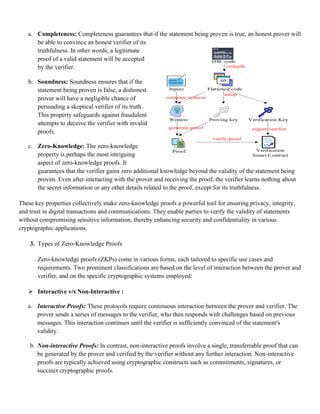
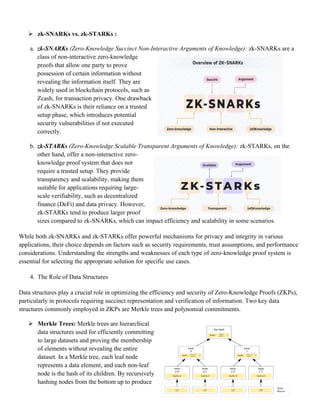
Zero-knowledge proofs (ZKPs) allow a party to prove possession of information without revealing that information. They use data structures like Merkle trees and polynomial commitments to optimize proof generation and verification. Merkle trees provide efficient proof of data membership while polynomial commitments enable succinct verification of computations. ZKPs see increasing use for privacy in applications like blockchain transactions, voting, and medical records by verifying validity without disclosing sensitive details.