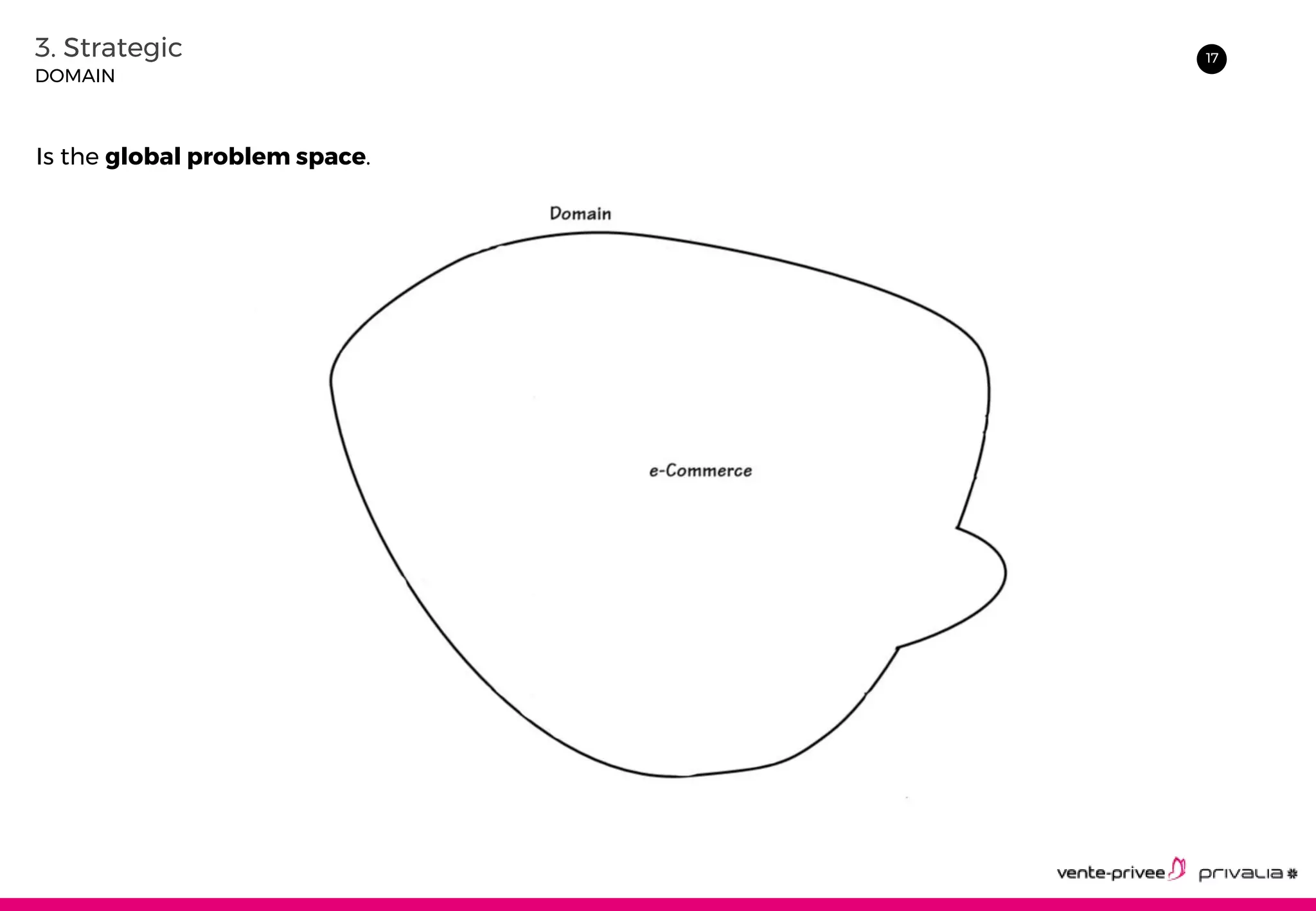
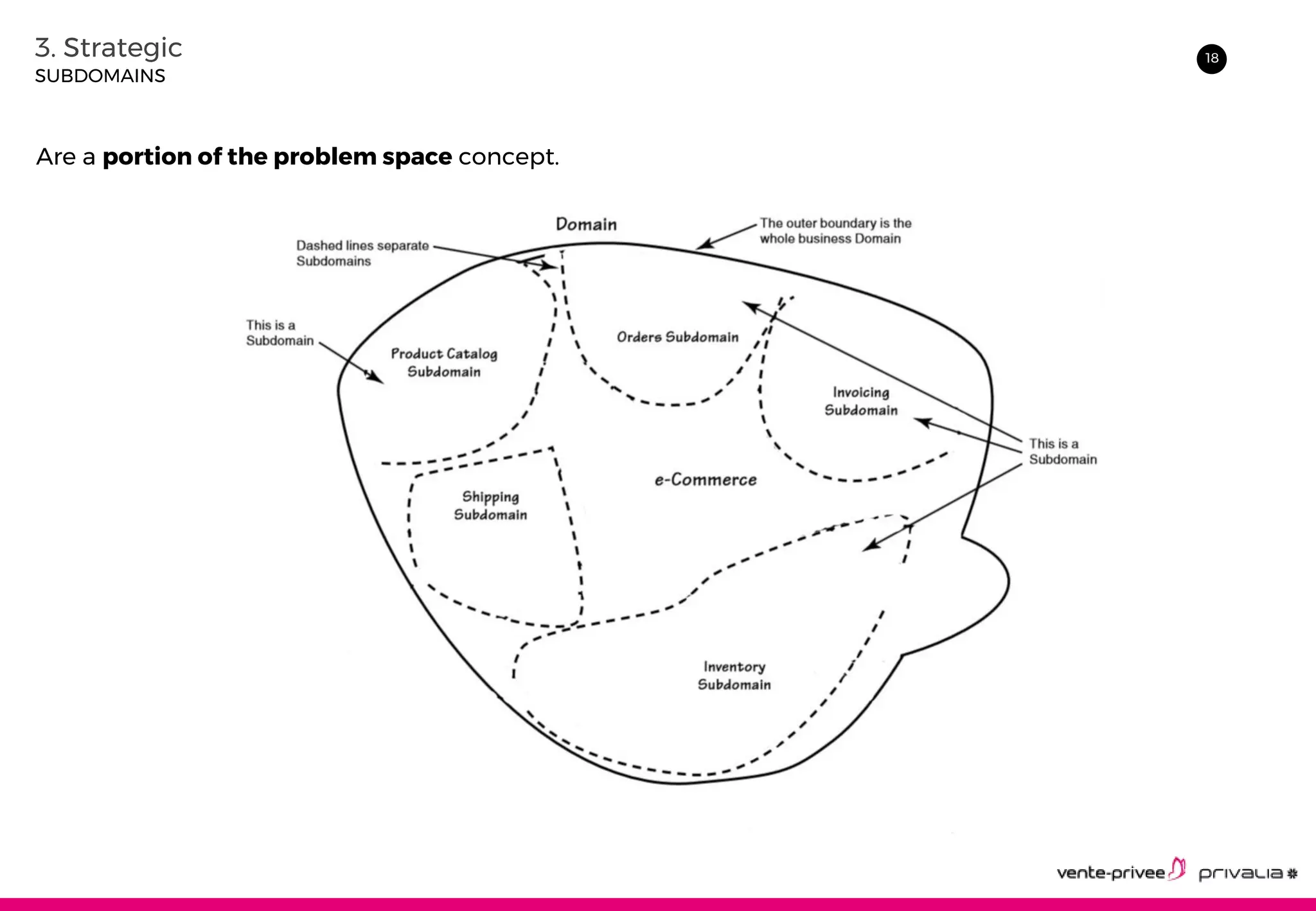
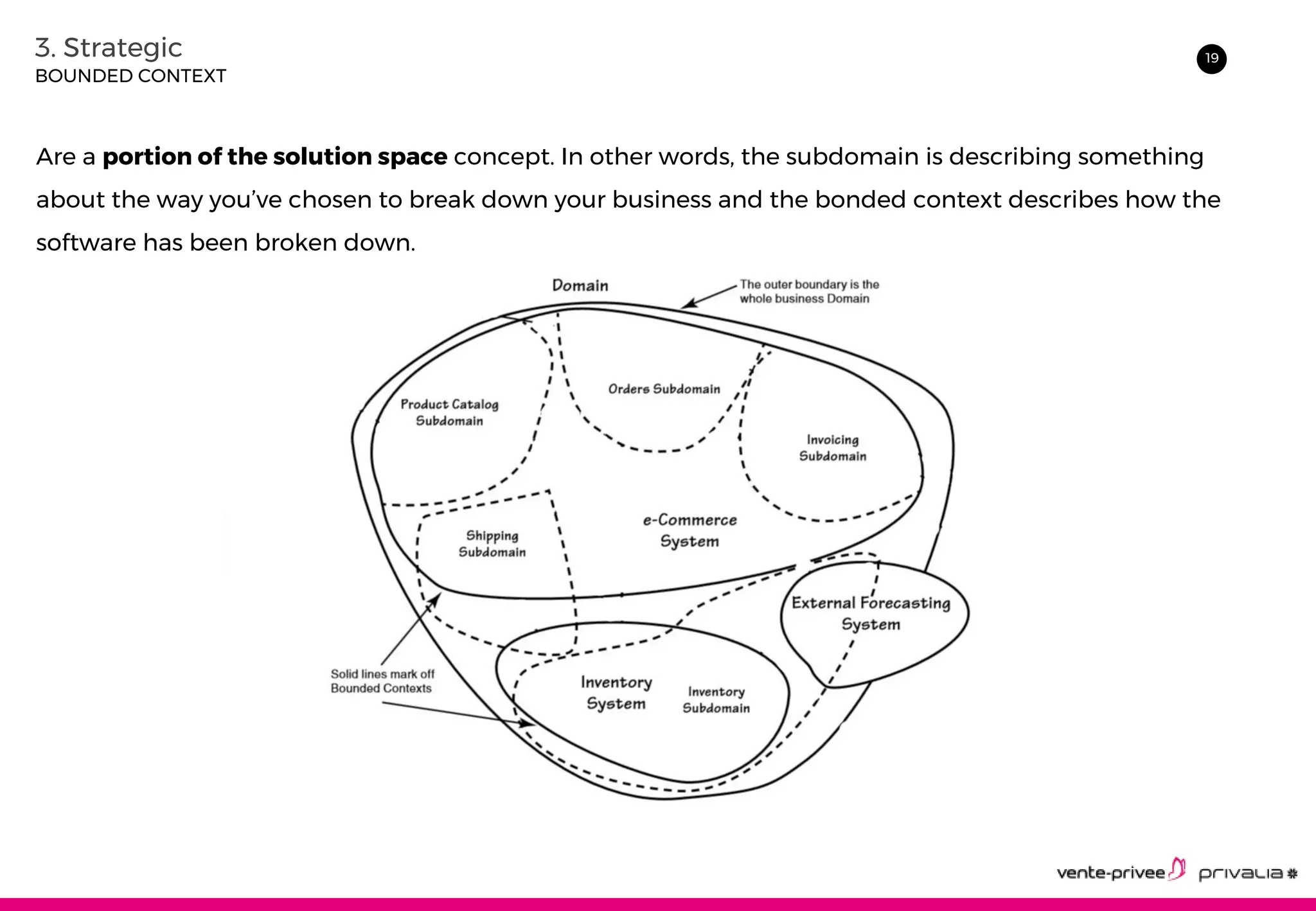
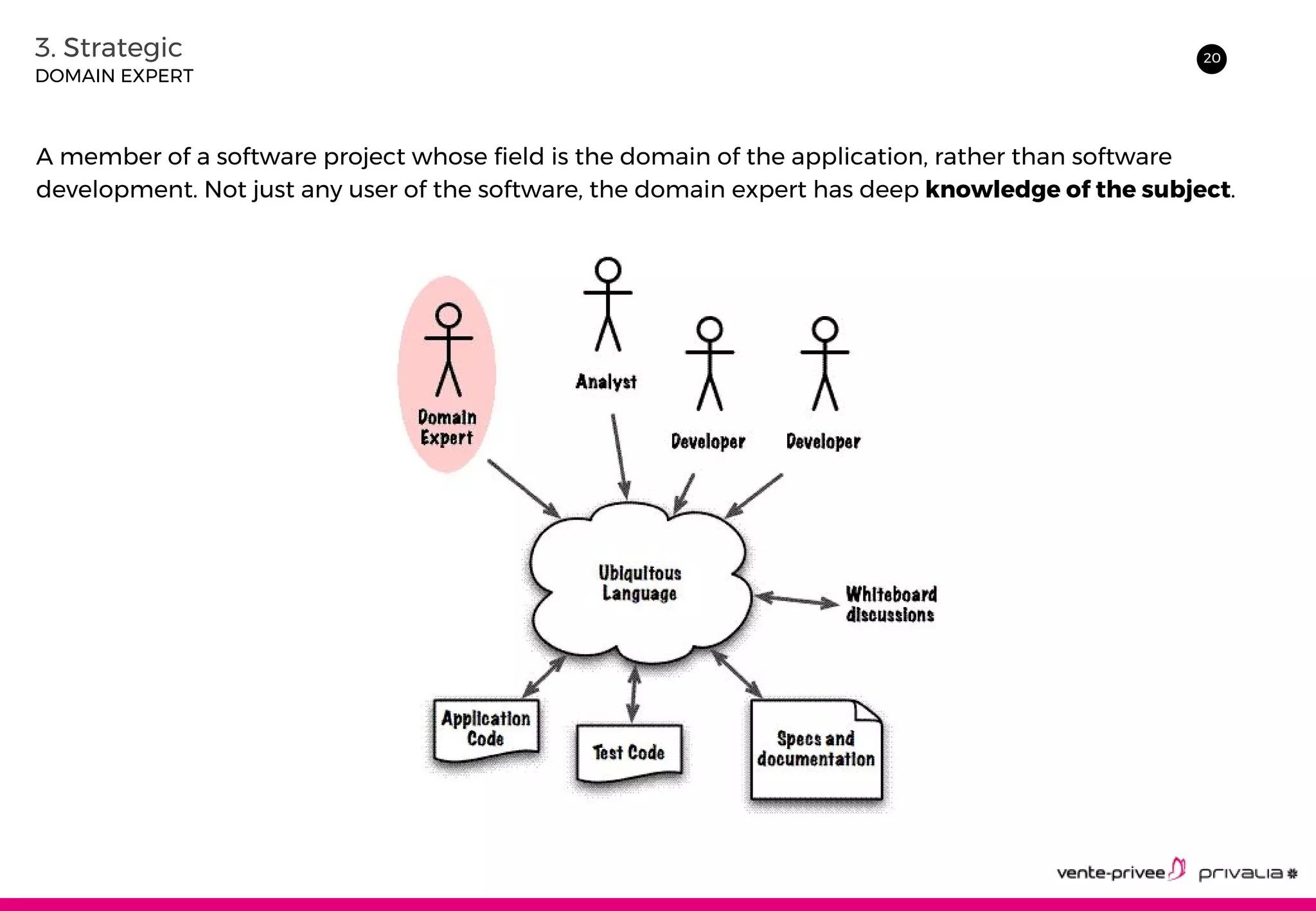
