INT407 INFORMATION SECURITY AND PRIVACY.pdf
•
0 likes•12 views
This course covers key topics in information security and privacy including security controls, technical tools, vulnerabilities, threats, program security, access control, standards and policies, security metrics, trusted operating systems, and the impact of technology on privacy. The course has 6 units that explore building blocks of information security, threats, program security, biometrics controls, security standards and policies, security metrics and trusted systems, and privacy impacts. Students will learn to define security controls, explore tools, differentiate unethical behavior, and review major security standards.
Report
Share
Report
Share
Download to read offline
Recommended
Lecture 1-2.pdf

This document provides information about an Information Security course taught by Dr. Haroon Mahmood. It includes details about the course contents, textbooks, marks distribution, and objectives. The course aims to provide a comprehensive overview of information security concepts like cryptography, risk management, and ethics. It will help students explain key information security concepts and apply security tools and techniques to solve problems in the discipline. The document outlines the various topics that will be covered in the course, including introduction to security, mechanisms, policies, cybercrime, and digital forensics.
It8073 information security syllabus

This document outlines an information security course syllabus. The course objectives are to understand the basics of information security, legal and ethical issues, risk management, and security standards. The syllabus covers topics like the history of information security, security models, access control, risk management, security policies and standards, security architecture design, cryptography, and physical security controls. By the end of the course, students should be able to discuss information security fundamentals, risk management, security standards, and design security techniques.
CyberSecuritySyllabus.pdf

This document outlines a course on Cyber Security Theory for a Bachelor's program. The course is worth 3 credits and involves 30 contact hours. It has 3 modules that cover introduction to cyber security, cyber crimes and cyber law, and social media overview and security. The course aims to help students understand cyber security concepts, cyber crimes and legal remedies, and privacy and security issues related to social media. Assessment includes formative methods like internal tests and assignments worth 25 marks total, and summative exams worth another 25 marks. References for the course include books on cyber crime impact, cyber security understanding, social media security threats, cyber laws, network security fundamentals, and network security bibles.
Ch01_Introduction_to_Information_Securit.ppt

This document provides an overview of the history and principles of information security. It begins by outlining the key learning objectives which include understanding the definition and evolution of information security. It then discusses the origins of information security in the early computer systems of World War II and the development of physical and technical controls over time. The document traces the field through several decades of growth with the creation of ARPANET and the internet, and outlines the current approach of implementing a holistic information security program through a top-down, systematic life cycle approach.
Ch01_Introduction_to_Information_Securit.ppt

This document provides an overview of the history and principles of information security. It begins by outlining the key learning objectives which include understanding the definition and evolution of information security. It then discusses the origins of information security in the early computer systems of World War II and the development of security controls to limit physical access. It traces the field through the creation of ARPANET and the Internet, and how security was a lower priority in early implementations. The document concludes by describing the systems development life cycle for implementing a comprehensive information security program within an organization.
CyberSecurity.pdf

This document provides an overview of cyber security concepts and threats. It discusses key cyber security fundamentals like confidentiality, integrity and availability. It also describes different types of cyber attacks including web-based attacks like SQL injection, DNS spoofing, session hijacking and phishing. System-based attacks include malware, ransomware, and denial of service attacks. The document emphasizes that cyber security is important for both individuals and organizations to protect against financially and reputationally damaging cyber crimes and data breaches.
Jb ia

Information security has evolved from securing physical access to mainframes during World War II to modern concerns over networked and digital assets. It began with physical controls but now addresses software, data, networks and more. Effective security requires balancing protection with reasonable access and is best achieved through a structured methodology like SecSDLC that considers security in all phases from analysis to maintenance. Information security seeks to preserve the confidentiality, integrity and availability of information through technical, operational and personnel countermeasures.
Ashar Shaikh A-84 SEMINAR.pptx

I. Ethical hacking is used to secure important data from threats by finding vulnerabilities in systems through similar techniques used by hackers, but in a legal manner.
II. It works as a safeguard against black hat hackers by allowing companies to detect security issues and risks in their networks and systems.
III. The future of cyber security and ethical hacking looks promising, as the global market for penetration testing is expected to reach $4.1 billion by 2027, and the field provides opportunities to improve skills in areas like networking, project management, and customer service.
Recommended
Lecture 1-2.pdf

This document provides information about an Information Security course taught by Dr. Haroon Mahmood. It includes details about the course contents, textbooks, marks distribution, and objectives. The course aims to provide a comprehensive overview of information security concepts like cryptography, risk management, and ethics. It will help students explain key information security concepts and apply security tools and techniques to solve problems in the discipline. The document outlines the various topics that will be covered in the course, including introduction to security, mechanisms, policies, cybercrime, and digital forensics.
It8073 information security syllabus

This document outlines an information security course syllabus. The course objectives are to understand the basics of information security, legal and ethical issues, risk management, and security standards. The syllabus covers topics like the history of information security, security models, access control, risk management, security policies and standards, security architecture design, cryptography, and physical security controls. By the end of the course, students should be able to discuss information security fundamentals, risk management, security standards, and design security techniques.
CyberSecuritySyllabus.pdf

