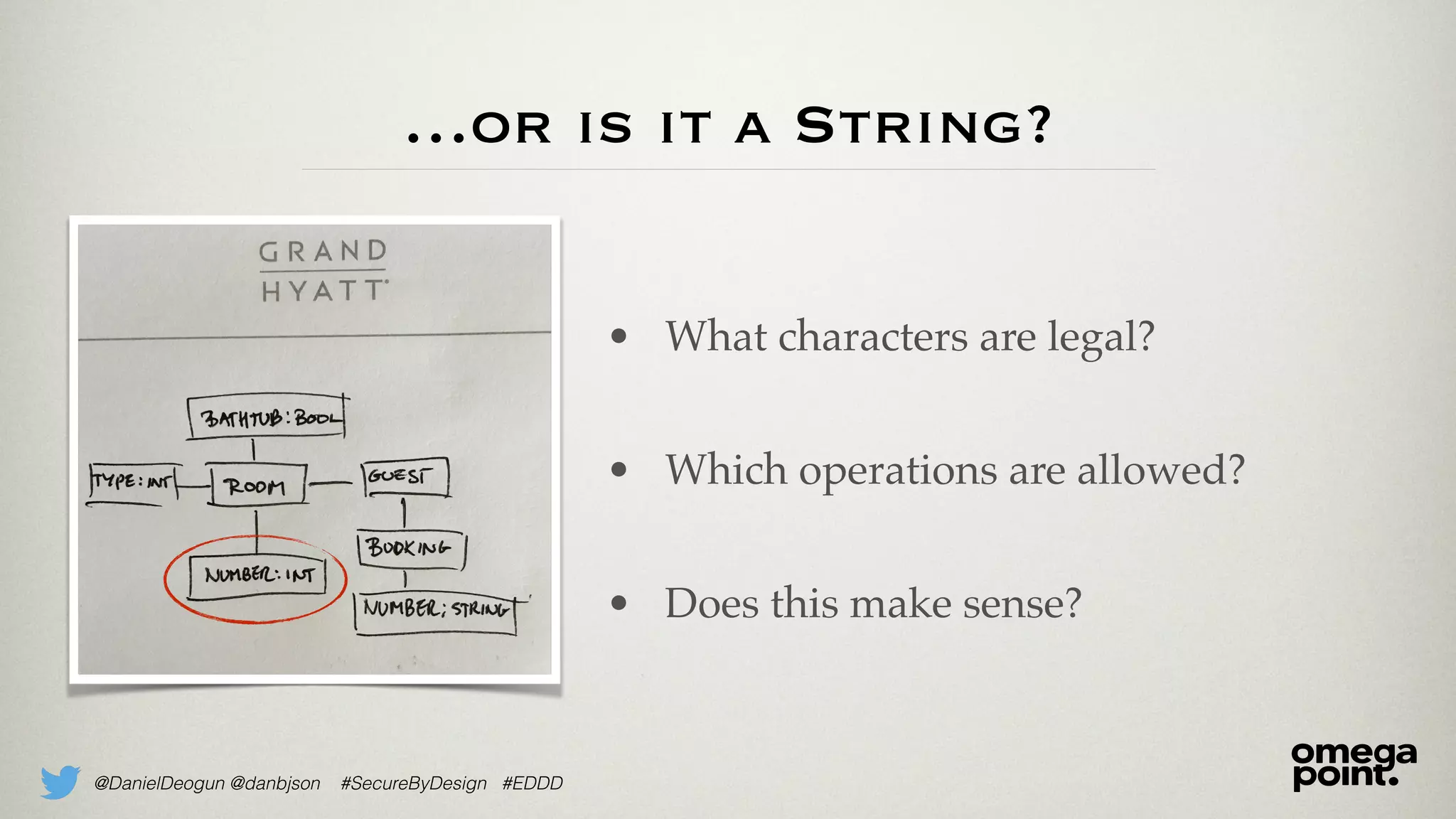
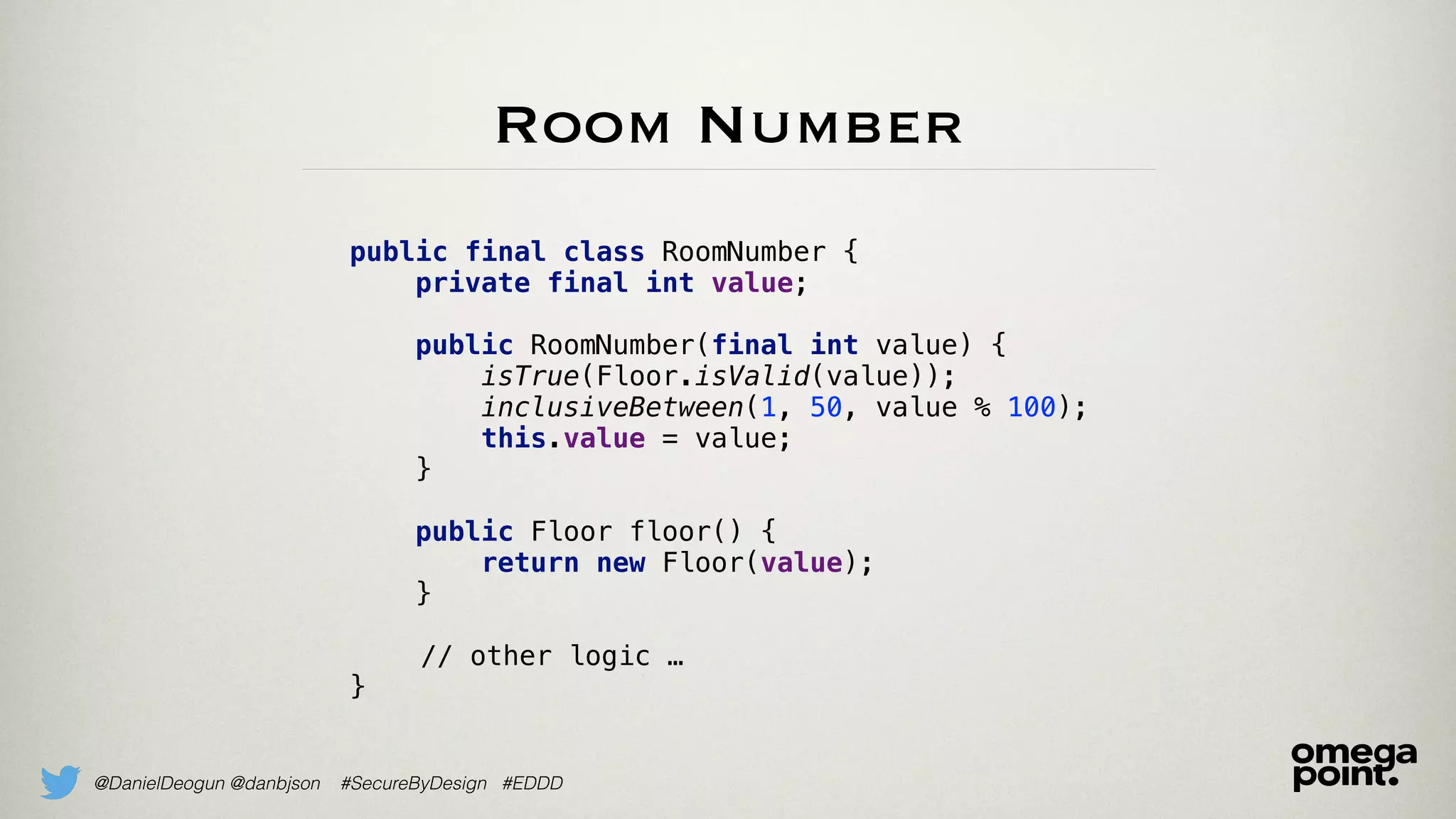
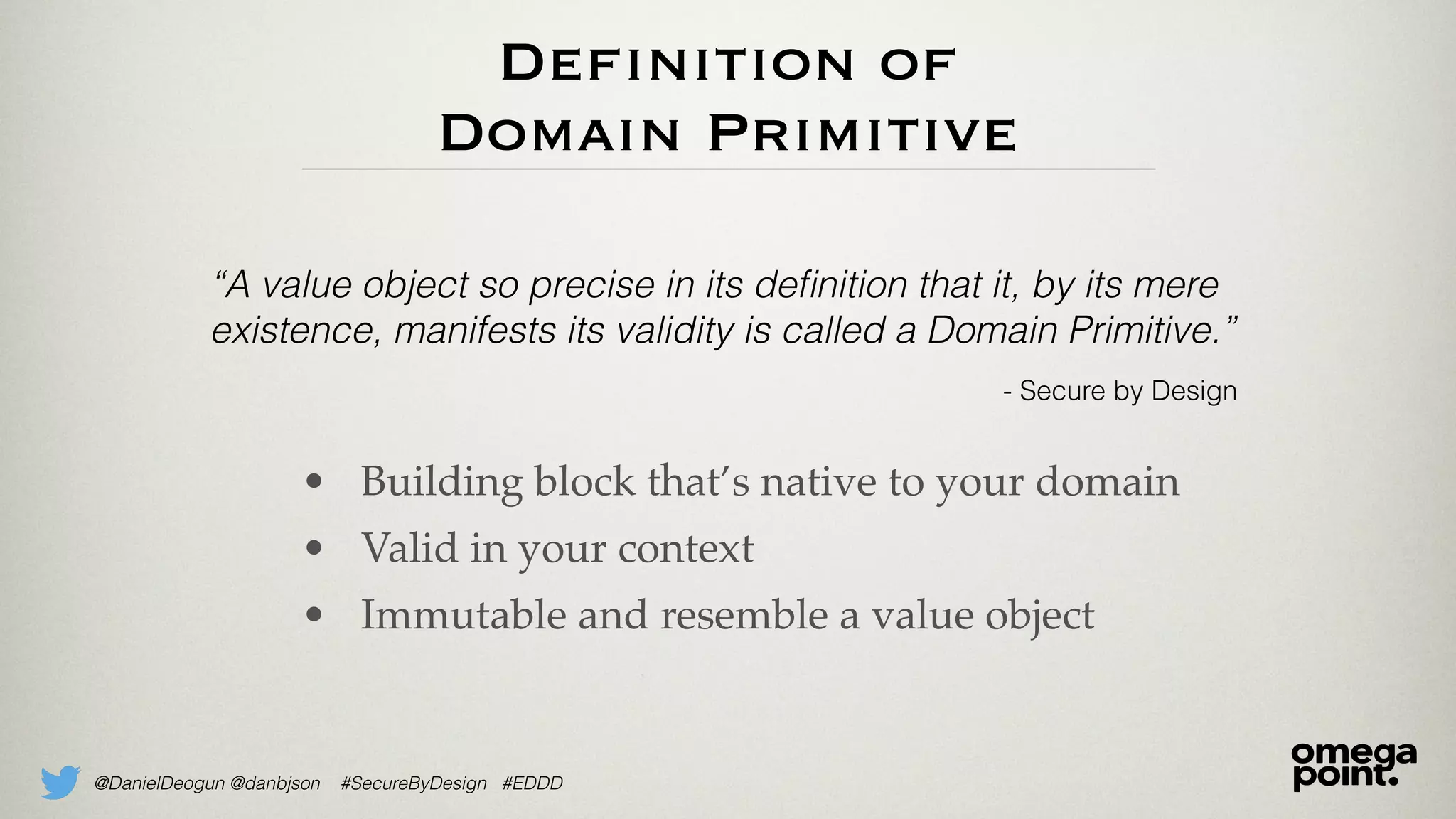
