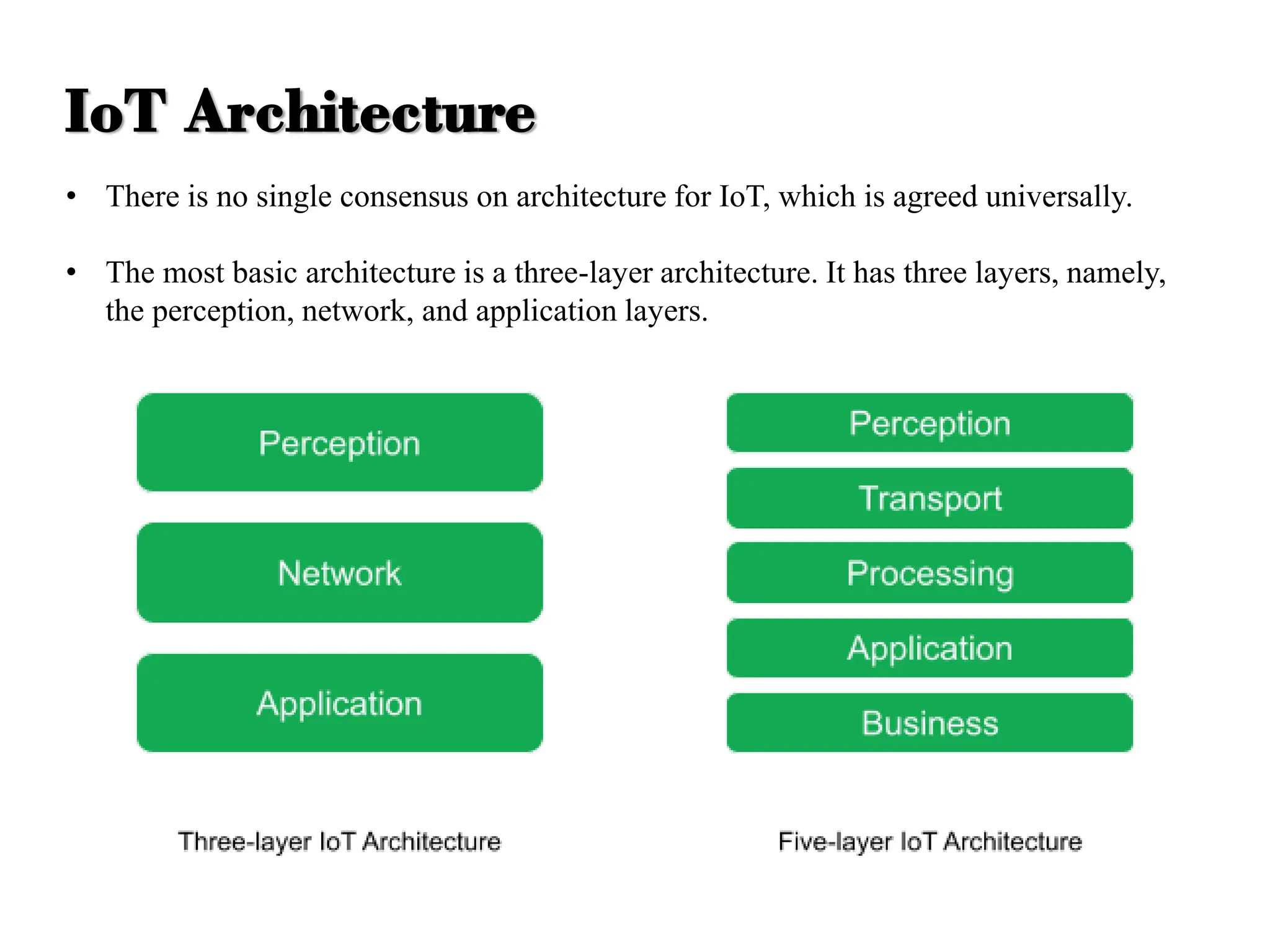
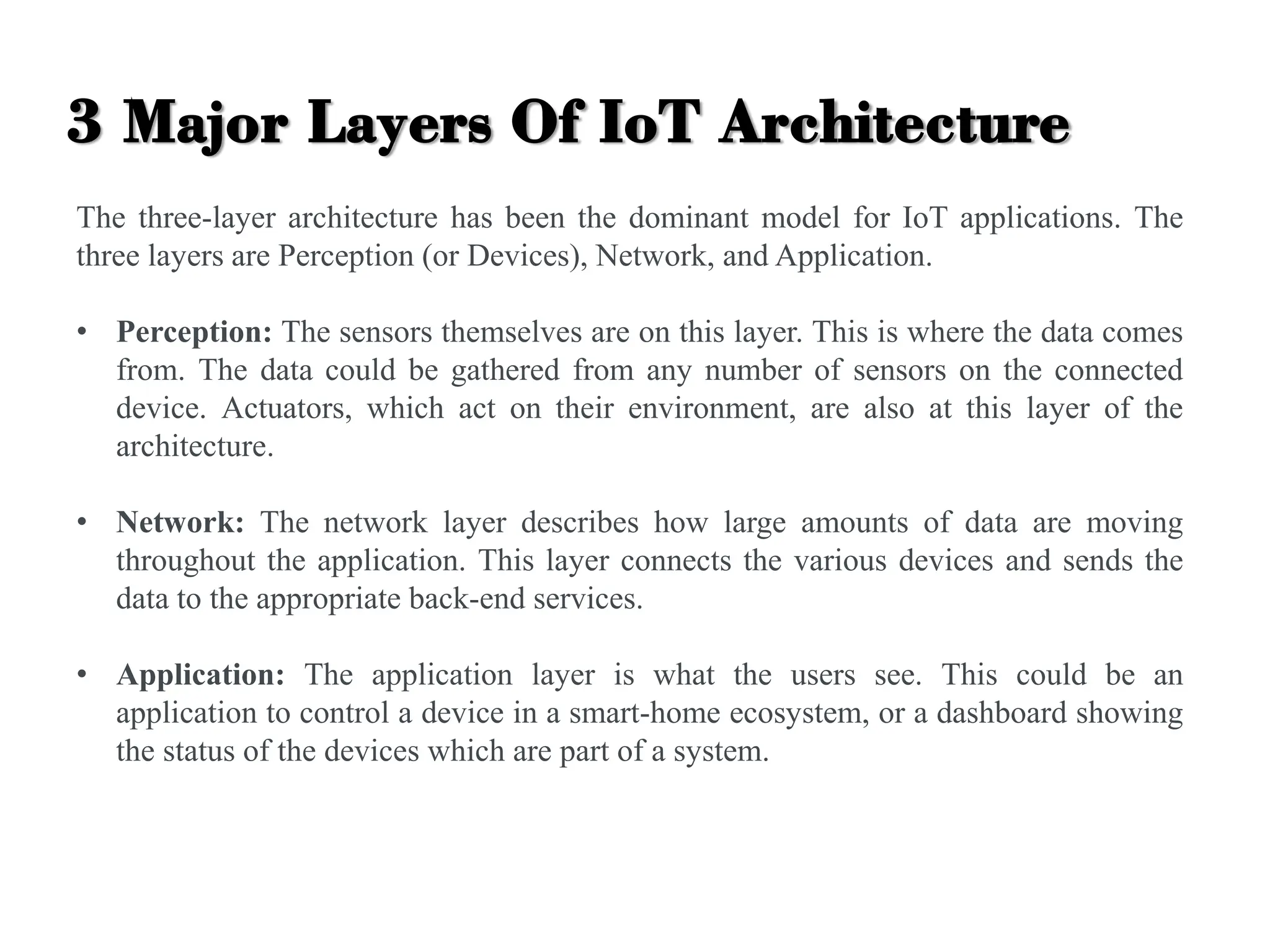
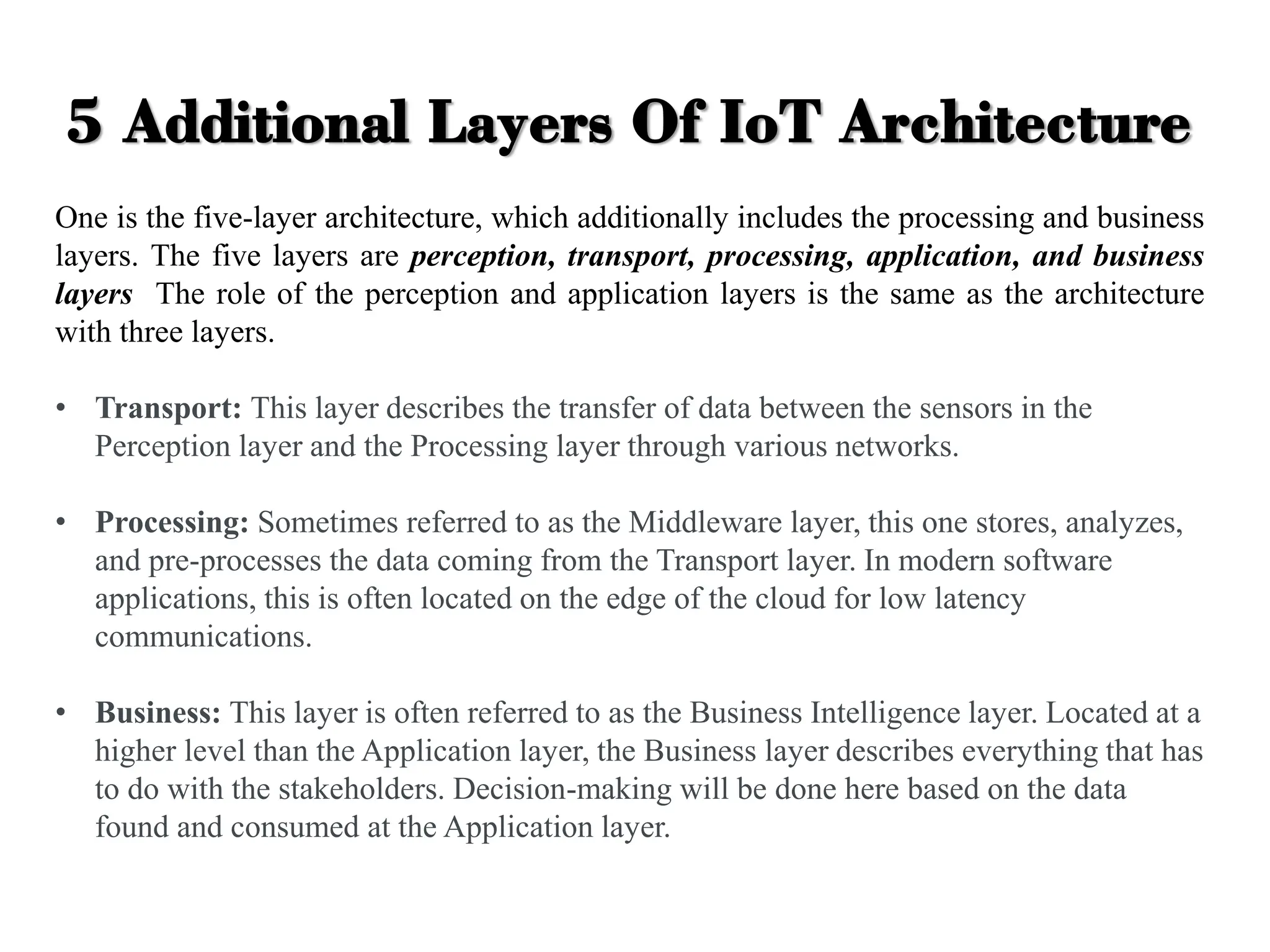