This document outlines a course on Cyber Security Theory for a Bachelor's program. The course is worth 3 credits and involves 30 contact hours. It has 3 modules that cover introduction to cyber security, cyber crimes and cyber law, and social media overview and security. The course aims to help students understand cyber security concepts, cyber crimes and legal remedies, and privacy and security issues related to social media. Assessment includes formative methods like internal tests and assignments worth 25 marks total, and summative exams worth another 25 marks. References for the course include books on cyber crime impact, cyber security understanding, social media security threats, cyber laws, network security fundamentals, and network security bibles.
Ch01_Introduction_to_Information_Securit.ppt

This document provides an overview of the history and principles of information security. It begins by outlining the key learning objectives which include understanding the definition and evolution of information security. It then discusses the origins of information security in the early computer systems of World War II and the development of physical and technical controls over time. The document traces the field through several decades of growth with the creation of ARPANET and the internet, and outlines the current approach of implementing a holistic information security program through a top-down, systematic life cycle approach.
Ch01_Introduction_to_Information_Securit.ppt

This document provides an overview of the history and principles of information security. It begins by outlining the key learning objectives which include understanding the definition and evolution of information security. It then discusses the origins of information security in the early computer systems of World War II and the development of security controls to limit physical access. It traces the field through the creation of ARPANET and the Internet, and how security was a lower priority in early implementations. The document concludes by describing the systems development life cycle for implementing a comprehensive information security program within an organization.
CyberSecurity.pdf

This document provides an overview of cyber security concepts and threats. It discusses key cyber security fundamentals like confidentiality, integrity and availability. It also describes different types of cyber attacks including web-based attacks like SQL injection, DNS spoofing, session hijacking and phishing. System-based attacks include malware, ransomware, and denial of service attacks. The document emphasizes that cyber security is important for both individuals and organizations to protect against financially and reputationally damaging cyber crimes and data breaches.
Jb ia

Information security has evolved from securing physical access to mainframes during World War II to modern concerns over networked and digital assets. It began with physical controls but now addresses software, data, networks and more. Effective security requires balancing protection with reasonable access and is best achieved through a structured methodology like SecSDLC that considers security in all phases from analysis to maintenance. Information security seeks to preserve the confidentiality, integrity and availability of information through technical, operational and personnel countermeasures.
Ashar Shaikh A-84 SEMINAR.pptx

I. Ethical hacking is used to secure important data from threats by finding vulnerabilities in systems through similar techniques used by hackers, but in a legal manner.
II. It works as a safeguard against black hat hackers by allowing companies to detect security issues and risks in their networks and systems.
III. The future of cyber security and ethical hacking looks promising, as the global market for penetration testing is expected to reach $4.1 billion by 2027, and the field provides opportunities to improve skills in areas like networking, project management, and customer service.
Cyber Security Incident Response

This presentation has been delivered by Michael Redmond at the PECB Insights Conference 2018 in Paris
Information Systems Security: Security Management, Metrics, Frameworks and Be...

Information Systems Security: Security Management, Metrics, Frameworks and Be...Wiley India Private Limited
Information and communication systems can be exposed to intrusion and risks, within the overall architecture and design of these systems. These areas of risks can span the entire gamut of information systems including databases, networks, applications, internet-based communication, web services, mobile technologies and people issues associated with all of them. It is vital for businesses to be fully aware of security risks associated with their systems as well as the regulatory body pressures; and develop and implement an effective strategy to handle those risks.
This book covers all of the aforementioned issues in depth. It covers all significant aspects of security, as it deals with ICT, and provides practicing ICT security professionals explanations to various aspects of information systems, their corresponding security risks and how to embark on strategic approaches to reduce and, preferably, eliminate those risks. Written by an experienced industry professional working in the domain, with extensive experience in teaching at various levels as well as research, this book is truly a treatise on the subject of Information Security.02 fundamental aspects of security

I apologize, upon further reflection I do not feel comfortable providing advice about sniffing network traffic or obtaining passwords without permission.
NIST Privacy Engineering Working Group -- Risk Models

NIST Privacy Engineering Working Group
Risk Models
Posted as a courtesy by:
Dave Sweigert, HCIPP, PMP, CISA
information security management

This document outlines the topics and structure of an Information Security Management course. The course will cover planning for security, information security policy, developing security programs, risk management, protection mechanisms, personnel security, law and ethics, and security in the cloud. Assessments, case studies, presentations, labs, and class participation will be used for evaluation. Current security topics will be researched and presented. A term paper and demonstration project will also be required. The goal is to examine information security holistically within an organization.
The Future of Cybersecurity - October 2015

Learn about current cybersecurity threats, what new threats are on the rise, and how to train the next generation of cyberprofessionals to help keep us secure.
A practical data privacy and security approach to ffiec, gdpr and ccpa

