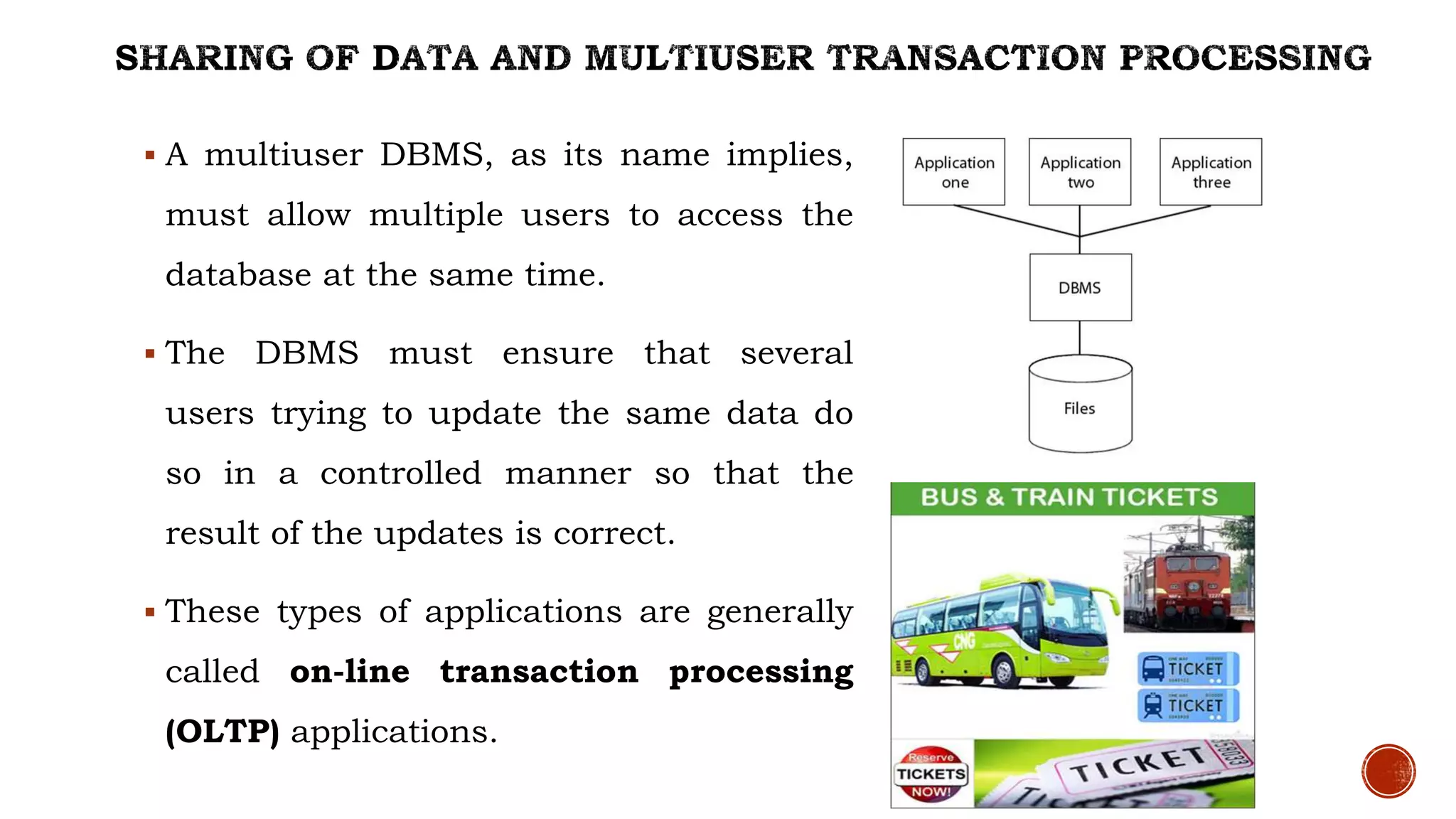
This document describes a database management systems course. It includes:
- Two textbooks that will be used
- The course learning objectives, which are to understand database concepts, practice SQL programming, learn about concurrency/transactions, and design real-world database applications.
- An outline of the 5 course modules, which will cover database introduction, data modeling, relational model/logical design, SQL, normalization, and transaction processing.











