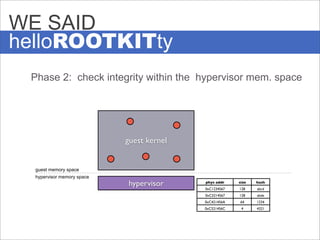
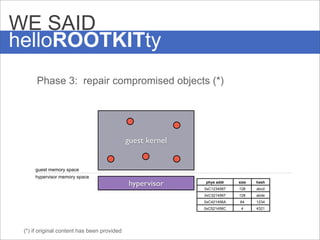
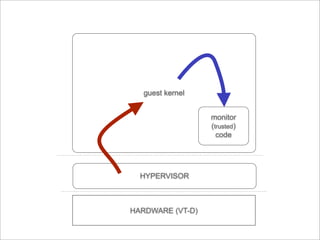
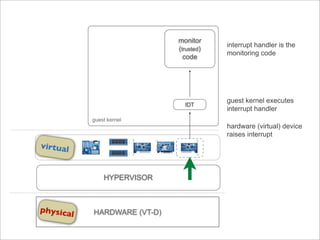
The document presents Hyperforce, a framework for enforcing the secure execution of security-critical code in virtual environments, particularly aimed at mitigating rootkits. It discusses the economic impact of malware and outlines performance metrics showing that Hyperforce allows for trusted monitoring with minimal performance loss. The conclusion suggests the potential for broader applications of this framework to enhance system security further.