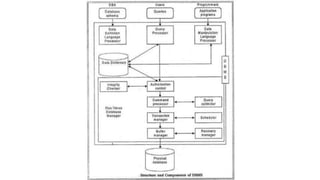
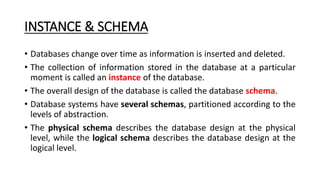
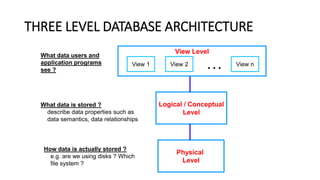
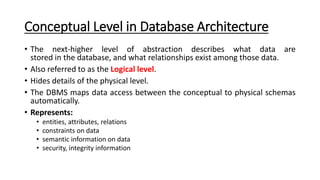
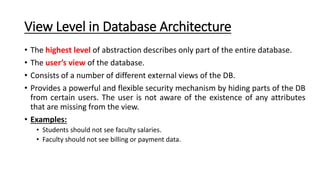
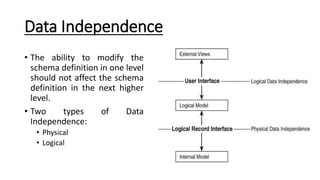
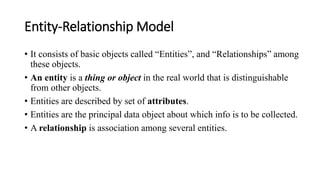
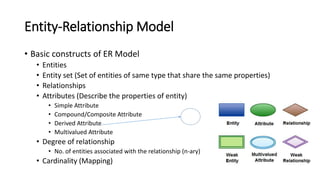
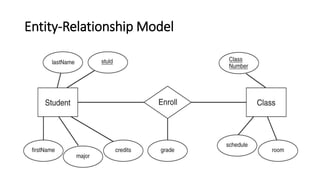
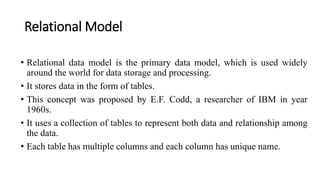
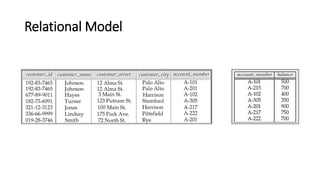
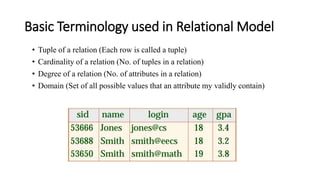
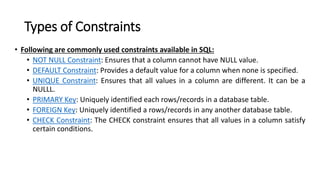
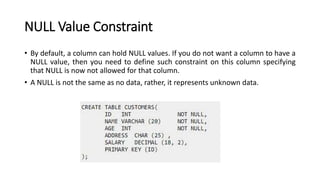
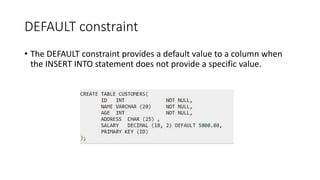
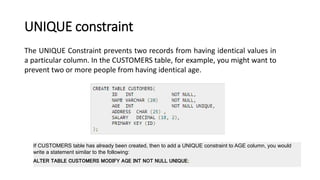
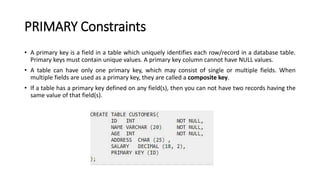
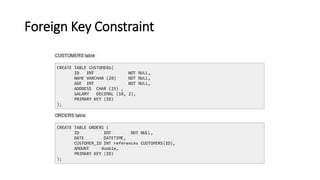
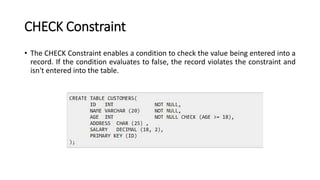
DBMS provide an organized collection of interrelated data stored and retrieved digitally in a computer system. A DBMS uses SQL to allow users to define, create, maintain and control access to the database. It consists of several components including a query processor, data dictionary, runtime database manager and data manager. The three schema architecture separates the logical and physical levels to provide data independence and abstraction.





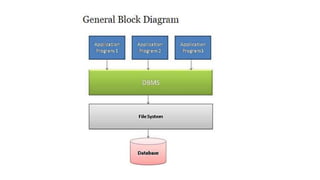



![Query Processor
• It is used to interpret the online user query and converts into a form capable of
being send to the data manager for execution.
• The query processor use the data dictionary to find the structure of a database.
• It is a program module that provides the interface between the database and the
application programs/queries.
• The Query Processor Components include –
• Data Definition Language(DDL) Compiler(Create, Alter[Add, Drop, Modify], Drop, Describe)
• Data Manipulation Language (DML) compiler(Insert, Update, Select)
• Query evaluation engine](https://image.slidesharecdn.com/dbmscopy-240407160711-65700e4f/85/Database-management-system-lecture-notes-12-320.jpg)