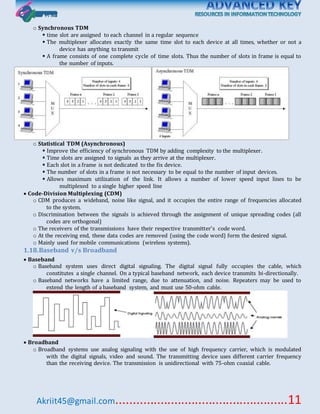
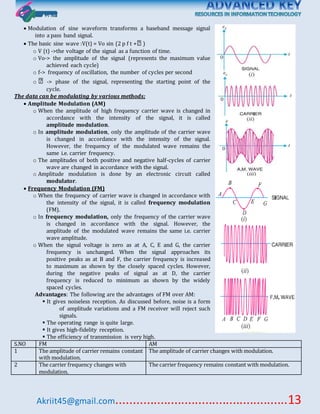
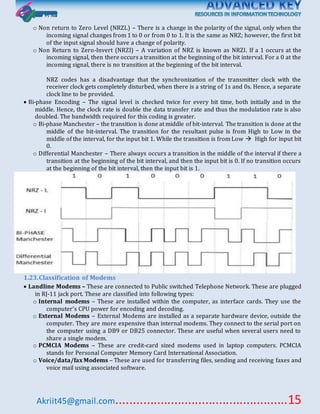
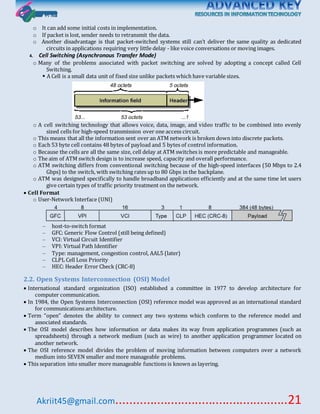
This document discusses various topics related to data communication and computer networks. It covers fundamental concepts like data, communication, networks, signals and circuits. It also covers topics like transmission modes, error detection techniques, flow control, multiplexing, modulation, network components, LAN protocols, WAN routing, and application protocols. The document provides an overview of key topics within data communication and networking.