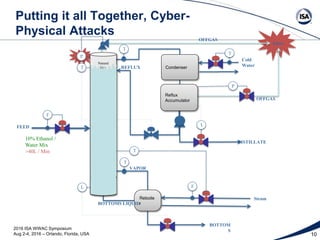
The document is a presentation by Bryan L. Singer at the 2016 ISA Water/Wastewater and Automatic Controls Symposium, focusing on the cybersecurity of industrial control systems (ICS). It discusses the vulnerabilities of ICS, the importance of mechanical and cyber-physical integrity, and outlines various attack scenarios that can compromise safety measures. The presentation emphasizes the need for improved security measures and the implementation of layered protections to safeguard against cyber threats in critical infrastructures.