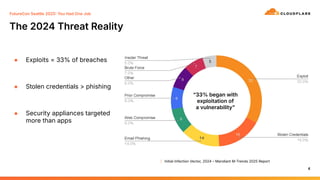
In 2024, attackers didn’t need phishing emails to compromise enterprises — they just waited for the latest zero-day in your firewall to be weaponized. Mandiant’s M-Trends 2025 report reveals that most intrusions now start with exploited vulnerabilities in edge security devices. Meanwhile, credentials are stolen by malware faster than MFA can save you, and security vendors themselves are being turned into initial access brokers — unintentionally.
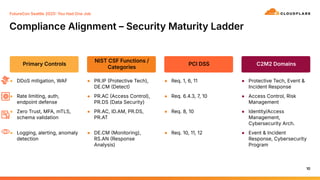
This talk is a call to get back to basics. We’ll walk through the top 10 ways organizations are still failing at foundational security, and provide a clear, no-nonsense roadmap for how to fix it. Aligned to NIST, PCI DSS, and C2M2 frameworks, this approach avoids complexity, avoids buzzwords, and avoids blaming users. You don’t need another vendor — you need to configure what you already have properly, document it, and follow through. Because at the end of the day, no one wants to explain to leadership how your “security box” was the reason you got owned.