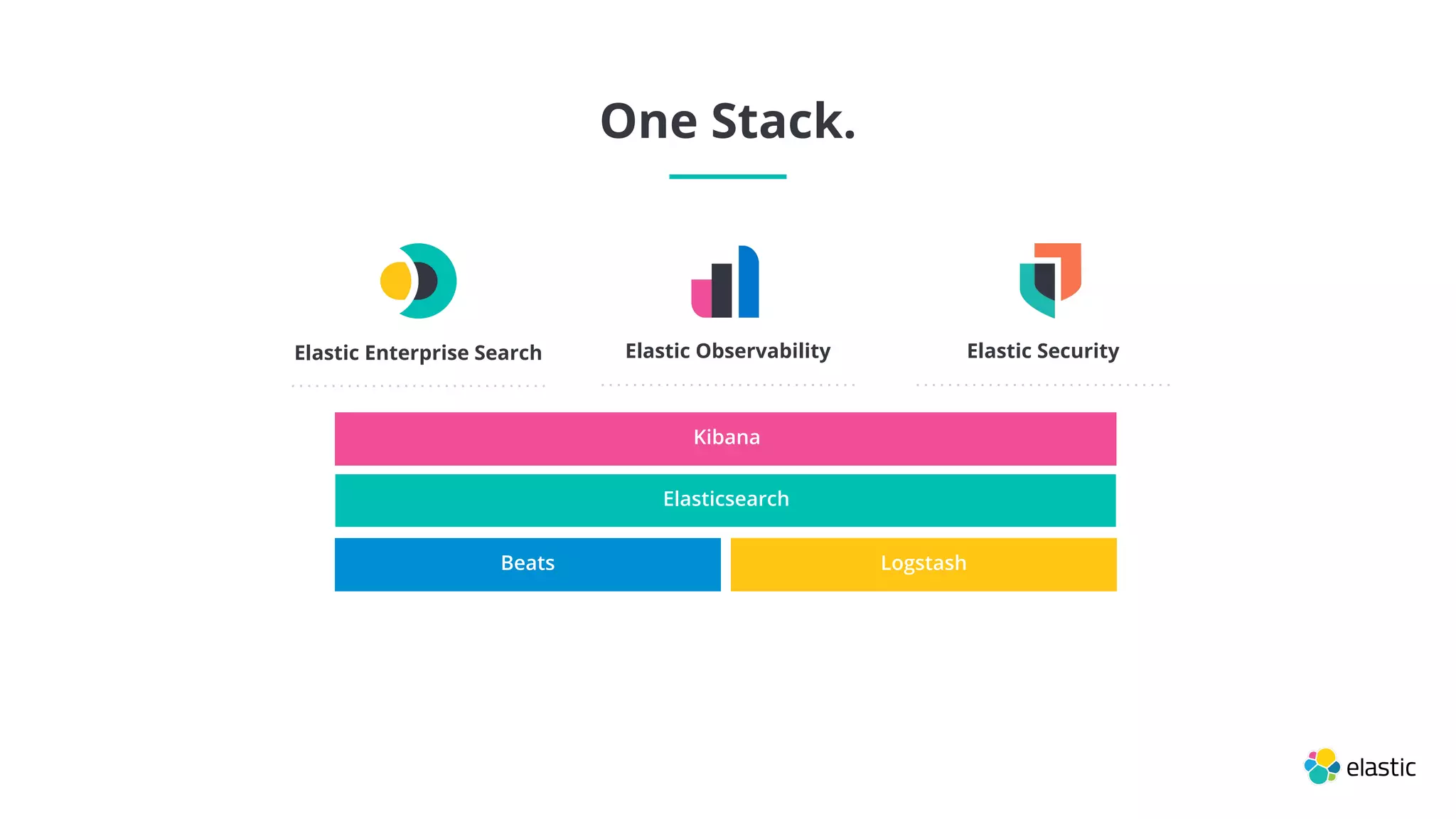
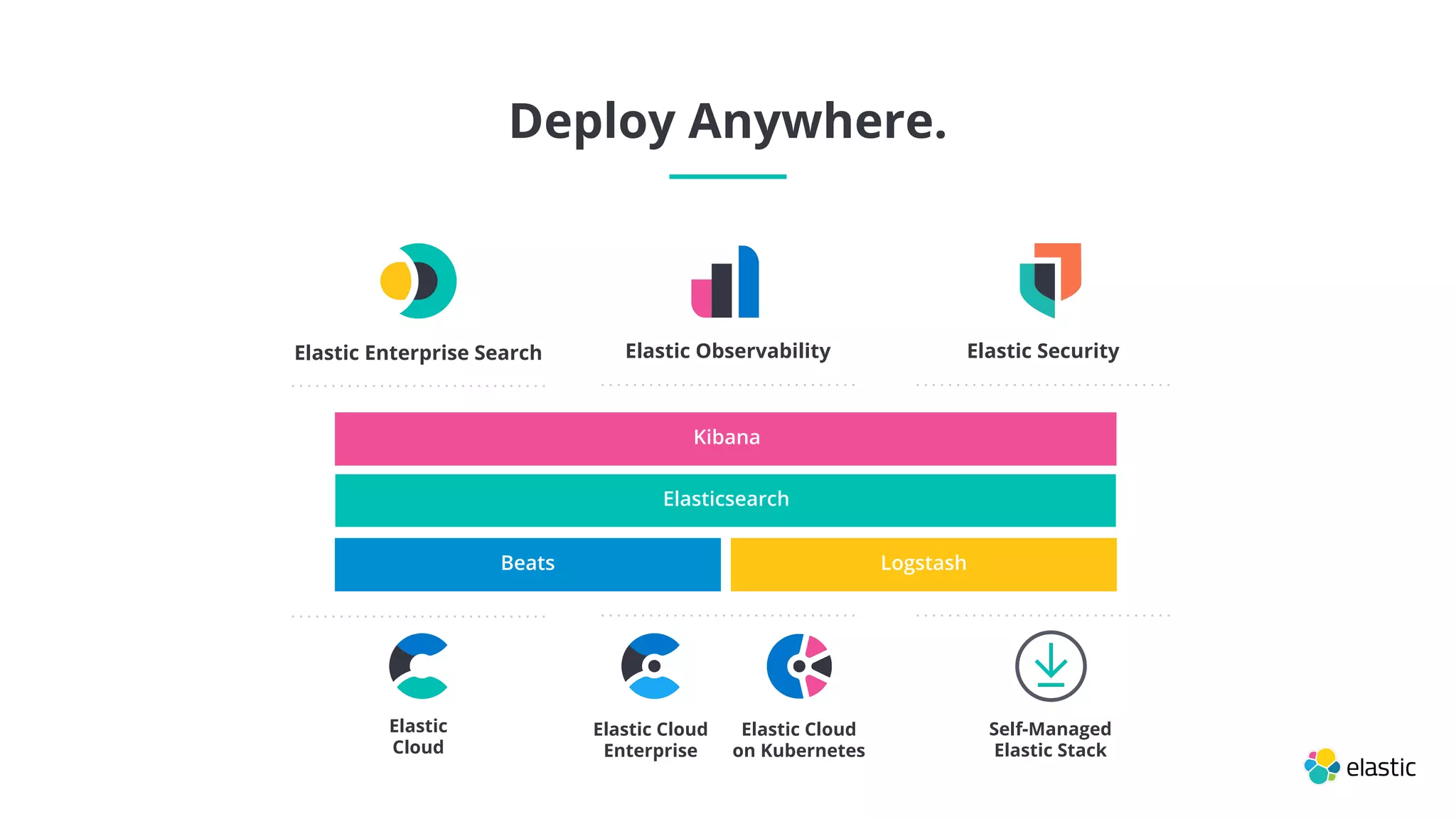
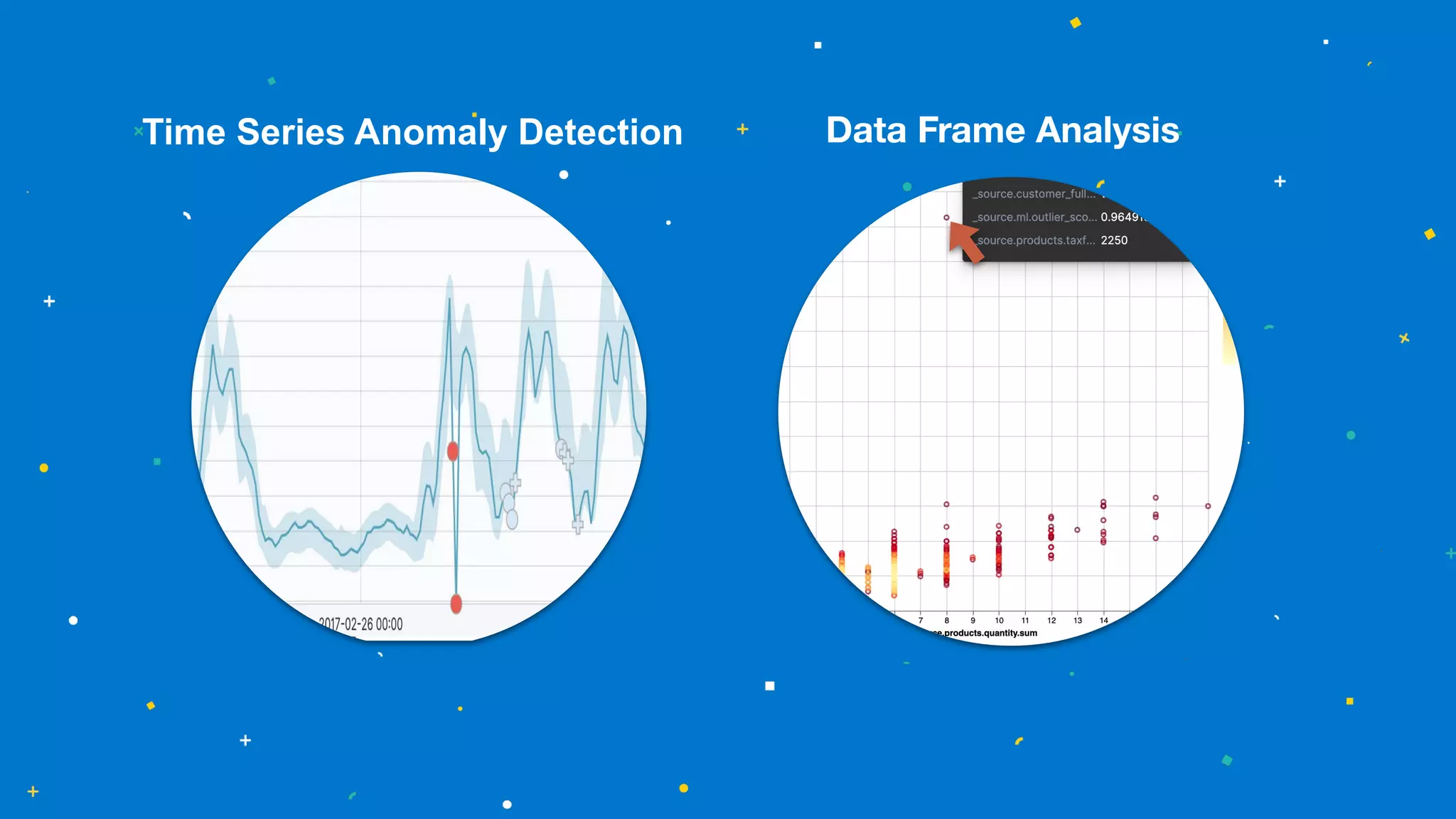