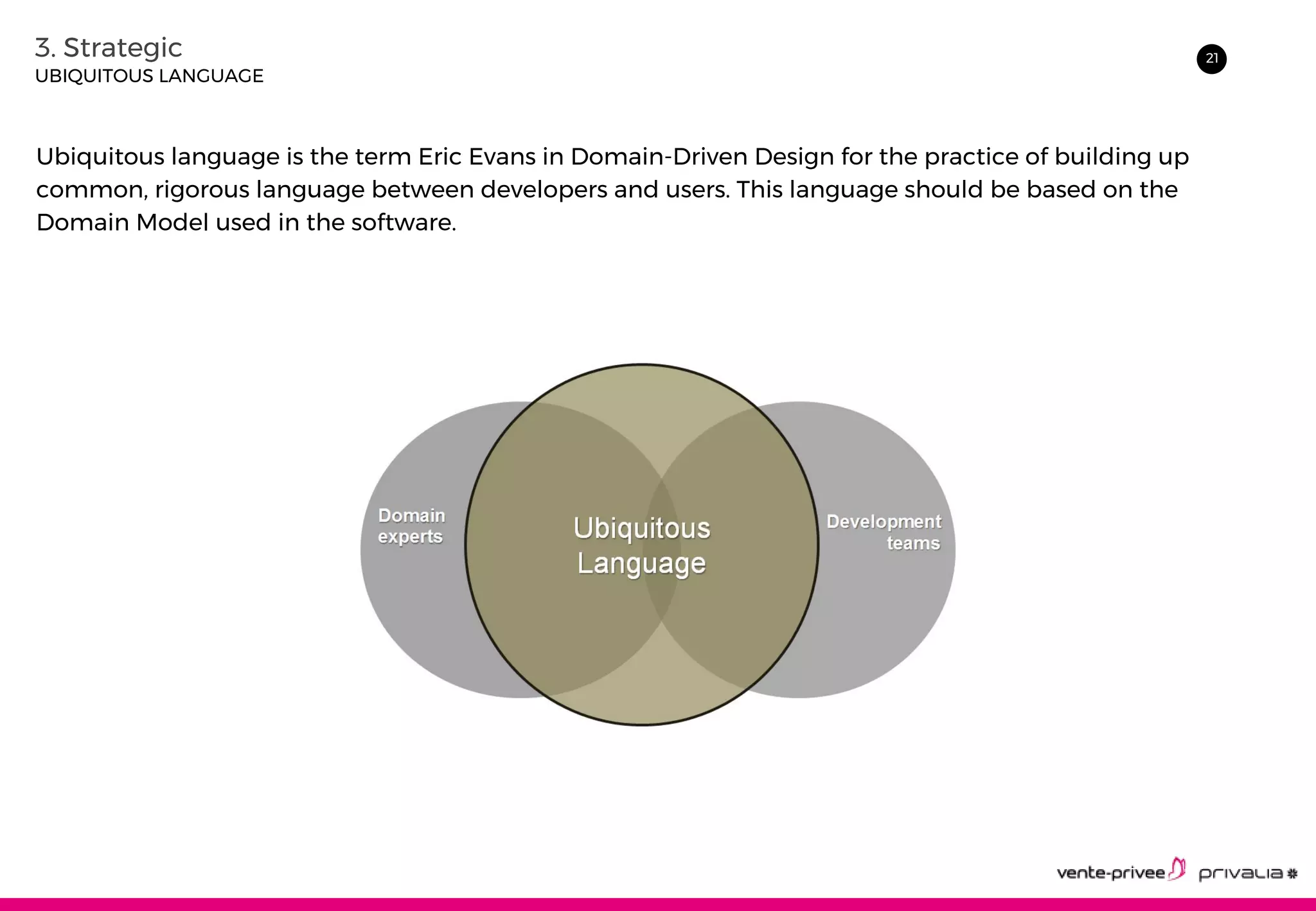
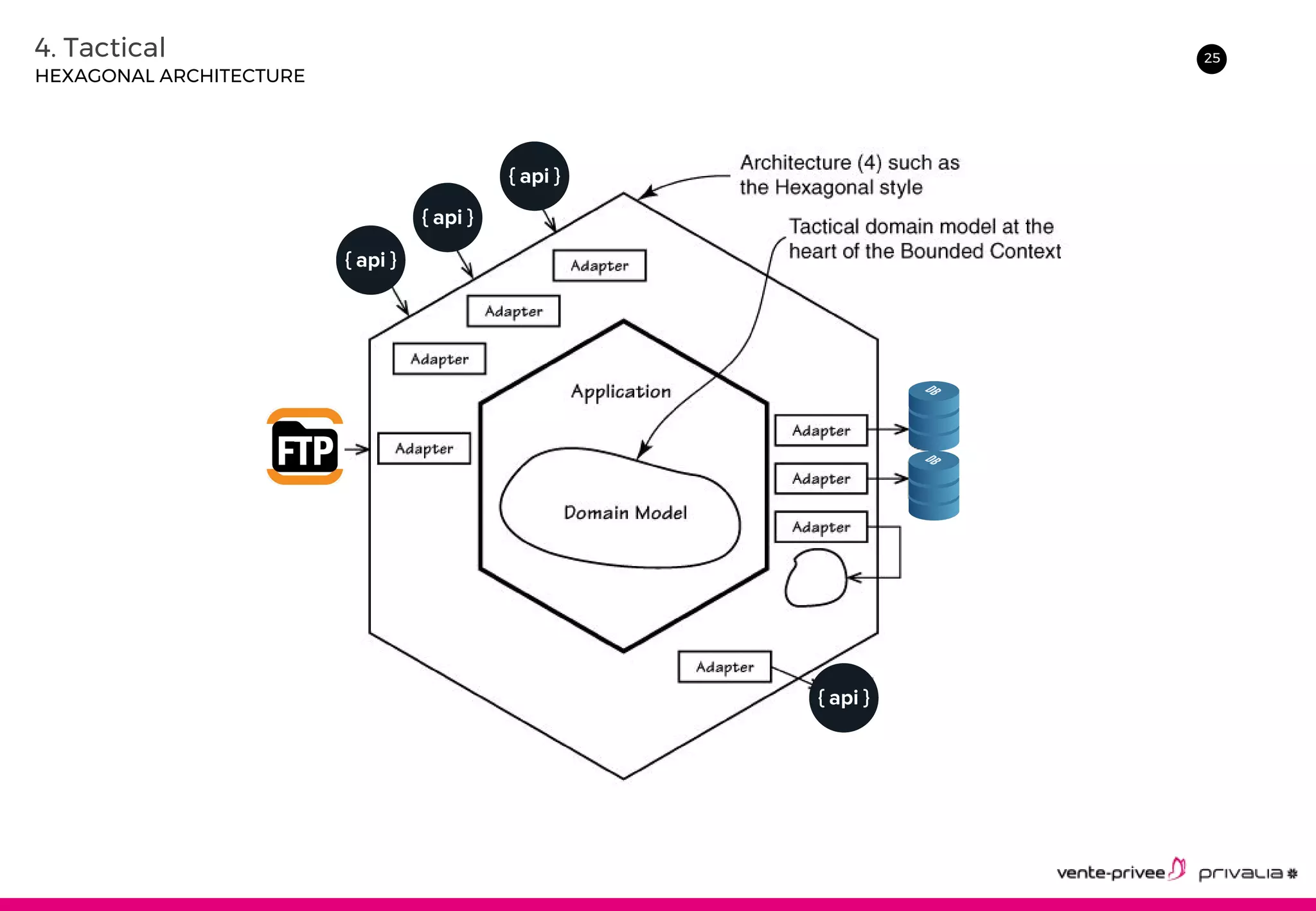
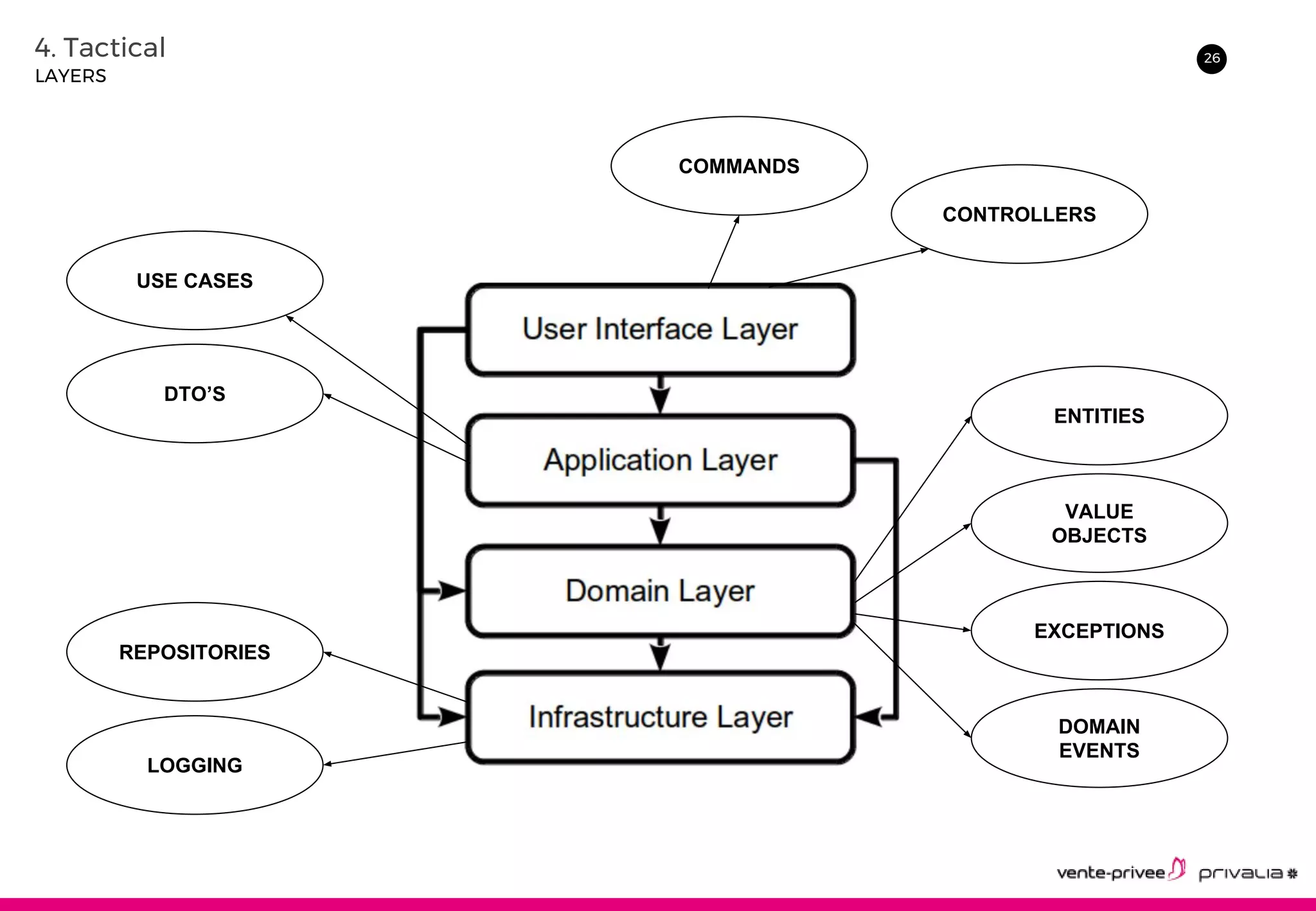
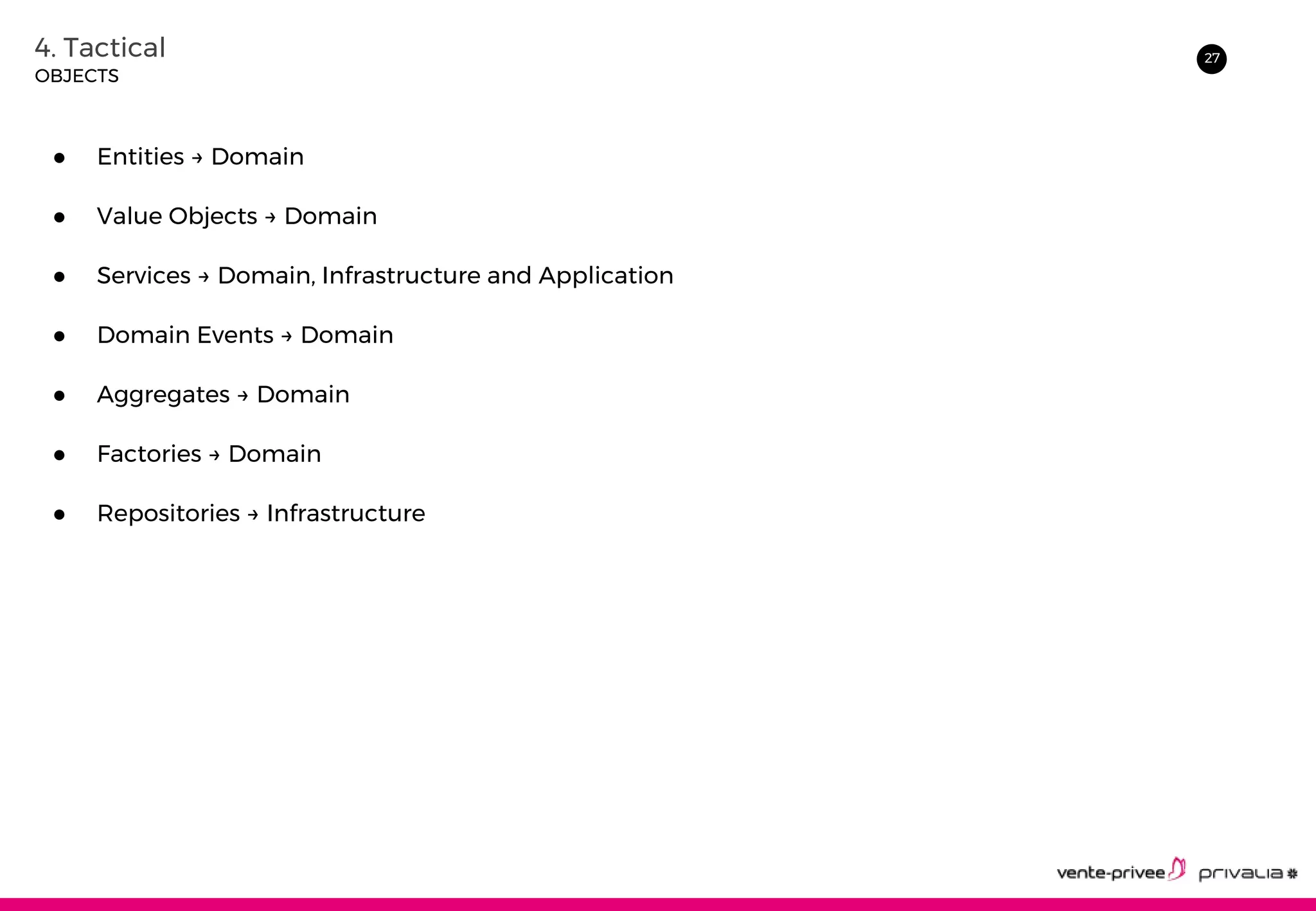
