventory and FTO analysis
Similar to IPM_E_17.3.12
CIM_E_24.2.12

Knowledge IT is a software company that offers various SaaS applications for different industries and business needs. Their solutions include products for intellectual property management, HR strategy, CRM, emergency management, and corporate governance. Their applications can be used by individuals, small businesses, or large enterprises. Knowledge IT's document highlights some of their incident management software, including features for adding and viewing incidents, registering incidents, responding to incidents, categorizing incidents in folders, searching incidents, and escalating incidents via email notifications.
HSM_E_21.4.12

Quick Solution Delivery Offered by Knowledge IT summarizes Knowledge IT's offerings in 3 sentences:
Knowledge IT provides industry-specific software solutions and products for functions like HR, intellectual property management, and incident response. Their software-as-a-service applications can be used by small businesses, large corporations, and governments and require no upfront installation. Knowledge IT's applications support configurable search forms, data migration management, annotation capabilities, and automated escalation emails.
IRM_E_1.4.12

This document summarizes the incident management software offered by Knowledge IT. The software allows users to register, track, and resolve incidents. Key features include the ability to assign incidents, add follow-ups, notify users of status updates, and escalate incidents that meet certain criteria. The software provides role-based access and is available in various tiers to suit organizations of different sizes.
HSM_E_1.4.12

Quick Solution Delivery Offered by Knowledge IT
Knowledge IT offers a variety of software-as-a-service (SaaS) applications across multiple industries that provide quick solutions without requiring initial investment or complex installation. Their applications support small and large businesses and can increase effectiveness while reducing expenses. Key features include customizable search forms, data migration management tools, annotation capabilities, and automatic escalation and email notifications.
CGS_E_19.3.12

Knowledge IT offers a variety of solutions and products for different industries including patent and intellectual property, manufacturing, medical and healthcare, beauty and care, education, oil and energy, electronics, franchising, construction, and government. Their solutions include HR strategy management, intellectual property management, incident response management, and corporate governance management. Their products include object manager, forensic manager, review manager, workflow manager, human resource manager, administration manager, project manager, discovery manager, schedule manager, and corporate manager. Knowledge IT offers applications tailored to different business needs from professional to ultimate.
CGS_E_1.3.12

Quick Solution Delivery Offered by Knowledge IT
Knowledge IT offers a variety of software as a service (SaaS) applications to meet different business needs. Their applications include tools for intellectual property management, human resources, customer relationship management, and more. Customers only need to use the specific functions relevant to their business. Knowledge IT also makes it easy to integrate their applications with third party software. They provide applications tailored for individuals, small and medium businesses, large enterprises, and customized solutions for very large companies.
CGS_E_23.4.12

Knowledge IT offers industry-specific solutions using their SaaS products which only utilize necessary functions. Their applications support various organization sizes from individuals to large corporations. The document describes their 4 types of applications - Professional, Business, Enterprise, and Ultimate - which differ based on needs, users, and control offered. It also outlines some key features including customer search, registration, mail escalation, and follow up functions.
CMS_01.03.12

Quick Solution Delivery Offered by Knowledge IT
Knowledge IT offers a variety of software as a service (SaaS) applications across different industries including manufacturing, healthcare, education, and government. Their applications include intellectual property management, HR strategy management, CRM incident response management, emergency incident management, and corporate governance management. Knowledge IT's products are modular and allow customers to use only the necessary functions, avoiding overuse of applications. Their applications are available at competitive prices without upfront costs and can support organizations of all sizes.
CGS_E_17.3.12

Knowledge IT offers industry-specific solutions and products for intellectual property management, human resources strategy management, incidence response management, and corporate governance management. Their solutions include object manager, forensic manager, review manager, workflow manager, and other applications that can be customized based on business needs. Knowledge IT also provides applications tailored for different business sizes from individual/SOHO use to large enterprises, with options for integration with third-party software. Customer relationship management features include customer search, registration, notifications, and follow-ups using internal and external emails.
CGS_E_7.4.12

Knowledge IT offers a variety of software solutions tailored for different industries and business needs. Their products include applications for HR strategy management, intellectual property management, incident response management, and corporate governance management. The document then describes their customizable software products which include object manager, forensic manager, review manager, and others. It explains that their applications are cloud-based and users only access the specific functions they require. Knowledge IT provides solutions for organizations of all sizes, from individuals and small businesses to large enterprises.
CGS_E_1.4.12

Knowledge IT offers a variety of solutions and products for different industries including patent & intellectual property, manufacturing, medical & health care, beauty & care, education, oil and energy, electronics, franchising, construction, and government. Their solutions include HR strategy management, intellectual property management, incident response management, and corporate governance management. Their products include object manager, forensic manager, review manager, workflow manager, human resource manager, administration manager, project manager, discovery manager, and schedule manager. Knowledge IT provides applications tailored to professional, business, enterprise, and ultimate users with flexible integration and customization options.
IRM_E_13.03.2012

Knowledge IT is a company that offers various IT solutions and products for different industries. It provides solutions for intellectual property management, HR strategy, and incident response management. Its products include modules for object management, forensic management, review management, and others. Knowledge IT also offers different types of applications - Professional, Business, Enterprise, and Ultimate - tailored to organizations of different sizes. The document provides details on Knowledge IT's solutions, products, application types and incident management workflow.
Similar to IPM_E_17.3.12 (12)
More from Hemant_Kumar_Setya
More from Hemant_Kumar_Setya (19)
Recently uploaded
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
A tale of scale & speed: How the US Navy is enabling software delivery from l...

