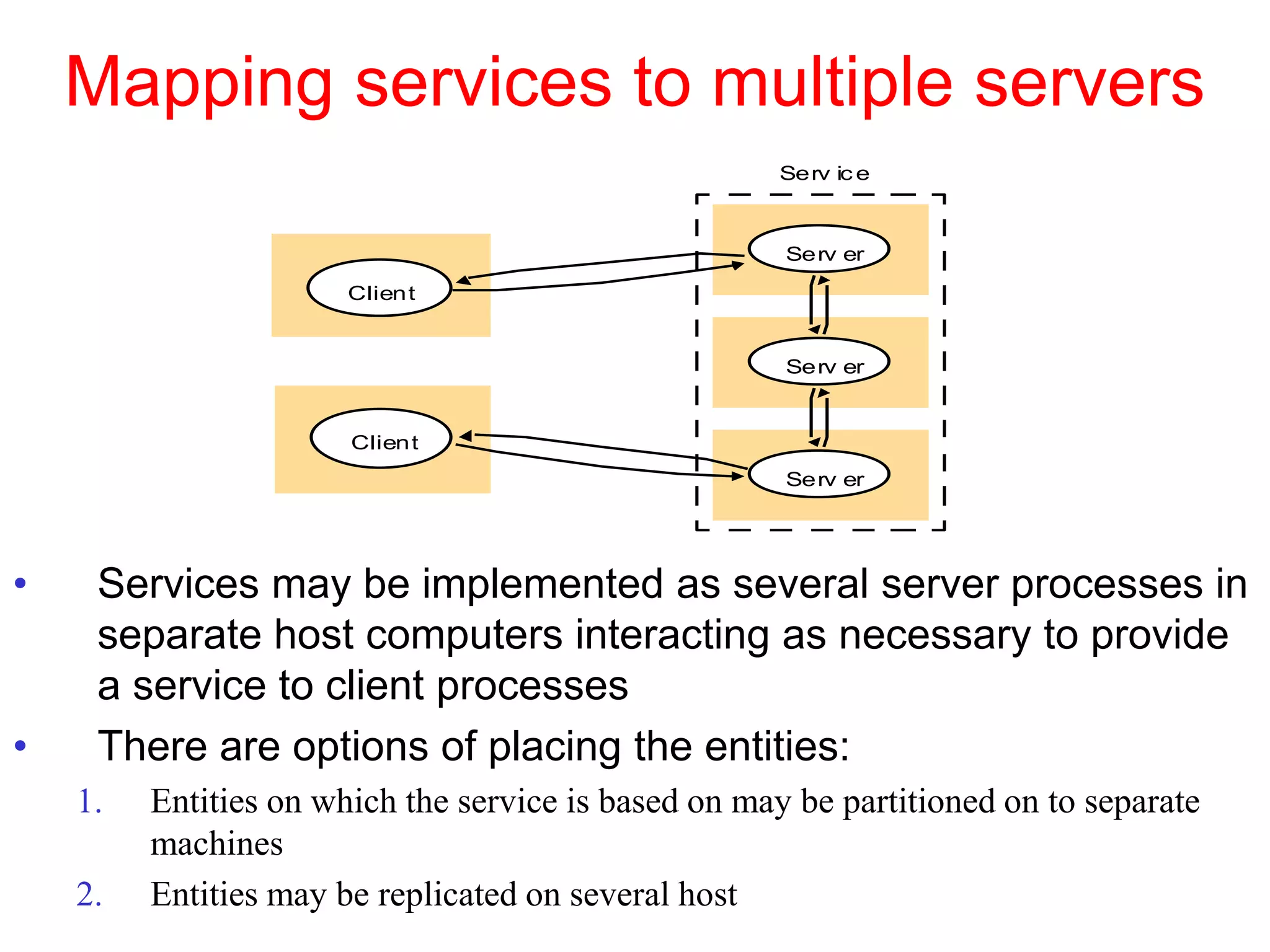
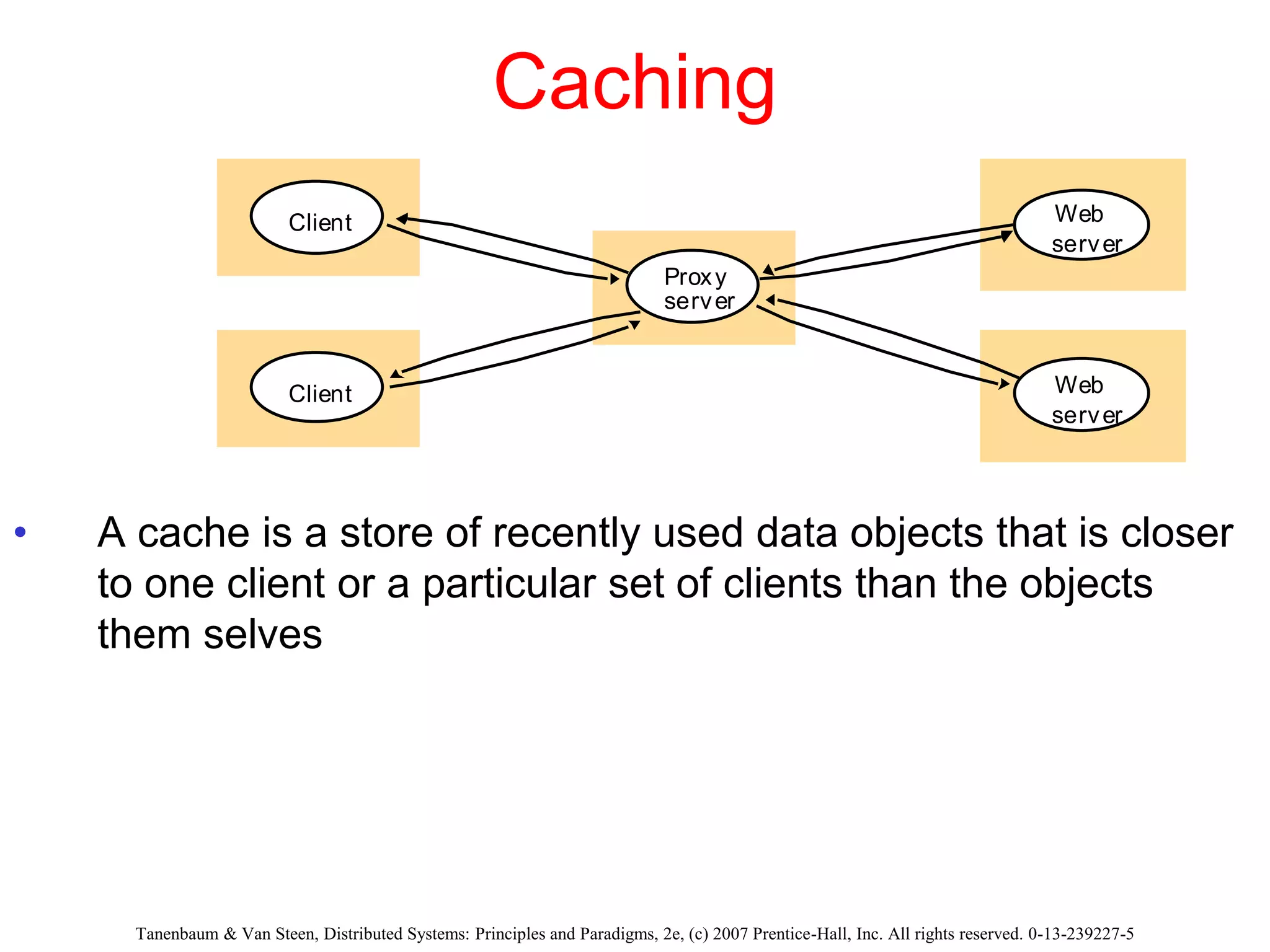
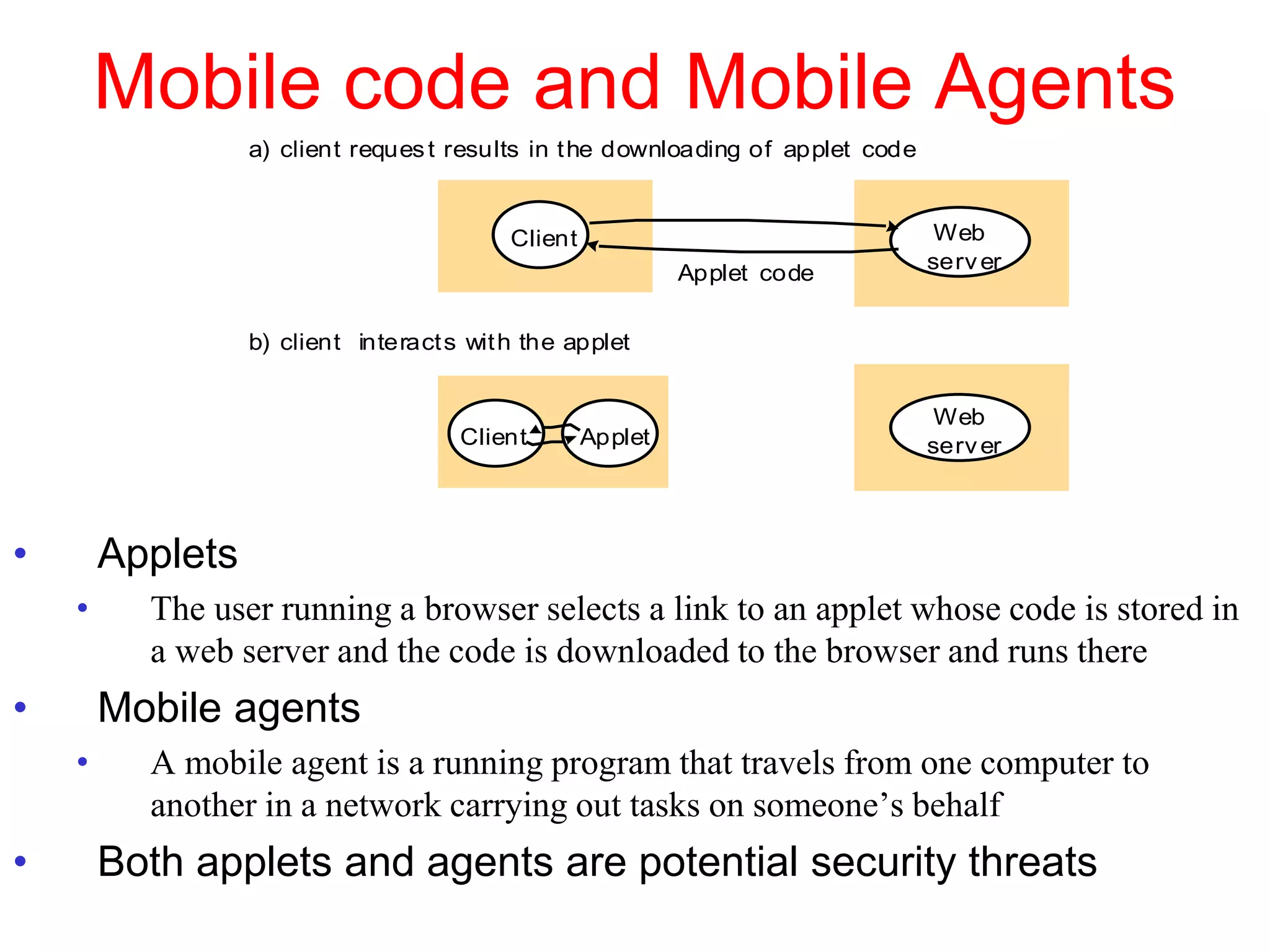
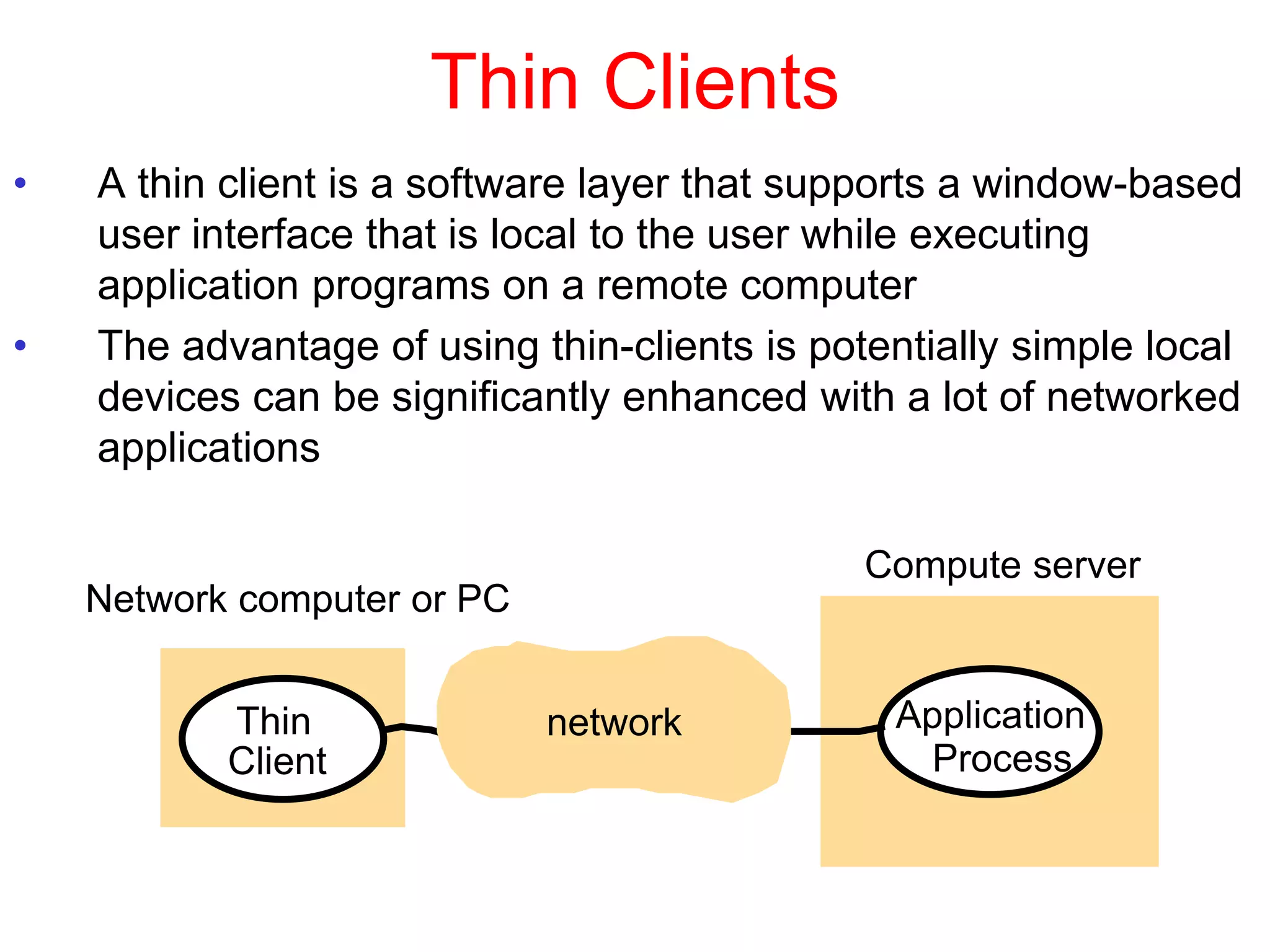
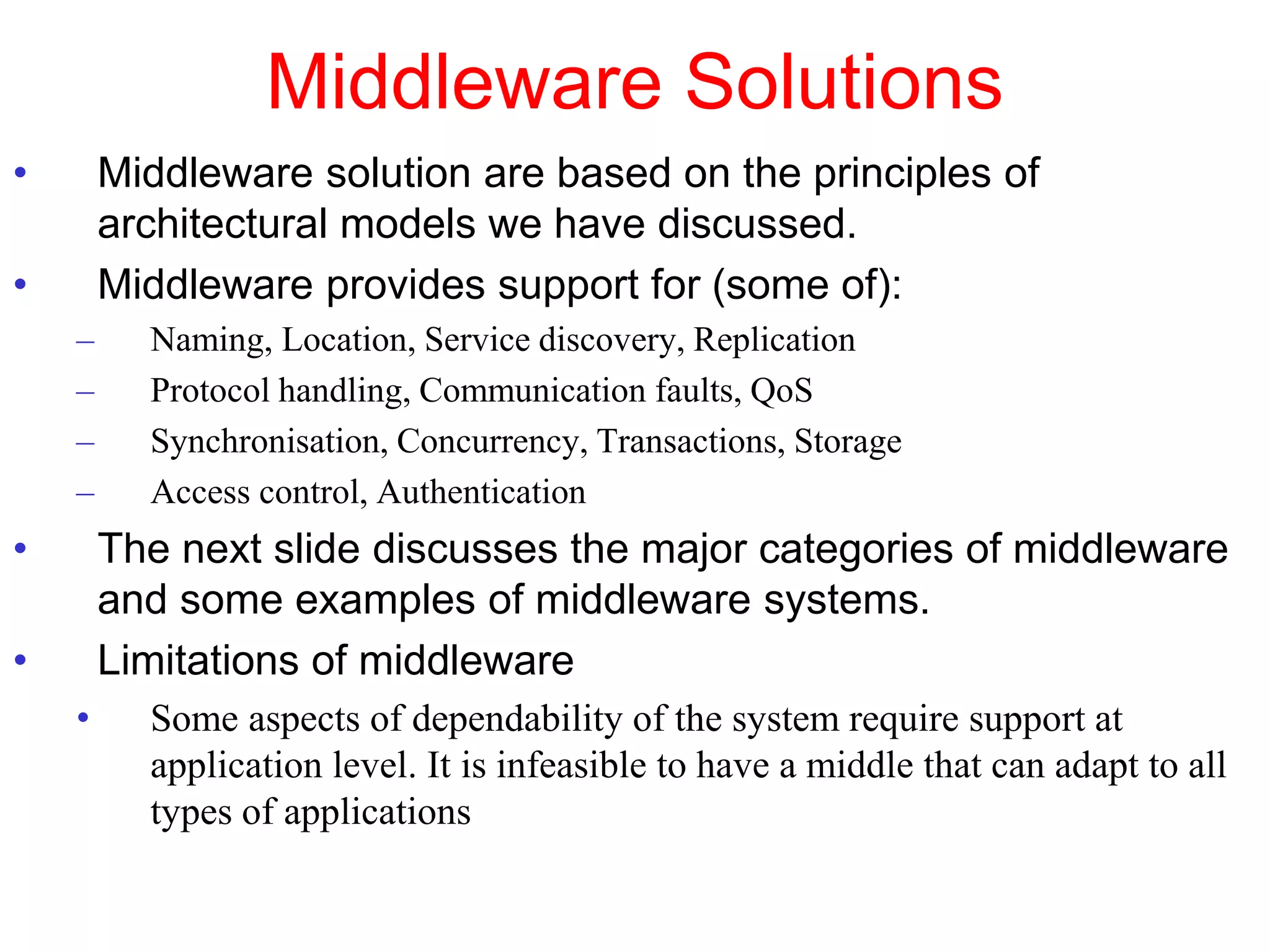
