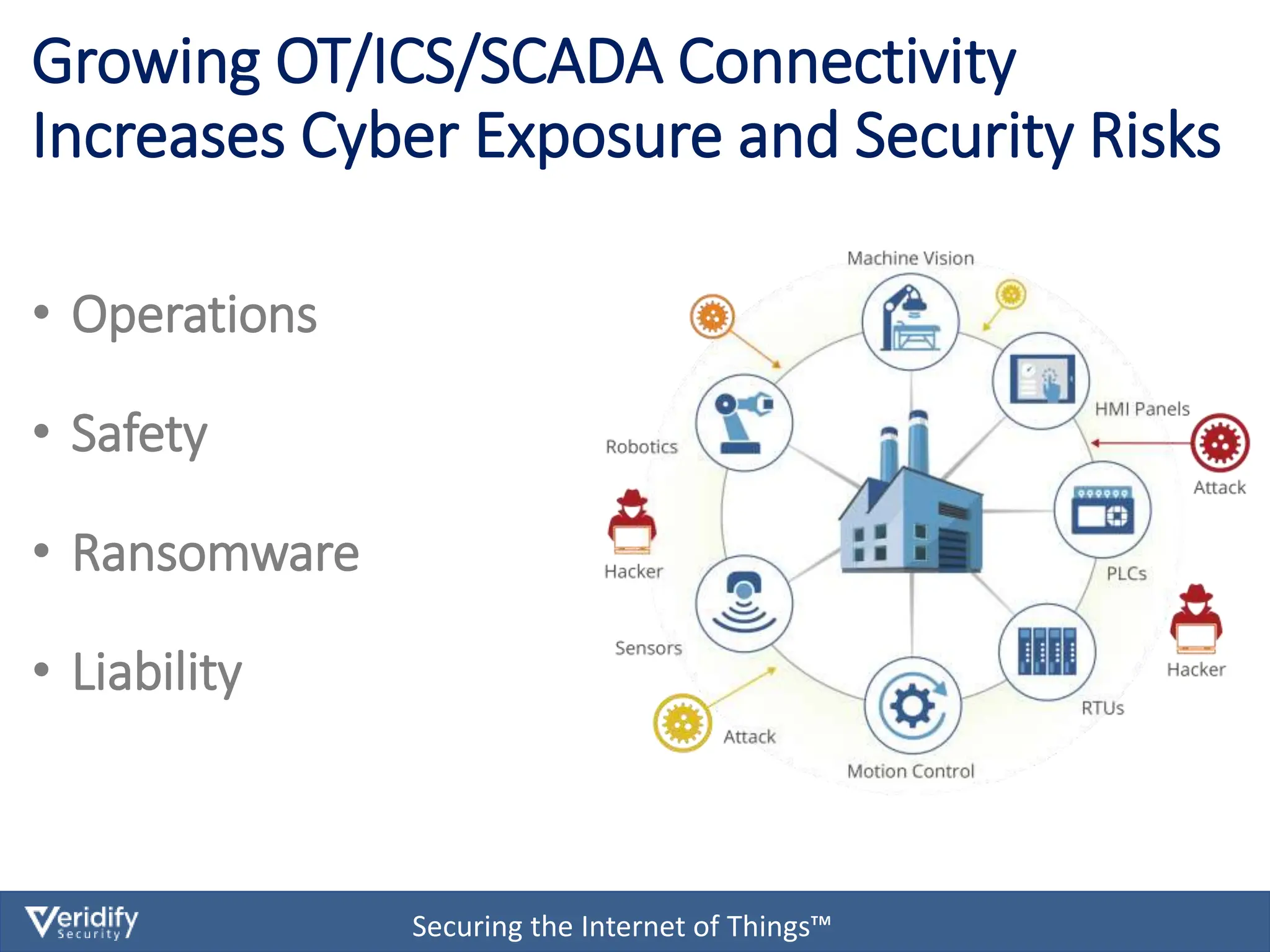