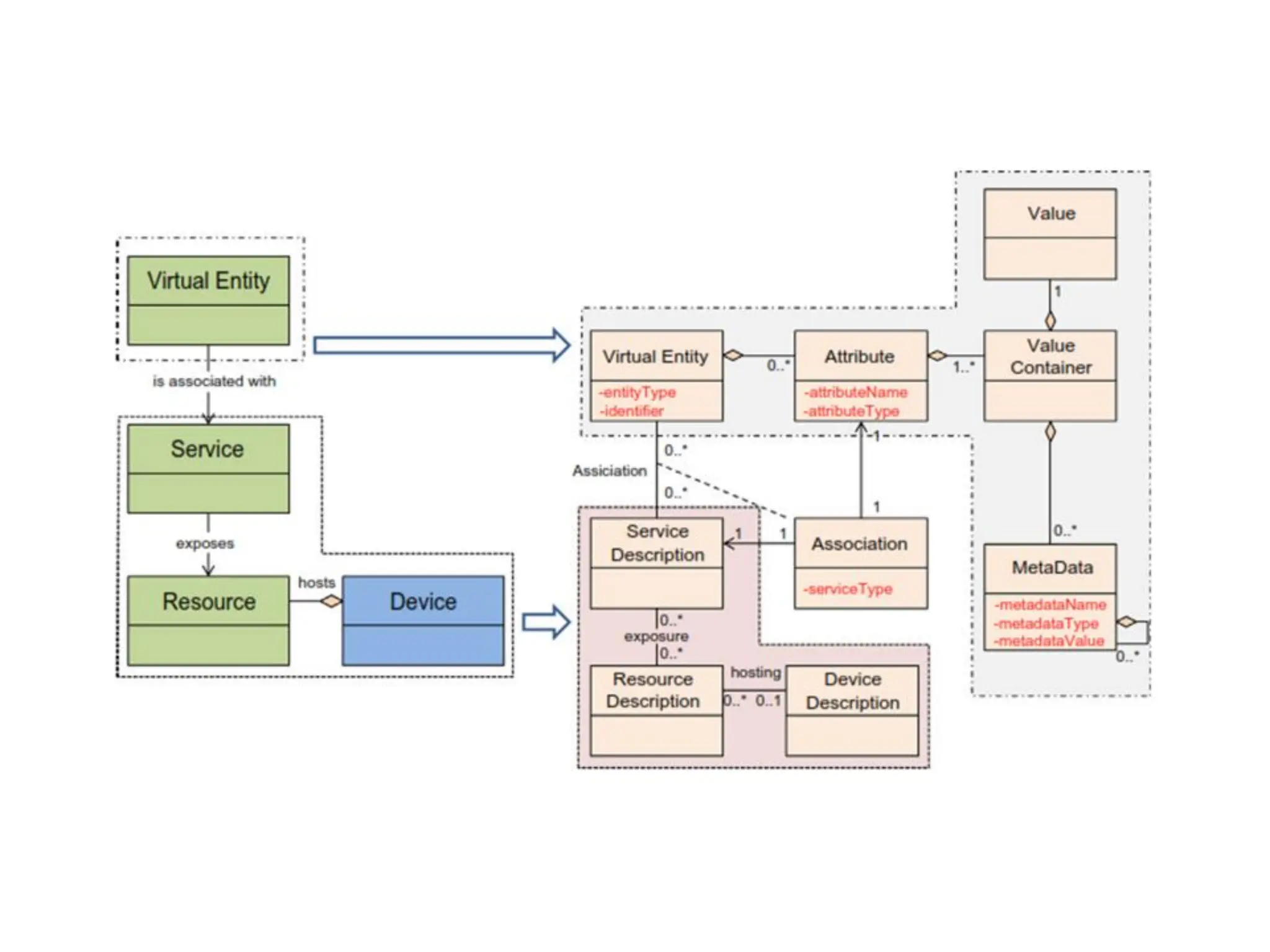
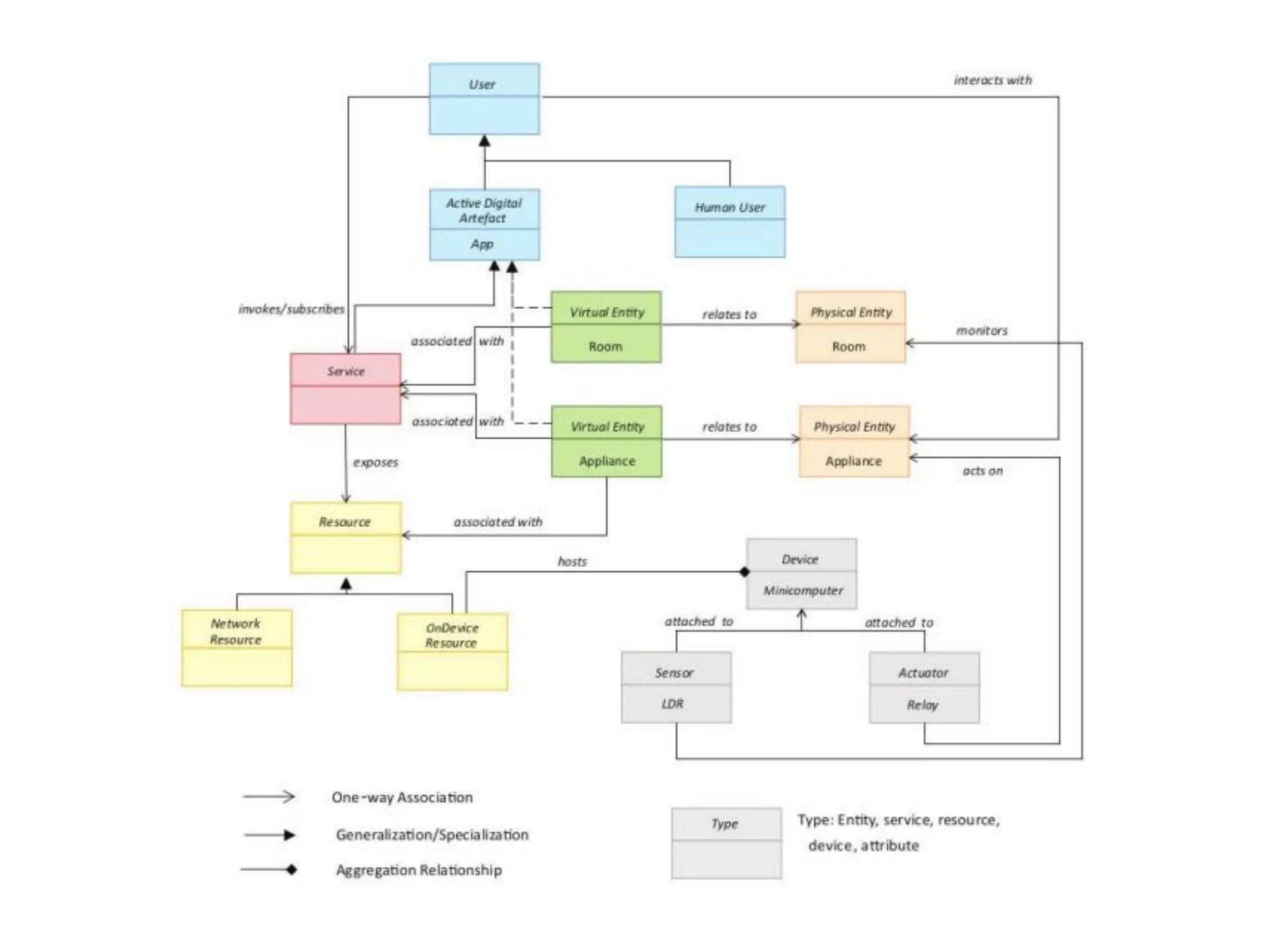
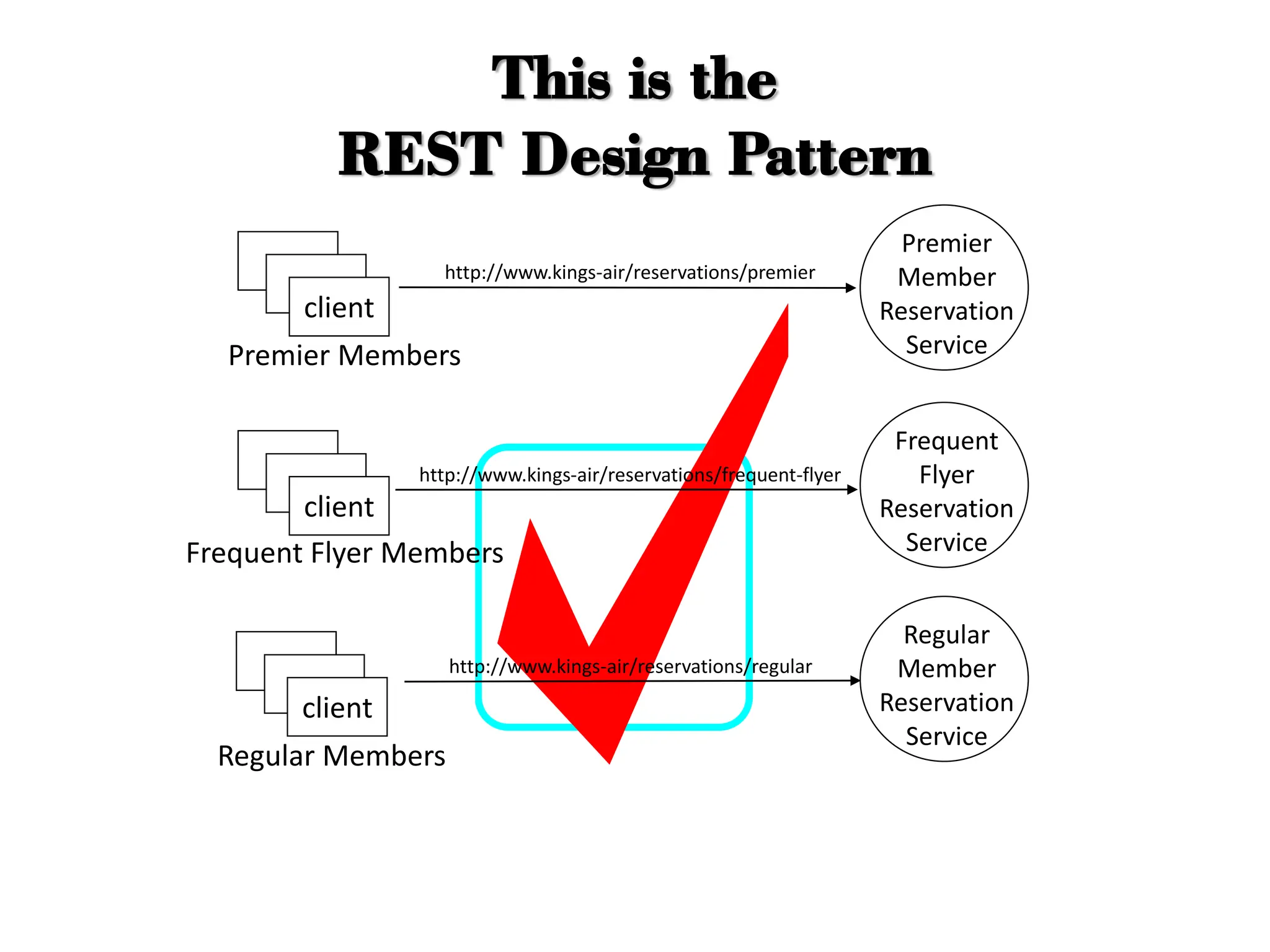
