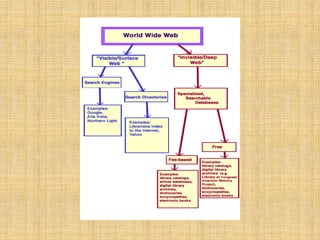
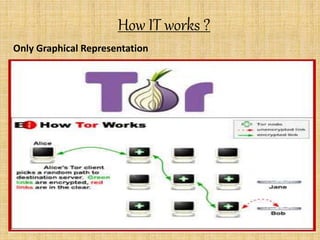
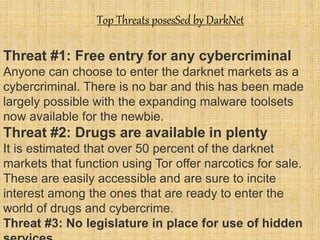
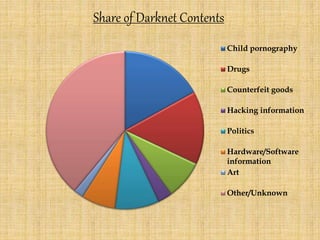
The document provides an overview of the darknet, detailing its definition, contents, and advantages while discussing the special software required for access, primarily Tor. It highlights the substantial threats associated with the darknet, including easy access for cybercriminals, availability of illegal goods like drugs, and the lack of regulation leading to issues such as child pornography. The conclusion warns users of the dangers while suggesting that, if navigated carefully, the darknet can also be a valuable source of information.