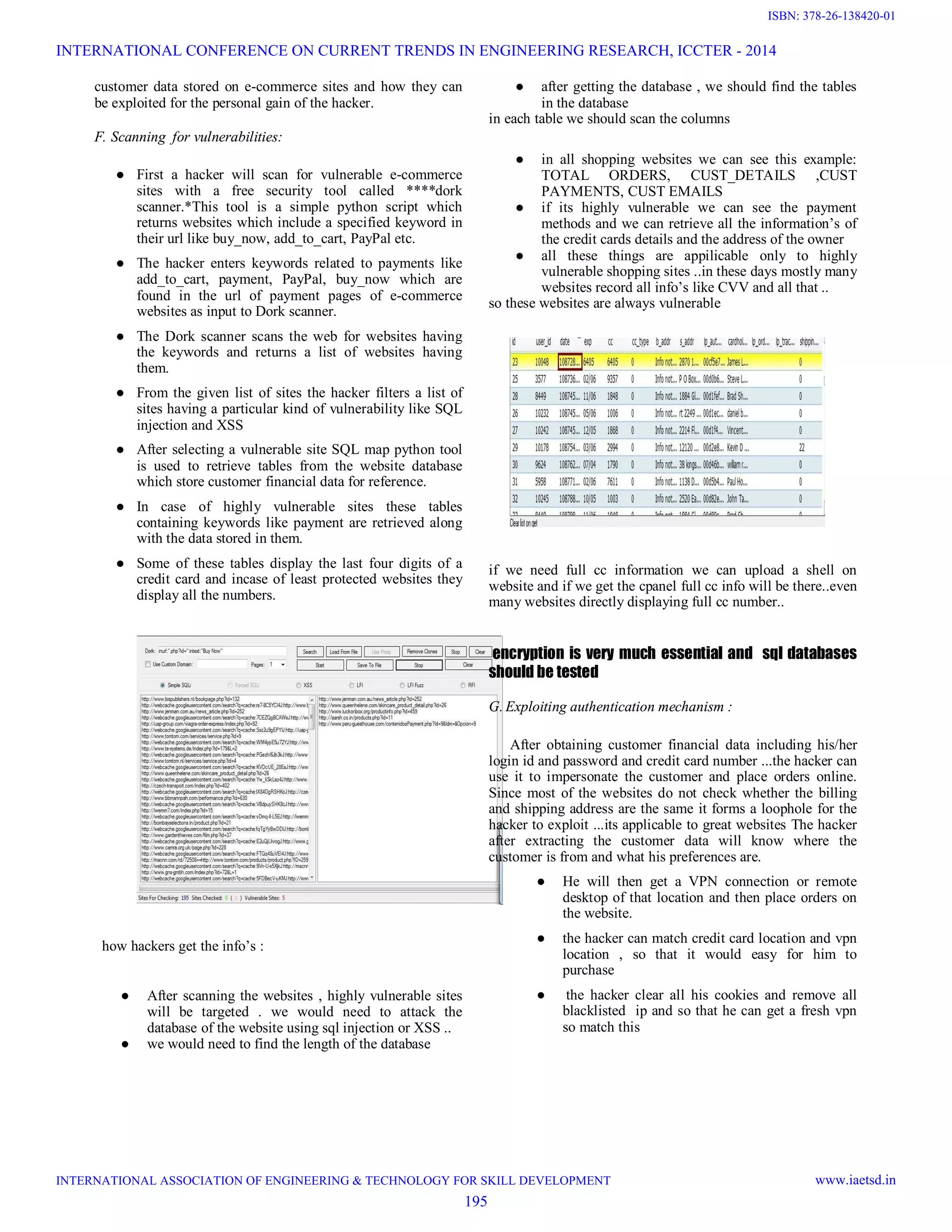
The document discusses vulnerabilities in how e-commerce websites store and protect customer credit card and personal information. It outlines how hackers can exploit these vulnerabilities to steal customer data by scanning websites for vulnerabilities, extracting data from vulnerable databases, and impersonating customers to make fraudulent purchases. It suggests methods for protecting customer information, such as encrypting stored data, avoiding storage of sensitive details like CVV numbers, and implementing stronger authentication of customers and IP addresses to prevent fraudulent orders.