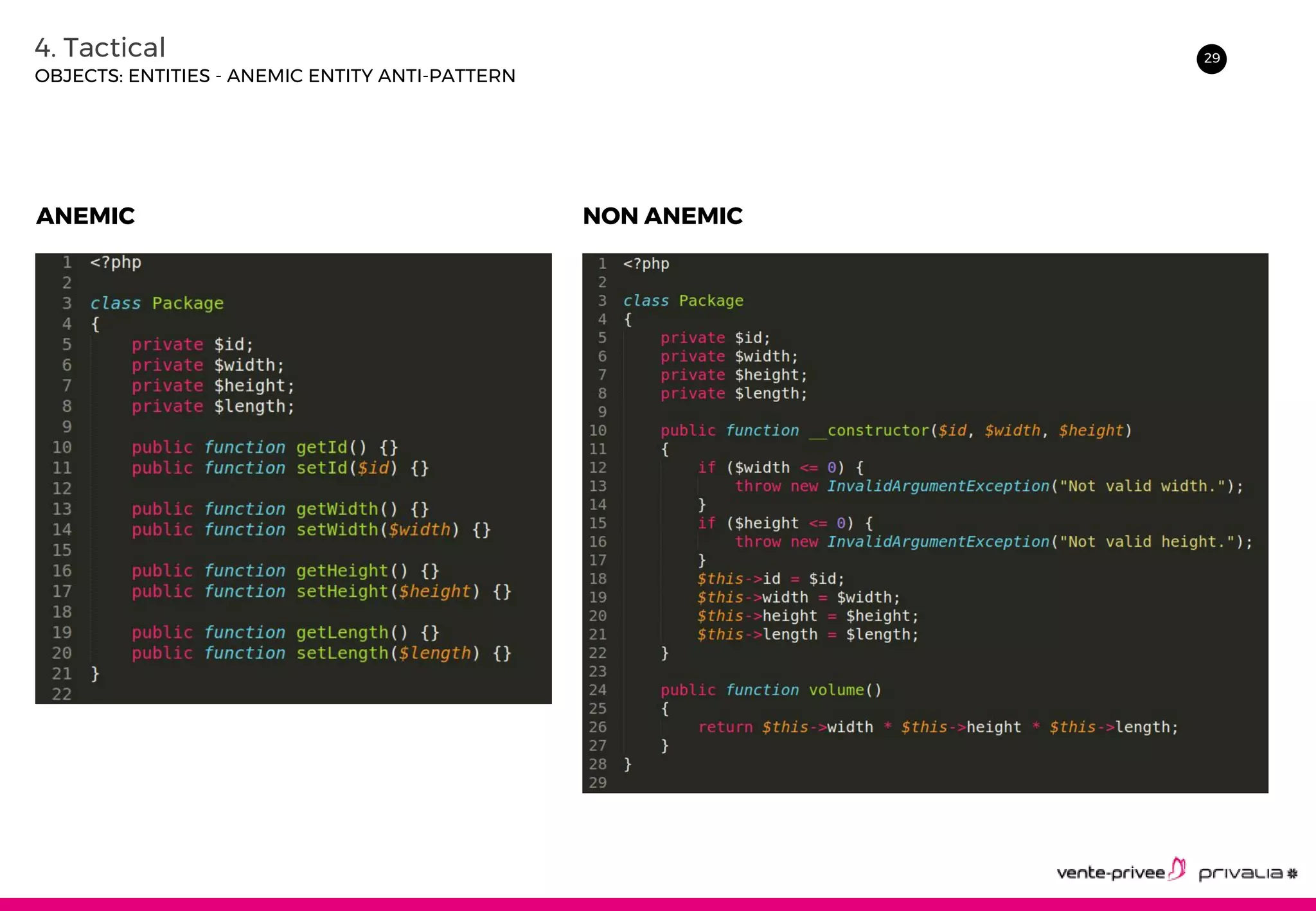
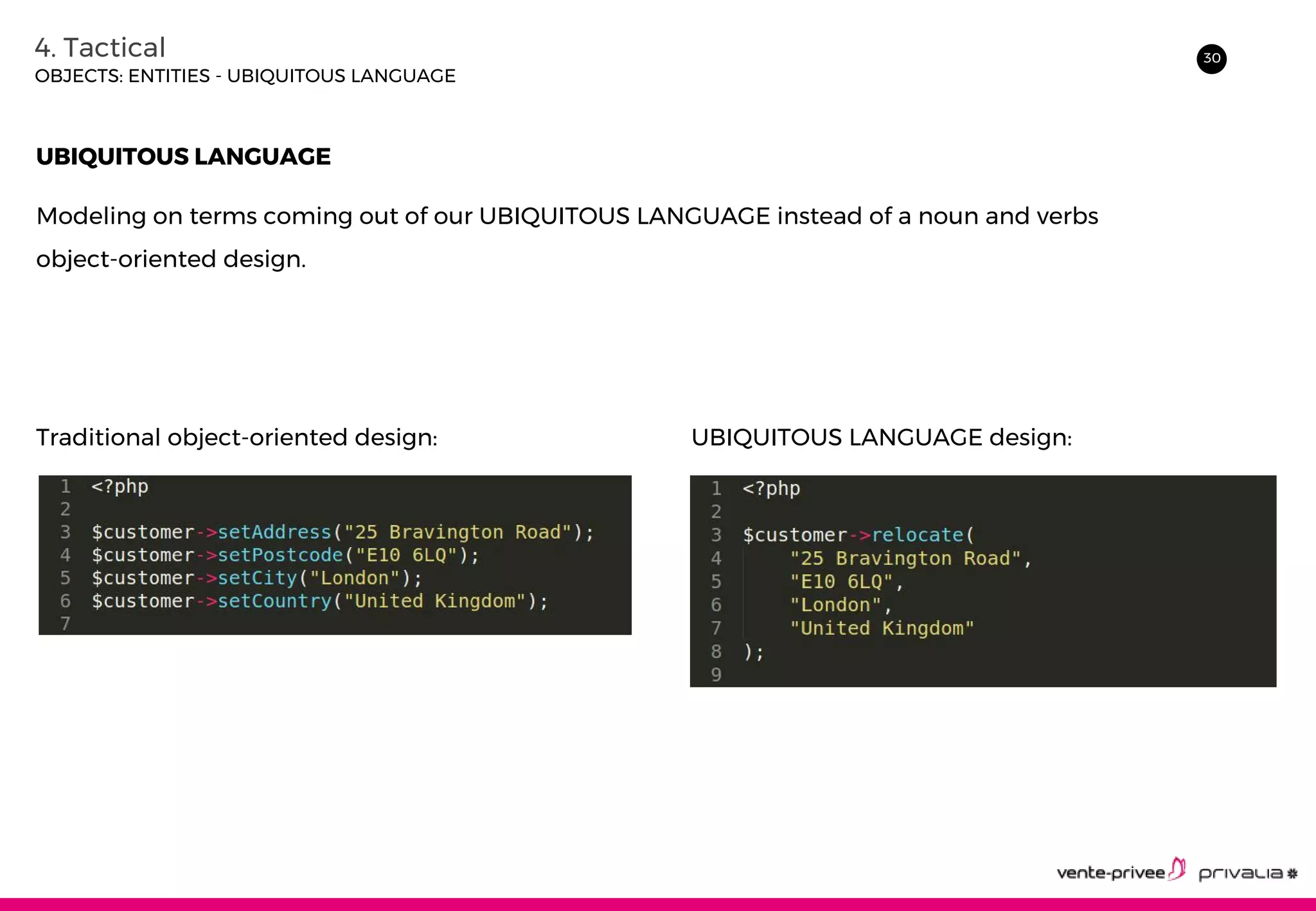
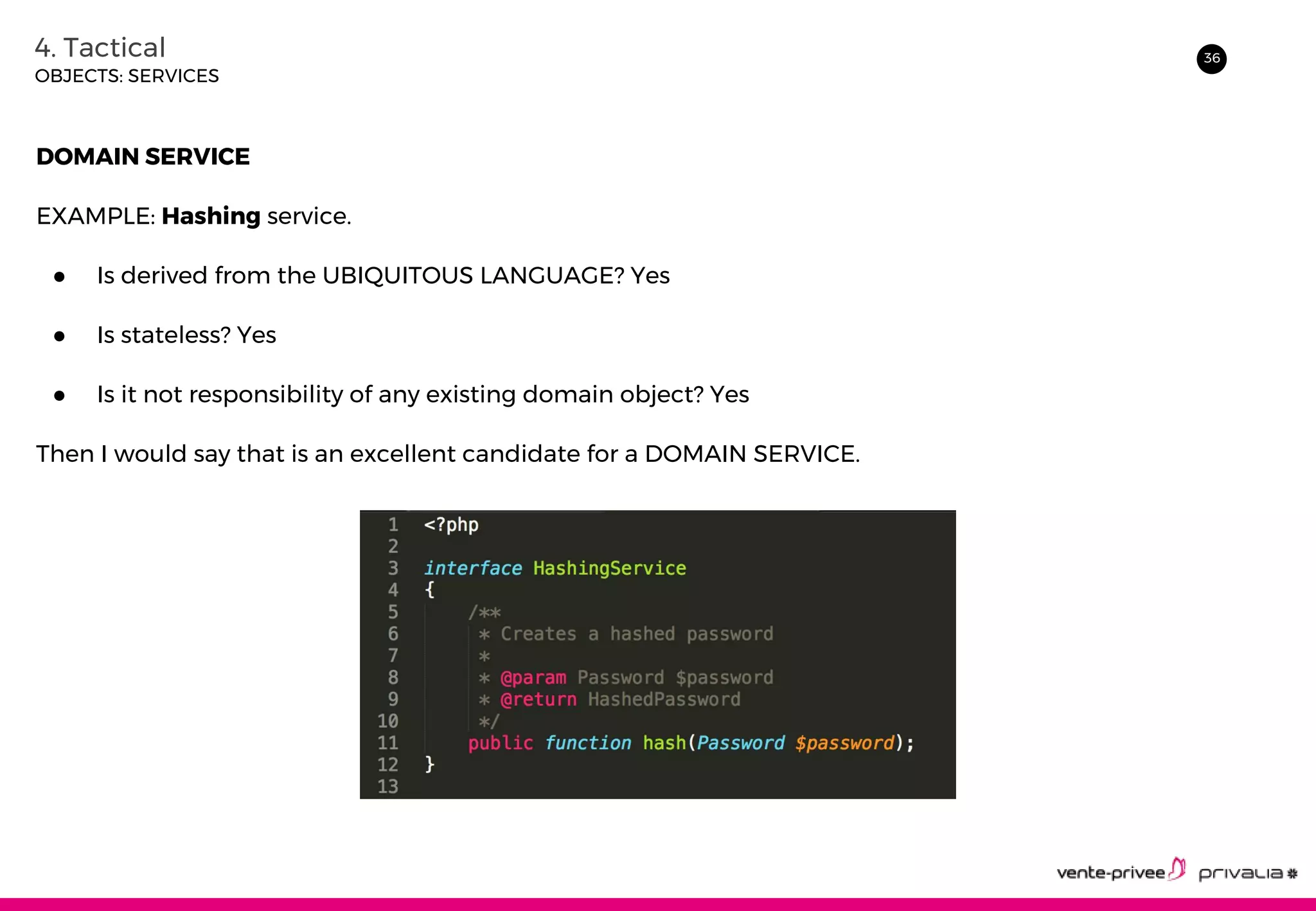
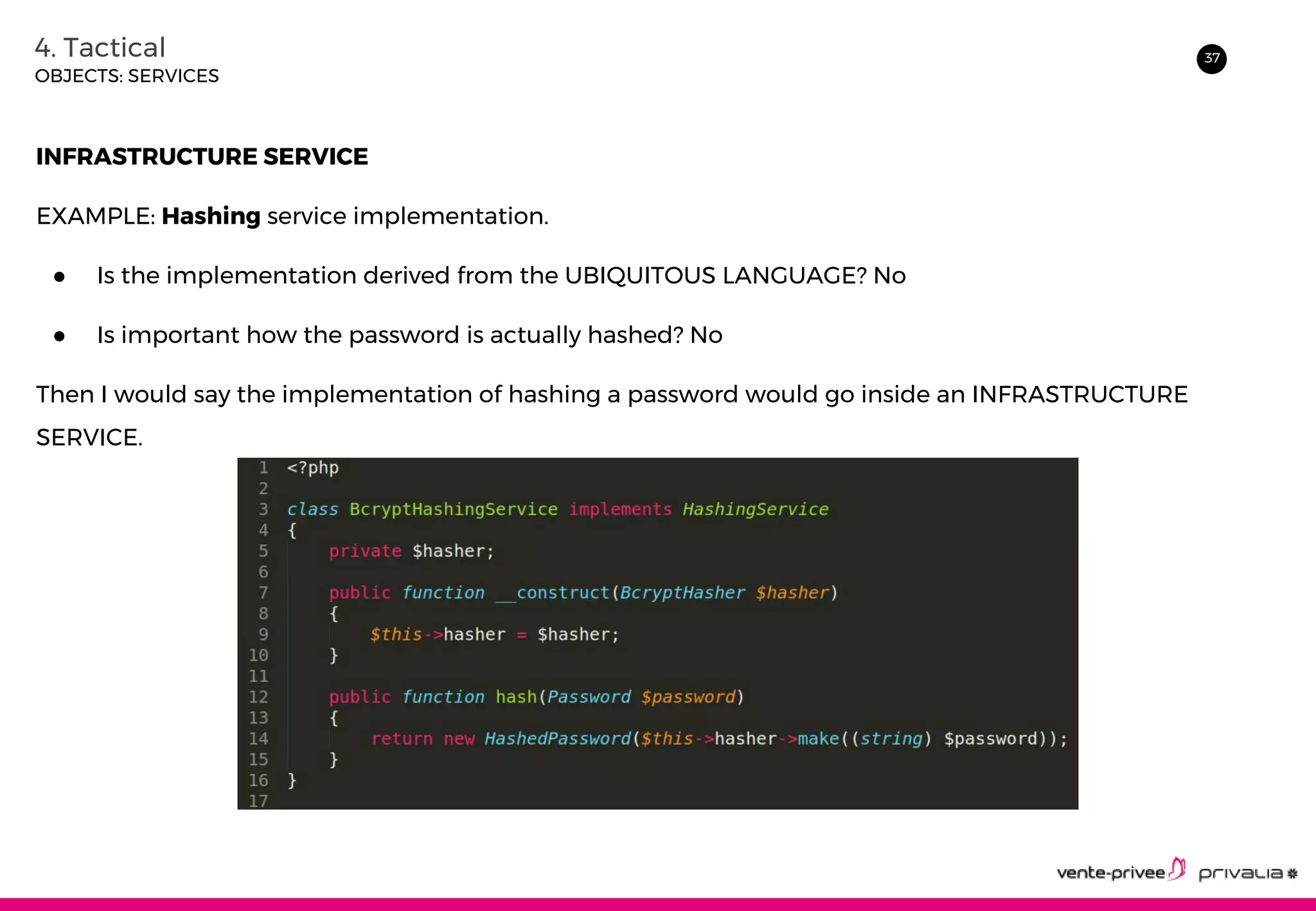