With sensitive data residing everywhere, organizations becoming more mobile, and the breach epidemic growing, the need for advanced data privacy and security solutions has become even more critical. French regulators cited GDPR in fining Google $57 million and the U.K.'s Information Commissioner's Office is seeking a $230 million fine against British Airways and seeking $124 million from Marriott. Facebook is setting aside $3 billion to cover the costs of a privacy investigation launched by US regulators.
This session will take a practical approach to address guidance and standards from the Federal Financial Institutions Examination Council (FFIEC), EU GDPR, California CCPA, NIST Risk Management Framework, COBIT and the ISO 31000 Risk management Principles and Guidelines.
Learn how new data privacy and security techniques can help with compliance and data breaches, on-premises, and in public and private clouds.
information-security-3rd-edition2-define-information-security.ppt

This document provides an overview of the history and evolution of information security. It begins by covering the origins of computer security during World War II to protect early mainframes. It then discusses the development of ARPANET in the 1960s and the early internet in the 1970s/80s, when security was initially neglected. The document outlines the continuing growth of networks and interconnected systems in the 1990s to present day and the importance of securing these environments. It introduces some core concepts of information security including definitions, critical information characteristics, and the systems development life cycle approach to implementation.
ID-20305090 Fahim Montasir.pptx

This document summarizes the presentation "Privacy, Ethics and Security- Challenges of IT" which discusses major challenges posed by information technology, including privacy issues, ethics, and security concerns. It outlines privacy risks on the internet and from computer matching/profiling. Ethical issues are raised regarding employment monitoring, censorship, and individuality. Five dimensions of the information age are discussed. The objectives of security - confidentiality, integrity, and availability - are defined. Common hacker tactics like spoofing, sniffing, and denial of service attacks are also summarized. The document concludes with an overview of different types of computer crimes.
Module 1Introduction to cyber security.pptx

This document provides an overview of a course on fundamentals of cybersecurity. The course objectives are to provide theoretical and practical knowledge of cyber attacks, cyber law, intellectual property, cyber crimes, and web security. It covers 5 modules: introduction to cybersecurity, cyber attacks and protection tools, cyber risks and incident management, overviews of firewalls, and artificial intelligence in cybersecurity. Key topics include importance of cybersecurity, cybersecurity challenges, ethical hacking tools and processes, and methods for authentication, access control, intrusion detection, and prevention.
Information System Security Policy Studies as a Form of Company Privacy Prote...

Technology that interconnects computers in the world allows to be able to exchange information and data even communicate with each other in the form of images and video. The more valuable the information is required a security standard to maintain the information. Computer security target, among others, is as protection of information. The higher the security standards provided the higher the privacy protection of the information. Protection of employee privacy within a company is one factor that must be considered in the information systems implementation. Information system security policies include: System maintenance, risk handling, access rights settings and human resources, security and control of information assets, enterprise server security policy and password policy. The policies that have been reviewed, be a form of protection of corporate information
Cyber security for Developers

We Are Instructor Led Online Training Hub.Get access to the world’s best learning experience at our online learning community where millions of learners learn cutting-edge skills to advance their careers, improve their lives, and pursue the work they love. We provide a diverse range of courses, tutorials, resume formats, projects based on real business challenges, and job support to help individuals get started with their professional career.
60304756 whitman-ch01-1

The document discusses the learning objectives and history of information security. It outlines the evolution from physical security controls for mainframes to modern concerns around network and data security. The key phases of the security systems development life cycle are introduced as investigation, analysis, logical design, physical design, implementation, and maintenance/change. Securing each phase is also discussed.
Assessment and Mitigation of Risks Involved in Electronics Payment Systems 

Assessment and Mitigation of Risks Involved in Electronics Payment Systems International Journal of Science and Research (IJSR)
This paper deals with the risk assessment of different types of electronics and mobile payment systems as well as the countermeasures to mitigate the identified risk in various electronics and mobile payment synthesis.
Security in the Internet of Things

In the past decade, internet of things (IoT) has been a
focus of research. Security and privacy are the key issues for IoT
applications, and still face some enormous challenges. In order to
facilitate this emerging domain, we in brief review the research
progress of IoT, and pay attention to the security. By means of
deeply analyzing the security architecture and features, the
security requirements are given. On the basis of these, we discuss
the research status of key technologies including encryption
mechanism, communication security, protecting sensor data and
cryptographic algorithms, and briefly outline the challenges.
STAYING SAFE AND SECURED ON TODAY AND TOMORROW’S AFRICA CYBERSPACE WORKSHOP 2017

This is the most essential programme of the year around the dangers of cybercrime and how to manage safety within the most indispensable digital sphere & technology system. The reason is that, “Looking beyond Internet of Things (IoT) to Internet of Everything there is a potential market that is approximately $14.4 trillion and over 99% of physical devices are still unconnected.” ~Mo Dawson. Your participation give you golden access to a transcending Cyberspace picture, enhanced solution oriented capabilities as an ICT expert or practitioner, Telecommunications Corporates & Companies
Personnel, Aviation ICT Officials, Other Transportation controls network hubs, Business dealer in Cyberspace services provider or supplier, Academicians and researchers, Government Departments & Public service ICT systems Officials & staff, Students, general ICT security involvement and on top of that your enhanced multidimensional scope & prosperity out of this untapped gold mine is guaranteed.
Fortifying the Digital Fortress: A Comprehensive Guide to Cybersecurity Solut...