Rapid and secure feature delivery is a goal across every application team and every branch of the DoD. The Navy’s DevSecOps platform, Party Barge, has achieved:
- Reduction in onboarding time from 5 weeks to 1 day
- Improved developer experience and productivity through actionable findings and reduction of false positives
- Maintenance of superior security standards and inherent policy enforcement with Authorization to Operate (ATO)
Development teams can ship efficiently and ensure applications are cyber ready for Navy Authorizing Officials (AOs). In this webinar, Sigma Defense and Anchore will give attendees a look behind the scenes and demo secure pipeline automation and security artifacts that speed up application ATO and time to production.
We will cover:
- How to remove silos in DevSecOps
- How to build efficient development pipeline roles and component templates
- How to deliver security artifacts that matter for ATO’s (SBOMs, vulnerability reports, and policy evidence)
- How to streamline operations with automated policy checks on container images
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications.
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
Building RAG with self-deployed Milvus vector database and Snowpark Container...

This talk will give hands-on advice on building RAG applications with an open-source Milvus database deployed as a docker container. We will also introduce the integration of Milvus with Snowpark Container Services.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Full-RAG: A modern architecture for hyper-personalization

Mike Del Balso, CEO & Co-Founder at Tecton, presents "Full RAG," a novel approach to AI recommendation systems, aiming to push beyond the limitations of traditional models through a deep integration of contextual insights and real-time data, leveraging the Retrieval-Augmented Generation architecture. This talk will outline Full RAG's potential to significantly enhance personalization, address engineering challenges such as data management and model training, and introduce data enrichment with reranking as a key solution. Attendees will gain crucial insights into the importance of hyperpersonalization in AI, the capabilities of Full RAG for advanced personalization, and strategies for managing complex data integrations for deploying cutting-edge AI solutions.
Essentials of Automations: The Art of Triggers and Actions in FME

In this second installment of our Essentials of Automations webinar series, we’ll explore the landscape of triggers and actions, guiding you through the nuances of authoring and adapting workspaces for seamless automations. Gain an understanding of the full spectrum of triggers and actions available in FME, empowering you to enhance your workspaces for efficient automation.
We’ll kick things off by showcasing the most commonly used event-based triggers, introducing you to various automation workflows like manual triggers, schedules, directory watchers, and more. Plus, see how these elements play out in real scenarios.
Whether you’re tweaking your current setup or building from the ground up, this session will arm you with the tools and insights needed to transform your FME usage into a powerhouse of productivity. Join us to discover effective strategies that simplify complex processes, enhancing your productivity and transforming your data management practices with FME. Let’s turn complexity into clarity and make your workspaces work wonders!
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Join us to introduce Milvus Lite, a vector database that can run on notebooks and laptops, share the same API with Milvus, and integrate with every popular GenAI framework. This webinar is perfect for developers seeking easy-to-use, well-integrated vector databases for their GenAI apps.
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

ABSTRACT: A prima vista, un mattoncino Lego e la backdoor XZ potrebbero avere in comune il fatto di essere entrambi blocchi di costruzione, o dipendenze di progetti creativi e software. La realtà è che un mattoncino Lego e il caso della backdoor XZ hanno molto di più di tutto ciò in comune.
Partecipate alla presentazione per immergervi in una storia di interoperabilità, standard e formati aperti, per poi discutere del ruolo importante che i contributori hanno in una comunità open source sostenibile.
BIO: Sostenitrice del software libero e dei formati standard e aperti. È stata un membro attivo dei progetti Fedora e openSUSE e ha co-fondato l'Associazione LibreItalia dove è stata coinvolta in diversi eventi, migrazioni e formazione relativi a LibreOffice. In precedenza ha lavorato a migrazioni e corsi di formazione su LibreOffice per diverse amministrazioni pubbliche e privati. Da gennaio 2020 lavora in SUSE come Software Release Engineer per Uyuni e SUSE Manager e quando non segue la sua passione per i computer e per Geeko coltiva la sua curiosità per l'astronomia (da cui deriva il suo nickname deneb_alpha).
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Recently uploaded (20)
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
A tale of scale & speed: How the US Navy is enabling software delivery from l...

A tale of scale & speed: How the US Navy is enabling software delivery from l...
Large Language Model (LLM) and it’s Geospatial Applications

Large Language Model (LLM) and it’s Geospatial Applications
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
Building RAG with self-deployed Milvus vector database and Snowpark Container...

