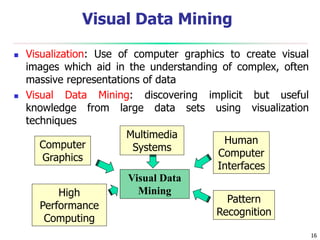
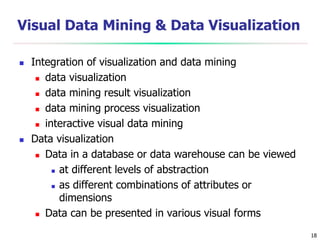
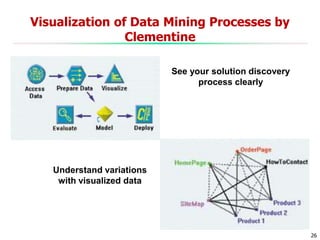
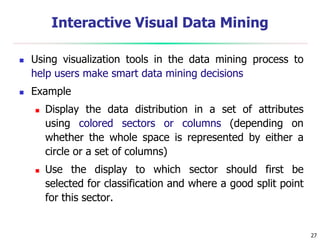
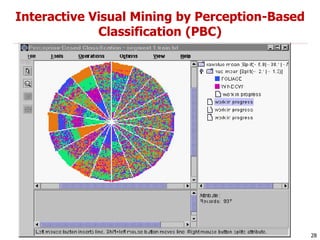
This document discusses data mining applications and trends. It covers topics like mining complex data types, other data mining methodologies, and various applications of data mining. Some key applications discussed include using data mining in finance, retail, telecommunications, science/engineering, intrusion detection, and recommender systems. The document also touches on topics like visual data mining, ubiquitous and invisible data mining, and the privacy and social impacts of data mining.