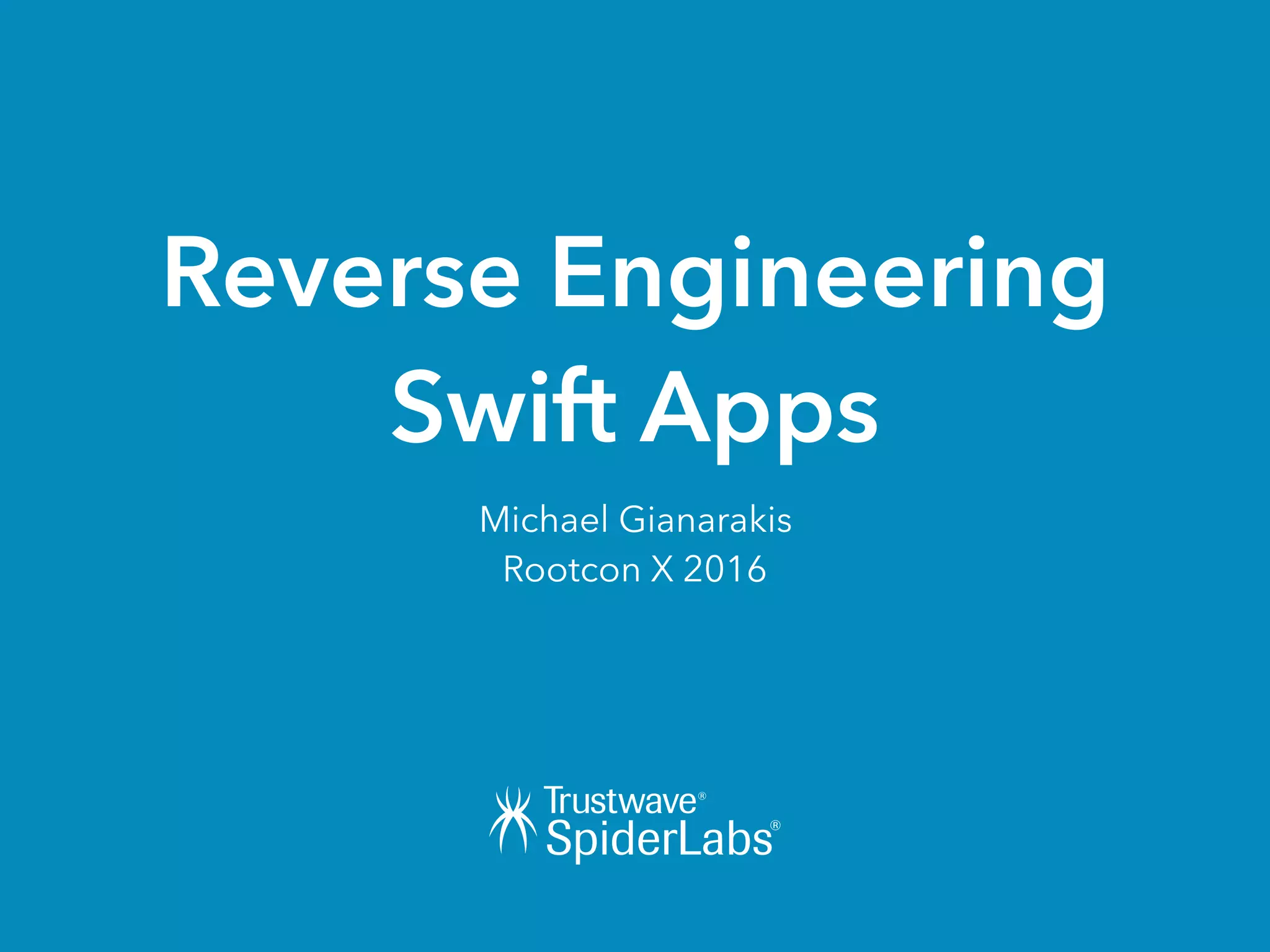
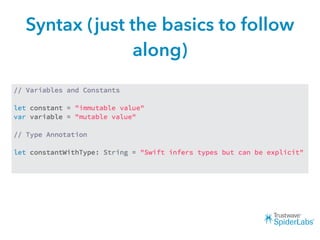
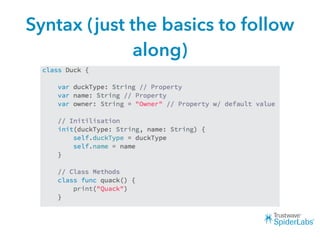
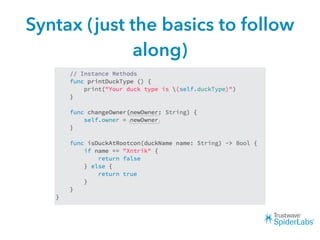
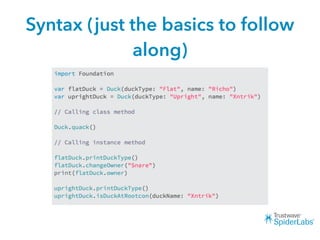
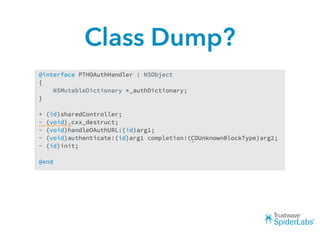
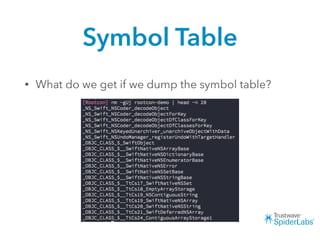
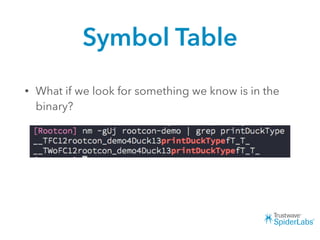
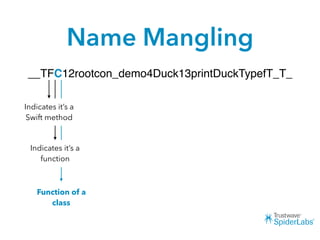
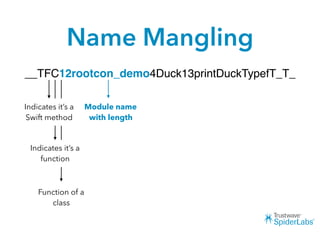
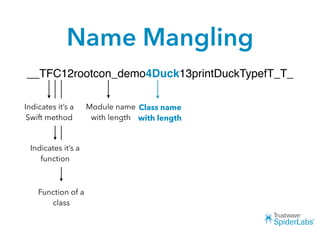
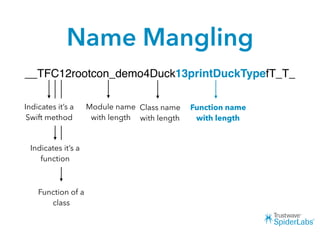
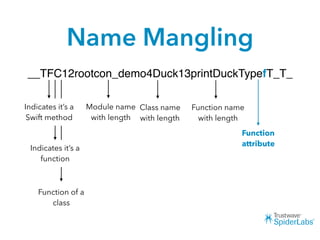
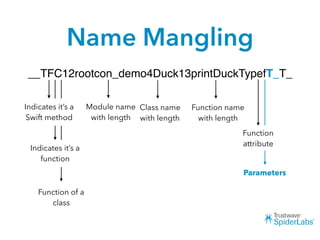
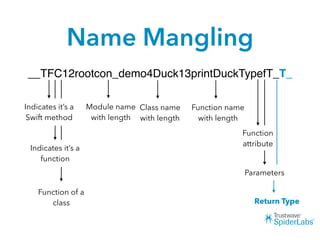
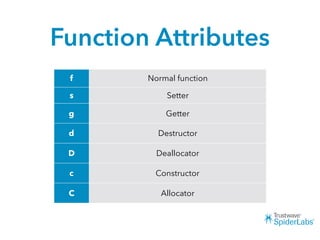
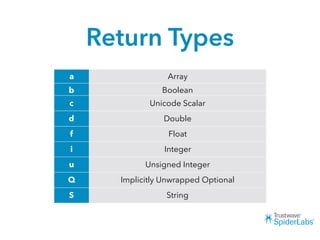
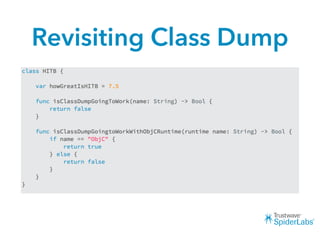
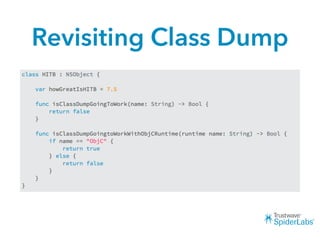
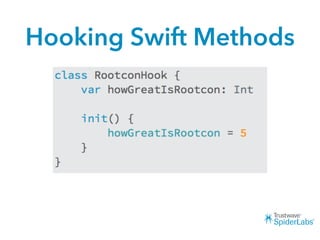
The document discusses challenges and techniques for reverse engineering Swift apps. It notes that class dump utilities do not work on Swift binaries due to name mangling. However, the symbol table, nm tool, and swift-demangle utility can be used to retrieve function signatures. A hacked script approximates class dump output. While stripping symbols makes analysis harder, Objective-C compatibility eases the process. Other tools like classdump-dyld and disassemblers also help. Function hooking is possible but setter methods require calling from top-level code due to inlining.