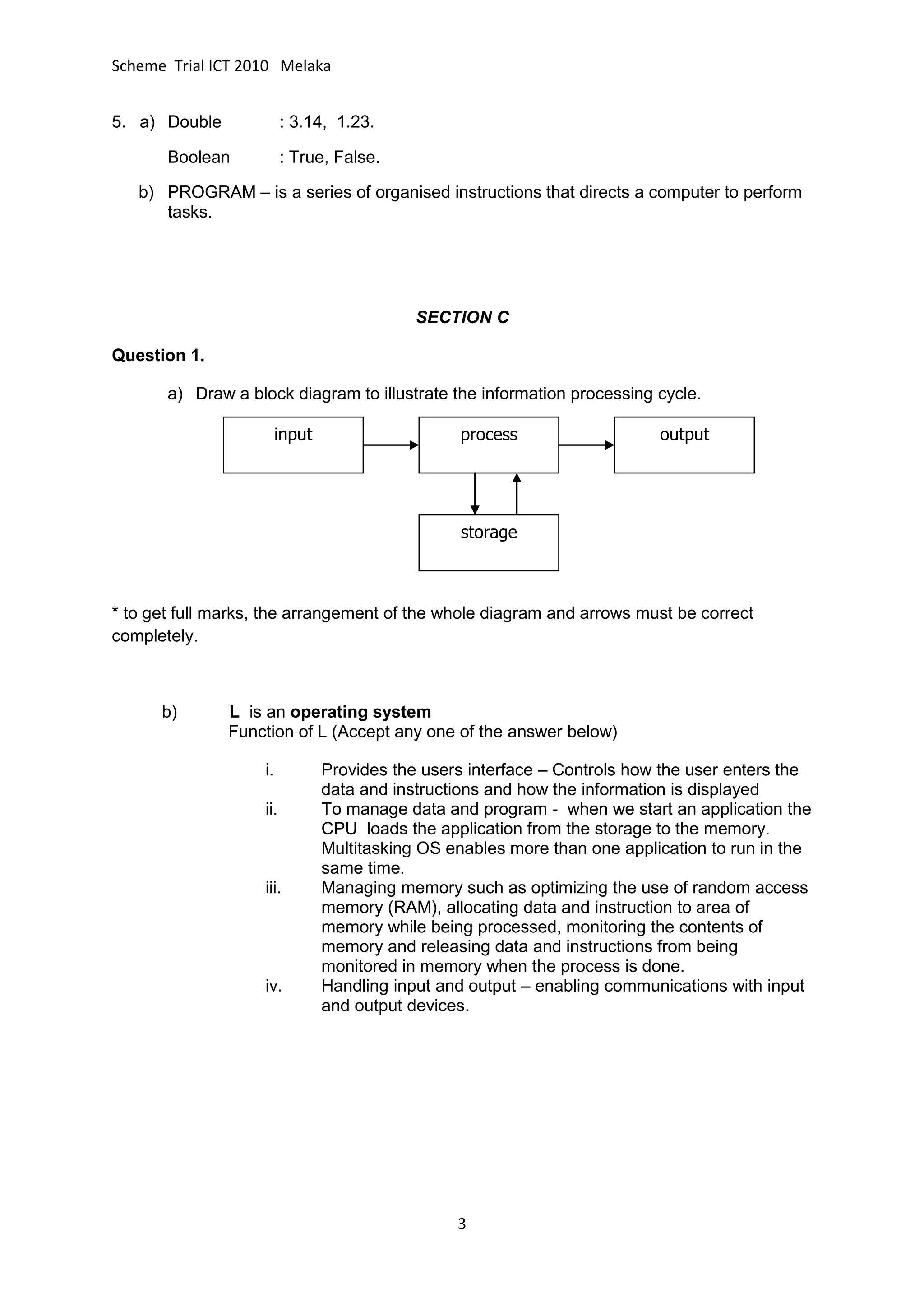
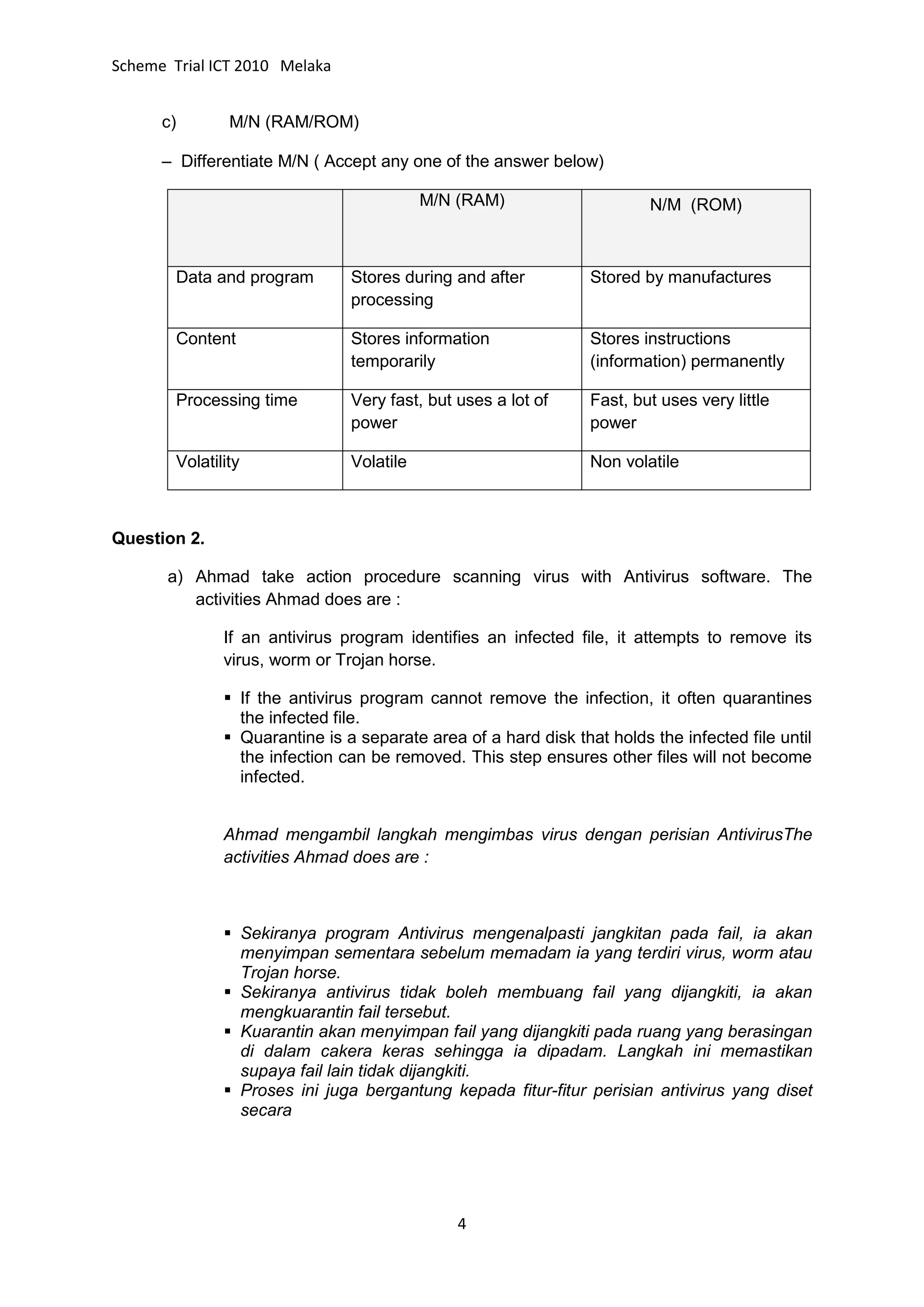
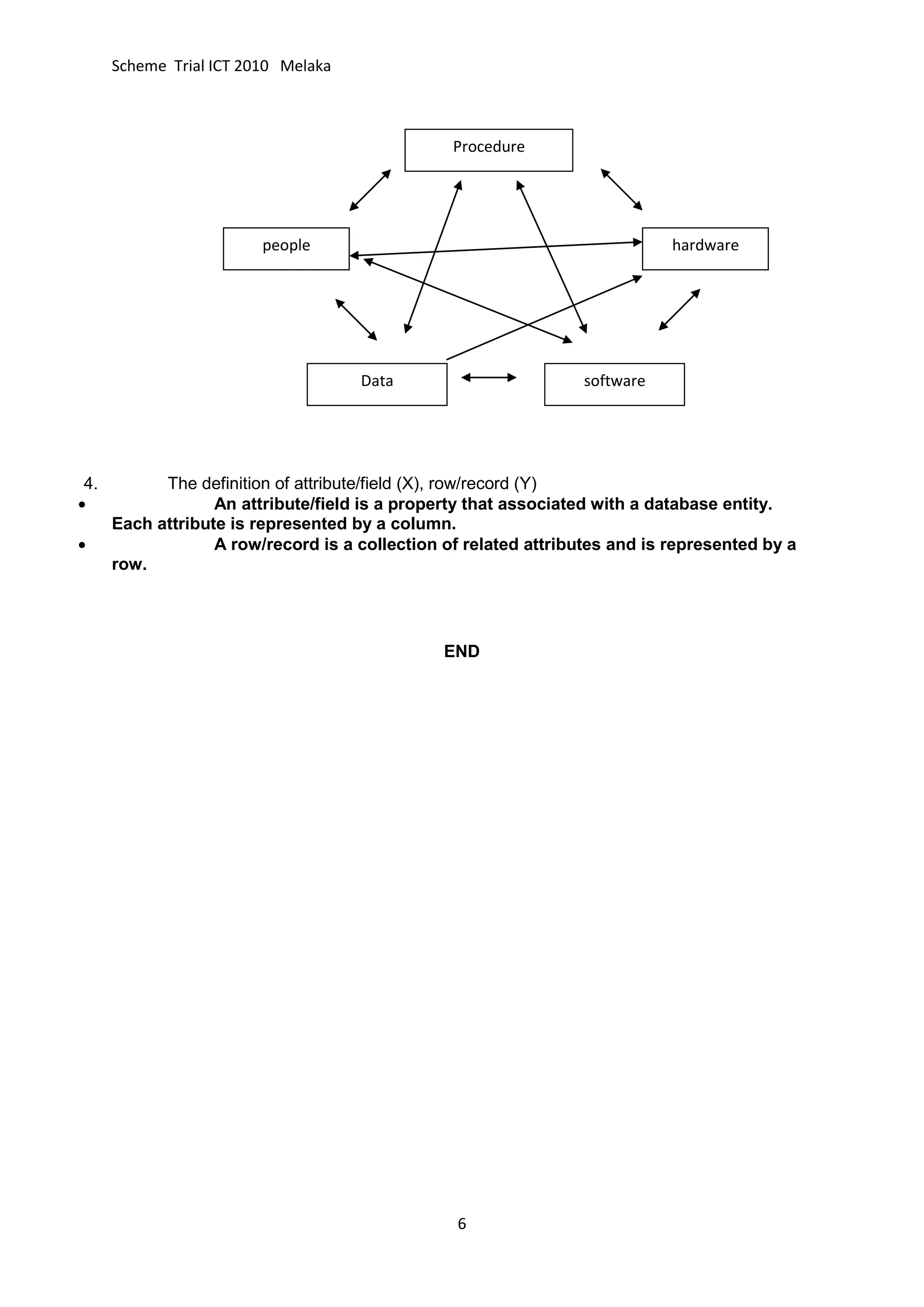
The document provides information about the SPM trial exam scheme for ICT in 2010 in Melaka, including sections A, B, and C. Section A contains multiple choice and short answer questions. Section B asks students to match terms with definitions and draw flowcharts. Section C requires students to describe the information processing cycle, the functions of an operating system, and the differences between RAM and ROM [END SUMMARY]