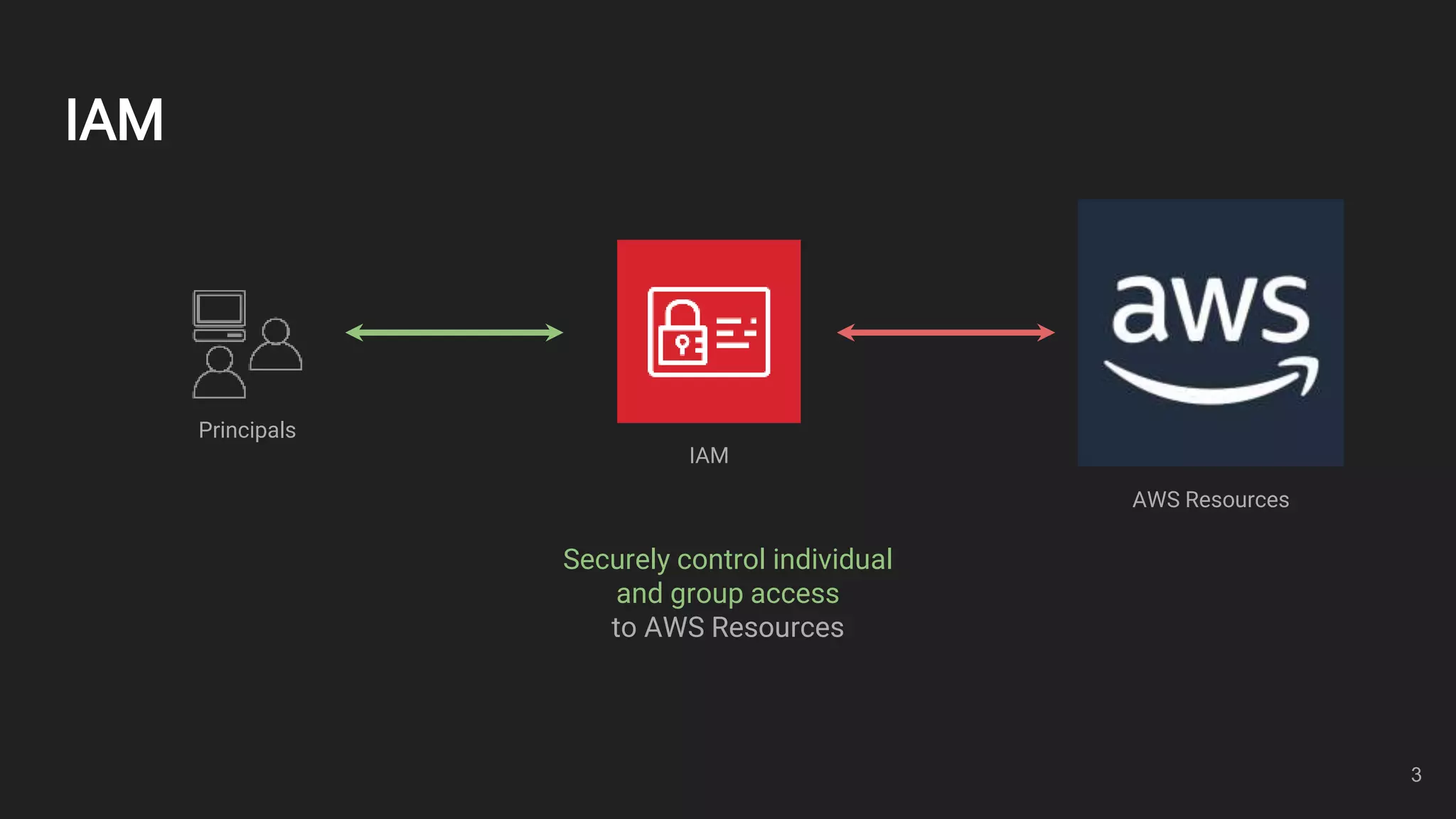
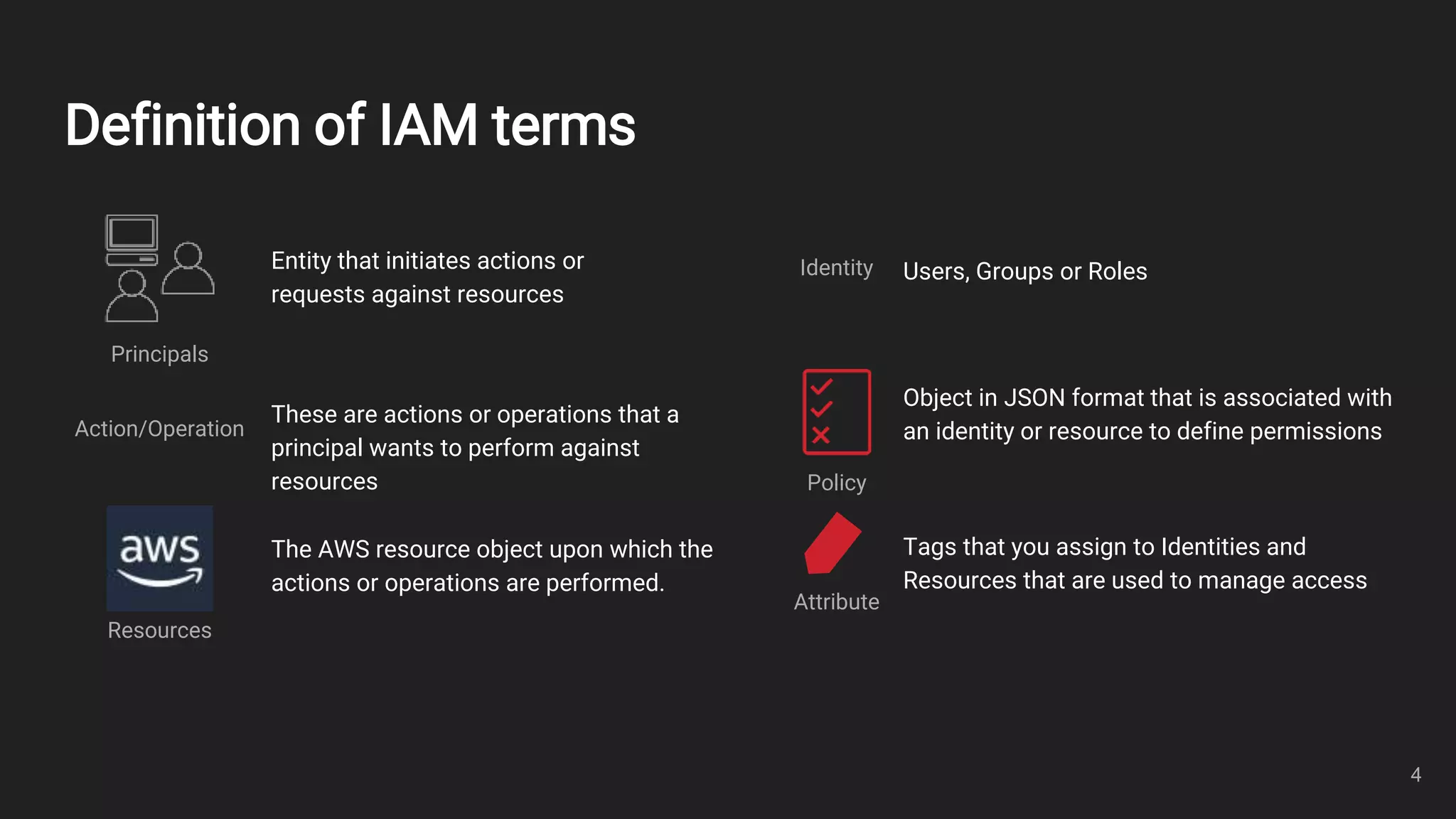
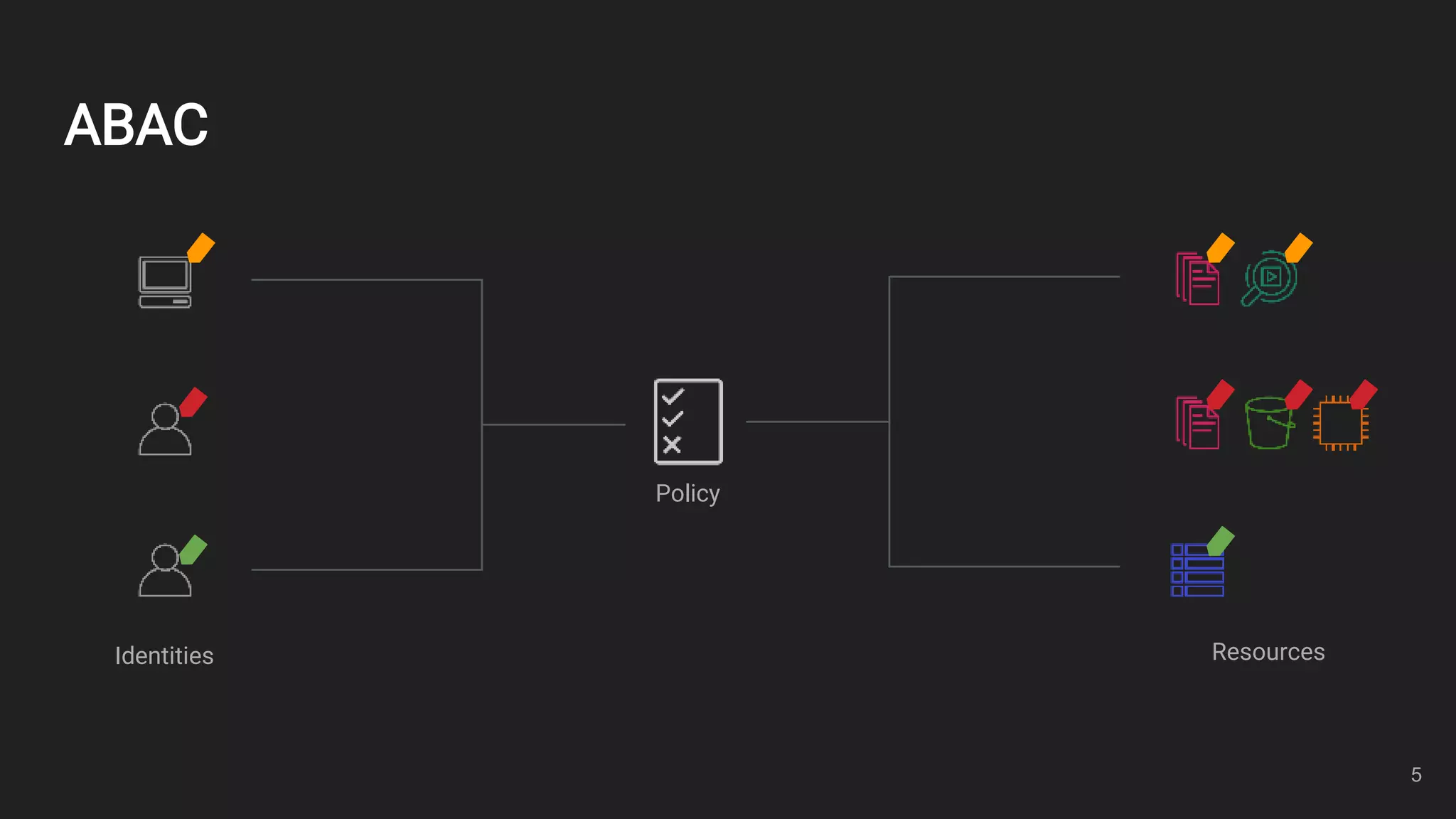
