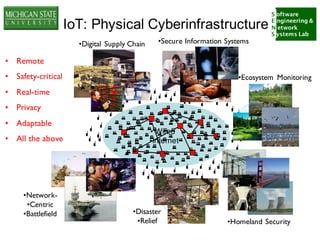
The document discusses the relationship between cybersecurity and safety in the context of ultra-large-scale systems and the Internet of Things (IoT). It highlights key cybersecurity challenges such as prevention, detection, and mitigation while emphasizing the need for multidisciplinary strategies to effectively address these issues. Additionally, it explores the complexities of interconnected systems and the importance of collaboration across various fields.