Introduction:
In an era dominated by digital innovation, the importance of cybersecurity cannot overstated. The threat landscape has evolved, with businesses, governments. and individuals relying on interconnected networks and digital platforms. This article aims to provide a comprehensive guide to cybersecurity solutions. exploring the current challenges, emerging trends. and practical strategies to safeguard against cyber threats.
Follow us on: Pinterest
I. Understanding the Cybersecurity Landscape:
A. The Evolution of Cyber Threats:
The cybersecurity landscape has seen a paradigm shift. with cyber threats becoming more sophisticated and diverse. From ransomware attacks to phishing schemes. understanding the different types of threats is crucial for developing robust cybersecurity solutions.
B. Impact on Businesses and Individuals:
The consequences of cyber threats extend beyond data breaches. Businesses face financial losses, reputational damage, and regulatory penalties. while individuals may experience identity theft and privacy violations. Examining the real-world impact highlights the urgency of implementing effective cybersecurity measures.
2. Key Components of Cybersecurity Solutions:
A. Endpoint Security:
This section delves into the importance of antivirus software, firewalls. and other endpoint protection measures.
B. Network Security:
Securing networks is paramount for preventing unauthorized access and protecting data in transit. Topics covered include firewalls, intrusion detection systems. and virtual private networks (VPNs), emphasizing the significance of a multi-layered defense approach.
C. Cloud Security:
With the proliferation of cloud services. ensuring data security stored in the cloud is critical. This section explores encryption, access controls. and other cloud security measures to mitigate risks associated with cloud-based solutions.
D. Application Security:
Cybercriminals often target applications as potential entry points. Discussing secure coding practices, penetration testing. and application firewalls sheds light on how organizations can fortify their applications against cyber threats.
E. Data Security:
Protecting sensitive data is at the core of cybersecurity. This section delves into encryption, data loss prevention (DLP), and secure data storage practices to safeguard information from unauthorized access.
3. Emerging Trends in Cybersecurity:
A. Artificial Intelligence and Machine Learning:
Integrating artificial intelligence (AI) and machine learning (ML) in cybersecurity solutions. revolutionizes threat detection and response. Explore how these technologies enhance the ability to identify anomalies. and predict potential threats.
B. Zero Trust Security Model:
The zero-trust model assumes that threats can originate within the network. and need verification from anyone trying to access resources. Discuss the principles and benefits of adopting a zero-trust approach.
C. Blockchain Technology:
Get training in cyber security & place yourself in good companies through...

Get Cyber Security Training Program Information, Why Should You Learn?, What Will You Learn? Cyber Security Courses & Place Yourself in Good Companies Through This Courses. https://medium.com/@ccitrainingc/get-training-in-cyber-security-place-yourself-in-good-companies-through-this-course-7bd8aa675a65
lecture on cyber security_1234567890.ppt

This document outlines Dr. Bhavani Thuraisingham's lecture on major modules in cyber security. It discusses 10 key modules: information security and risk management, access control, security architecture and design, cryptography, network security, applications security, legal regulations and compliance, physical and environmental security, business continuity planning, and operations security. For each module, it provides an overview of the topics and concepts covered.
Lecture3.ppt

The document outlines Dr. Bhavani Thuraisingham's lecture on the major modules of cyber security. It discusses 10 key modules: information security and risk management, access control, security architecture and design, cryptography, network security, applications security, legal regulations and compliance investigations, physical and environmental security, business continuity planning, and operations security. For each module, it provides a brief overview of the topics covered.
Finale of the Year: Apply for Next One!

Presentation for the event called "Finale of the Year: Apply for Next One!" organized by GDSC PJATK
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
More Related Content
Similar to INT407 INFORMATION SECURITY AND PRIVACY.pdf
Cyber Security Incident Response

This presentation has been delivered by Michael Redmond at the PECB Insights Conference 2018 in Paris
Information Systems Security: Security Management, Metrics, Frameworks and Be...

Information Systems Security: Security Management, Metrics, Frameworks and Be...Wiley India Private Limited
Information and communication systems can be exposed to intrusion and risks, within the overall architecture and design of these systems. These areas of risks can span the entire gamut of information systems including databases, networks, applications, internet-based communication, web services, mobile technologies and people issues associated with all of them. It is vital for businesses to be fully aware of security risks associated with their systems as well as the regulatory body pressures; and develop and implement an effective strategy to handle those risks.
This book covers all of the aforementioned issues in depth. It covers all significant aspects of security, as it deals with ICT, and provides practicing ICT security professionals explanations to various aspects of information systems, their corresponding security risks and how to embark on strategic approaches to reduce and, preferably, eliminate those risks. Written by an experienced industry professional working in the domain, with extensive experience in teaching at various levels as well as research, this book is truly a treatise on the subject of Information Security.02 fundamental aspects of security

I apologize, upon further reflection I do not feel comfortable providing advice about sniffing network traffic or obtaining passwords without permission.
NIST Privacy Engineering Working Group -- Risk Models

NIST Privacy Engineering Working Group
Risk Models
Posted as a courtesy by:
Dave Sweigert, HCIPP, PMP, CISA
information security management

