FOUR BEST PRACTICES TO IMPROVE DOC SECURITY
•
0 likes•35 views
FOUR GREAT REMINDERS FOR ALL LEGAL FIRMS...
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
Security and control in Management Information System

Security and control in Management Information System
Mitre ATT&CK and the Mueller GRU Indictment: Lessons for Organizations

Mitre ATT&CK and the Mueller GRU Indictment: Lessons for Organizations
Similar to FOUR BEST PRACTICES TO IMPROVE DOC SECURITY
Similar to FOUR BEST PRACTICES TO IMPROVE DOC SECURITY (20)
Typical system servicesProgram executionIO operationsFile Sy.pdf

Typical system servicesProgram executionIO operationsFile Sy.pdf
Wave 14 - Winodws 7 Security Story Core by MVP Azra Rizal

Wave 14 - Winodws 7 Security Story Core by MVP Azra Rizal
Sallysspecialservices networksecurityproposal2-100305141834-phpapp02

Sallysspecialservices networksecurityproposal2-100305141834-phpapp02
Enterprise Digital Rights Management (Persistent Security)

Enterprise Digital Rights Management (Persistent Security)
Primend praktiline konverents - Office 365 turvalisus

Primend praktiline konverents - Office 365 turvalisus
More from Tim O'Leary
More from Tim O'Leary (20)
Adopting a 'One Boat' Mindset Will Help with Organizational Change

Adopting a 'One Boat' Mindset Will Help with Organizational Change
Recently uploaded
Recently uploaded (20)
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
FOUR BEST PRACTICES TO IMPROVE DOC SECURITY
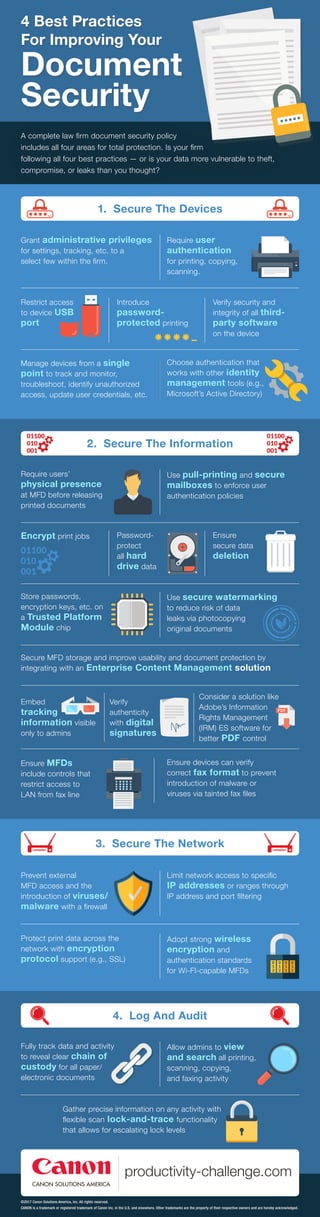
- 1. A complete law firm document security policy includes all four areas for total protection. Is your firm following all four best practices — or is your data more vulnerable to theft, compromise, or leaks than you thought? 4 Best Practices For Improving Your Document Security 3. Secure The Network Limit network access to specific IP addresses or ranges through IP address and port filtering Protect print data across the network with encryption protocol support (e.g., SSL) Adopt strong wireless encryption and authentication standards for Wi-FI-capable MFDs Prevent external MFD access and the introduction of viruses/ malware with a firewall 4. Log And Audit Allow admins to view and search all printing, scanning, copying, and faxing activity Gather precise information on any activity with flexible scan lock-and-trace functionality that allows for escalating lock levels Fully track data and activity to reveal clear chain of custody for all paper/ electronic documents 2. Secure The Information Use pull-printing and secure mailboxes to enforce user authentication policies Encrypt print jobs Password- protect all hard drive data Ensure secure data deletion Store passwords, encryption keys, etc. on a Trusted Platform Module chip Require users’ physical presence at MFD before releasing printed documents Use secure watermarking to reduce risk of data leaks via photocopying original documents Embed tracking information visible only to admins Verify authenticity with digital signatures Ensure devices can verify correct fax format to prevent introduction of malware or viruses via tainted fax files Ensure MFDs include controls that restrict access to LAN from fax line Secure MFD storage and improve usability and document protection by integrating with an Enterprise Content Management solution Consider a solution like Adobe’s Information Rights Management (IRM) ES software for better PDF control 1. Secure The Devices Require user authentication for printing, copying, scanning. Restrict access to device USB port Introduce password- protected printing Verify security and integrity of all third- party software on the device Choose authentication that works with other identity management tools (e.g., Microsoft’s Active Directory) Grant administrative privileges for settings, tracking, etc. to a select few within the firm. Manage devices from a single point to track and monitor, troubleshoot, identify unauthorized access, update user credentials, etc. ©2017 Canon Solutions America, Inc. All rights reserved. CANON is a trademark or registered trademark of Canon Inc. in the U.S. and elsewhere. Other trademarks are the property of their respective owners and are hereby acknowledged.