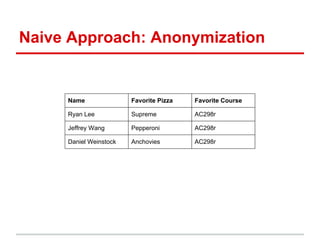
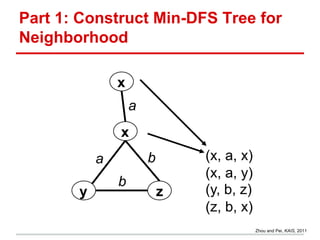
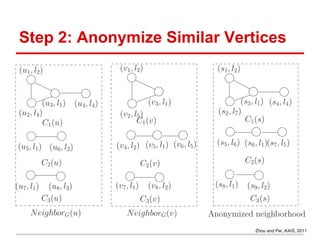
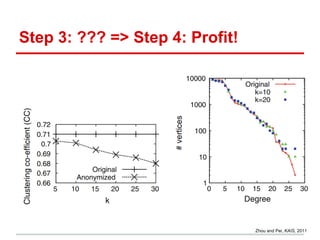
The document discusses the challenges of maintaining privacy in social networks and databases, highlighting issues with naive anonymization techniques. It cites various studies on the uses of social data in research, marketing, and government, and explores concepts like k-anonymity and differential privacy as potential solutions. Additionally, it emphasizes the ease of deanonymization through unique identifiers and the need for more robust methods to protect user privacy.