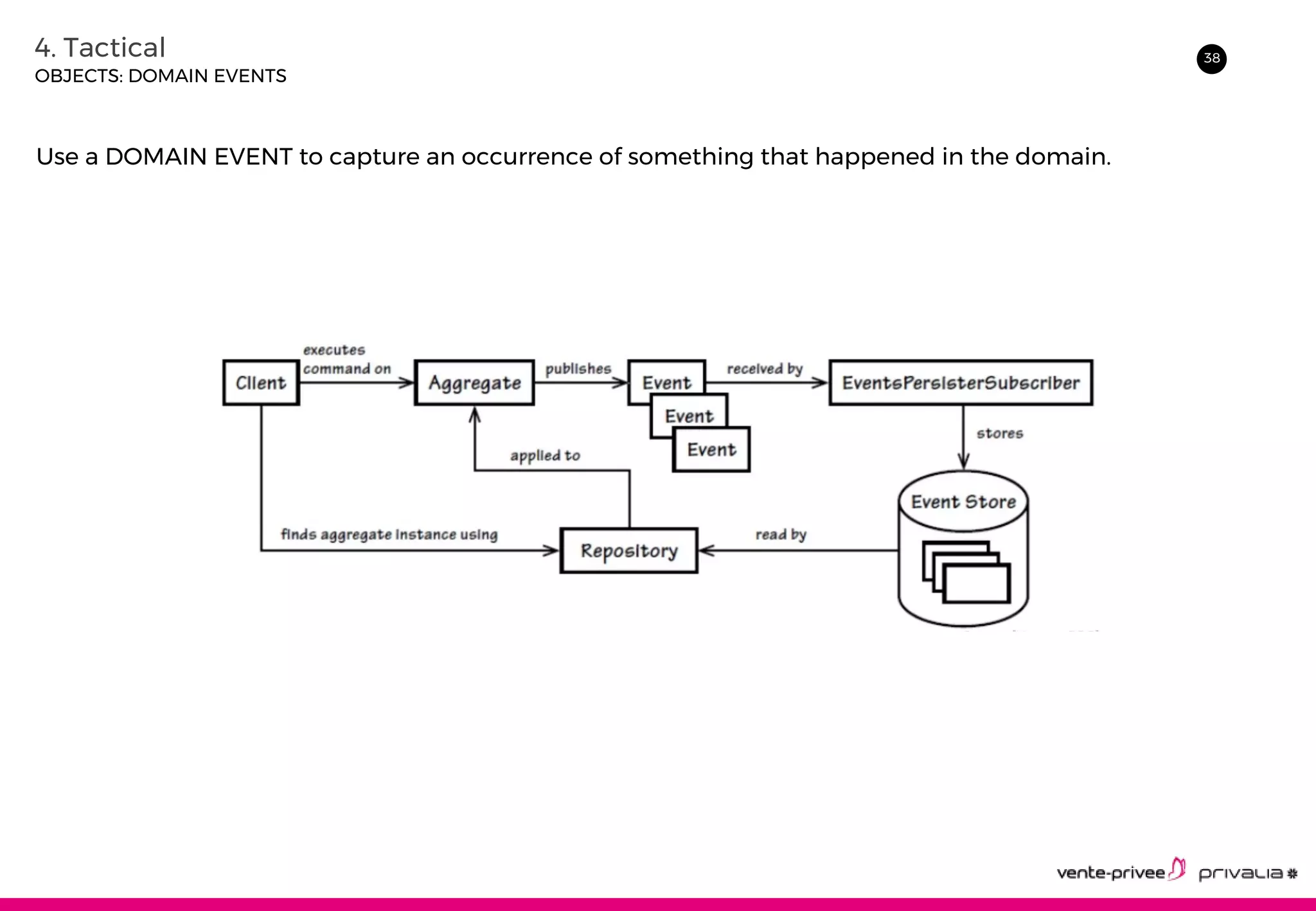
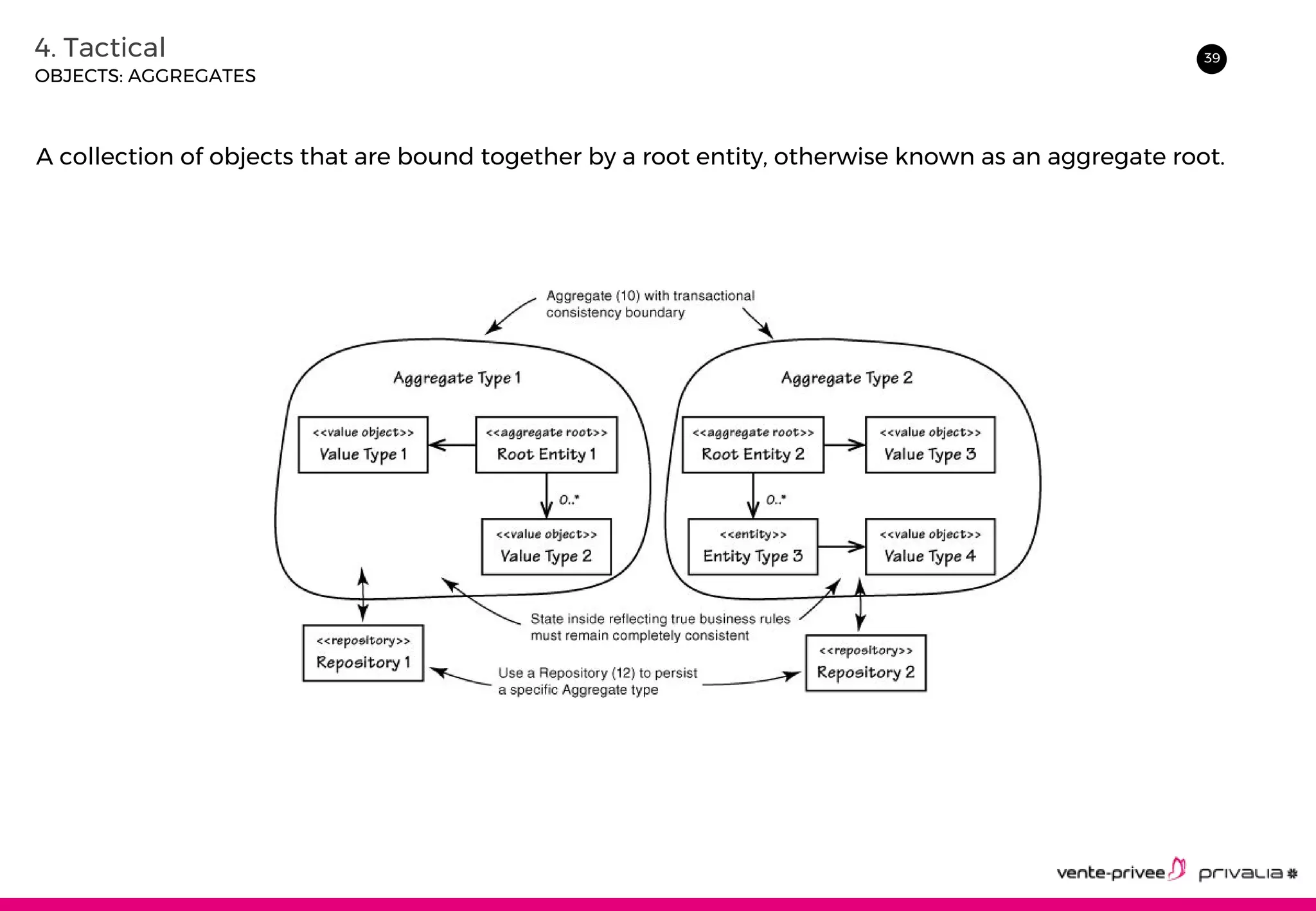
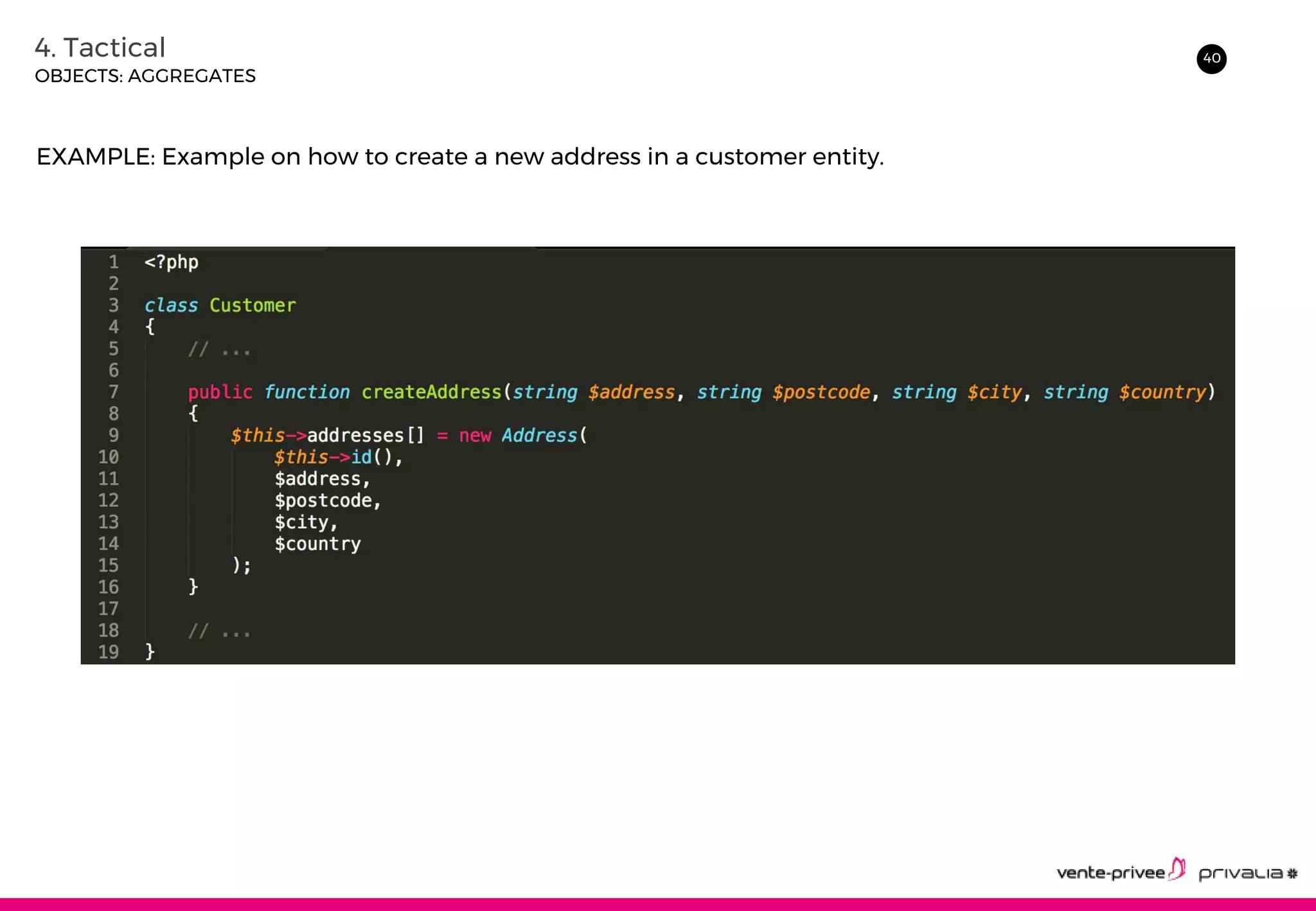