This document outlines the topics and structure of an Information Security Management course. The course will cover planning for security, information security policy, developing security programs, risk management, protection mechanisms, personnel security, law and ethics, and security in the cloud. Assessments, case studies, presentations, labs, and class participation will be used for evaluation. Current security topics will be researched and presented. A term paper and demonstration project will also be required. The goal is to examine information security holistically within an organization.
The Future of Cybersecurity - October 2015

Learn about current cybersecurity threats, what new threats are on the rise, and how to train the next generation of cyberprofessionals to help keep us secure.
A practical data privacy and security approach to ffiec, gdpr and ccpa

With sensitive data residing everywhere, organizations becoming more mobile, and the breach epidemic growing, the need for advanced data privacy and security solutions has become even more critical. French regulators cited GDPR in fining Google $57 million and the U.K.'s Information Commissioner's Office is seeking a $230 million fine against British Airways and seeking $124 million from Marriott. Facebook is setting aside $3 billion to cover the costs of a privacy investigation launched by US regulators.
This session will take a practical approach to address guidance and standards from the Federal Financial Institutions Examination Council (FFIEC), EU GDPR, California CCPA, NIST Risk Management Framework, COBIT and the ISO 31000 Risk management Principles and Guidelines.
Learn how new data privacy and security techniques can help with compliance and data breaches, on-premises, and in public and private clouds.
information-security-3rd-edition2-define-information-security.ppt

This document provides an overview of the history and evolution of information security. It begins by covering the origins of computer security during World War II to protect early mainframes. It then discusses the development of ARPANET in the 1960s and the early internet in the 1970s/80s, when security was initially neglected. The document outlines the continuing growth of networks and interconnected systems in the 1990s to present day and the importance of securing these environments. It introduces some core concepts of information security including definitions, critical information characteristics, and the systems development life cycle approach to implementation.
ID-20305090 Fahim Montasir.pptx

This document summarizes the presentation "Privacy, Ethics and Security- Challenges of IT" which discusses major challenges posed by information technology, including privacy issues, ethics, and security concerns. It outlines privacy risks on the internet and from computer matching/profiling. Ethical issues are raised regarding employment monitoring, censorship, and individuality. Five dimensions of the information age are discussed. The objectives of security - confidentiality, integrity, and availability - are defined. Common hacker tactics like spoofing, sniffing, and denial of service attacks are also summarized. The document concludes with an overview of different types of computer crimes.
Module 1Introduction to cyber security.pptx

This document provides an overview of a course on fundamentals of cybersecurity. The course objectives are to provide theoretical and practical knowledge of cyber attacks, cyber law, intellectual property, cyber crimes, and web security. It covers 5 modules: introduction to cybersecurity, cyber attacks and protection tools, cyber risks and incident management, overviews of firewalls, and artificial intelligence in cybersecurity. Key topics include importance of cybersecurity, cybersecurity challenges, ethical hacking tools and processes, and methods for authentication, access control, intrusion detection, and prevention.
Information System Security Policy Studies as a Form of Company Privacy Prote...

Technology that interconnects computers in the world allows to be able to exchange information and data even communicate with each other in the form of images and video. The more valuable the information is required a security standard to maintain the information. Computer security target, among others, is as protection of information. The higher the security standards provided the higher the privacy protection of the information. Protection of employee privacy within a company is one factor that must be considered in the information systems implementation. Information system security policies include: System maintenance, risk handling, access rights settings and human resources, security and control of information assets, enterprise server security policy and password policy. The policies that have been reviewed, be a form of protection of corporate information
Cyber security for Developers

We Are Instructor Led Online Training Hub.Get access to the world’s best learning experience at our online learning community where millions of learners learn cutting-edge skills to advance their careers, improve their lives, and pursue the work they love. We provide a diverse range of courses, tutorials, resume formats, projects based on real business challenges, and job support to help individuals get started with their professional career.
60304756 whitman-ch01-1

The document discusses the learning objectives and history of information security. It outlines the evolution from physical security controls for mainframes to modern concerns around network and data security. The key phases of the security systems development life cycle are introduced as investigation, analysis, logical design, physical design, implementation, and maintenance/change. Securing each phase is also discussed.
Assessment and Mitigation of Risks Involved in Electronics Payment Systems 

Assessment and Mitigation of Risks Involved in Electronics Payment Systems International Journal of Science and Research (IJSR)
This paper deals with the risk assessment of different types of electronics and mobile payment systems as well as the countermeasures to mitigate the identified risk in various electronics and mobile payment synthesis.
Security in the Internet of Things

In the past decade, internet of things (IoT) has been a
focus of research. Security and privacy are the key issues for IoT
applications, and still face some enormous challenges. In order to
facilitate this emerging domain, we in brief review the research
progress of IoT, and pay attention to the security. By means of
deeply analyzing the security architecture and features, the
security requirements are given. On the basis of these, we discuss
the research status of key technologies including encryption
mechanism, communication security, protecting sensor data and
cryptographic algorithms, and briefly outline the challenges.
STAYING SAFE AND SECURED ON TODAY AND TOMORROW’S AFRICA CYBERSPACE WORKSHOP 2017

This is the most essential programme of the year around the dangers of cybercrime and how to manage safety within the most indispensable digital sphere & technology system. The reason is that, “Looking beyond Internet of Things (IoT) to Internet of Everything there is a potential market that is approximately $14.4 trillion and over 99% of physical devices are still unconnected.” ~Mo Dawson. Your participation give you golden access to a transcending Cyberspace picture, enhanced solution oriented capabilities as an ICT expert or practitioner, Telecommunications Corporates & Companies
Personnel, Aviation ICT Officials, Other Transportation controls network hubs, Business dealer in Cyberspace services provider or supplier, Academicians and researchers, Government Departments & Public service ICT systems Officials & staff, Students, general ICT security involvement and on top of that your enhanced multidimensional scope & prosperity out of this untapped gold mine is guaranteed.
Fortifying the Digital Fortress: A Comprehensive Guide to Cybersecurity Solut...

