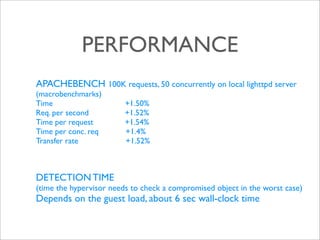
This document proposes a lightweight framework called helloRootkitty that enforces kernel integrity using virtualization. It traps events like control register changes to check the integrity of critical kernel objects. When it detects compromised objects, it can repair them if the original values are known. Evaluation on BitVisor showed it introduces minimal overhead while reducing the attack surface for rootkits compared to traditional approaches.