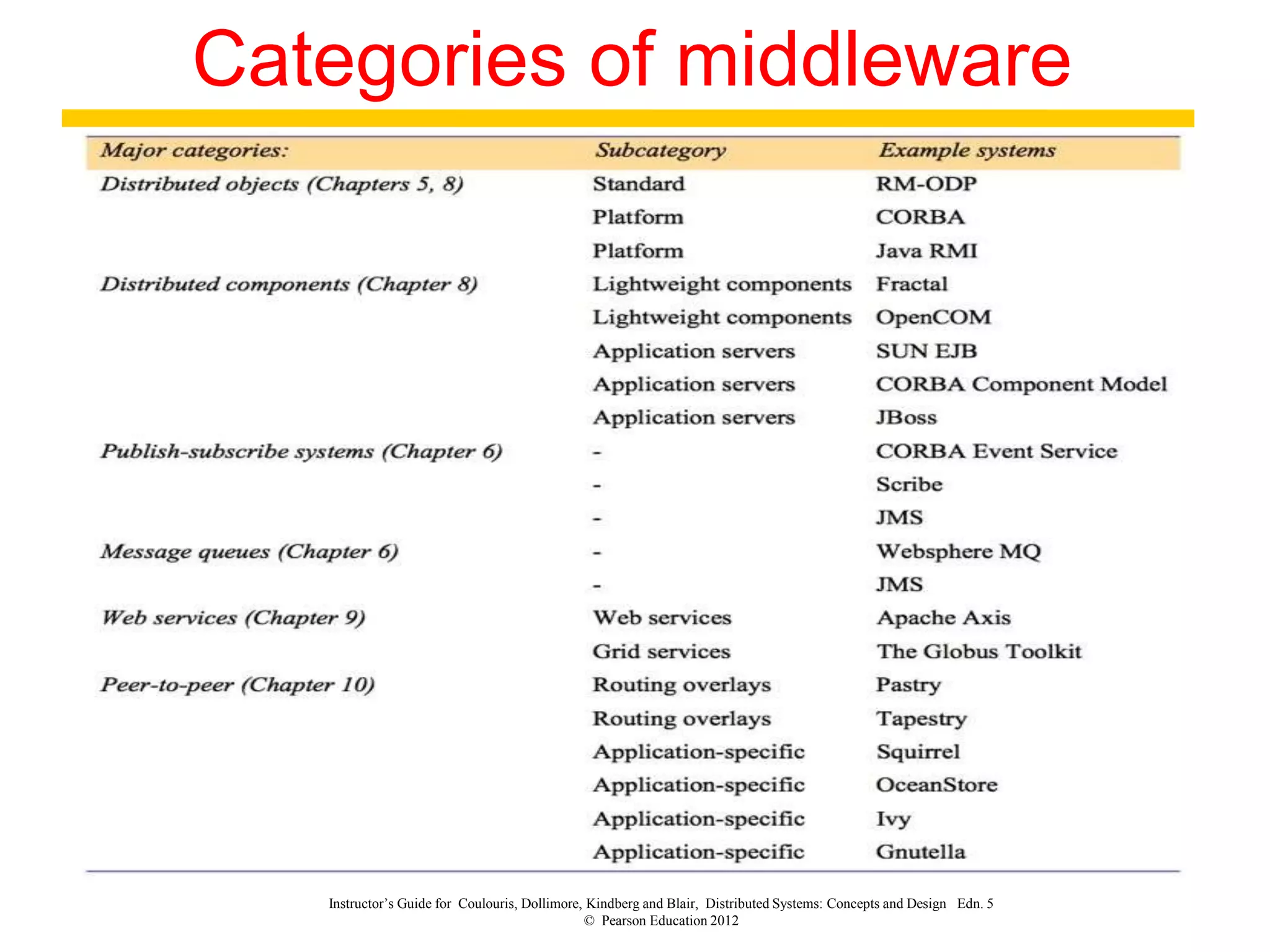
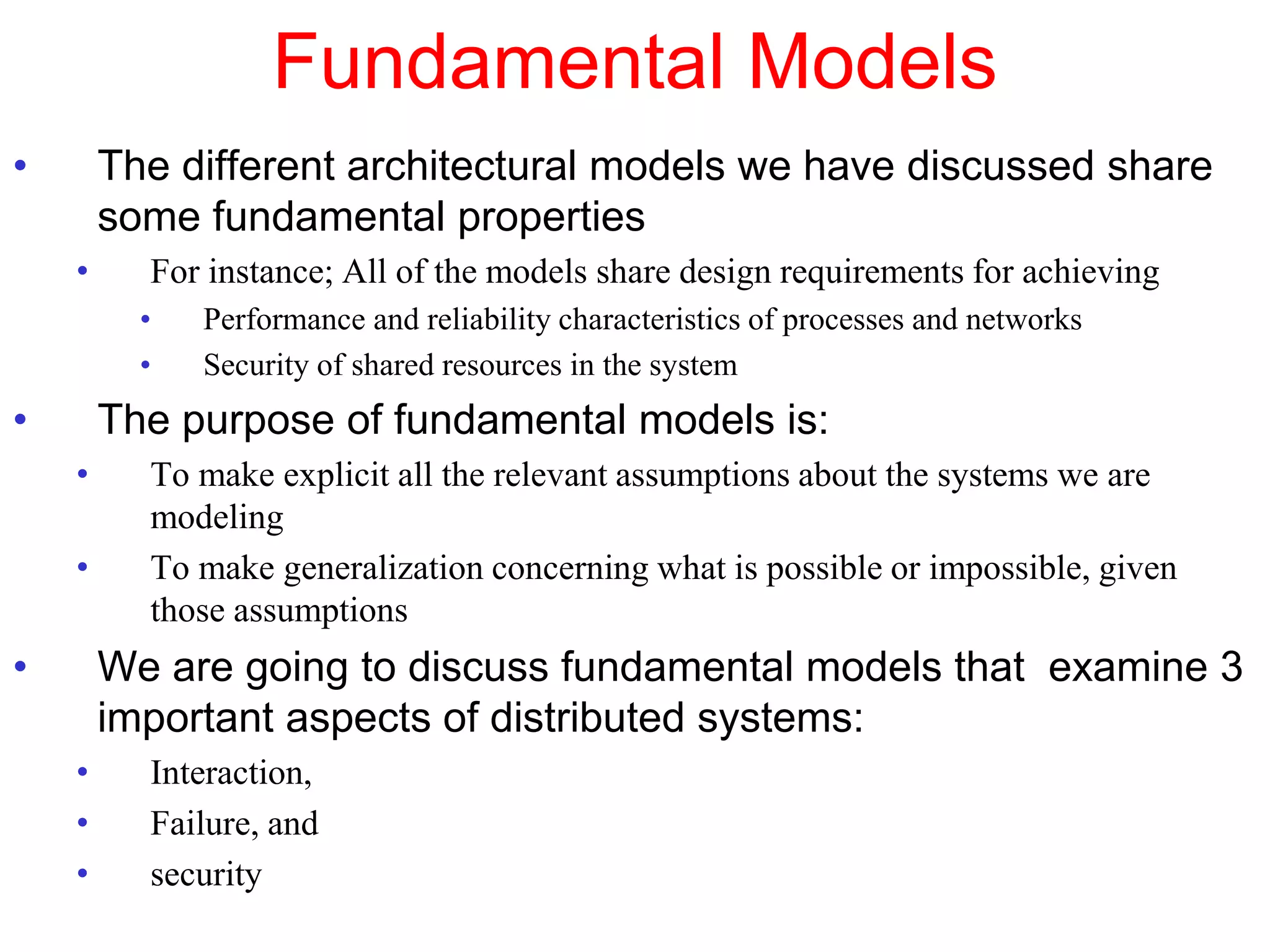
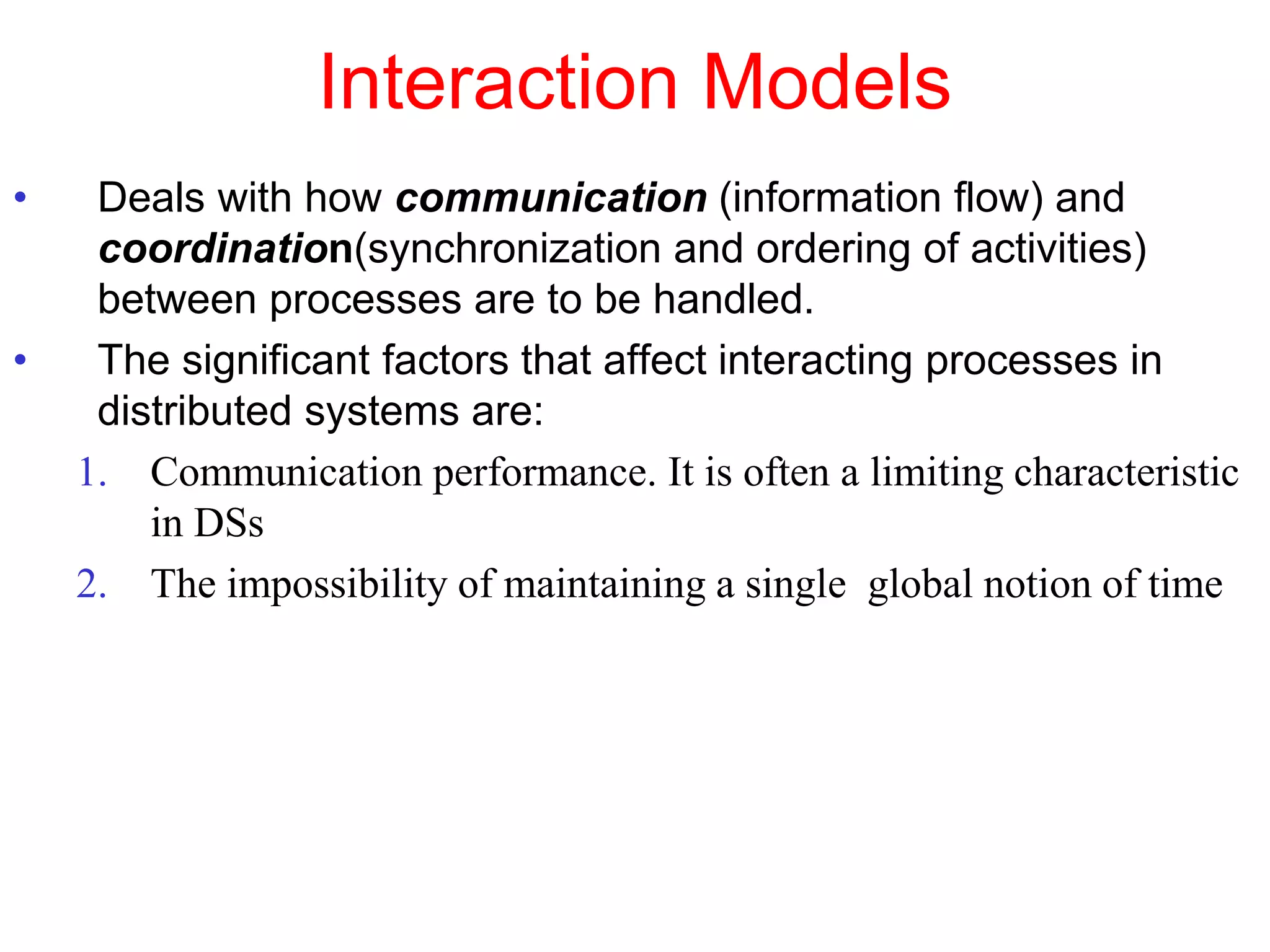
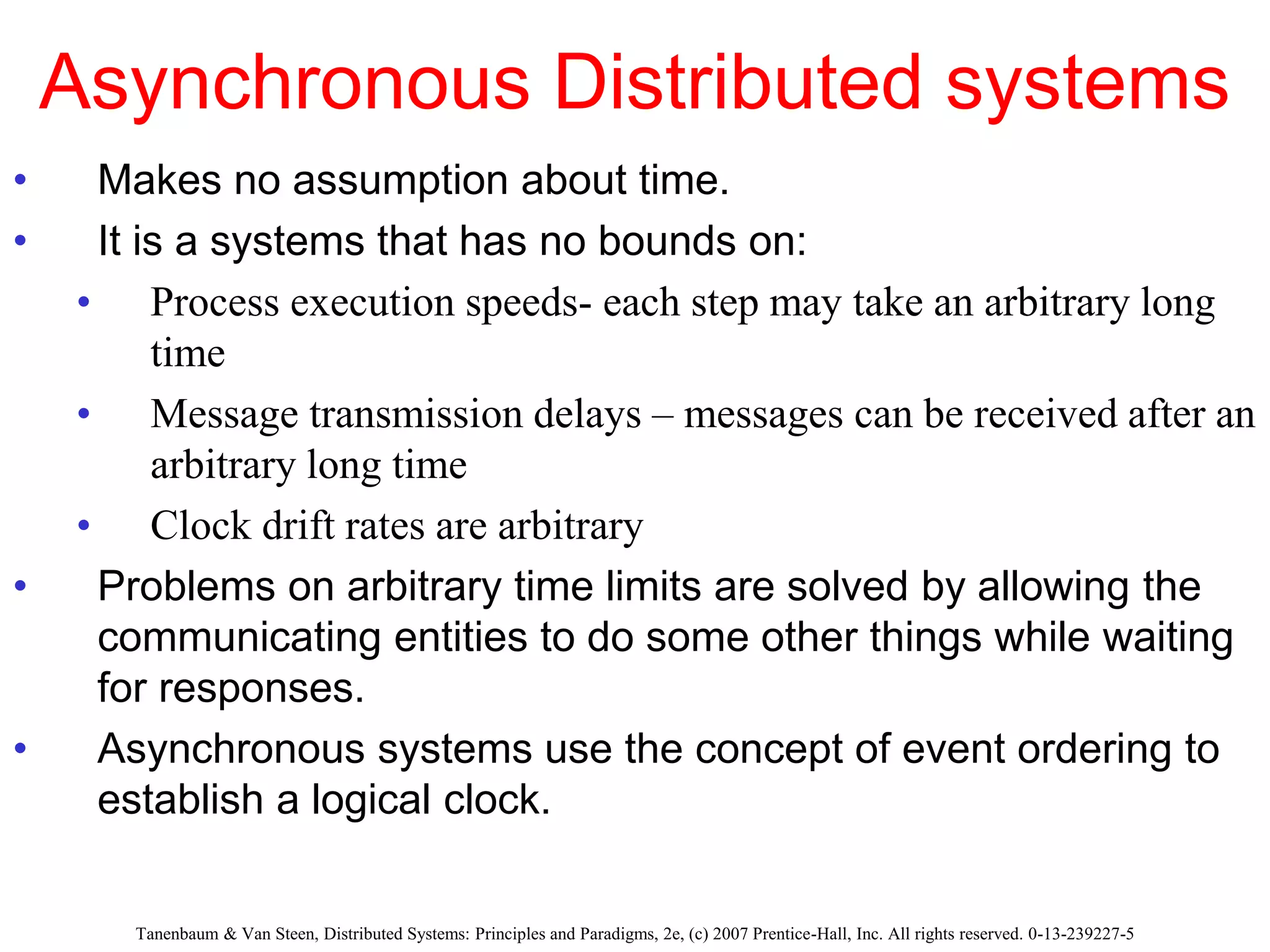
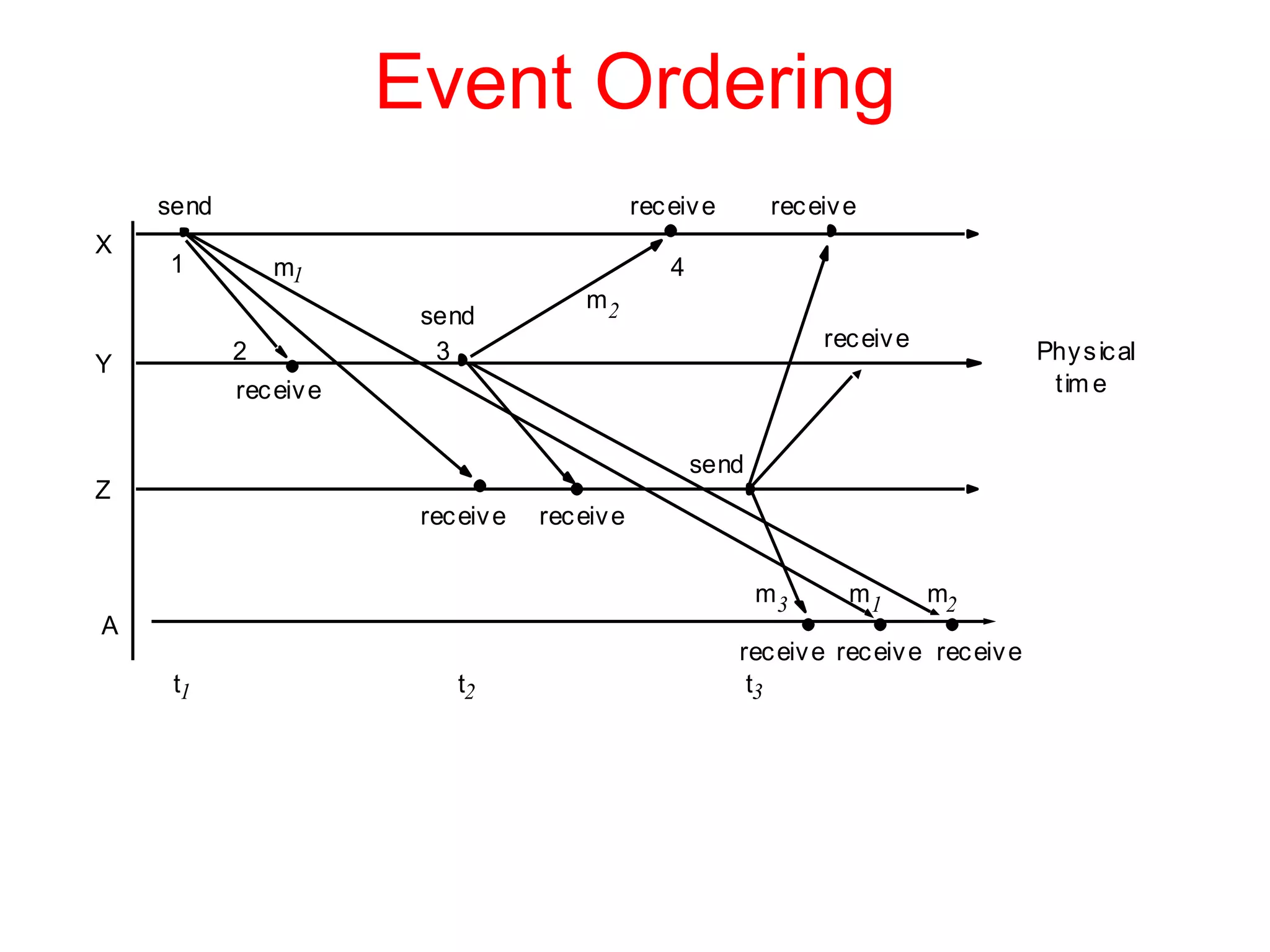