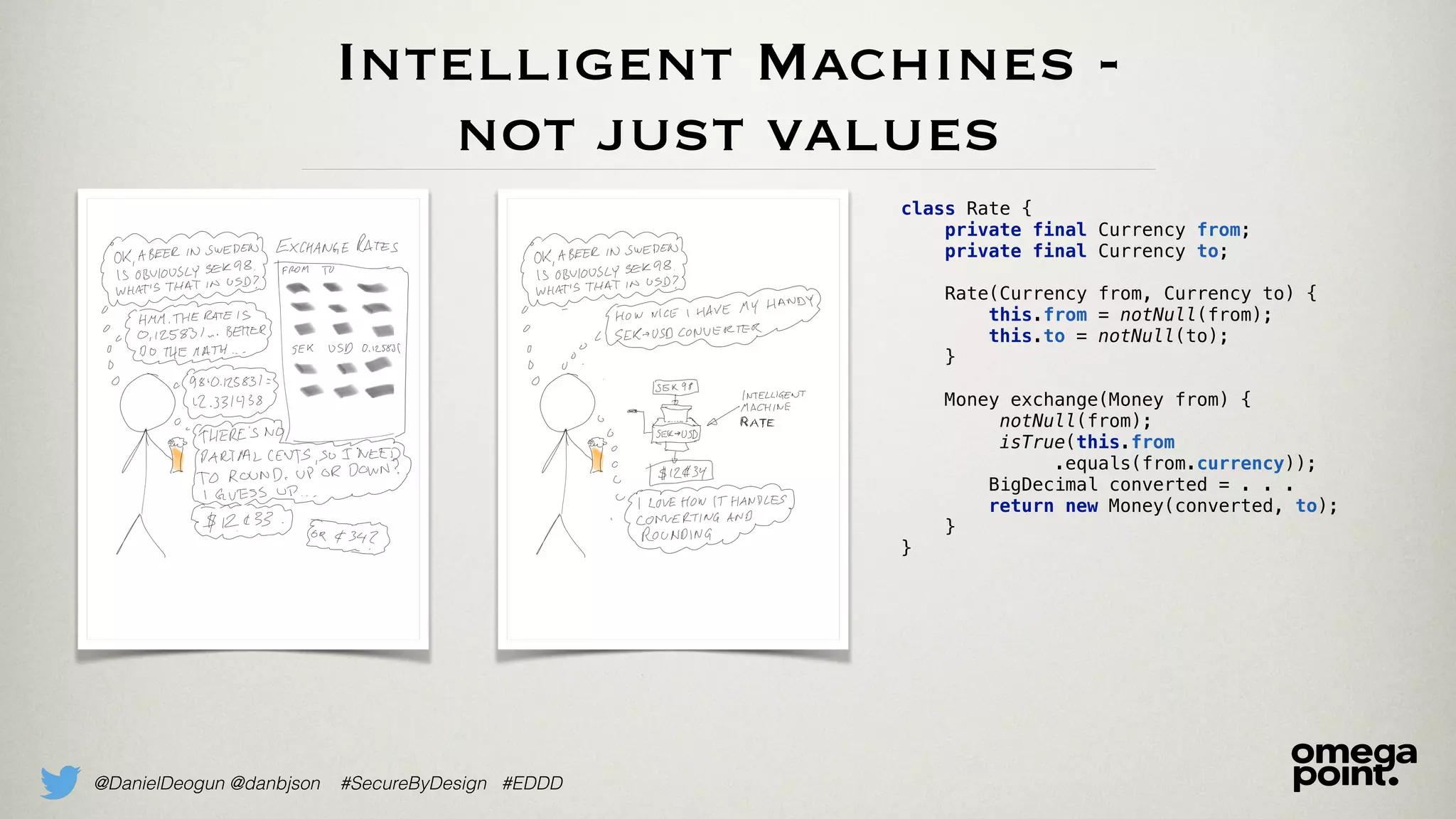
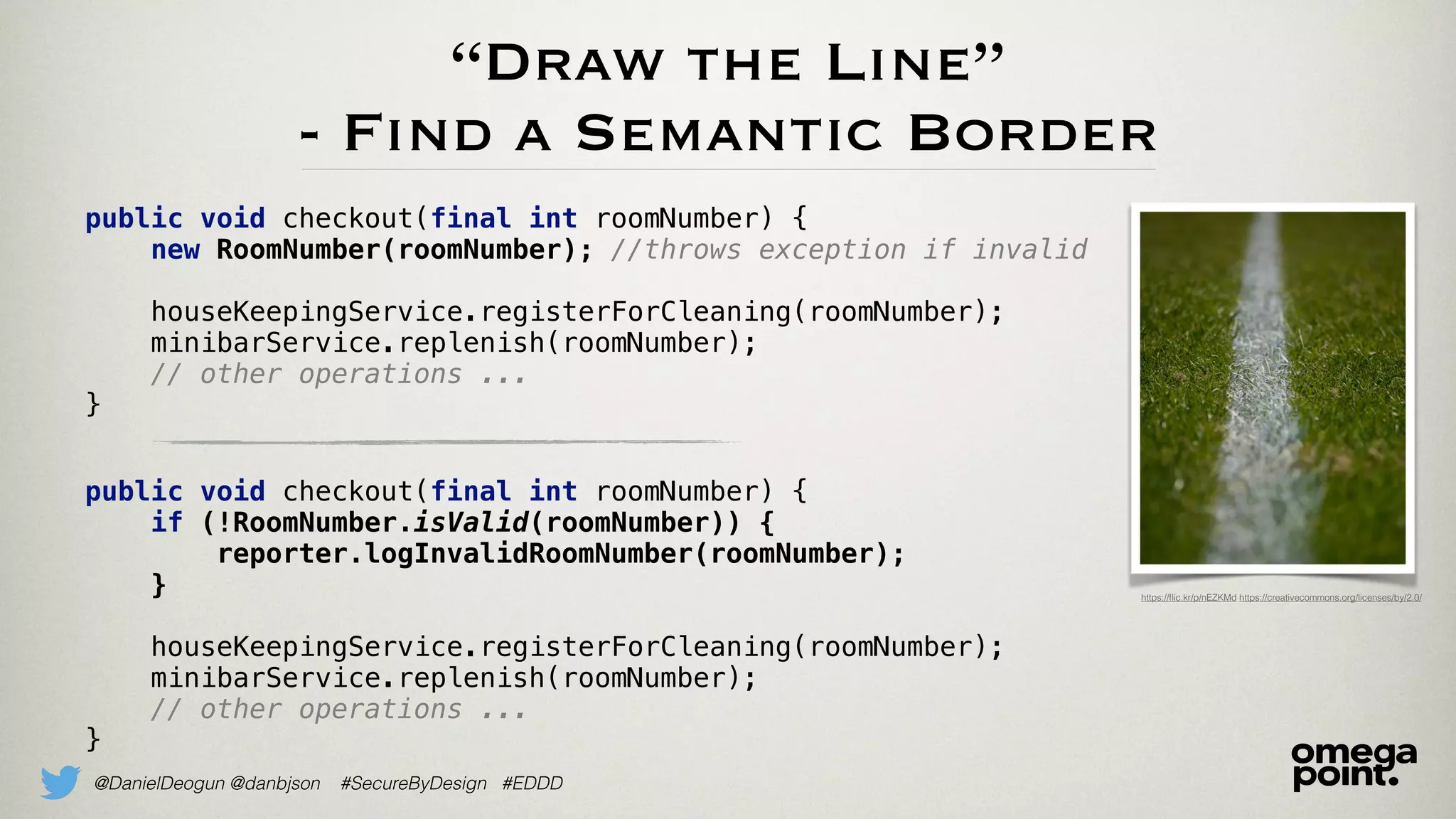
The document discusses the concept of domain primitives, which are essential building blocks native to specific domains, that aid in securing and improving code. It emphasizes the importance of modeling domain-specific data accurately to enhance software security and data integrity. Additionally, it provides examples of implementing domain primitives in various contexts, such as hotel room management and monetary transactions.










