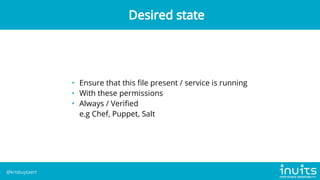
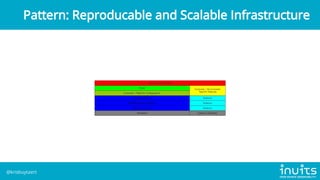
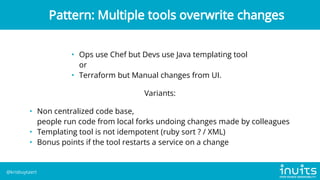
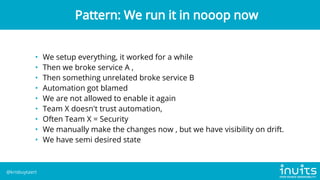
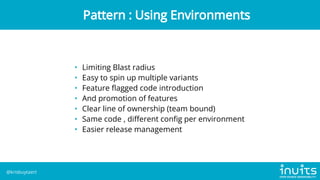
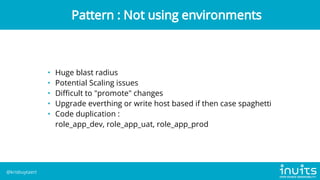
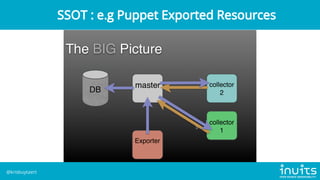
Kris Buytaert discusses the evolution of infrastructure as code (IaC) over 20 years, emphasizing the transition from manual installations to automated deployments using modern tools. He outlines the challenges of configuration drift, image sprawl, and the need for reproducible environments while advocating for best practices in IaC including version control, orchestration, and automated monitoring. Buytaert also stresses the importance of collaboration, centralized code management, and reclaiming control over infrastructure through effective automation strategies.