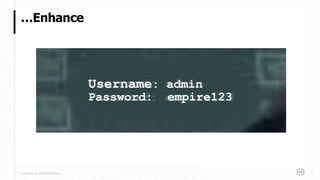
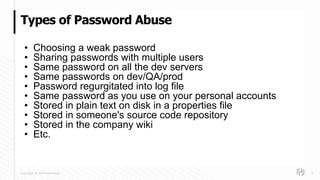
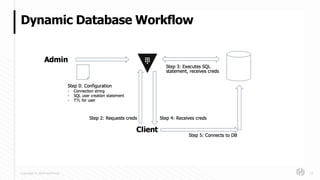
The document discusses HashiCorp's mission and products, emphasizing the need for secure management of credentials, particularly in the context of password abuse. It outlines various forms of password vulnerabilities and introduces HashiCorp Vault as a solution for managing dynamic database credentials. The content includes architectural details and a promotional angle for the company's offerings.