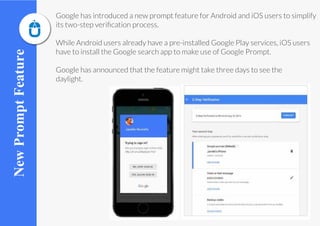
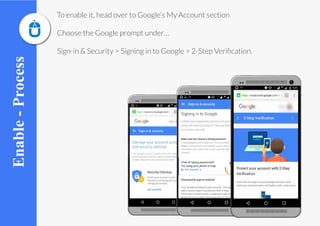
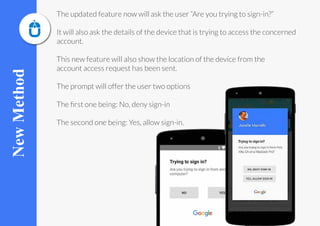
Google is introducing a new prompt feature to simplify its two-step verification process for sign-ins on iOS and Android. The new feature will ask users if they are trying to sign in and show device details and location when an account access request is made. Users will have the option to allow or deny the sign in. The update makes it easier to manage privacy and security settings within a Google account.