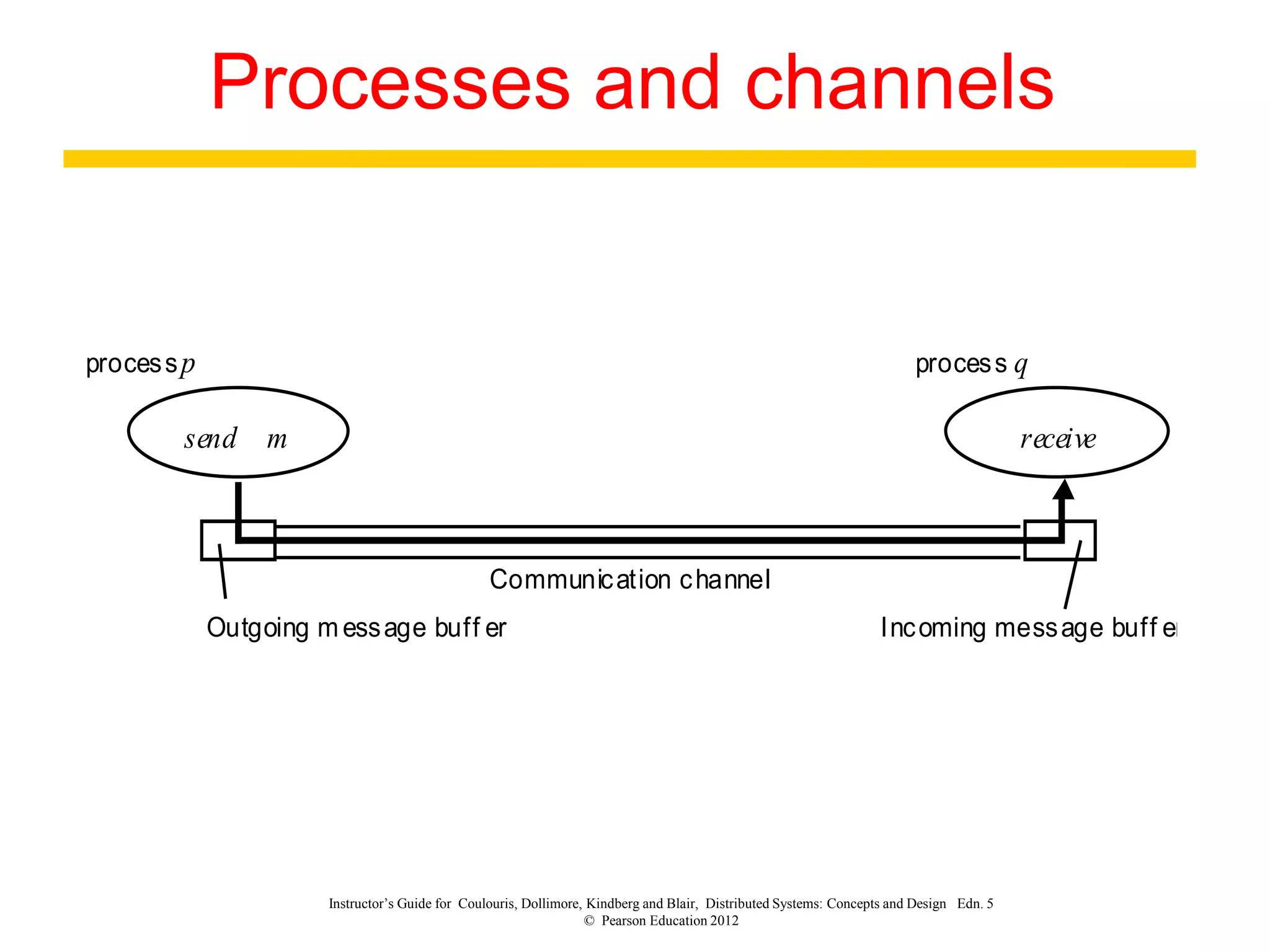
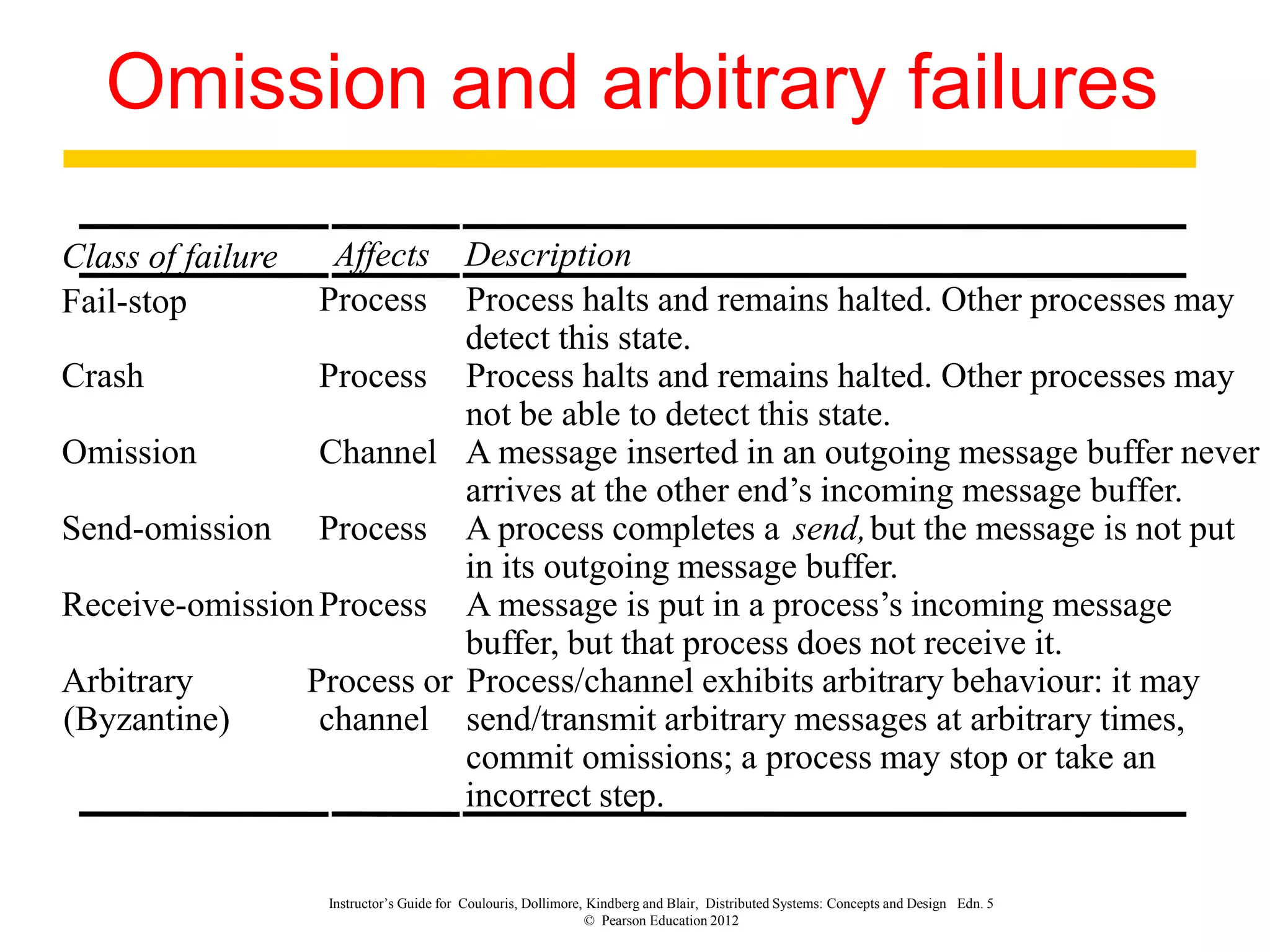
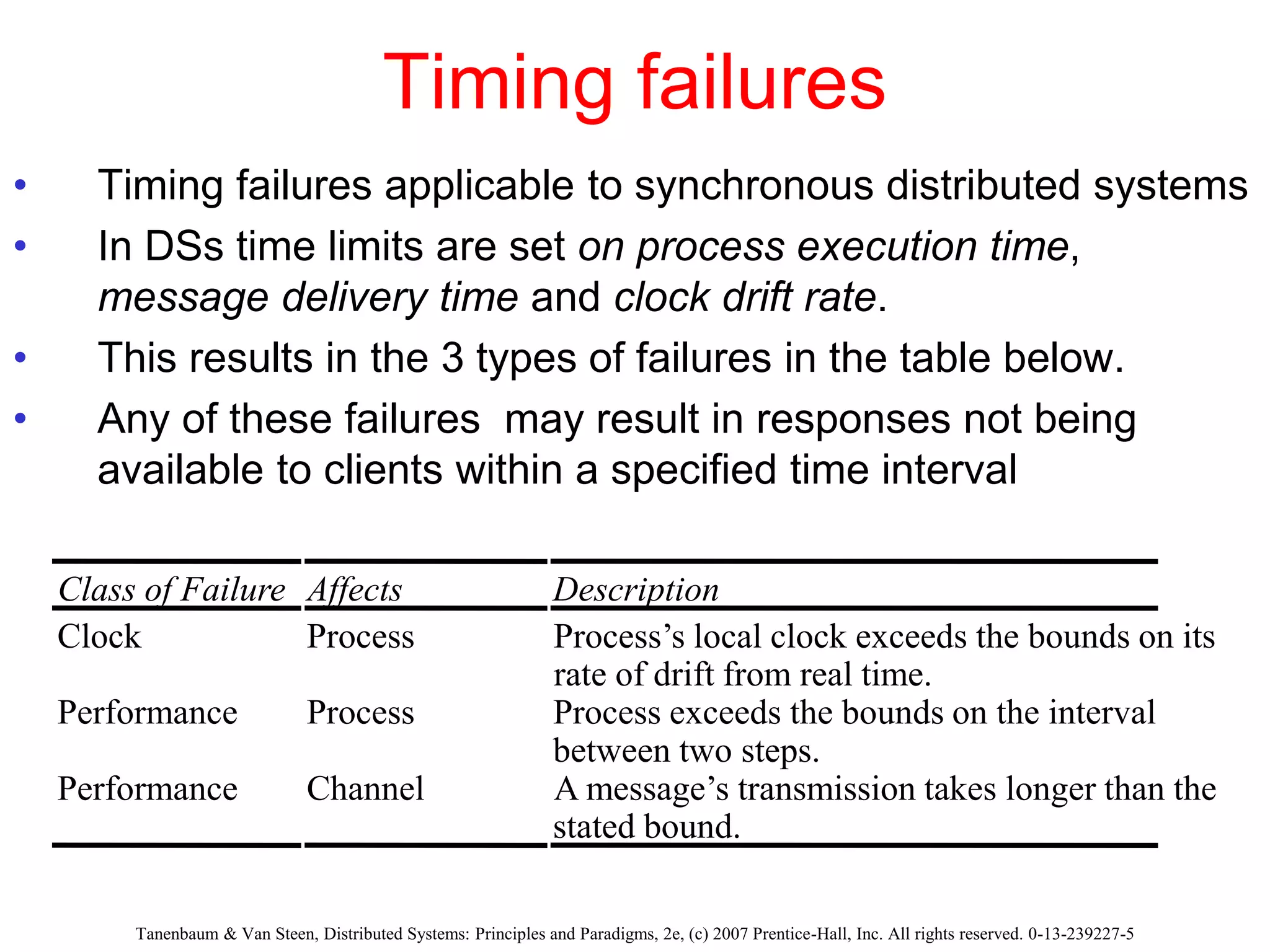
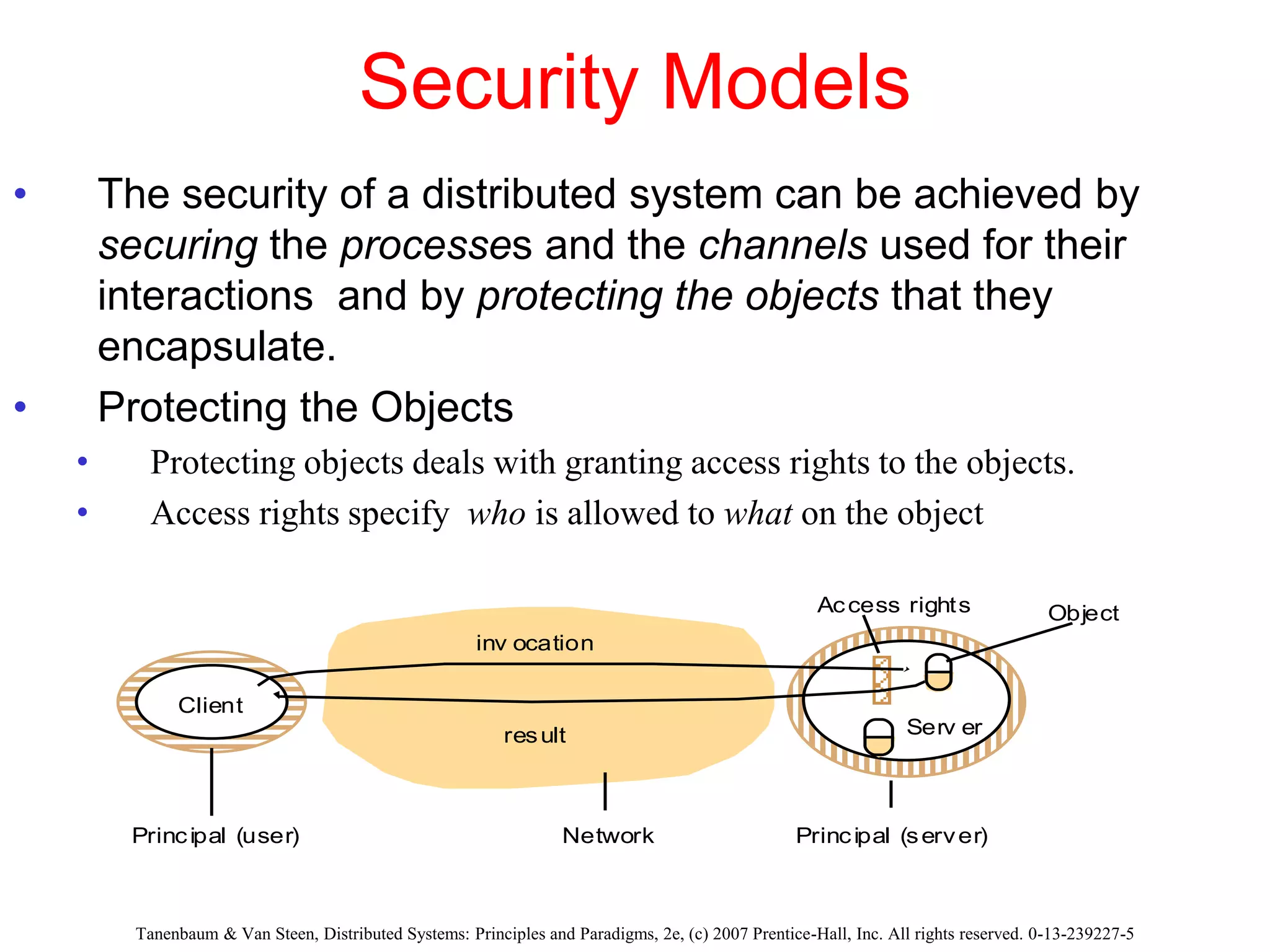
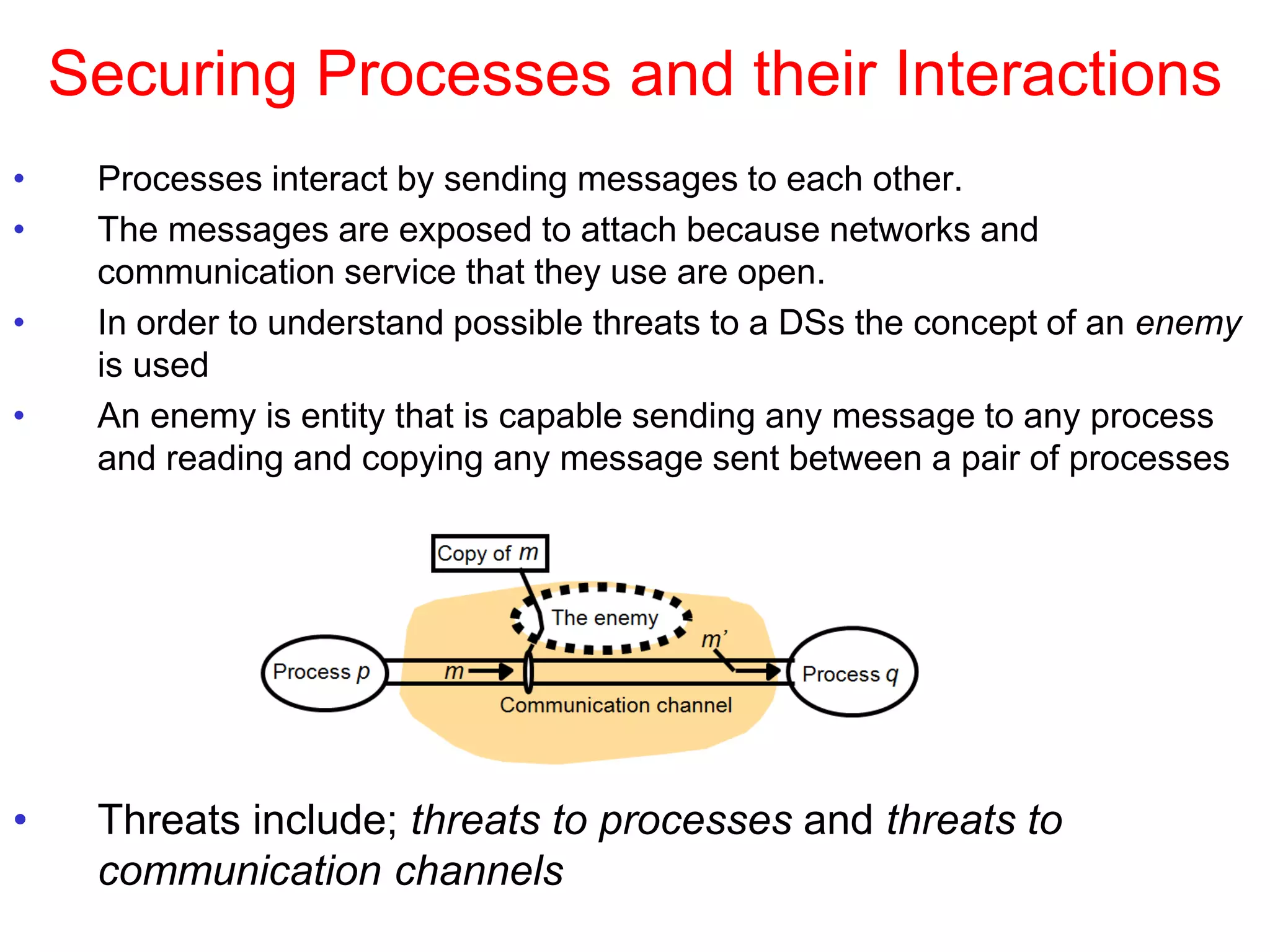