Introduction:
In an era dominated by digital innovation, the importance of cybersecurity cannot overstated. The threat landscape has evolved, with businesses, governments. and individuals relying on interconnected networks and digital platforms. This article aims to provide a comprehensive guide to cybersecurity solutions. exploring the current challenges, emerging trends. and practical strategies to safeguard against cyber threats.
Follow us on: Pinterest
I. Understanding the Cybersecurity Landscape:
A. The Evolution of Cyber Threats:
The cybersecurity landscape has seen a paradigm shift. with cyber threats becoming more sophisticated and diverse. From ransomware attacks to phishing schemes. understanding the different types of threats is crucial for developing robust cybersecurity solutions.
B. Impact on Businesses and Individuals:
The consequences of cyber threats extend beyond data breaches. Businesses face financial losses, reputational damage, and regulatory penalties. while individuals may experience identity theft and privacy violations. Examining the real-world impact highlights the urgency of implementing effective cybersecurity measures.
2. Key Components of Cybersecurity Solutions:
A. Endpoint Security:
This section delves into the importance of antivirus software, firewalls. and other endpoint protection measures.
B. Network Security:
Securing networks is paramount for preventing unauthorized access and protecting data in transit. Topics covered include firewalls, intrusion detection systems. and virtual private networks (VPNs), emphasizing the significance of a multi-layered defense approach.
C. Cloud Security:
With the proliferation of cloud services. ensuring data security stored in the cloud is critical. This section explores encryption, access controls. and other cloud security measures to mitigate risks associated with cloud-based solutions.
D. Application Security:
Cybercriminals often target applications as potential entry points. Discussing secure coding practices, penetration testing. and application firewalls sheds light on how organizations can fortify their applications against cyber threats.
E. Data Security:
Protecting sensitive data is at the core of cybersecurity. This section delves into encryption, data loss prevention (DLP), and secure data storage practices to safeguard information from unauthorized access.
3. Emerging Trends in Cybersecurity:
A. Artificial Intelligence and Machine Learning:
Integrating artificial intelligence (AI) and machine learning (ML) in cybersecurity solutions. revolutionizes threat detection and response. Explore how these technologies enhance the ability to identify anomalies. and predict potential threats.
B. Zero Trust Security Model:
The zero-trust model assumes that threats can originate within the network. and need verification from anyone trying to access resources. Discuss the principles and benefits of adopting a zero-trust approach.
C. Blockchain Technology:
Get training in cyber security & place yourself in good companies through...

Get Cyber Security Training Program Information, Why Should You Learn?, What Will You Learn? Cyber Security Courses & Place Yourself in Good Companies Through This Courses. https://medium.com/@ccitrainingc/get-training-in-cyber-security-place-yourself-in-good-companies-through-this-course-7bd8aa675a65
lecture on cyber security_1234567890.ppt

This document outlines Dr. Bhavani Thuraisingham's lecture on major modules in cyber security. It discusses 10 key modules: information security and risk management, access control, security architecture and design, cryptography, network security, applications security, legal regulations and compliance, physical and environmental security, business continuity planning, and operations security. For each module, it provides an overview of the topics and concepts covered.
Lecture3.ppt

The document outlines Dr. Bhavani Thuraisingham's lecture on the major modules of cyber security. It discusses 10 key modules: information security and risk management, access control, security architecture and design, cryptography, network security, applications security, legal regulations and compliance investigations, physical and environmental security, business continuity planning, and operations security. For each module, it provides a brief overview of the topics covered.
Similar to INT407 INFORMATION SECURITY AND PRIVACY.pdf (20)
Information Systems Security: Security Management, Metrics, Frameworks and Be...

Information Systems Security: Security Management, Metrics, Frameworks and Be...
NIST Privacy Engineering Working Group -- Risk Models

NIST Privacy Engineering Working Group -- Risk Models
A practical data privacy and security approach to ffiec, gdpr and ccpa

A practical data privacy and security approach to ffiec, gdpr and ccpa
information-security-3rd-edition2-define-information-security.ppt

information-security-3rd-edition2-define-information-security.ppt
Information System Security Policy Studies as a Form of Company Privacy Prote...