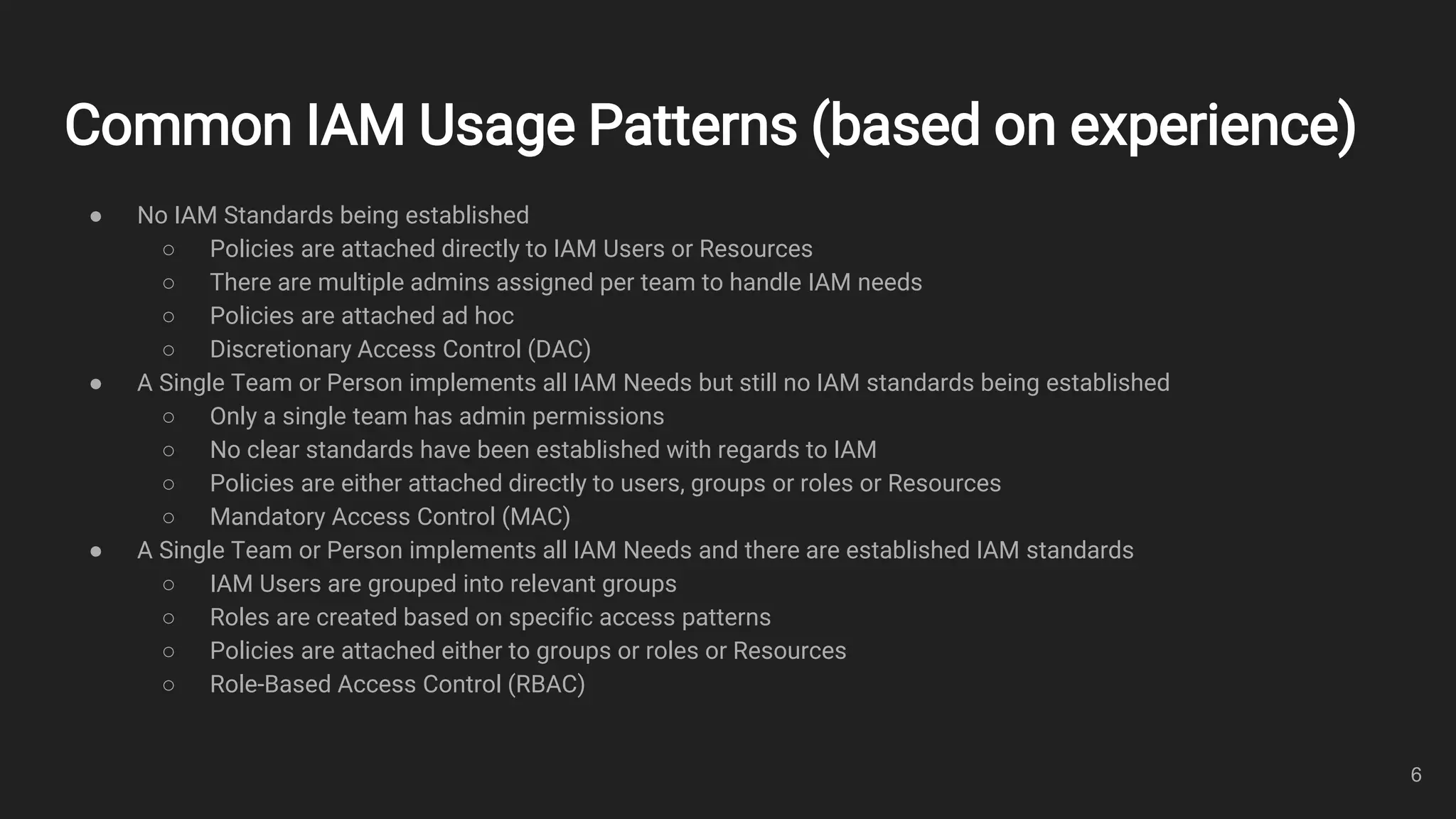
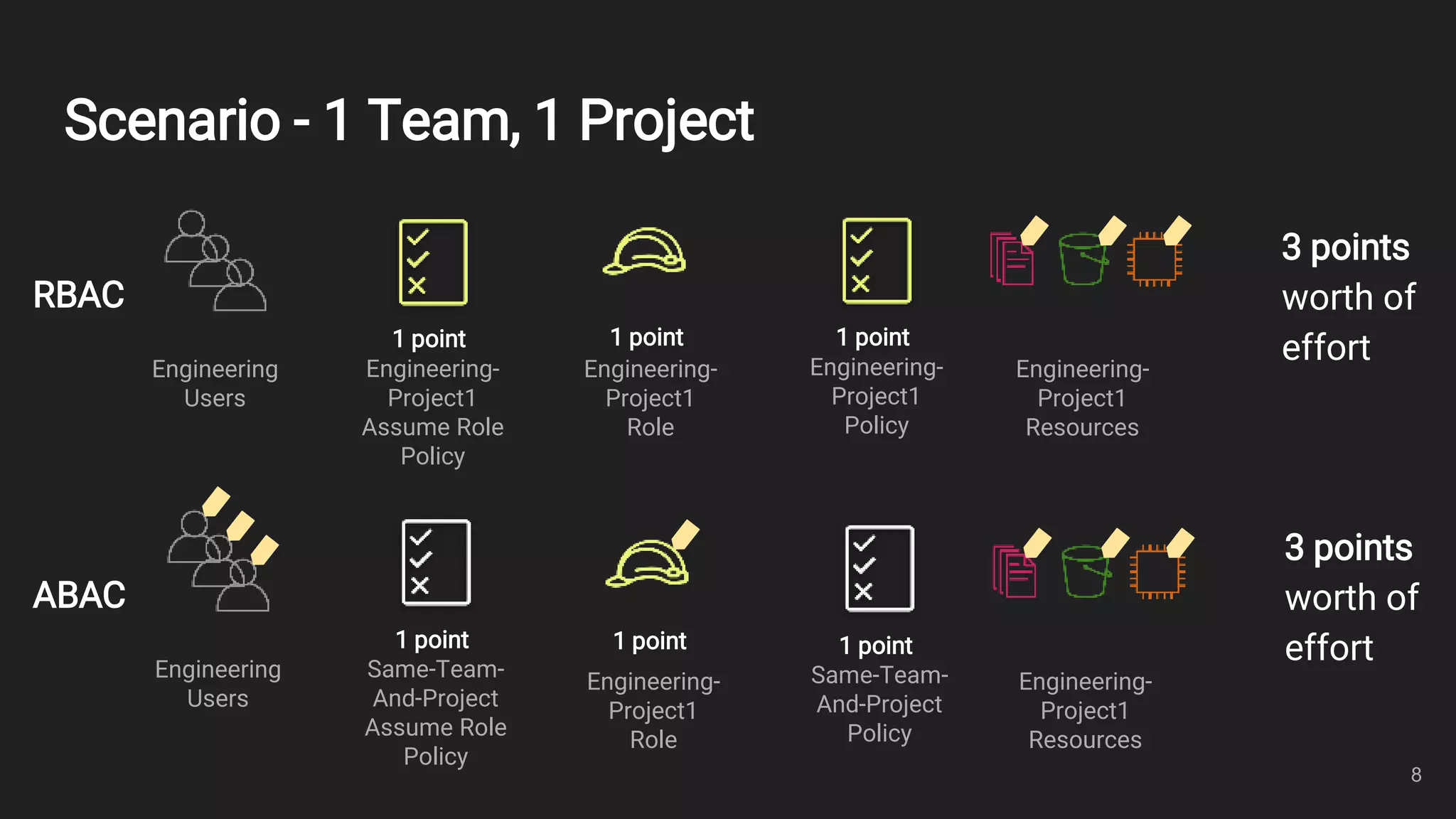
