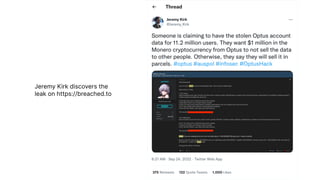
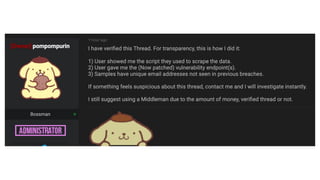
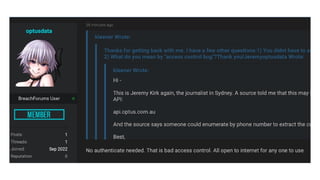
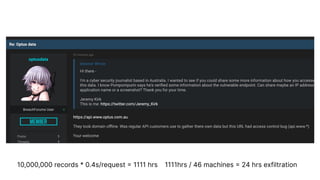
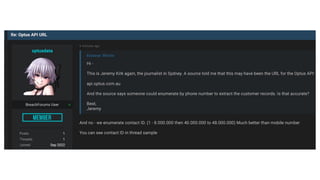
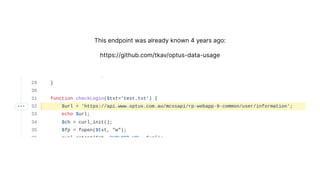
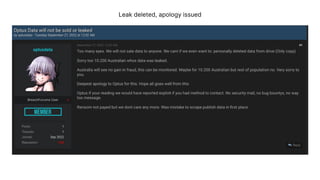
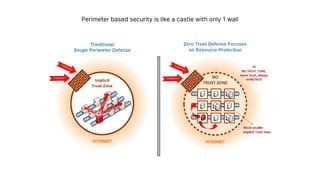
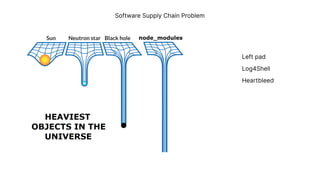
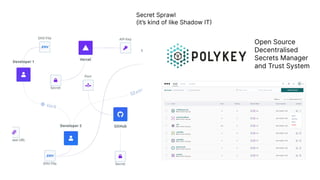
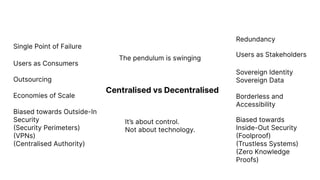
The document discusses a major data breach involving Optus, where 10 million records were leaked due to inadequate security protocols and a vulnerable API. It highlights the need for improved digital asset visibility, zero-trust architectures, and better security practices to prevent such incidents. Various security theories are explored, including outside-in and inside-out perspectives, emphasizing the importance of monitoring and securing systems effectively.