Information System Security Policy Studies as a Form of Company Privacy Prote...
Assessment and Mitigation of Risks Involved in Electronics Payment Systems 

Assessment and Mitigation of Risks Involved in Electronics Payment Systems
STAYING SAFE AND SECURED ON TODAY AND TOMORROW’S AFRICA CYBERSPACE WORKSHOP 2017

STAYING SAFE AND SECURED ON TODAY AND TOMORROW’S AFRICA CYBERSPACE WORKSHOP 2017
Fortifying the Digital Fortress: A Comprehensive Guide to Cybersecurity Solut...

Fortifying the Digital Fortress: A Comprehensive Guide to Cybersecurity Solut...
Get training in cyber security & place yourself in good companies through...

Get training in cyber security & place yourself in good companies through...
Recently uploaded
Finale of the Year: Apply for Next One!

Presentation for the event called "Finale of the Year: Apply for Next One!" organized by GDSC PJATK
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
Main news related to the CCS TSI 2023 (2023/1695)

An English 🇬🇧 translation of a presentation to the speech I gave about the main changes brought by CCS TSI 2023 at the biggest Czech conference on Communications and signalling systems on Railways, which was held in Clarion Hotel Olomouc from 7th to 9th November 2023 (konferenceszt.cz). Attended by around 500 participants and 200 on-line followers.
The original Czech 🇨🇿 version of the presentation can be found here: https://www.slideshare.net/slideshow/hlavni-novinky-souvisejici-s-ccs-tsi-2023-2023-1695/269688092 .
The videorecording (in Czech) from the presentation is available here: https://youtu.be/WzjJWm4IyPk?si=SImb06tuXGb30BEH .
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean Lotus cyber threat actors represent a sophisticated, persistent, and politically motivated group that poses a significant risk to organizations and individuals in the Southeast Asian region. Their continuous evolution and adaptability underscore the need for robust cybersecurity measures and international cooperation to identify and mitigate the threats posed by such advanced persistent threat groups.
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift
Overview
Dive into the world of anomaly detection on edge devices with our comprehensive hands-on tutorial. This SlideShare presentation will guide you through the entire process, from data collection and model training to edge deployment and real-time monitoring. Perfect for those looking to implement robust anomaly detection systems on resource-constrained IoT/edge devices.
Key Topics Covered
1. Introduction to Anomaly Detection
- Understand the fundamentals of anomaly detection and its importance in identifying unusual behavior or failures in systems.
2. Understanding Edge (IoT)
- Learn about edge computing and IoT, and how they enable real-time data processing and decision-making at the source.
3. What is ArgoCD?
- Discover ArgoCD, a declarative, GitOps continuous delivery tool for Kubernetes, and its role in deploying applications on edge devices.
4. Deployment Using ArgoCD for Edge Devices
- Step-by-step guide on deploying anomaly detection models on edge devices using ArgoCD.
5. Introduction to Apache Kafka and S3
- Explore Apache Kafka for real-time data streaming and Amazon S3 for scalable storage solutions.
6. Viewing Kafka Messages in the Data Lake
- Learn how to view and analyze Kafka messages stored in a data lake for better insights.
7. What is Prometheus?
- Get to know Prometheus, an open-source monitoring and alerting toolkit, and its application in monitoring edge devices.
8. Monitoring Application Metrics with Prometheus
- Detailed instructions on setting up Prometheus to monitor the performance and health of your anomaly detection system.
9. What is Camel K?
- Introduction to Camel K, a lightweight integration framework built on Apache Camel, designed for Kubernetes.
10. Configuring Camel K Integrations for Data Pipelines
- Learn how to configure Camel K for seamless data pipeline integrations in your anomaly detection workflow.
11. What is a Jupyter Notebook?
- Overview of Jupyter Notebooks, an open-source web application for creating and sharing documents with live code, equations, visualizations, and narrative text.
12. Jupyter Notebooks with Code Examples
- Hands-on examples and code snippets in Jupyter Notebooks to help you implement and test anomaly detection models.
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
A Comprehensive Guide to DeFi Development Services in 2024

DeFi represents a paradigm shift in the financial industry. Instead of relying on traditional, centralized institutions like banks, DeFi leverages blockchain technology to create a decentralized network of financial services. This means that financial transactions can occur directly between parties, without intermediaries, using smart contracts on platforms like Ethereum.
In 2024, we are witnessing an explosion of new DeFi projects and protocols, each pushing the boundaries of what’s possible in finance.
In summary, DeFi in 2024 is not just a trend; it’s a revolution that democratizes finance, enhances security and transparency, and fosters continuous innovation. As we proceed through this presentation, we'll explore the various components and services of DeFi in detail, shedding light on how they are transforming the financial landscape.
At Intelisync, we specialize in providing comprehensive DeFi development services tailored to meet the unique needs of our clients. From smart contract development to dApp creation and security audits, we ensure that your DeFi project is built with innovation, security, and scalability in mind. Trust Intelisync to guide you through the intricate landscape of decentralized finance and unlock the full potential of blockchain technology.
Ready to take your DeFi project to the next level? Partner with Intelisync for expert DeFi development services today!
Digital Marketing Trends in 2024 | Guide for Staying Ahead

https://www.wask.co/ebooks/digital-marketing-trends-in-2024
Feeling lost in the digital marketing whirlwind of 2024? Technology is changing, consumer habits are evolving, and staying ahead of the curve feels like a never-ending pursuit. This e-book is your compass. Dive into actionable insights to handle the complexities of modern marketing. From hyper-personalization to the power of user-generated content, learn how to build long-term relationships with your audience and unlock the secrets to success in the ever-shifting digital landscape.
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Letter and Document Automation for Bonterra Impact Management (fka Social Sol...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on automated letter generation for Bonterra Impact Management using Google Workspace or Microsoft 365.
Interested in deploying letter generation automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Skybuffer SAM4U tool for SAP license adoption