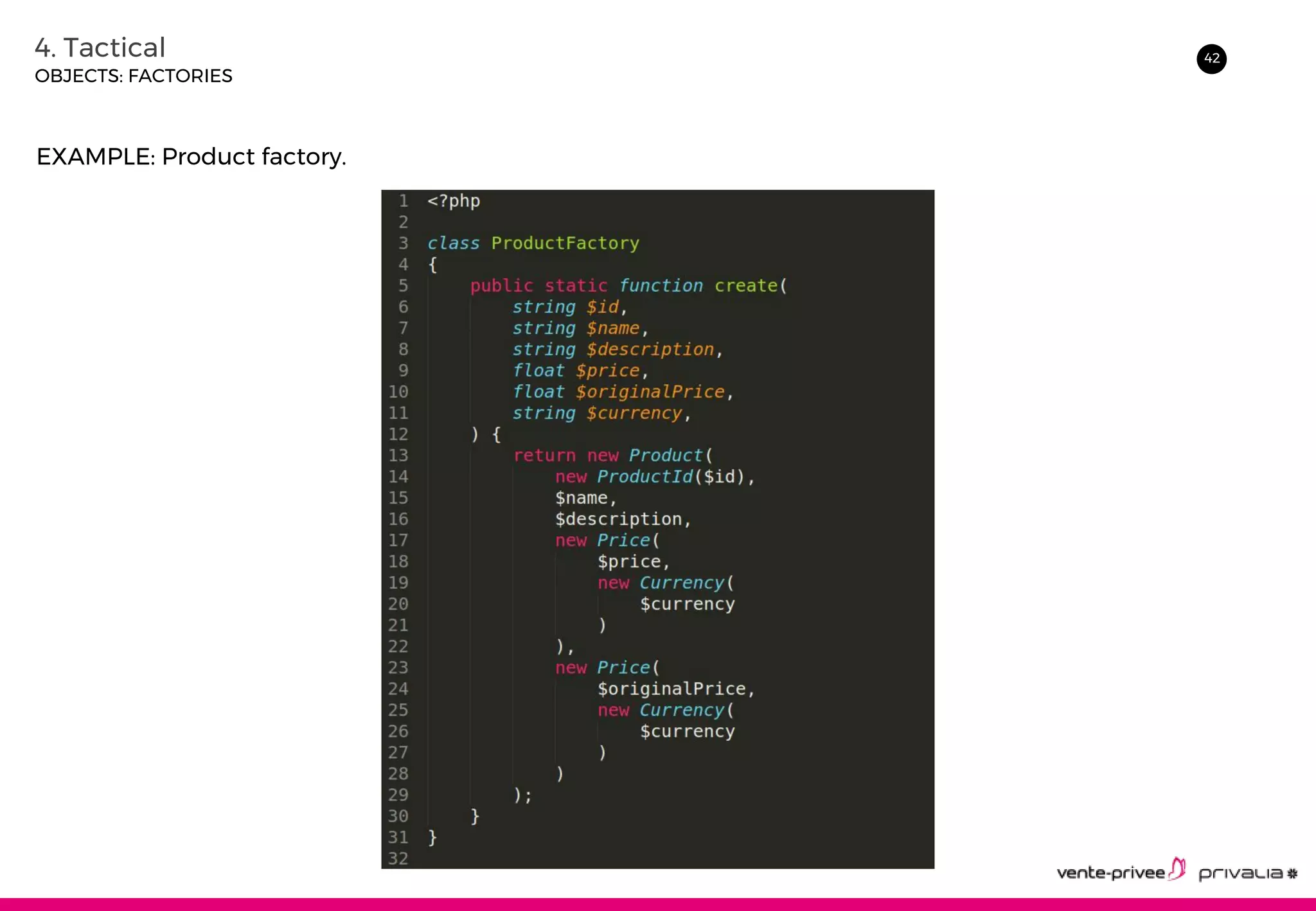
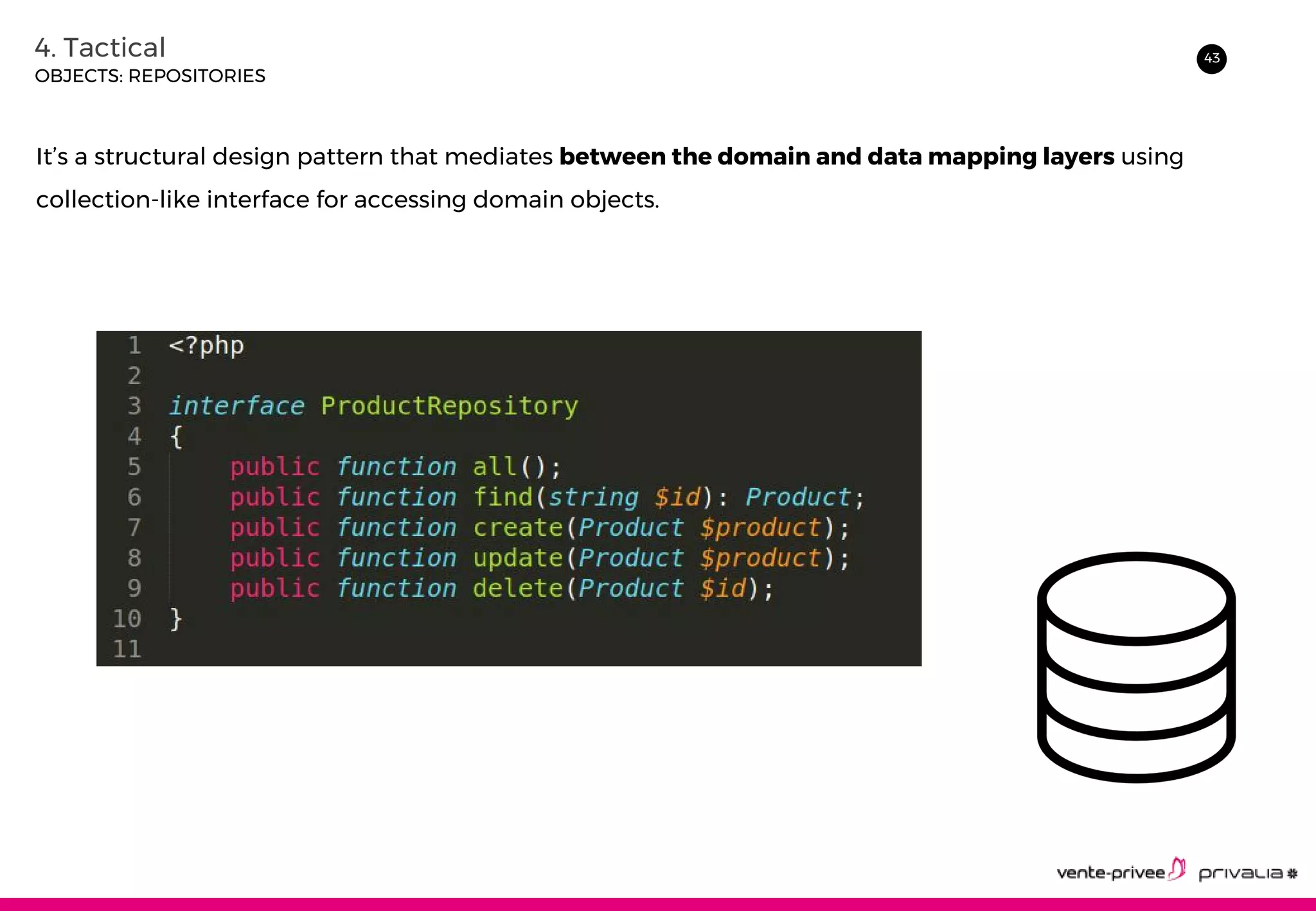
The document discusses Domain-Driven Design (DDD), an approach to software development for complex domains. It covers DDD concepts like the domain, subdomain, bounded context, and ubiquitous language. It also discusses strategic DDD concepts and tactical implementations, including hexagonal architecture, entities, value objects, services, domain events, aggregates, factories, and repositories. The advantages of DDD are clearer code, better domain understanding, and focus on the business domain. Disadvantages include a high upfront time cost and learning curve.