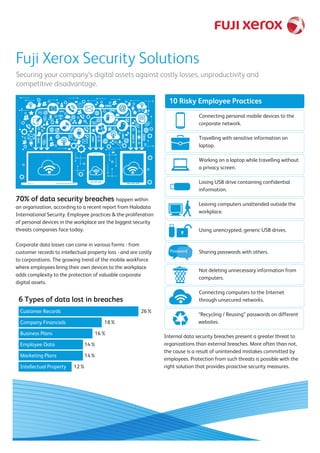
10 Risky Employee Practices - Security solutions
- 1. Fuji Xerox Security Solutions Securing your company’s digital assets against costly losses, unproductivity and competitive disadvantage. 70% of data security breaches happen within an organization, according to a recent report from Halodata International Security. Employee practices & the proliferation of personal devices in the workplace are the biggest security threats companies face today. Corporate data losses can come in various forms - from customer records to intellectual property loss - and are costly to corporations. The growing trend of the mobile workforce where employees bring their own devices to the workplace adds complexity to the protection of valuable corporate digital assets. 10 Risky Employee Practices Connecting personal mobile devices to the corporate network. Connecting computers to the Internet through unsecured networks. Not deleting unnecessary information from computers. Password Sharing passwords with others. Using unencrypted, generic USB drives. Leaving computers unattended outside the workplace. Losing USB drive containing confidential information. Working on a laptop while travelling without a privacy screen. Travelling with sensitive information on laptop. Customer Records 26% Company Financials 18% Business Plans 16% Employee Data 14% Marketing Plans 14% Intellectual Property 12% 6 Types of data lost in breaches “Recycling / Reusing” passwords on different websites. Internal data security breaches present a greater threat to organizations than external breaches. More often than not, the cause is a result of unintended mistakes committed by employees. Protection from such threats is possible with the right solution that provides proactive security measures.
- 2. 2) Disk Encryption for Data Protection against Theft The theft of laptops is getting more common place as the workforce becomes more mobile. Once the hard drive is removed from the laptop, content from the hard drive can be accessed, resulting in costly loss of confidential data. Encrypting the hard drives of laptops provides additional security against laptop thefts or any unauthorized removal of hard drives. In addition to the 256 bit AES full drive encryption, Fuji Xerox Security Solutions can be centrally managed by an administrator. The footprint is so small that there is no compromise on the performance of computer systems even when the data is being encrypted. Streamline your Data Security with Proactive Solutions Proactive Solutions to Secure your Business 1) Endpoint Security with Remote Manageability In a world where portable lifestyle devices are transform- ing the way we work and live, Endpoint Security is designed to maintain productivity and make work more convenient, secure and enjoyable. Using a whitelist based policy approach, it allows the use of specific devices for certain computers/users/groups so that users stay productive while organizations maintain control over devices being used as well as the data being transferred by users. Xerox and the sphere of connectivity design are trademarks or registered trademarks of Xerox Corporation in the U.S. and/or other countries. http://www.fujixerox.com.sg 80 Anson Road, #01-01 Fuji Xerox Towers, Singapore 079907 Tel: (65) 6766-8888 Fuji Xerox Singapore Pte. Ltd. The contents described herein are correct as of June, 2013. Prevention is always better than cure. Security solutions that defend well against data breaches should be able to block or clamp down on activities before any damaged is done. A good security solution should also be holistic and provide protection for as many scenarios as possible. Fuji Xerox Security Solutions provides your organization with the tools to proactively manage possible security breaches from within the organization down to the portable devices (such as thumbdrives) employees use for information distribution. The complexity of security management is taken out of the equation with Fuji Xerox Security Solutions. In its place is an affordable, scalable and more importantly, tested standard of proactive mechanisms that helps businesses focus on their core business and leave security protection in the right hands. Computer systems connected to corporate network Devices commonly connected to users’ computers for file sharing Endpoint securely manages rights over use of devices connected to corporate systems 3) Hardware encrypted Flashdrives Flashdrives are the most common approach to physical file distribution. Not only are most flashdrives easily misplaced, there is little control over how flashdrives change hands. Software encryption provides little protection against loss of data as the drive can easily be reformatted. Issuing hardware encrypted flashdrives offers security against theft as well as the manageability of critical organization’s prorietary content. Encrypted flashdrives by Fuji Xerox are 256 bit AES compliant, have an onboard Antivirus scanner and come in a rugged housing resistant to spills. For ease of manageability, these flashdrives can be administered remotely for ease of deployment. For more information, please visit http://goo.gl/Dw866 (case sensitive) *Fuji Xerox Singapore is the authorized reseller for Halodata International for the products described in this brochure For more information or to see a demonstration, please contact: Mr Gareth Liew Senior Sustainability Business Analyst (65) 6766-6387 gareth.liew@sgp.fujixerox.com
