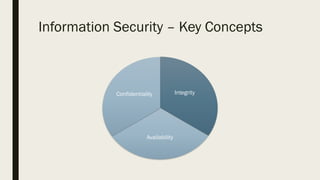
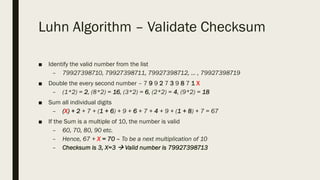
The document discusses data integrity within information security, focusing on key concepts like confidentiality, integrity, and availability, and describes assurance methods such as data encryption and validation. It emphasizes the use of checksums, particularly the Luhn algorithm, for verifying data integrity and validating identification numbers, including various practical applications. Additionally, it touches on penetration testing related to the Luhn algorithm and its effectiveness in brute-force scenarios.