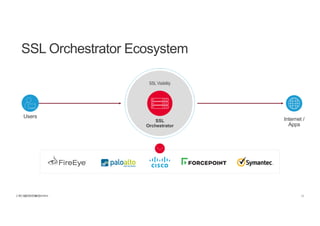
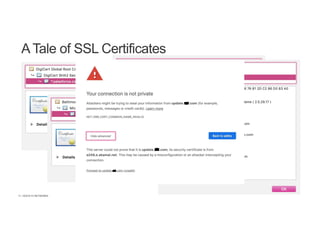
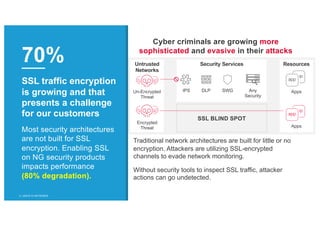
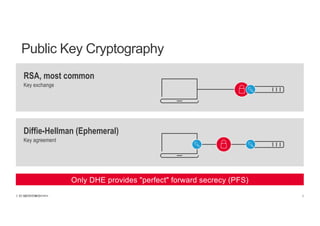
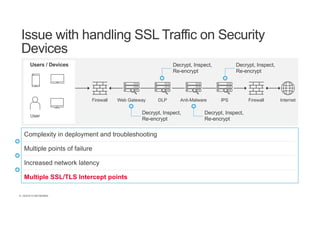
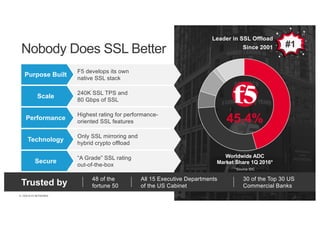
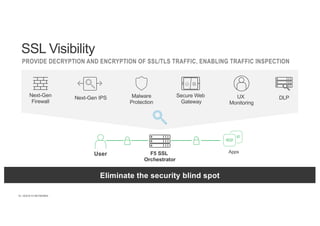
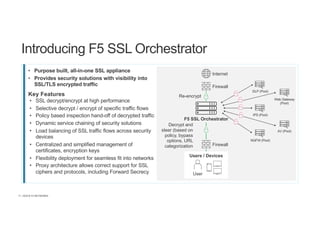
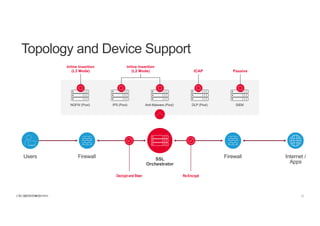
The document discusses the evolution and challenges of SSL/TLS encryption and its impact on network security. It highlights how increasing SSL traffic can create blind spots for traditional security architectures, making them less effective against sophisticated cyber attacks. F5 Networks introduces the SSL Orchestrator as a solution to provide visibility into encrypted traffic, enabling better security inspection and management of SSL/TLS communications.




![| ©2018 F5 NETWORKS13
• Allows determination of decryption OR selection of
services based on connection context
• Policy based, dynamic
Policy Based Dynamic Service Chaining
Classification Engine
• Source IP
• Destination IP
• IP intelligence
• IP geolocation
• Domain name
• URL filtering category
• Destination port
• Protocol
“We field over 12 different security services, and we struggle
with using all of them effectively.”
“We [currently] chain the security services statically leading to
over provisioning and investment overruns.”
“We want to pre-filter traffic going to [our Firewall] so we make
more effective use of them.”
Firewall Firewall Firewall
IDS IPS IPS
WAF WAF WAF
DLP DLP
Forensics
1 2 3](https://image.slidesharecdn.com/melbournetechxchange-decryptingandselectivelyinspectingmoderntrafficwithf5sslorchestratormar2019-190306030212/85/Decrypting-and-Selectively-Inspecting-Modern-Traffic-13-320.jpg)