Embed presentation
Download to read offline




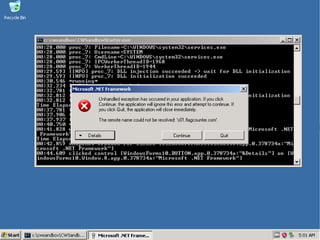
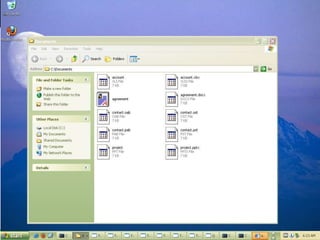
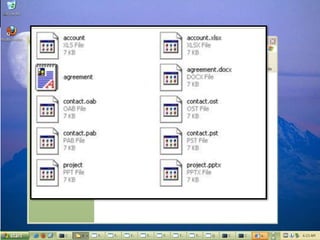
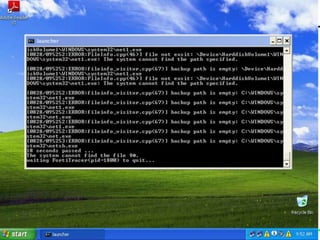
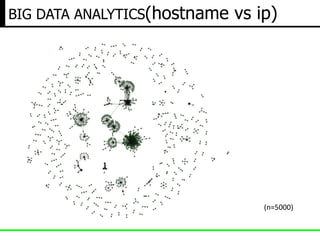
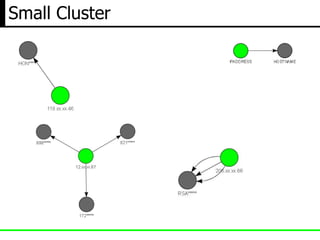
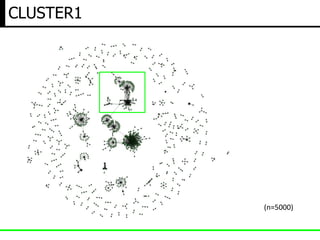
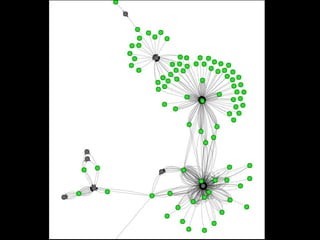
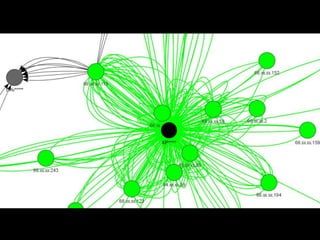
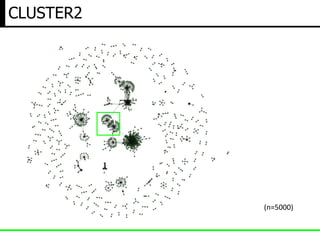
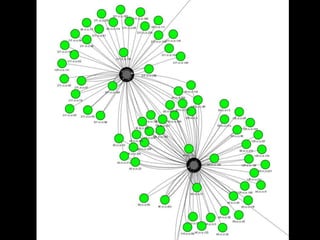
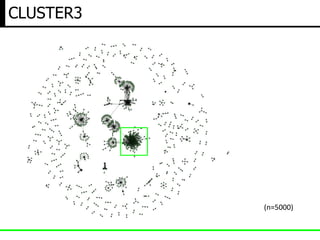
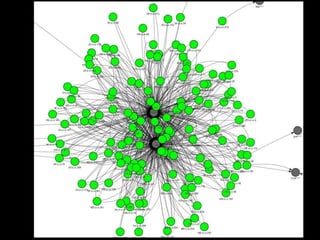
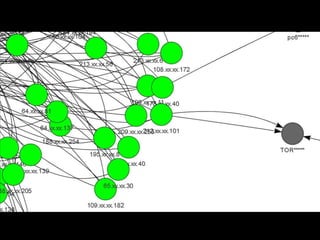

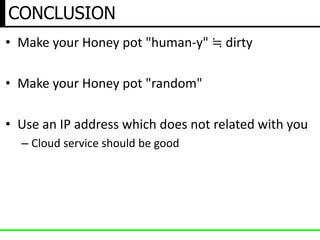

The document discusses insights from a security researcher regarding honeypots and malware analysis systems from the attacker's perspective. It emphasizes the importance of designing honeypots to appear more realistic and random to effectively trick attackers. The researcher suggests using unrelated IP addresses and cloud services for better concealment.





