![@DanielDeogun @danbjson #SecureByDesign #EDDD
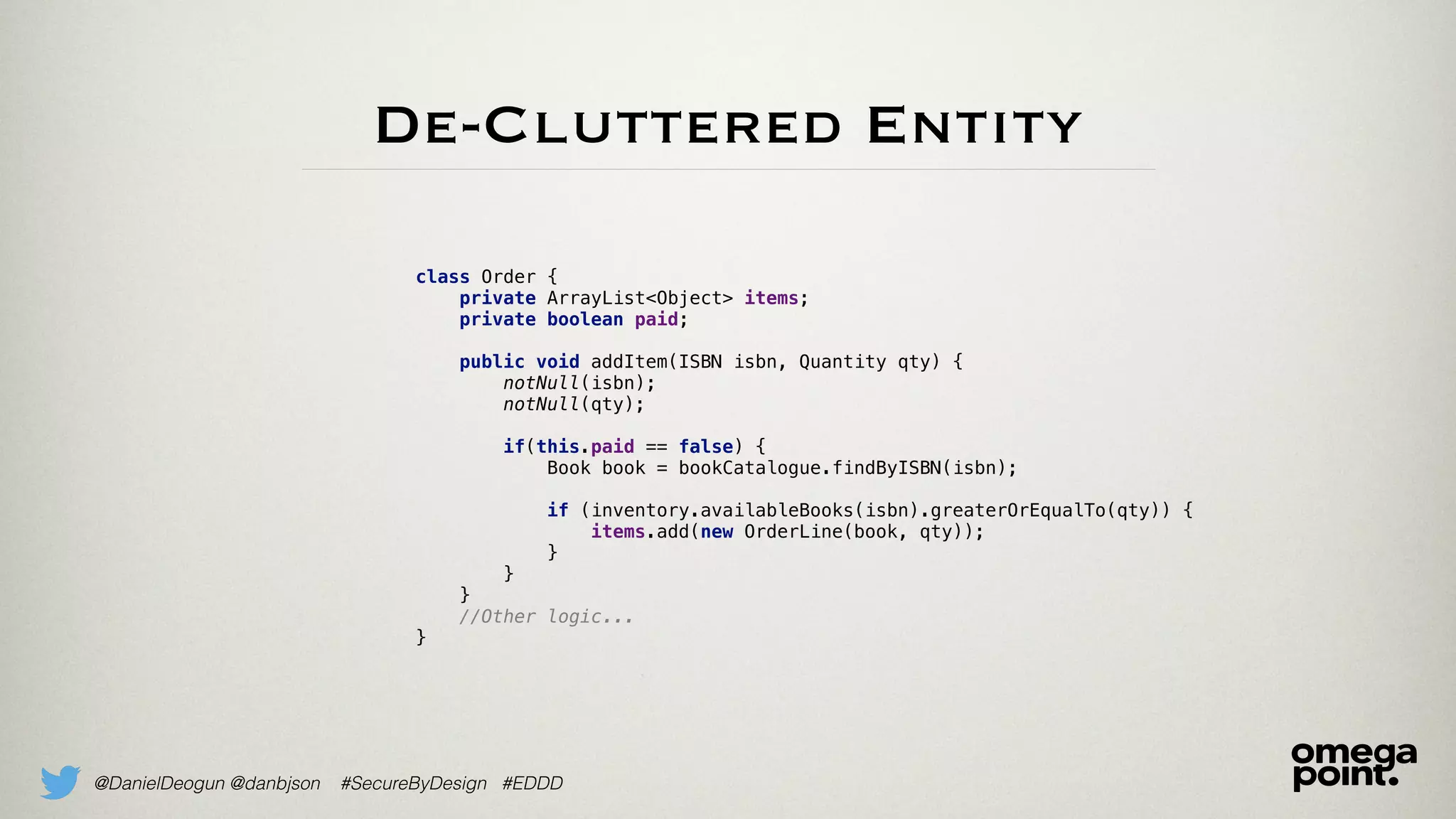
Cluttered Entity
class Order {
private ArrayList<Object> items;
private boolean paid;
public void addItem(String isbn, int qty) {
if(this.paid == false) {
notNull(isbn);
inclusiveBetween(10, 10, isbn.length());
isTrue(isbn.matches("[0-9X]*"));
isTrue(isbn.matches("[0-9]{9}[0-9X]"));
Book book = bookCatalogue.findByISBN(isbn);
if (inventory.availableBooks(isbn) >= qty) {
items.add(new OrderLine(book, qty));
}
}
}
//Other logic...
}](https://image.slidesharecdn.com/domainprimitivesinaction-170922155952/75/Domain-Primitives-In-Action-Explore-DDD-2017-16-2048.jpg)