1. The document discusses various models for distributed systems including physical, architectural, and fundamental models.
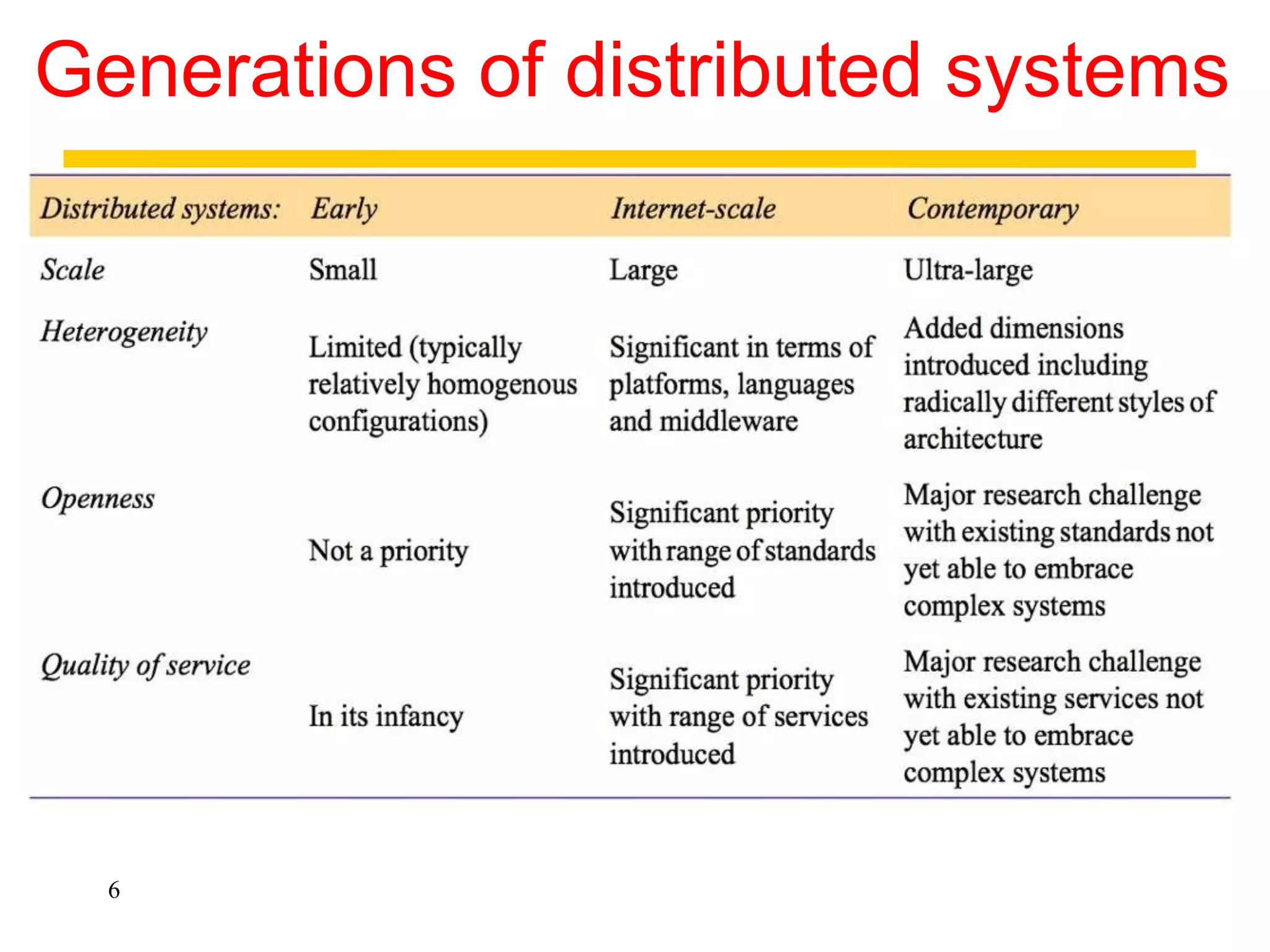
2. Physical models describe the hardware components and network connections. Architectural models capture the computational elements and communication tasks. Fundamental models take an abstract view of key aspects like interaction and failure.