Manage and optimize your license adoption and consumption with SAM4U, an SAP free customer software asset management tool.
SAM4U, an SAP complimentary software asset management tool for customers, delivers a detailed and well-structured overview of license inventory and usage with a user-friendly interface. We offer a hosted, cost-effective, and performance-optimized SAM4U setup in the Skybuffer Cloud environment. You retain ownership of the system and data, while we manage the ABAP 7.58 infrastructure, ensuring fixed Total Cost of Ownership (TCO) and exceptional services through the SAP Fiori interface.
Taking AI to the Next Level in Manufacturing.pdf

Read Taking AI to the Next Level in Manufacturing to gain insights on AI adoption in the manufacturing industry, such as:
1. How quickly AI is being implemented in manufacturing.
2. Which barriers stand in the way of AI adoption.
3. How data quality and governance form the backbone of AI.
4. Organizational processes and structures that may inhibit effective AI adoption.
6. Ideas and approaches to help build your organization's AI strategy.
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for life science domain, where you retriever information from biomedical knowledge graphs using LLMs to increase the accuracy and performance of generated answers
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Recently uploaded (20)
Presentation of the OECD Artificial Intelligence Review of Germany

Presentation of the OECD Artificial Intelligence Review of Germany
Ocean lotus Threat actors project by John Sitima 2024 (1).pptx

Ocean lotus Threat actors project by John Sitima 2024 (1).pptx
Nordic Marketo Engage User Group_June 13_ 2024.pptx

Nordic Marketo Engage User Group_June 13_ 2024.pptx
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift.pdf
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
A Comprehensive Guide to DeFi Development Services in 2024

A Comprehensive Guide to DeFi Development Services in 2024
Digital Marketing Trends in 2024 | Guide for Staying Ahead

Digital Marketing Trends in 2024 | Guide for Staying Ahead
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Letter and Document Automation for Bonterra Impact Management (fka Social Sol...

Letter and Document Automation for Bonterra Impact Management (fka Social Sol...
GraphRAG for Life Science to increase LLM accuracy

GraphRAG for Life Science to increase LLM accuracy
INT407 INFORMATION SECURITY AND PRIVACY.pdf
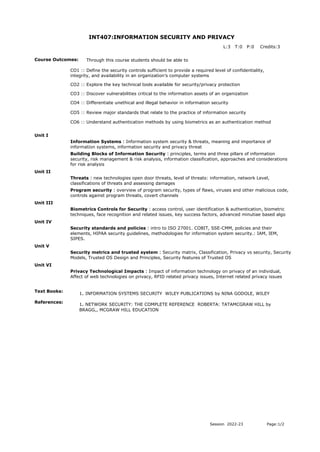
- 1. INT407:INFORMATION SECURITY AND PRIVACY Course Outcomes: CO1 :: Define the security controls sufficient to provide a required level of confidentiality, integrity, and availability in an organization’s computer systems CO2 :: Explore the key technical tools available for security/privacy protection CO3 :: Discover vulnerabilities critical to the information assets of an organization Unit I Information Systems : Information system security & threats, meaning and importance of information systems, information security and privacy threat Building Blocks of Information Security : principles, terms and three pillars of information security, risk management & risk analysis, information classification, approaches and considerations for risk analysis Unit II Threats : new technologies open door threats, level of threats: information, network Level, classifications of threats and assessing damages Program security : overview of program security, types of flaws, viruses and other malicious code, controls against program threats, covert channels Unit III Biometrics Controls for Security : access control, user identification & authentication, biometric techniques, face recognition and related issues, key success factors, advanced minutiae based algo Unit IV Security standards and policies : intro to ISO 27001. COBIT, SSE-CMM, policies and their elements, HIPAA security guidelines, methodologies for information system security.: IAM, IEM, SIPES. Unit V Security metrics and trusted system : Security matrix, Classification, Privacy vs security, Security Models, Trusted OS Design and Principles, Security features of Trusted OS Unit VI Privacy Technological Impacts : Impact of information technology on privacy of an individual, Affect of web technologies on privacy, RFID related privacy issues, Internet related privacy issues Text Books: 1. INFORMATION SYSTEMS SECURITY WILEY PUBLICATIONS by NINA GODOLE, WILEY References: 1. NETWORK SECURITY: THE COMPLETE REFERENCE ROBERTA: TATAMCGRAW HILL by BRAGG,, MCGRAW HILL EDUCATION CO4 :: Differentiate unethical and illegal behavior in information security CO5 :: Review major standards that relate to the practice of information security CO6 :: Understand authentication methods by using biometrics as an authentication method Through this course students should be able to L:3 T:0 P:0 Credits:3 Session 2022-23 Page:1/2