Building RAG with self-deployed Milvus vector database and Snowpark Container...
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
Full-RAG: A modern architecture for hyper-personalization

Full-RAG: A modern architecture for hyper-personalization
Essentials of Automations: The Art of Triggers and Actions in FME

Essentials of Automations: The Art of Triggers and Actions in FME
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...
Cosa hanno in comune un mattoncino Lego e la backdoor XZ?

Cosa hanno in comune un mattoncino Lego e la backdoor XZ?
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Presentation of the OECD Artificial Intelligence Review of Germany

Presentation of the OECD Artificial Intelligence Review of Germany
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
IPM_E_17.3.12
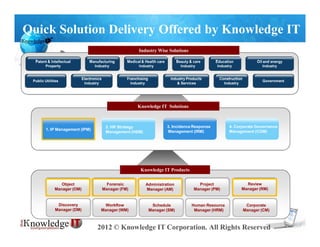
- 1. Quick Solution Delivery Offered by Knowledge IT Industry Wise Solutions Patent & Intellectual Manufacturing Medical & Health care Beauty & care Education Oil and energy Property Industry Industry Industry Industry Industry Electronics Franchising Industry Products Construction Public Utilities Government Industry Industry & Services Industry Knowledge IT Solutions 2. HR Strategy 3. Incidence Response 4. Corporate Governance 1. IP Management (IPM) Management (HSM) Management (IRM) Management (CGM) Knowledge IT Products Object Forensic Administration Project Review Manager (OM) Manager (FM) Manager (AM) Manager (PM) Manager (RM) Discovery Workflow Schedule Human Resource Corporate Manager (DM) Manager (WM) Manager (SM) Manager (HRM) Manager (CM) 2012 © Knowledge IT Corporation. All Rights Reserved
- 2. Pick and Use Functions that you Need With any application, you effectively use only 10% of the application. But with Knowledge IT’s SaaS applications, you use only those functions that you need. The Knowledge IT Products Object Forensic Manager (OM) Manager (FM) Review Workflow Manager (RM) Manager (WM) Human Resource Administration Manager (HRM) Manager (AM) Project Discovery Manager (PM) Manager (DM) Corporate Schedule Manager (CM) Manager (SM) Easy Third Party Software Integration 2012 © Knowledge IT Corporation. All Rights Reserved
- 3. Knowledge IT’s 4 Types of Application Based on Needs & User Demand Knowledge IT offers a variety of SaaS applications which do not require initial investment and installation effort, by providing easy-to-deploy software services at competitive pricing. The applications supports small businesses and large corporations, contributing to increasing effectiveness and reducing expenses. Professional Business Enterprise Ultimate Individuals・SOHO Small and Medium Small and Medium For large companies Personal Offices enterprises or Enterprises or looking for full control or Small Offices Shop owners Enterprise Subcontractors and autonomy Best for individual Suitable for system ranging Ideal for organizations and Highly specialized set of use and smaller from two to multiple users. businesses with large groups. administration tools in an businesses Data access for packaged Security, access privileges as application is ideal for large groups predetermined privilege based. well as functions can be of people in an organization. This Size: 1-5 Persons Secure user access. determined by the customer and Ultimate set comes with the freedom Users: 1 Person set/added per category of users to build a solution view and dig- Size: 2-1000 Persons from Packaged Solution. down feature according to each Users: 30 and above customer’s need. Role based as well Size: 100-1000 Persons as privilege based access control can Users: 50 and above be set by the Business and above. Size: 100 Persons and above Users: 100 and above 2012 © Knowledge IT Corporation. All Rights Reserved
- 4. Document and Folder Management Login By IP Firm Add documents from here Options are provided to search You can view all or latest versions your documents of the documents added By this function you can add, modify or delete the folder/ subfolder Perform different operation on your Documents under folders privileged. Folders can be viewed in the tree according to the privilege provided Folder added security wise. Secure your documents under secured folders. 2012 © Knowledge IT Corporation. All Rights Reserved
- 5. Client by Client Folder View Login by Client1 Secured folder and document view for client1 Login by Client2 Secured folder and document view for client2 2012 © Knowledge IT Corporation. All Rights Reserved
- 6. Add Annotations/Comments Login By IP Firm Annotation added by IP Firm for Client 1 Login by Client 1 Various Index Forms Client 1 can add or respond to the added annotation. Annotation icon 2012 © Knowledge IT Corporation. All Rights Reserved
- 7. Document Search with Different Criteria Login by Client 1 Document full Text Search by different customized forms. Various Search Forms Document Search Result for the above Searched criteria. 2012 © Knowledge IT Corporation. All Rights Reserved
- 8. View Auto Mails on Document Operations Login by IP Firm Get Document Information details by an auto mail feature whenever any operation is performed like add, modify, adding annotations etc. Auto Mail forwarded to Client1 after adding some document attachments. 2012 © Knowledge IT Corporation. All Rights Reserved
- 9. Document Attachment View Security Wise Login by Client1 This is a secured document of client 2, hence Client 1 has no permission to view this file 2012 © Knowledge IT Corporation. All Rights Reserved