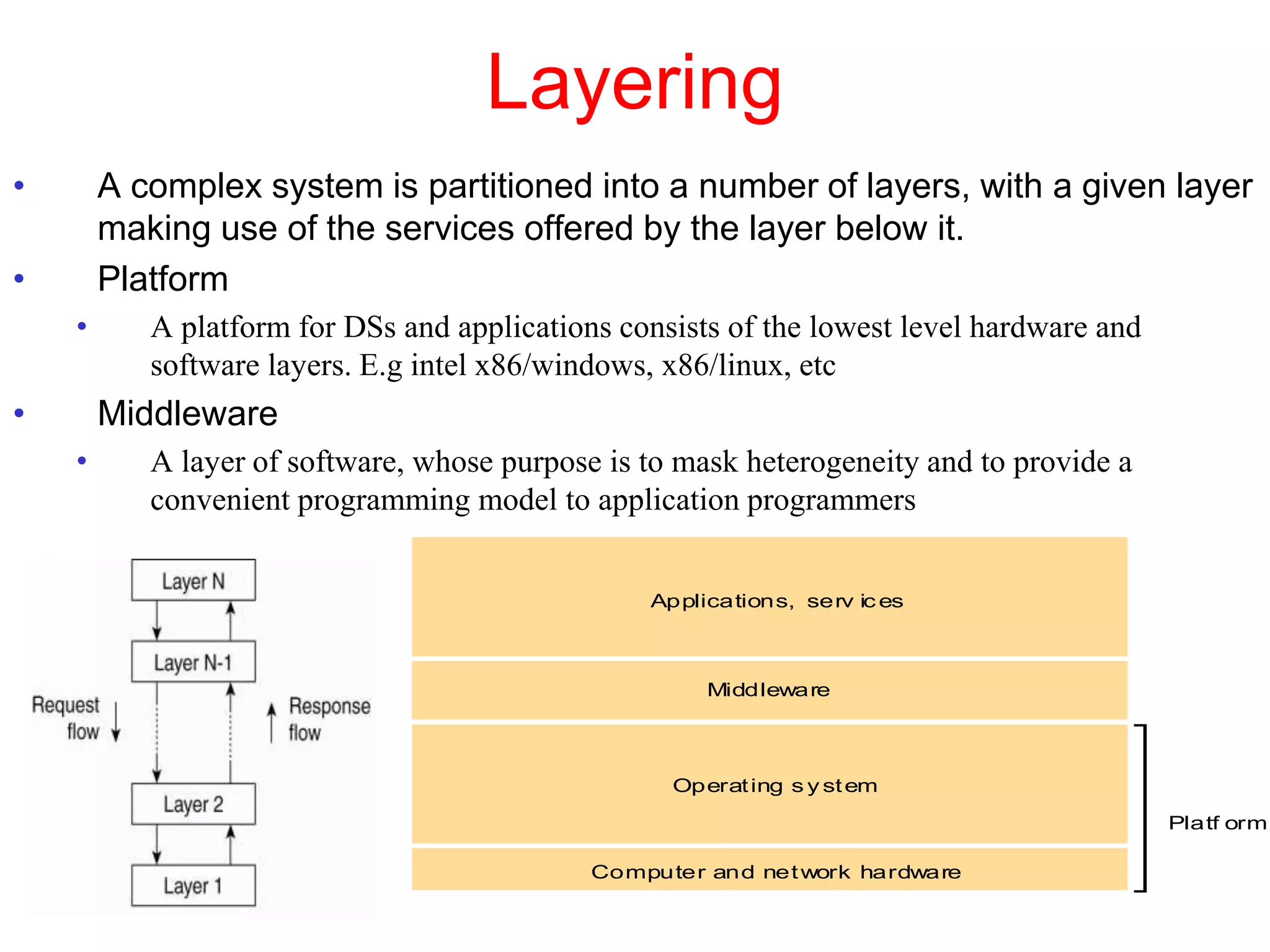
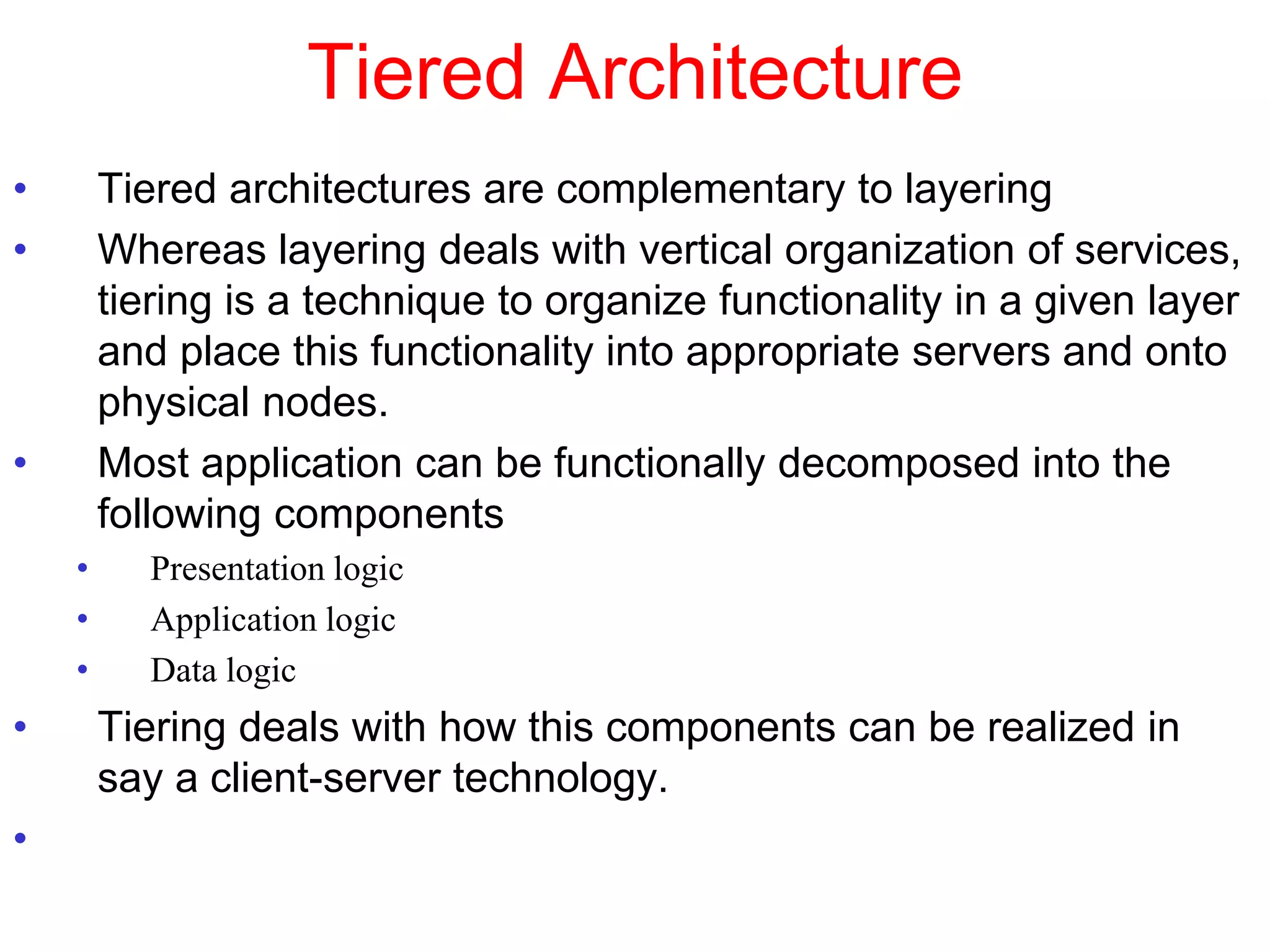
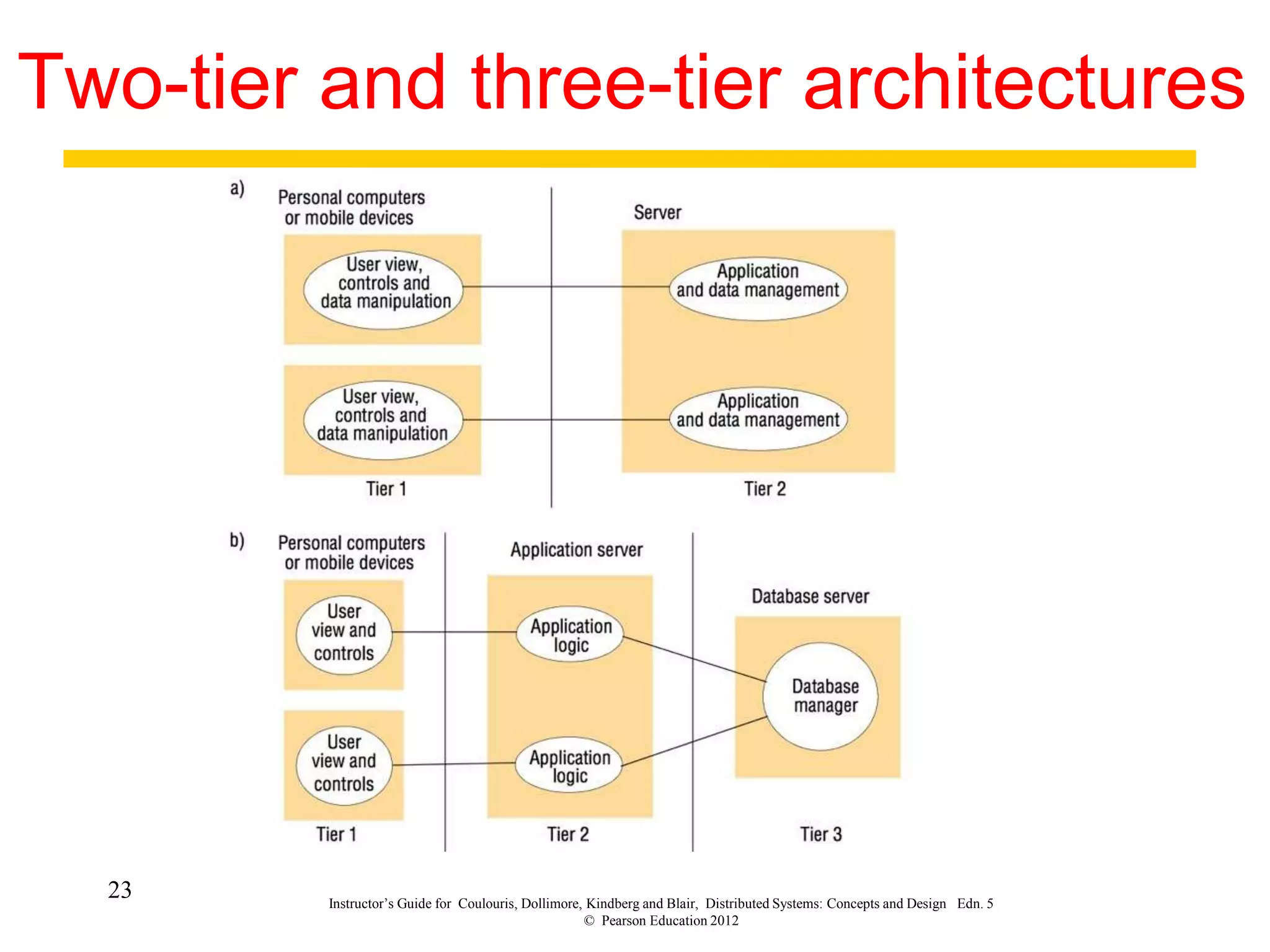
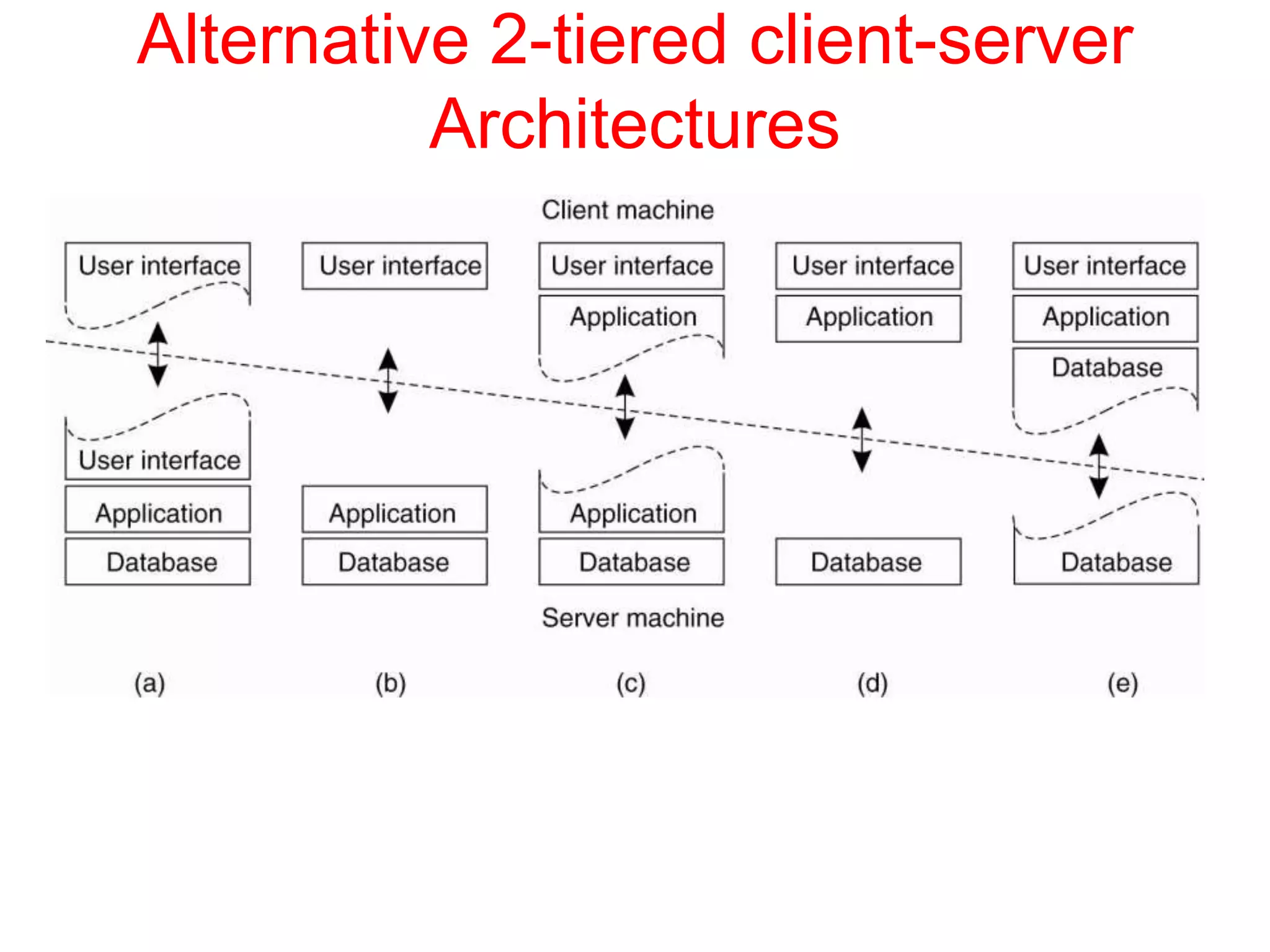
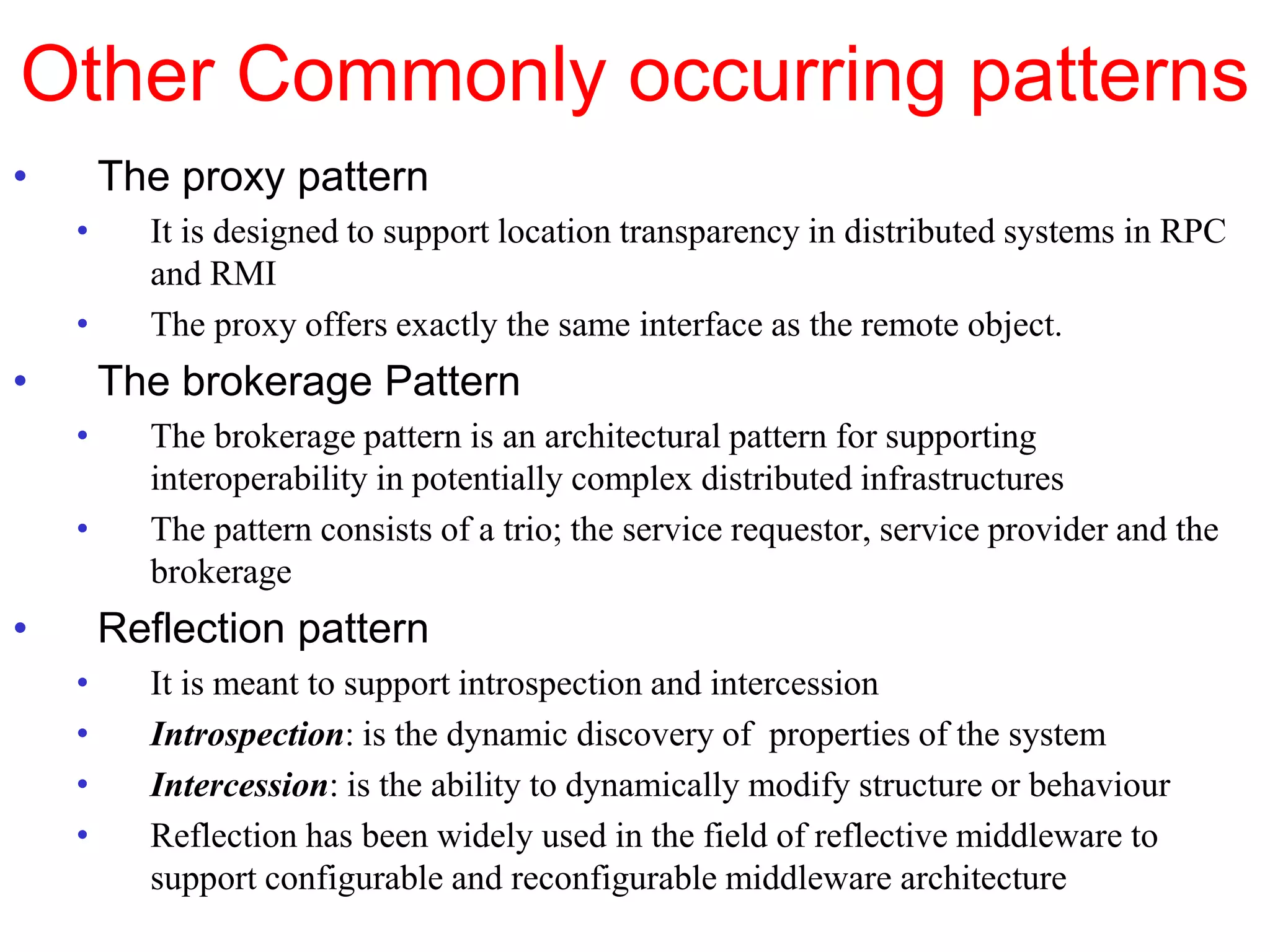
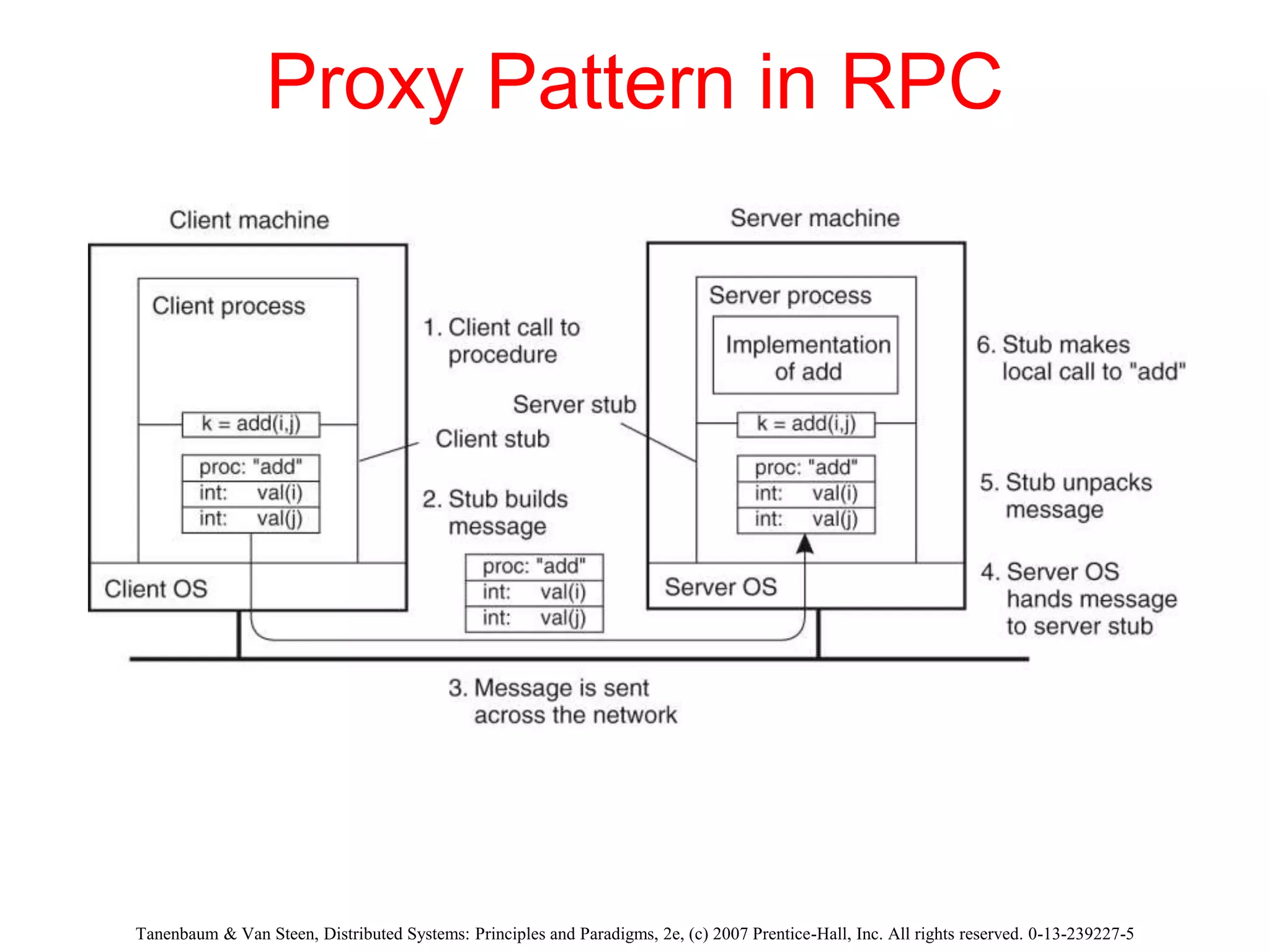
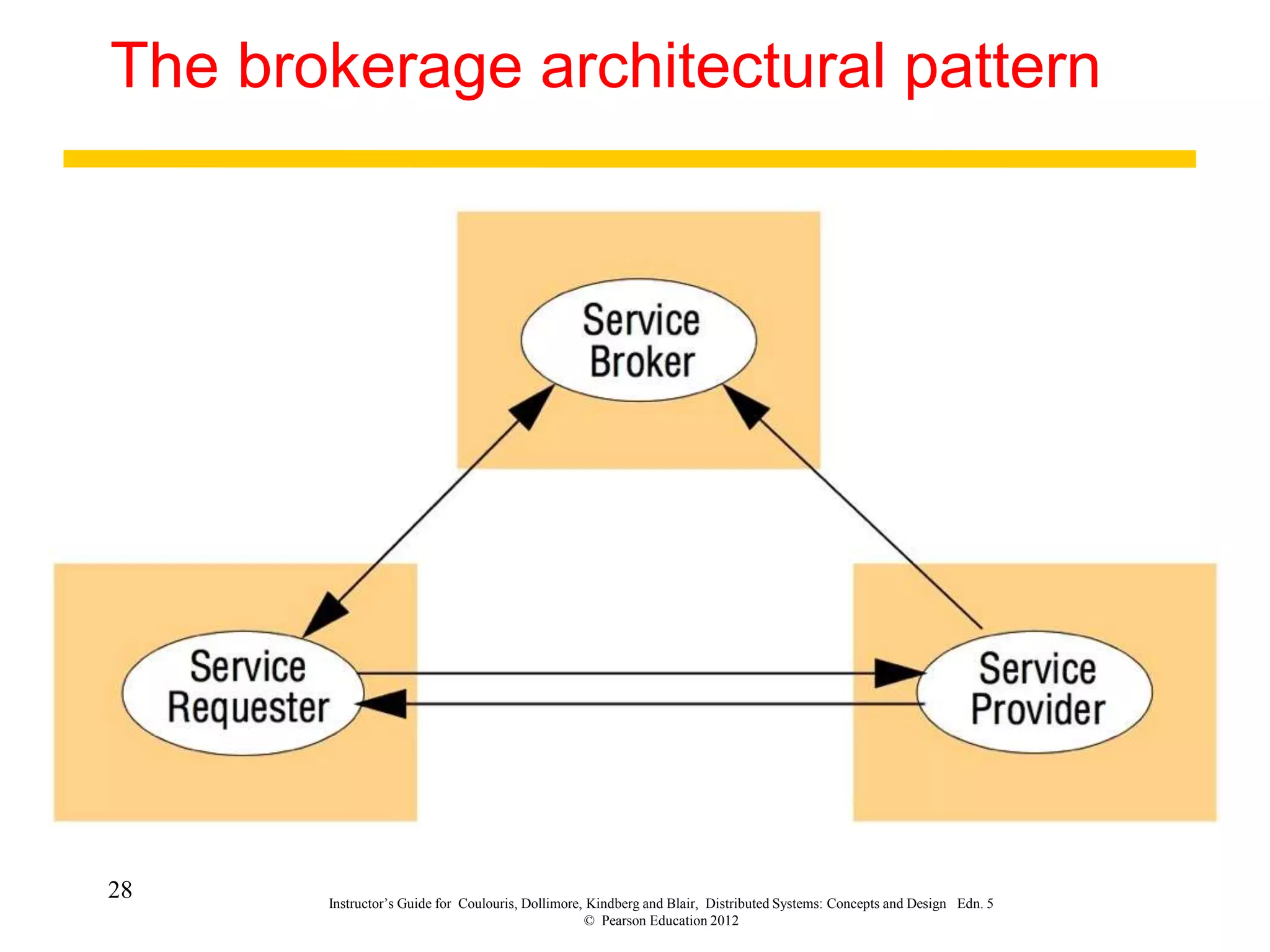
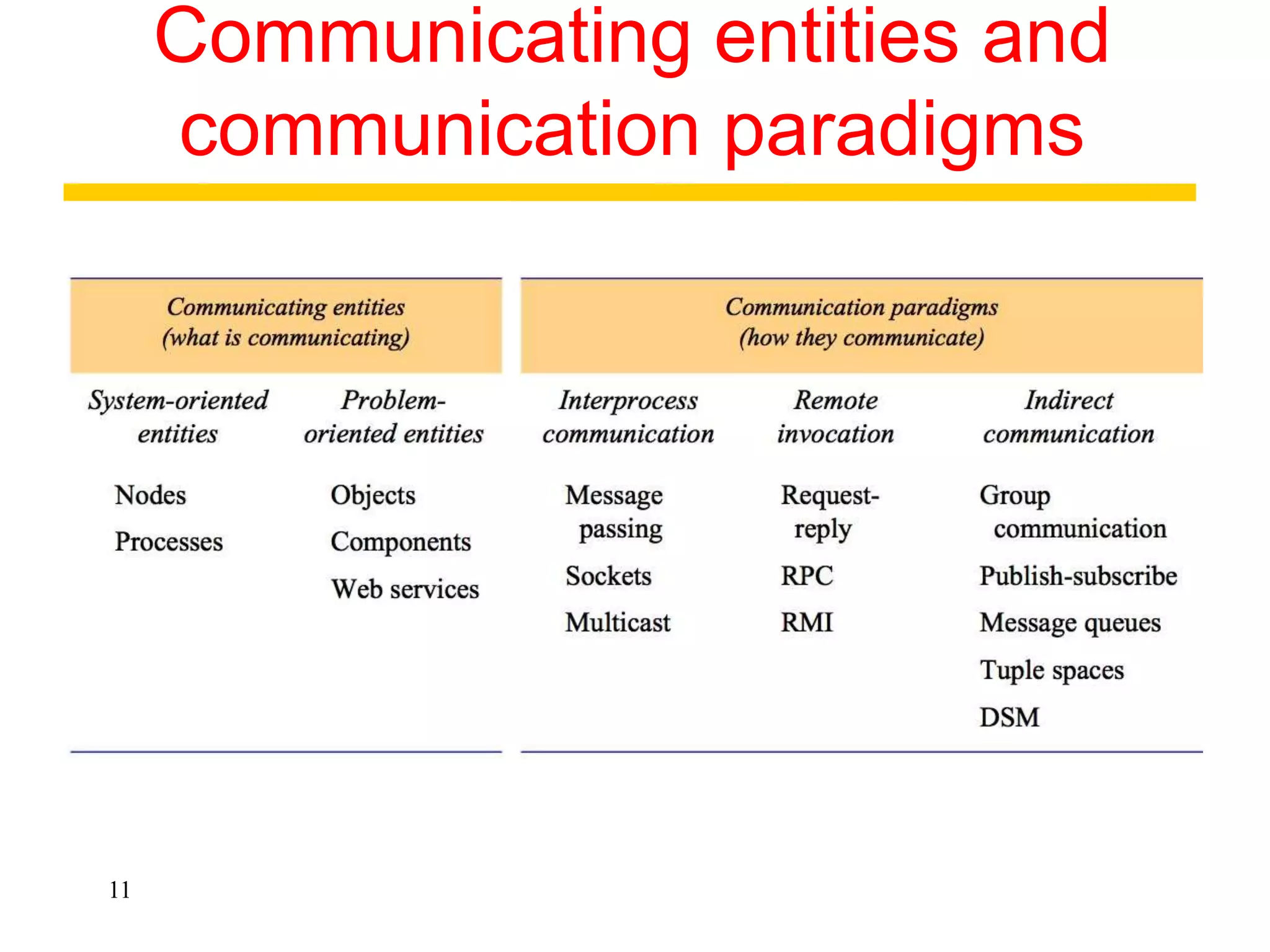