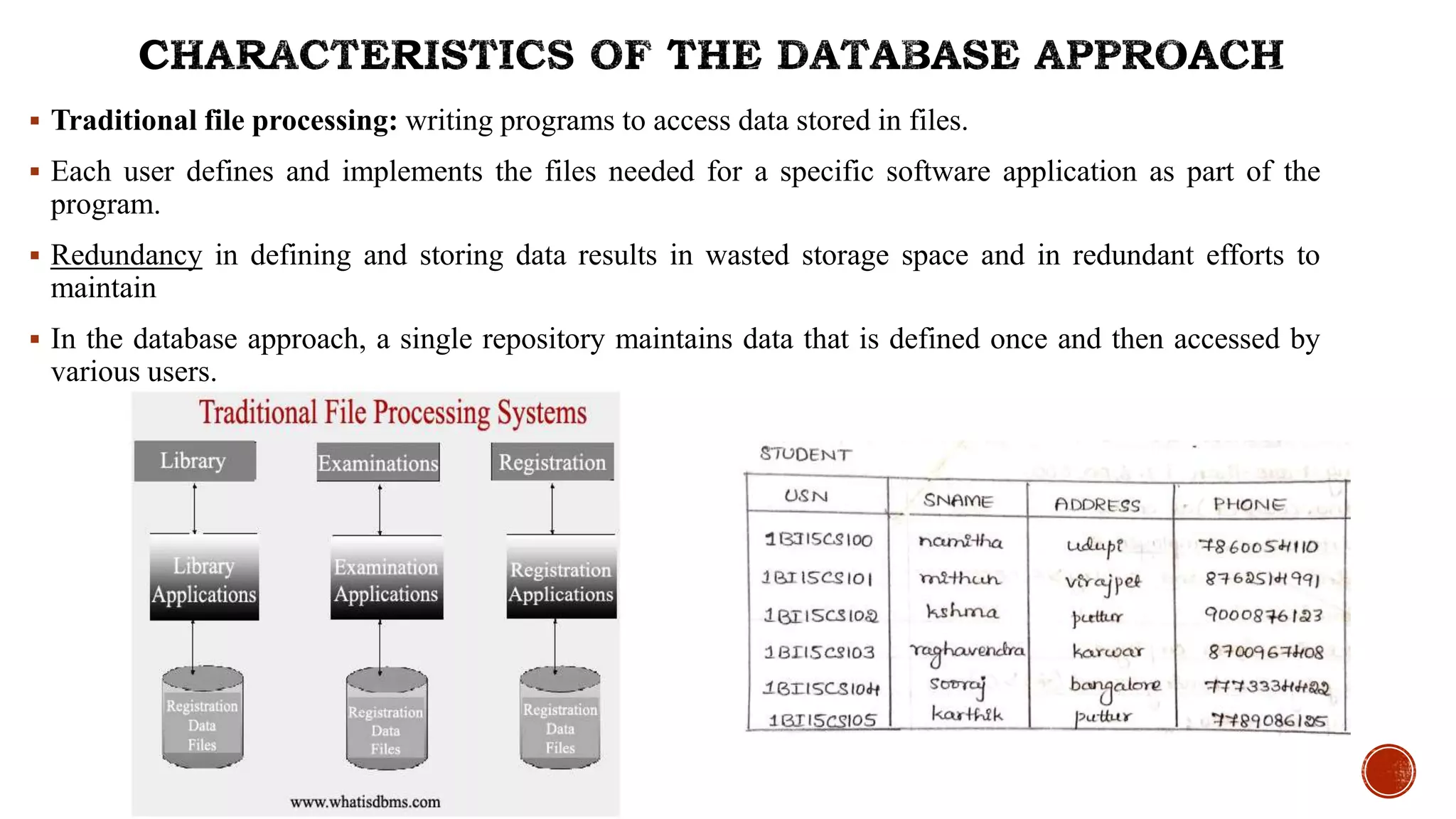


![#include <stdio.h>
int main()
{
int snum , i;
char sname[20];
FILE *fptr;
fptr = fopen("C:student.txt" ,"w");
for (i=0;i<10;i++)
{
printf("Enter student num , name ");
scanf("%d %s",&snum,sname);
fprintf(fptr,"%d %s",snum,sname);
}
fclose(fptr);
return 0;
}](https://image.slidesharecdn.com/module1-221101180032-72e6ade2/75/Introduction-to-DBMS-pptx-23-2048.jpg)