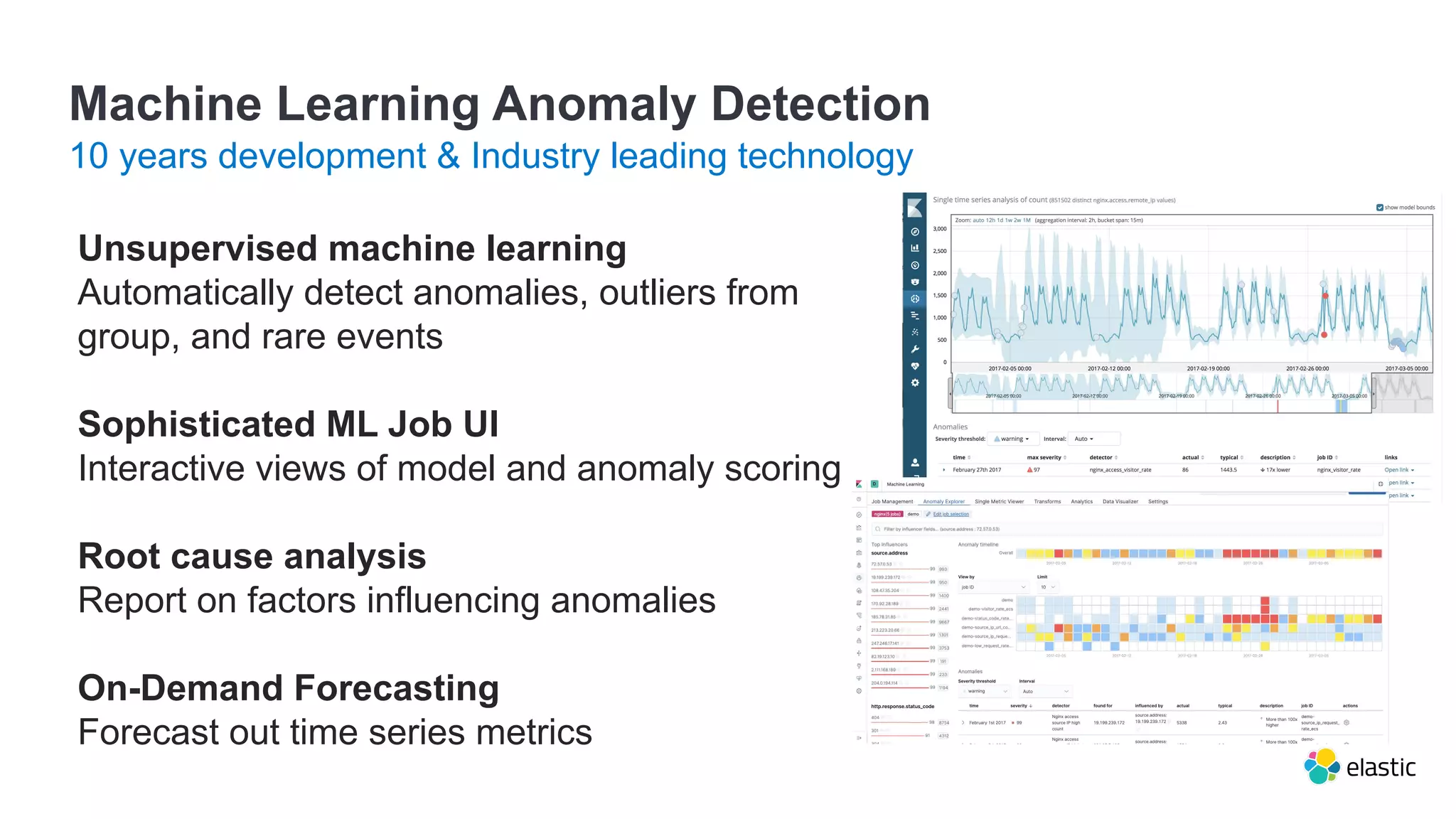
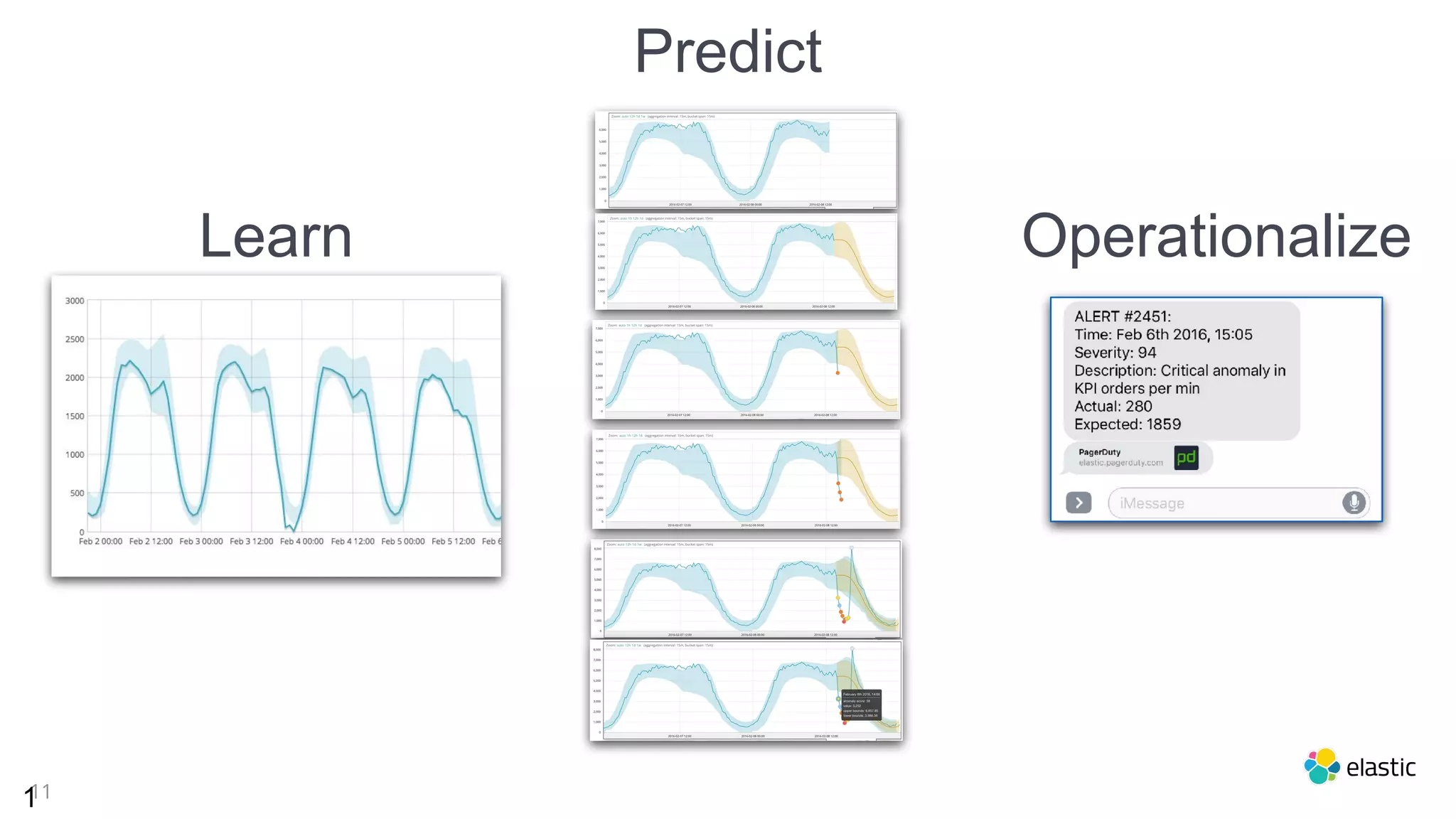
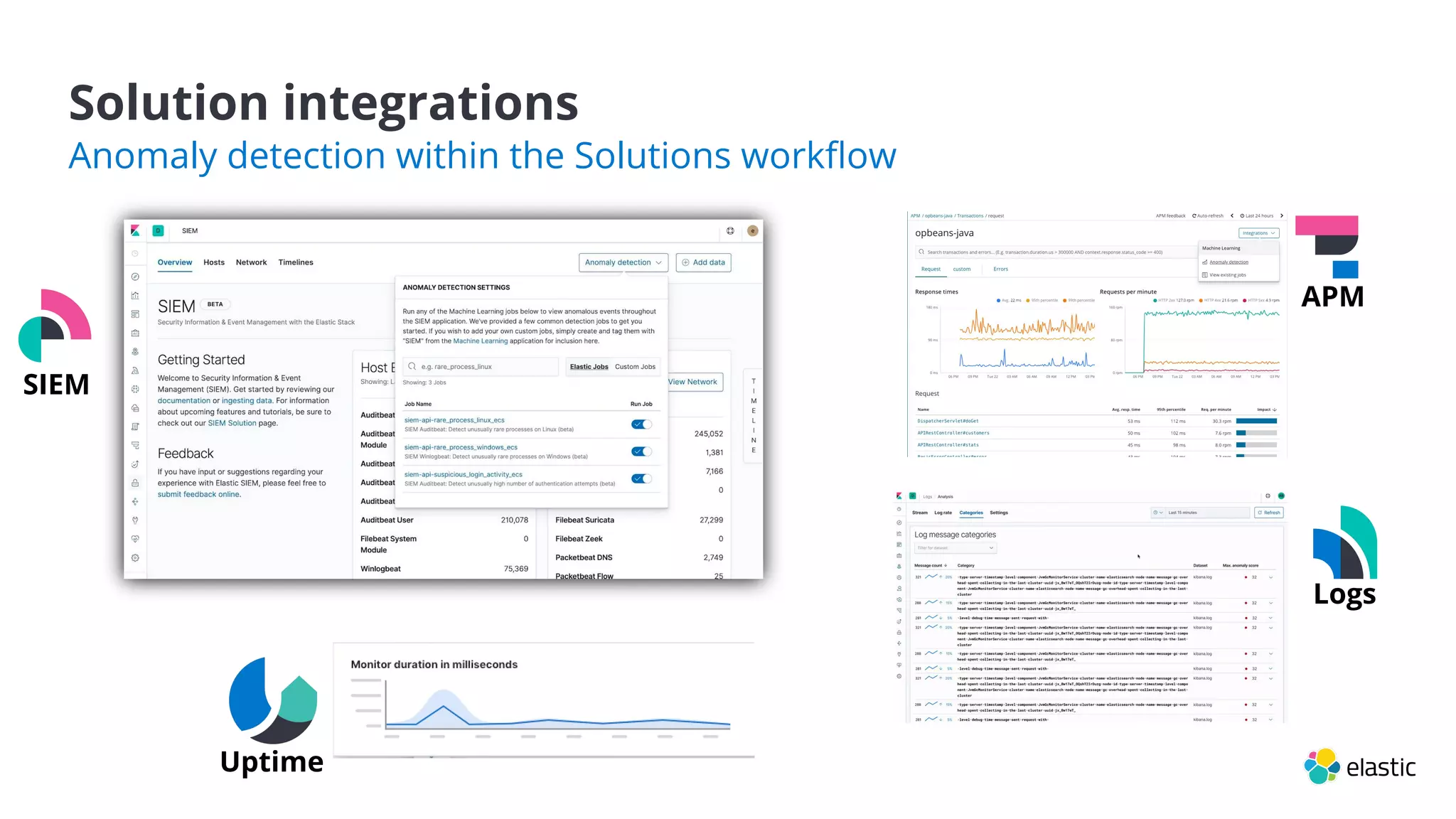