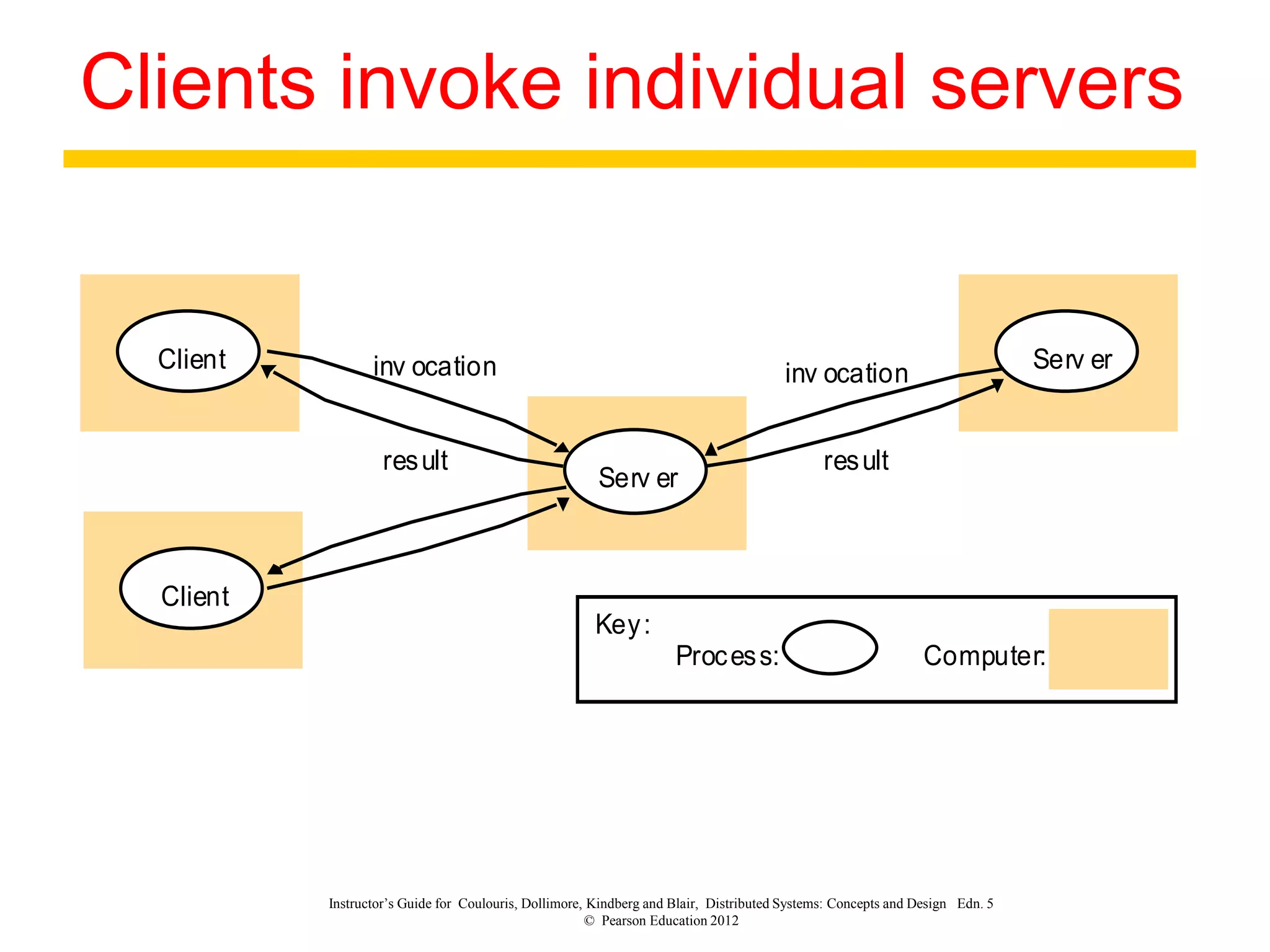
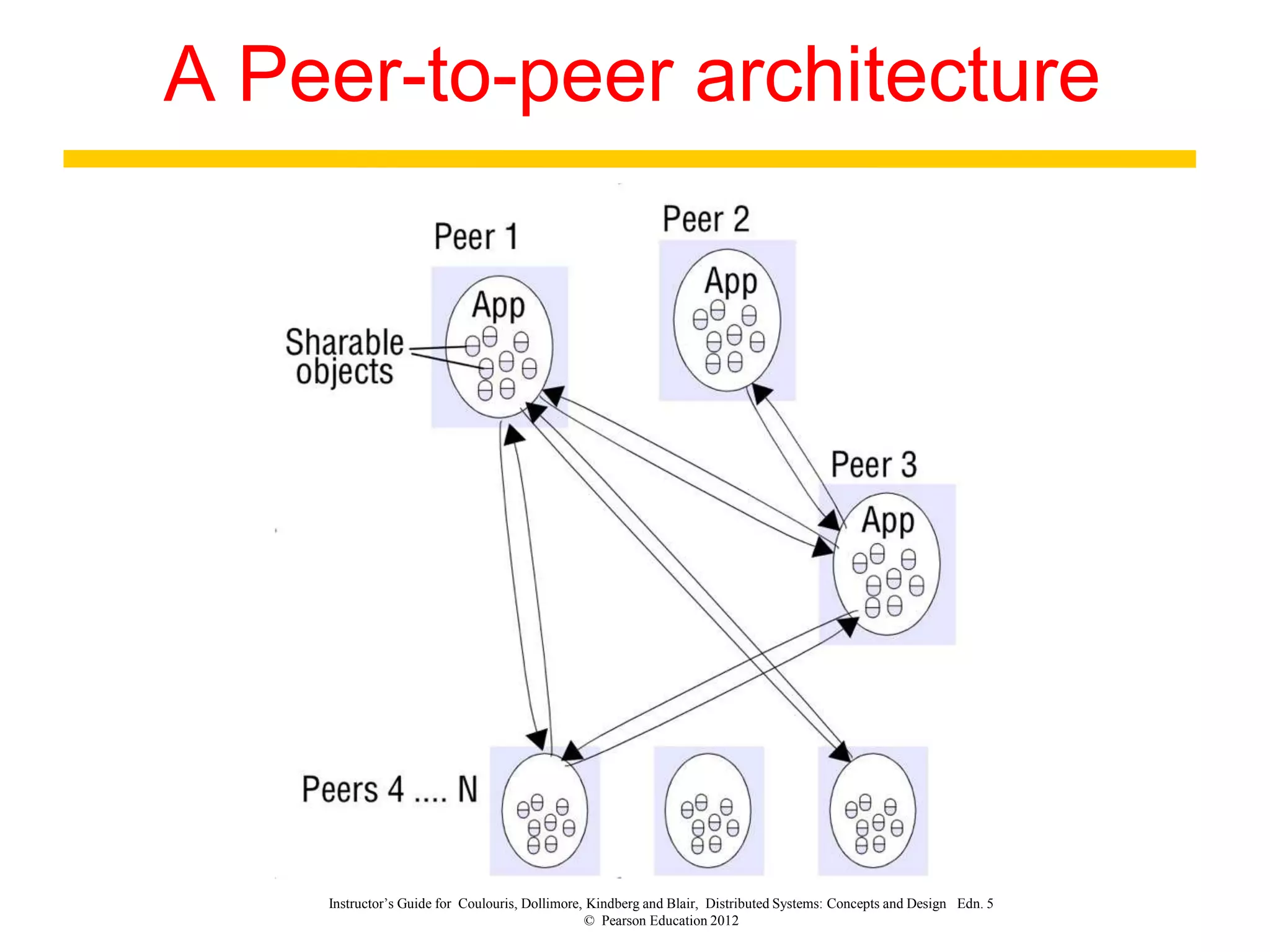
3. Key architectural elements include communicating entities, communication paradigms, roles and responsibilities, and placement strategies. Common patterns are also described like layering, tiered architectures, and proxies.




![Tanenbaum & Van Steen, Distributed Systems: Principles and Paradigms, 2e, (c) 2007 Prentice-Hall, Inc. All rights reserved. 0-13-239227-5
An example P2P system
The principal working of BitTorrent [Pouwelse et al. (2004)].](https://image.slidesharecdn.com/dschap-02-220818085918-7e538a1e/75/DSchap-02-ppt-15-2048.jpg)