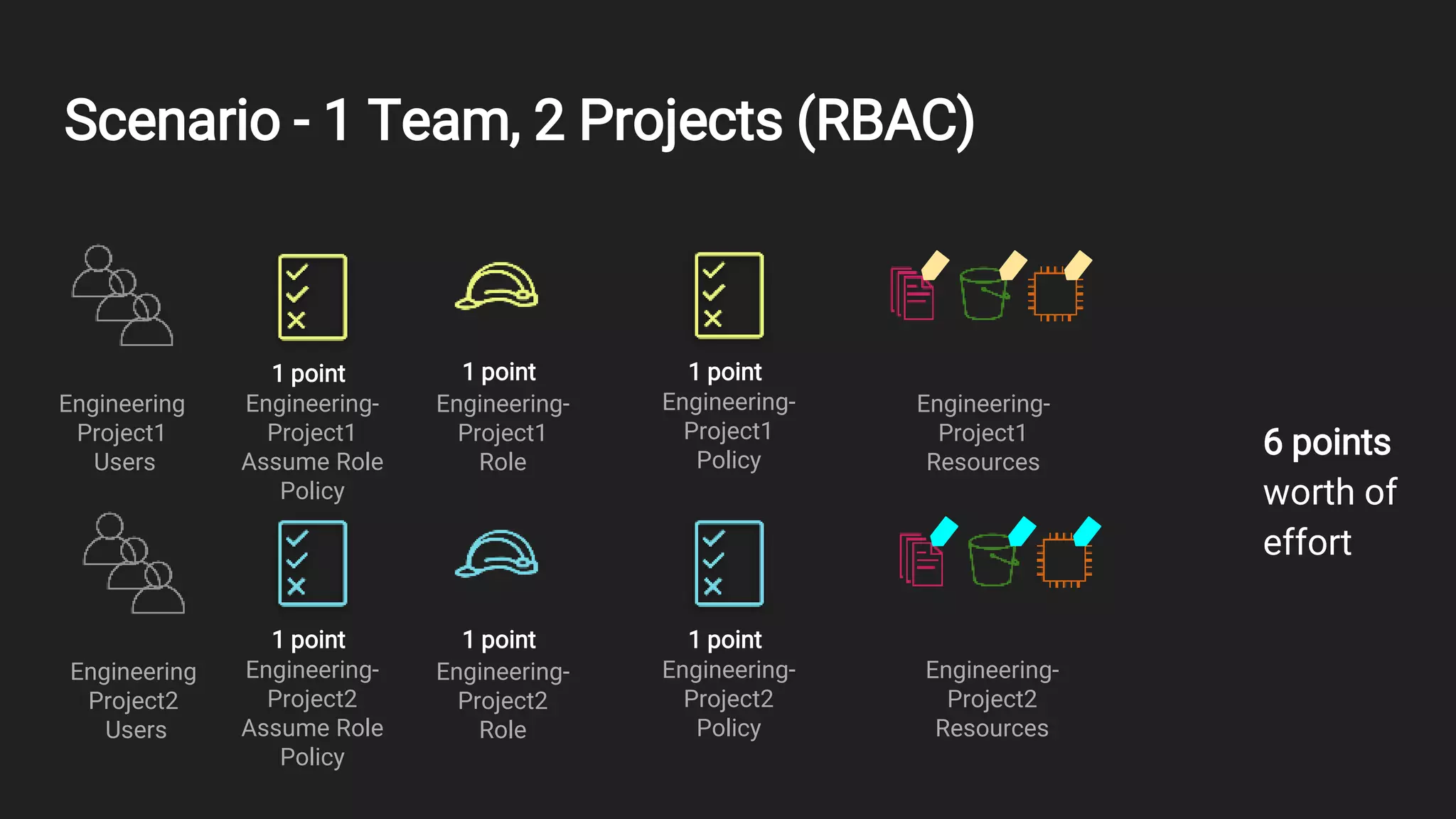
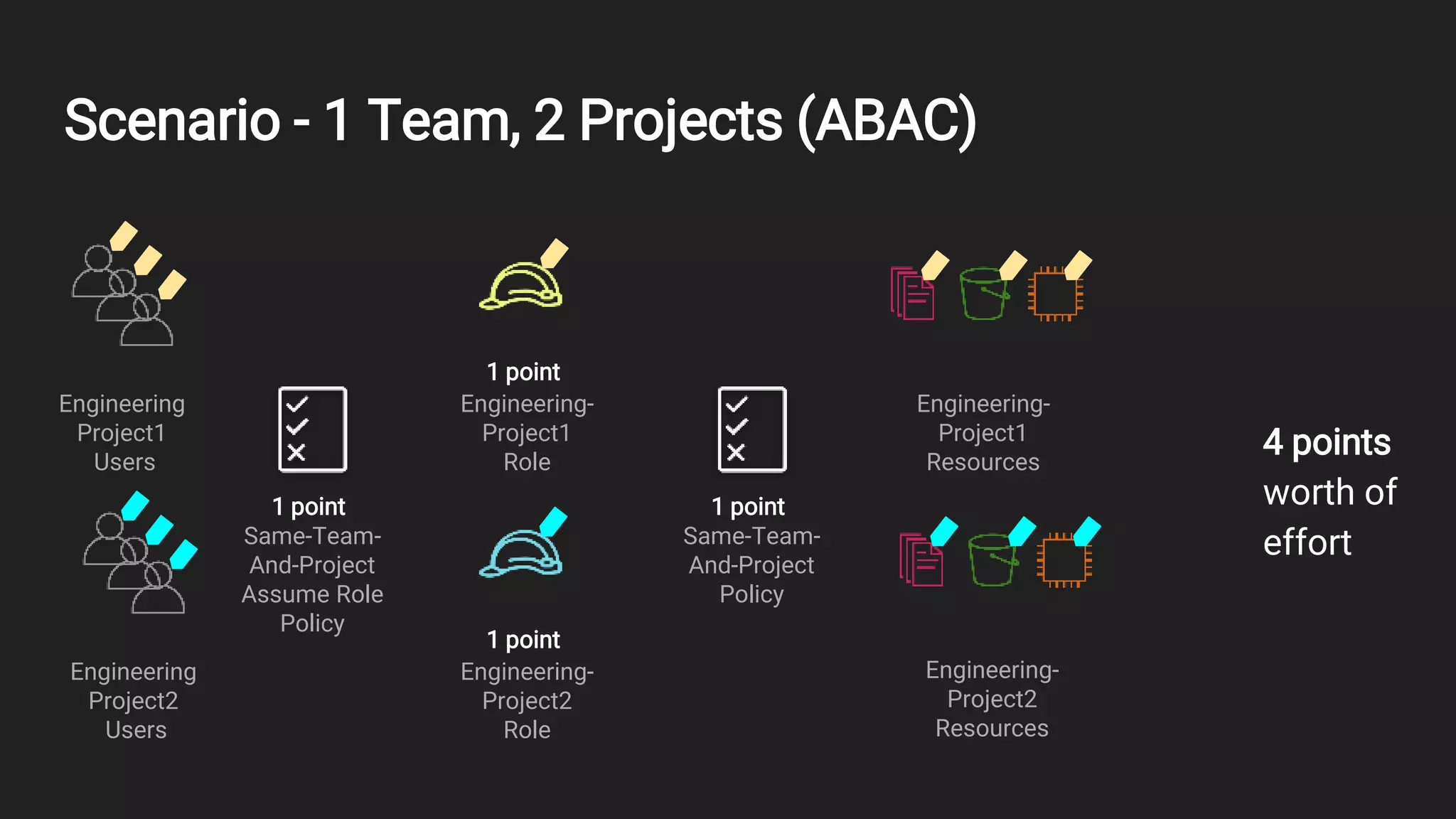
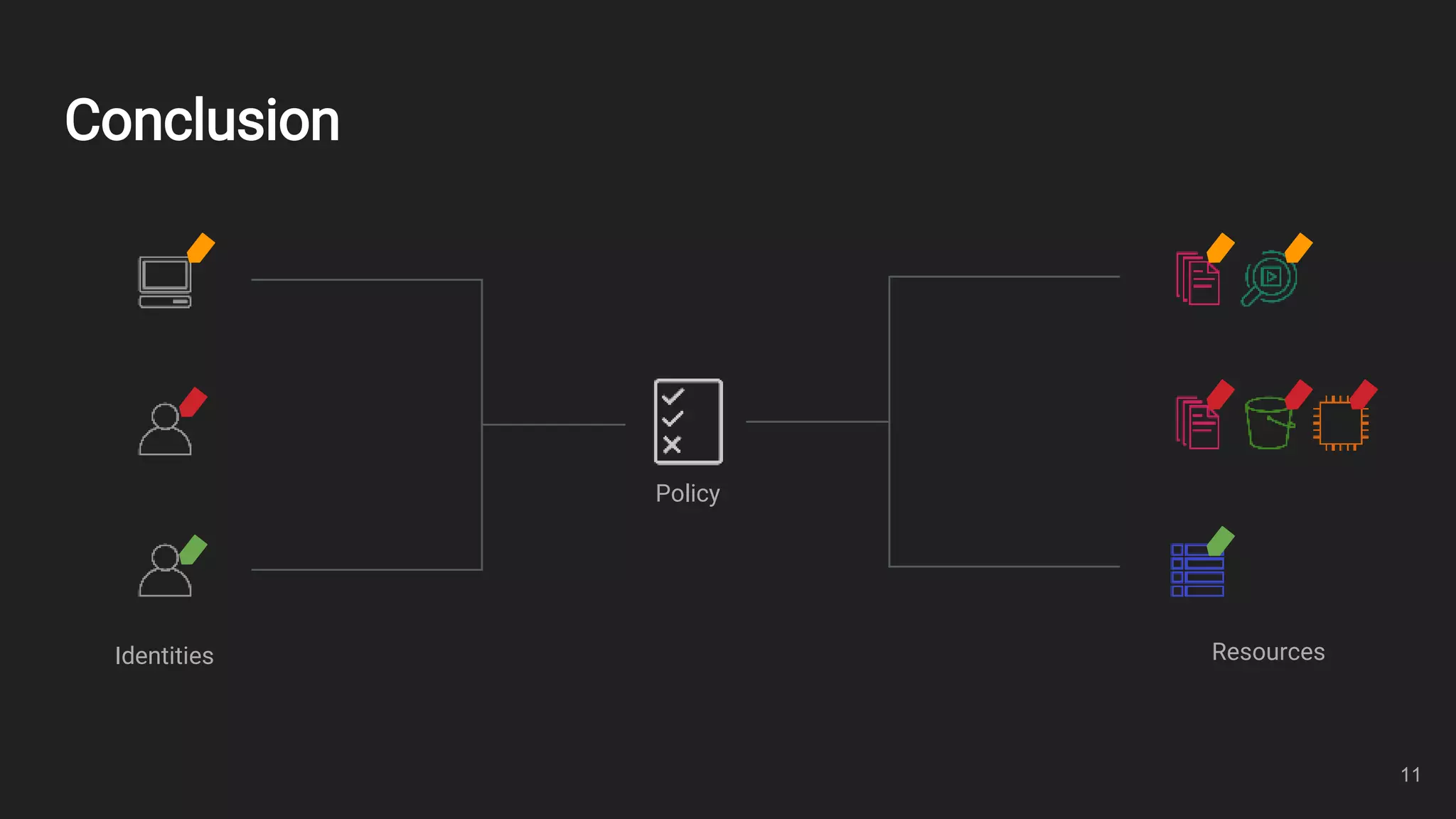
This document outlines an overview of identity and access management (IAM) with a focus on attribute-based access control (ABAC). It defines key IAM terms like principals, actions, resources, identities, and policies. It then provides examples of common IAM usage patterns and how ABAC compares to role-based access control (RBAC) in scenarios involving one team with one or two projects. Metrics for evaluating IAM solutions are proposed. In conclusion, the document emphasizes controlling access using identities, resources, and policies.