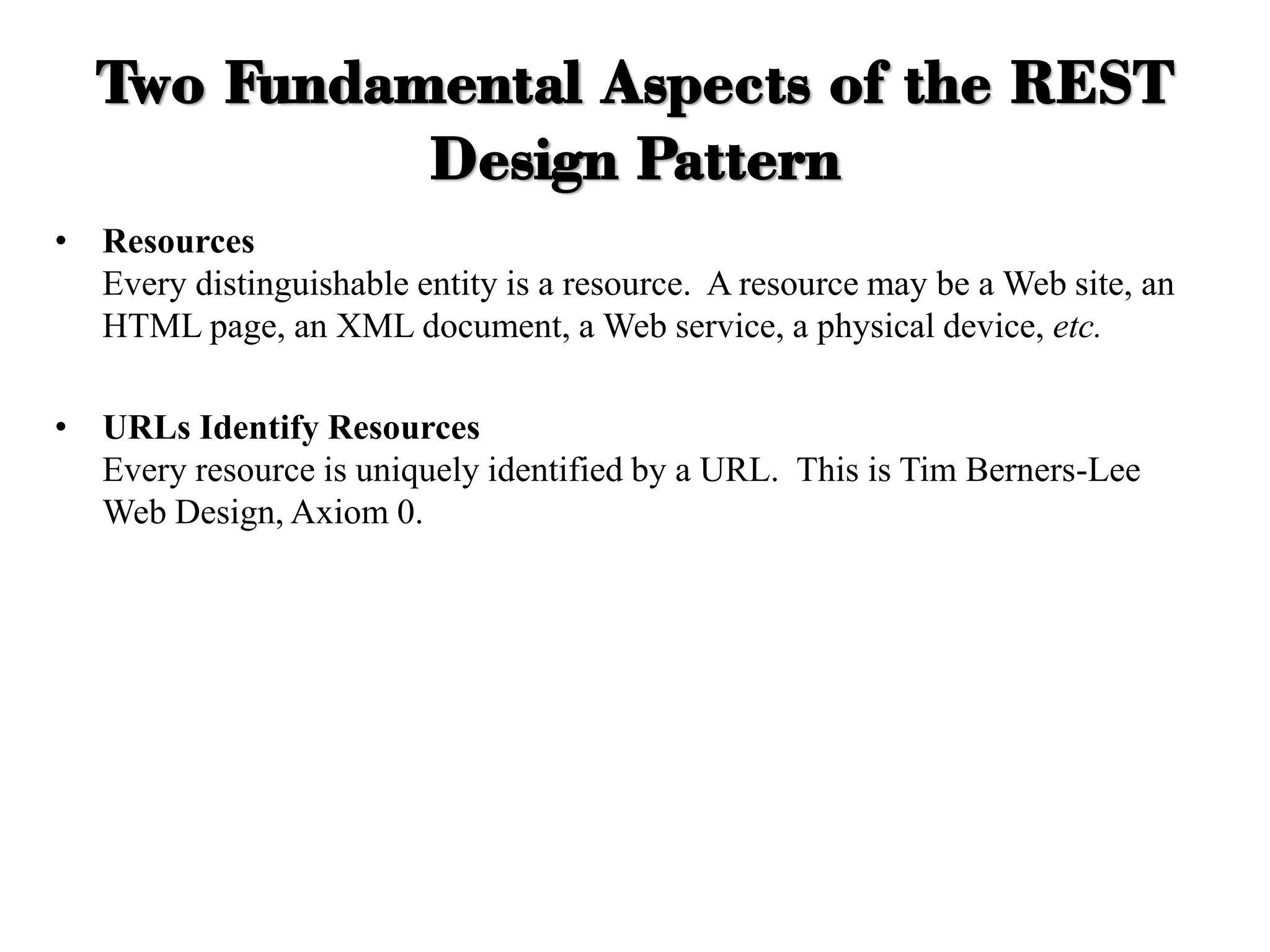
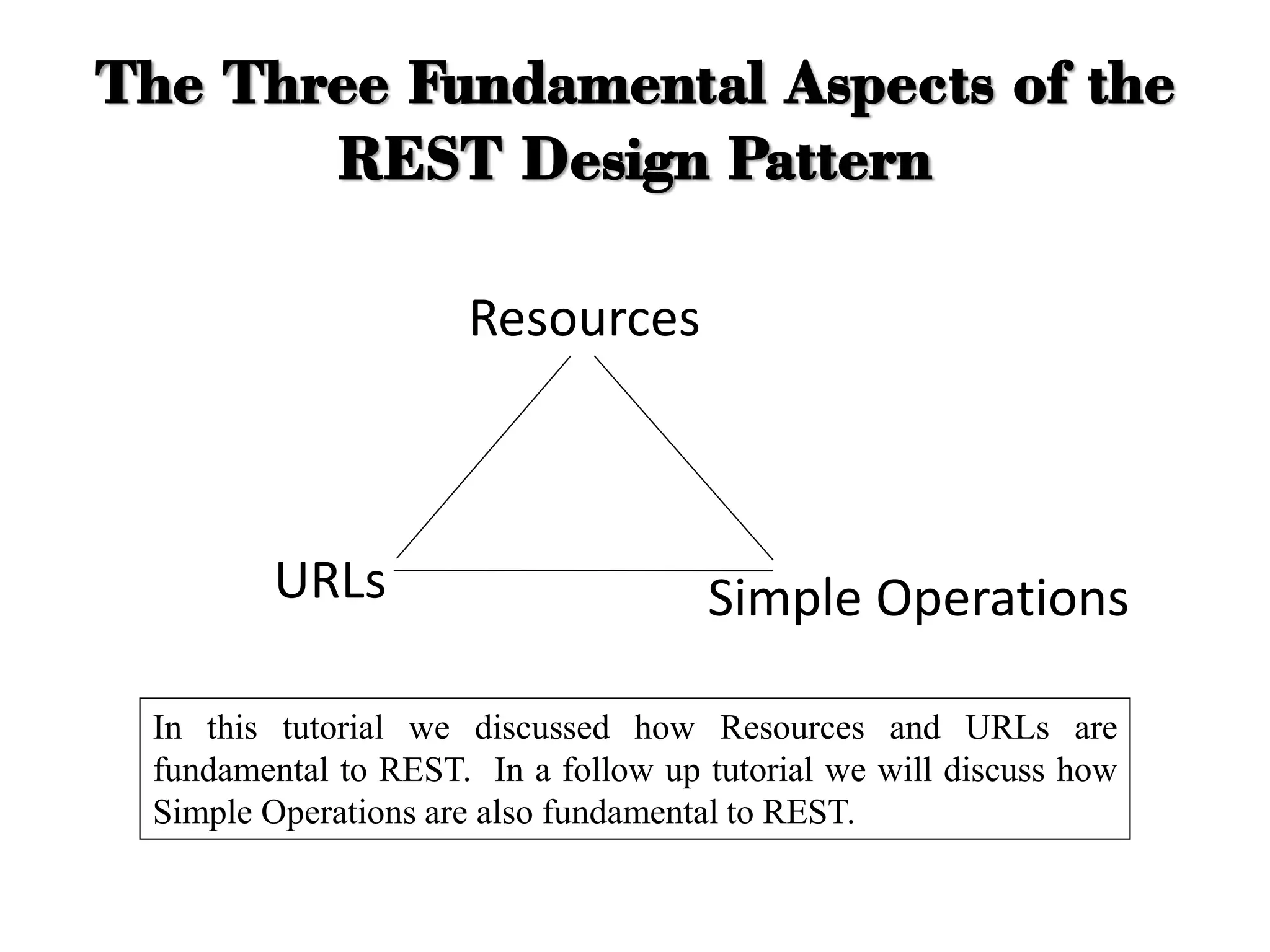
The document discusses various IoT architectures, emphasizing three-layer, five-layer, and four-stage models alongside IoT reference and functional models. Key components of these models include perception, network, application, middleware, and business layers, which distinguish roles in data collection, transfer, processing, and user interaction. Additionally, it explores the REpresentational State Transfer (REST) design pattern, differentiating RESTful approaches in web services from traditional methods, focusing on resources, URLs, and the implications of stateless interactions.