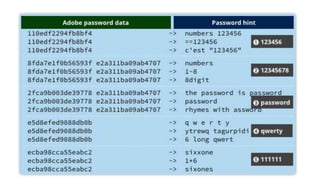
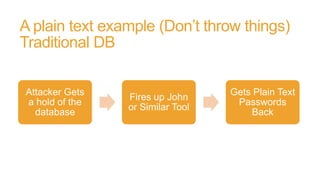
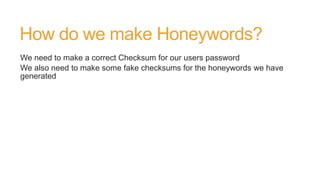
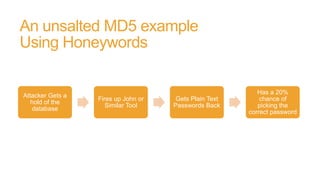
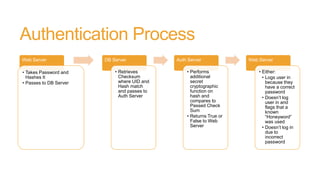
The document discusses honeywords, which are fake passwords that are inserted into a user database along with real user passwords. This allows systems to detect if a password database is stolen by monitoring for logins using the fake honeyword passwords. The document outlines how honeywords can be generated to look realistic, how authentication would work to prevent honeyword logins, and the benefits of using honeywords such as enabling detection of password theft. However, it notes that honeywords do not prevent a database compromise or replace the need for strong password policies and storage mechanisms.