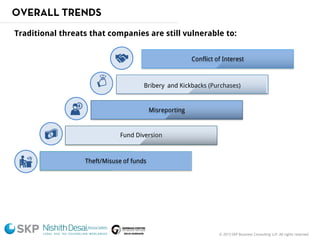
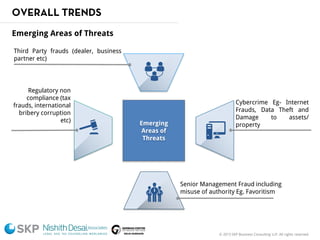
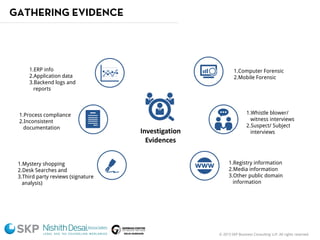
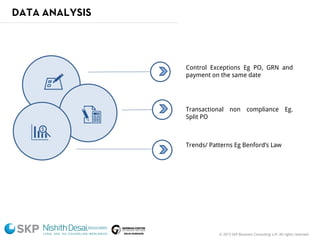
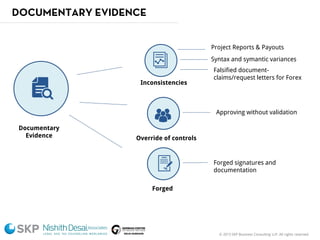
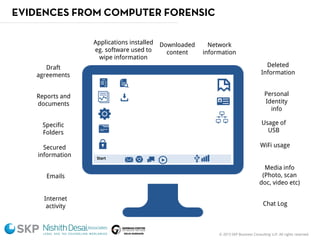
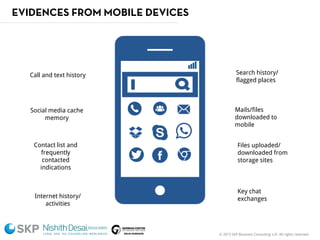
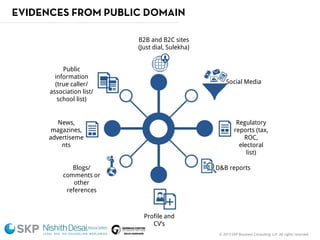
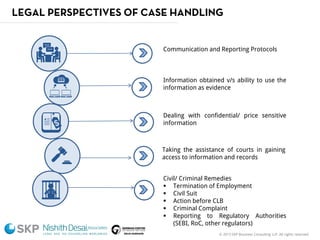
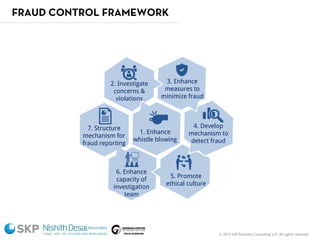
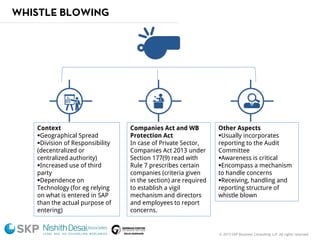
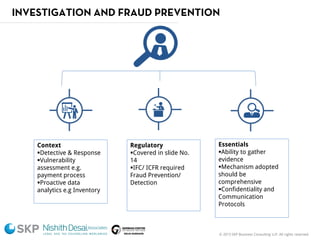
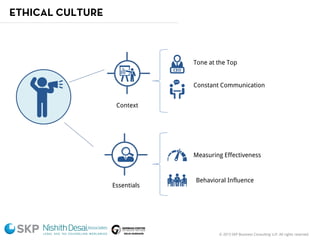
The document outlines a fraud control framework, discussing current fraud trends, evidence gathering techniques, and key elements of an effective framework. It notes that while traditional fraud threats still exist, emerging areas now include regulatory non-compliance, cybercrime, and third-party fraud. Effective controls require enhancing whistleblowing policies, investigative capacity, fraud prevention measures, and promoting an ethical organizational culture.