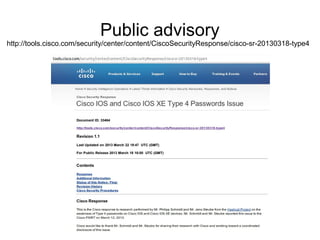
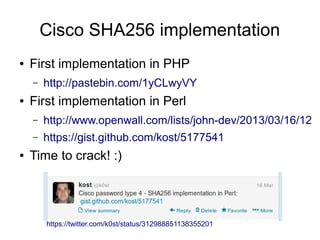
Vlatko Kosturjak discusses weaknesses found in a Cisco SHA256 password hash implementation. He describes how he was able to determine the hash was using an insecure custom charset and no salt or iterations. This allowed him to crack the hash using rainbow tables. He created tools to convert Cisco configuration files to the John the Ripper format and cracked multiple passwords. His recommendations include implementing stronger cryptography, avoiding password reuse, and working with security researchers to improve implementations.



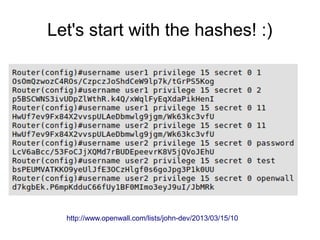








![cisco2john.pl
multiple configurations
$ ls *conf
127.0.0.1-startup-config
127.0.0.1-running-config
[..]
192.168.1.1-startup-config
192.168.1.1-running-config
$ cat *.conf | ./cisco2john.pl >cisco.in 2>cisco.seed
$ ./john -wo:cisco.seed -rules cisco.in
https://github.com/magnumripper/JohnTheRipper/blob/unstable-jumbo/run/cisco2john.pl](https://image.slidesharecdn.com/fsec-2013-crypto-implementations-weaknesses-130922063744-phpapp02/85/Cryptography-implementation-weaknesses-based-on-true-story-15-320.jpg)