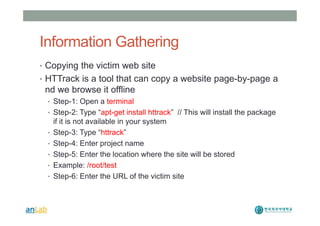
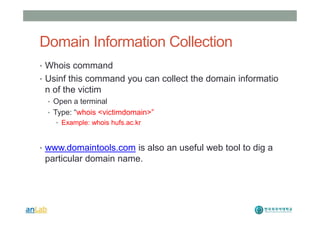
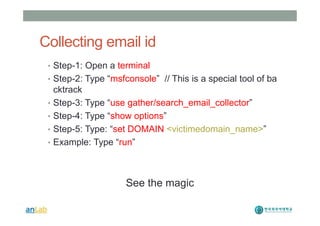
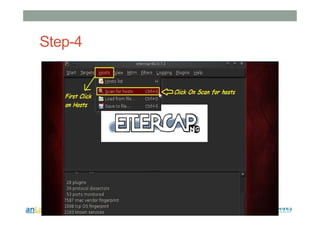
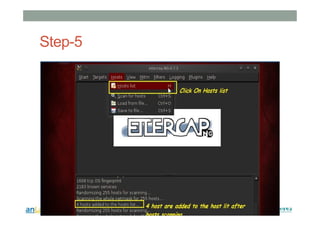
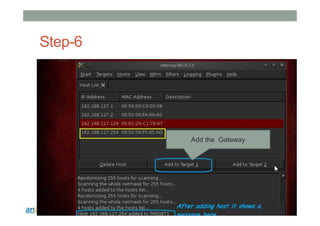
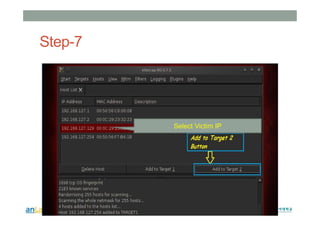
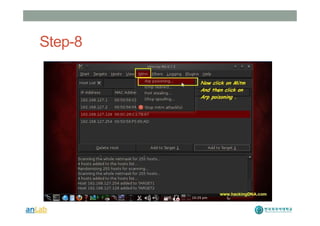
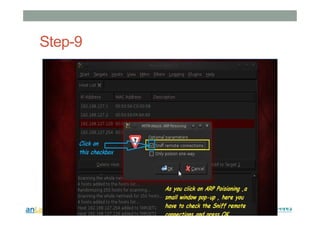
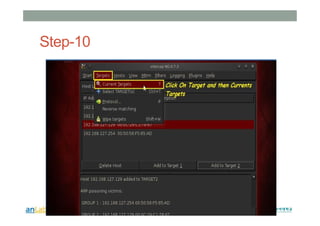
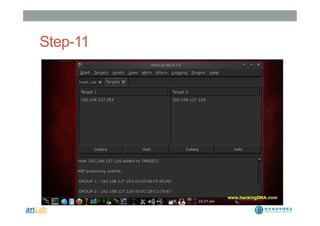
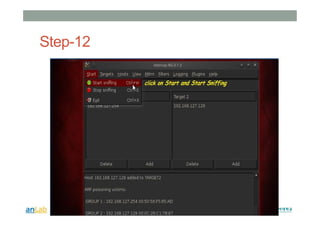
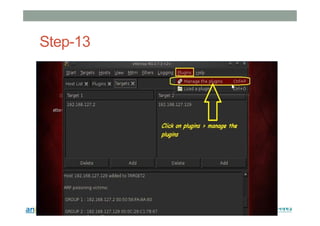
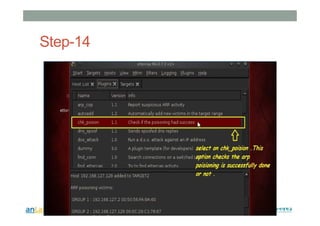
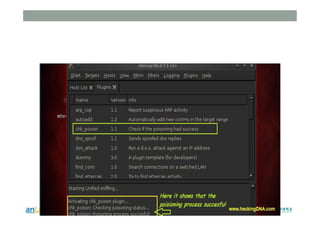
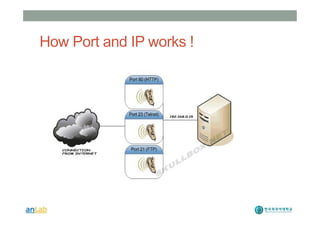
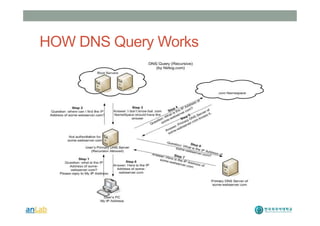
This document provides instructions for performing various tasks in Backtrack 5 such as gathering information from websites and domains, network scanning, packet sniffing, and man-in-the-middle attacks. It begins with safety cautions and instructions for configuring network settings in Backtrack. It then explains how to use tools like apt-get, HTTrack, Whois, Zenmap, Wireshark, and Ettercap to collect information and conduct attacks. The document emphasizes the educational purpose of these techniques and cautions the reader not to use them for harmful purposes.