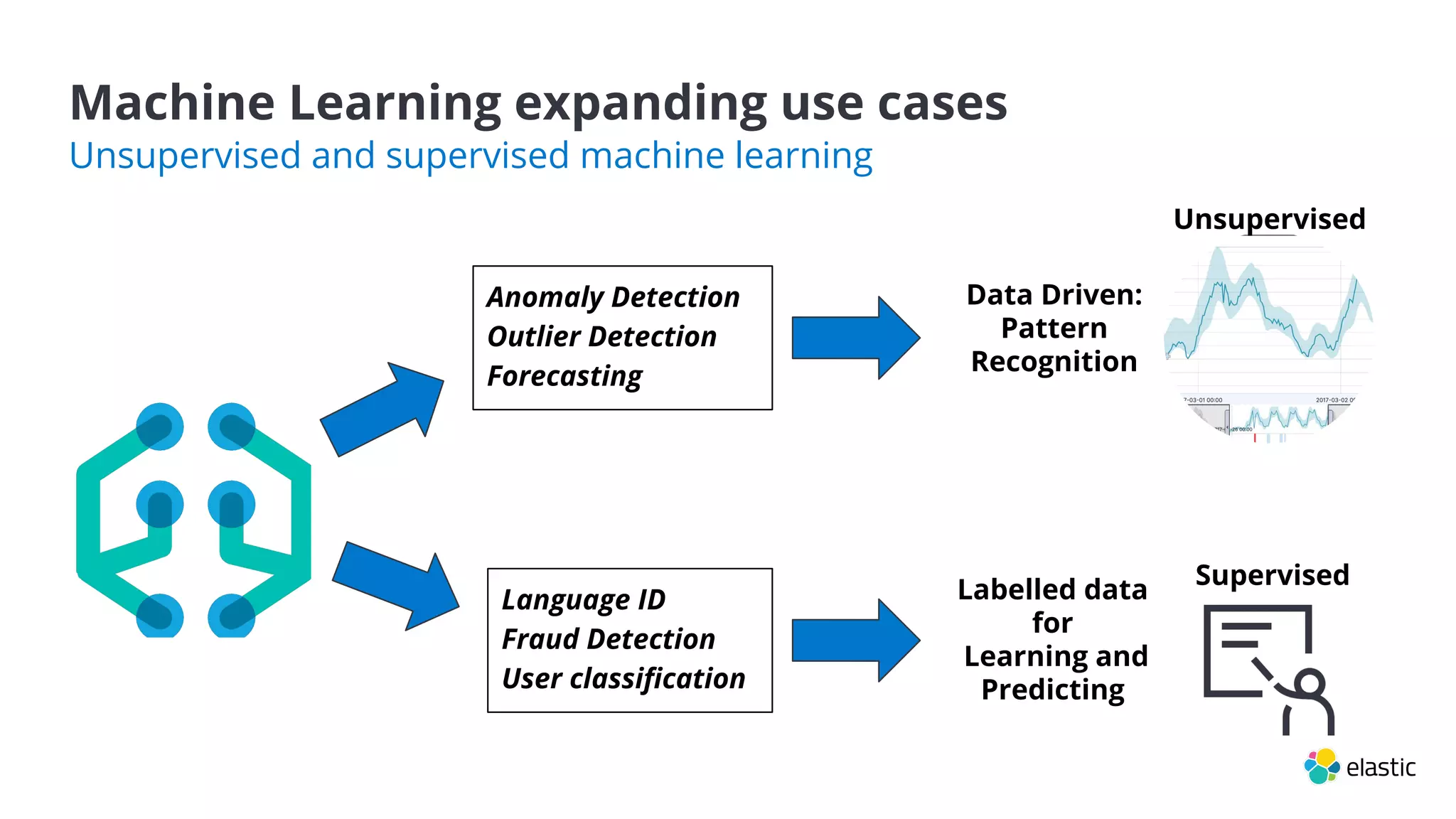
This document summarizes an Elastic webinar on machine learning in Elastic Search. It introduces the speakers and provides an overview of Elastic's machine learning capabilities including anomaly detection, time series analysis, and forecasting. It also demonstrates anomaly detection and discusses how machine learning can be used for tasks like language identification, fraud detection, and user classification. The webinar explores both unsupervised and supervised machine learning techniques and how ML can help with search relevance, observability, and security use cases.