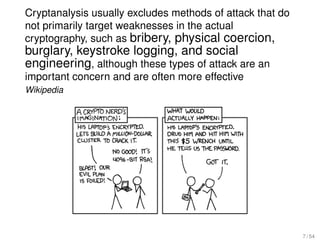
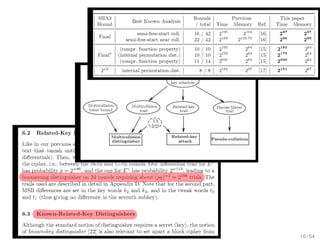
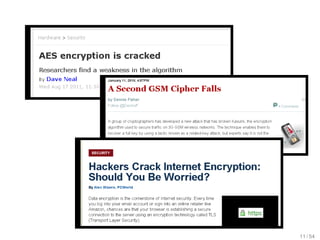
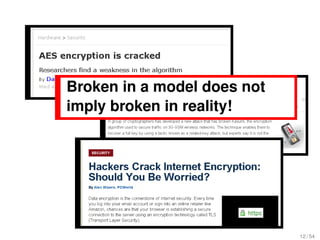
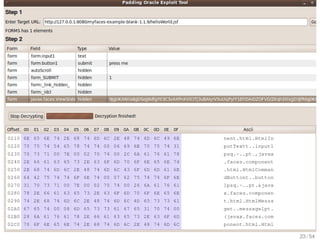
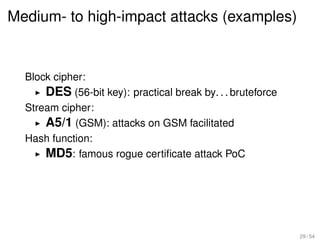
The document analyzes the relevance and connection of cryptanalysis to practical security, emphasizing that models and assumptions in cryptanalysis may not reflect real-world vulnerabilities. It discusses the shift from theoretical attacks to practical methods such as physical and side-channel attacks that often bypass cryptographic measures altogether. Ultimately, it highlights that while algorithmic threats exist, weak implementations pose a greater risk to security.