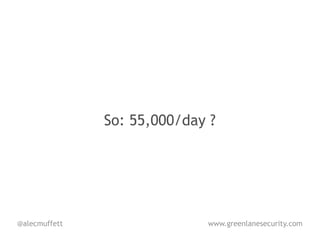The document discusses the concept of "cybersecurity" and argues that it is an unsuitable model for describing challenges related to information and network security. It notes that the word "cybersecurity" implies a virtual space or domain that functions similarly to the real world, but that this is an inaccurate analogy. Several examples are given to illustrate how aspects like theft work differently in a digital context versus the physical world. The thesis being defended is that the "cybersecurity" model tends to promote misguided strategies, excessive costs, and illiberal policies if not supplemented with other perspectives.




































































































































![http://goo.gl/MXCsG - computerworld
The cost of cybercrime to the global
economy is estimated at $1 trillion
[US General Keith] Alexander stated and
malware is being introduced at a rate of
55,000 pieces per day,
or one per second.
@alecmuffett www.greenlanesecurity.com](https://image.slidesharecdn.com/wcir-2-120307035554-phpapp02/85/How-To-Think-Clearly-About-Cybersecurity-v2-140-320.jpg)

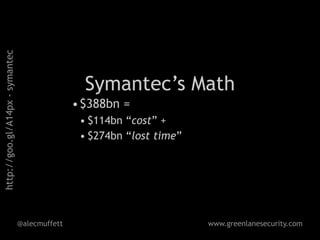









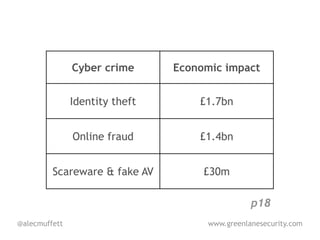
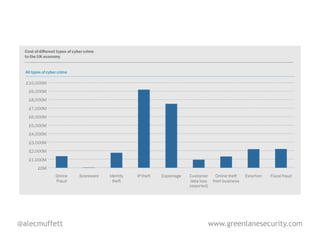
![Overall, we estimate the most likely impact
[of online theft is] £1.3bn per annum, with the best
and worst case estimates £1.0bn and
£2.7bn respectively. p21
@alecmuffett www.greenlanesecurity.com](https://image.slidesharecdn.com/wcir-2-120307035554-phpapp02/85/How-To-Think-Clearly-About-Cybersecurity-v2-152-320.jpg)