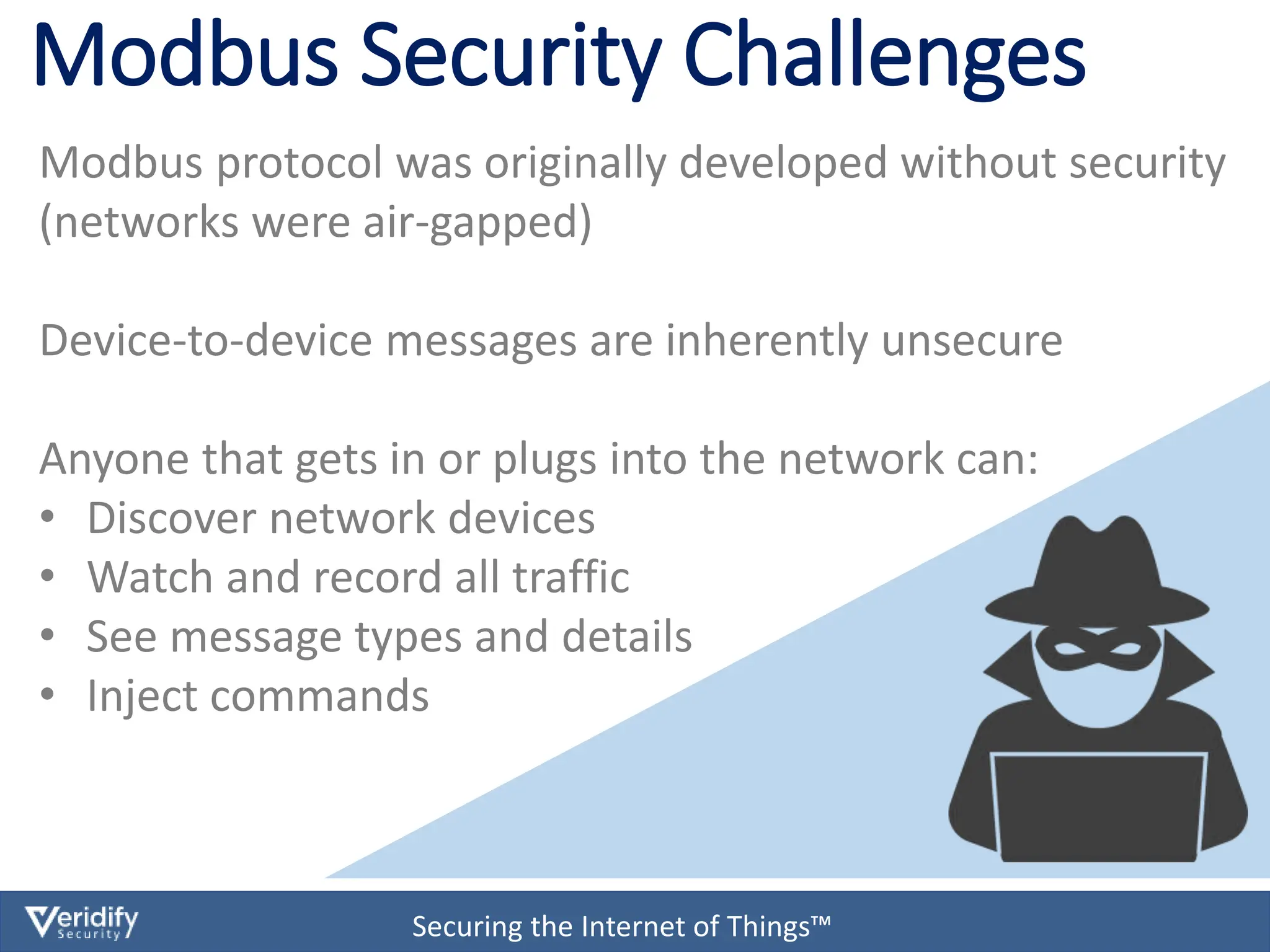
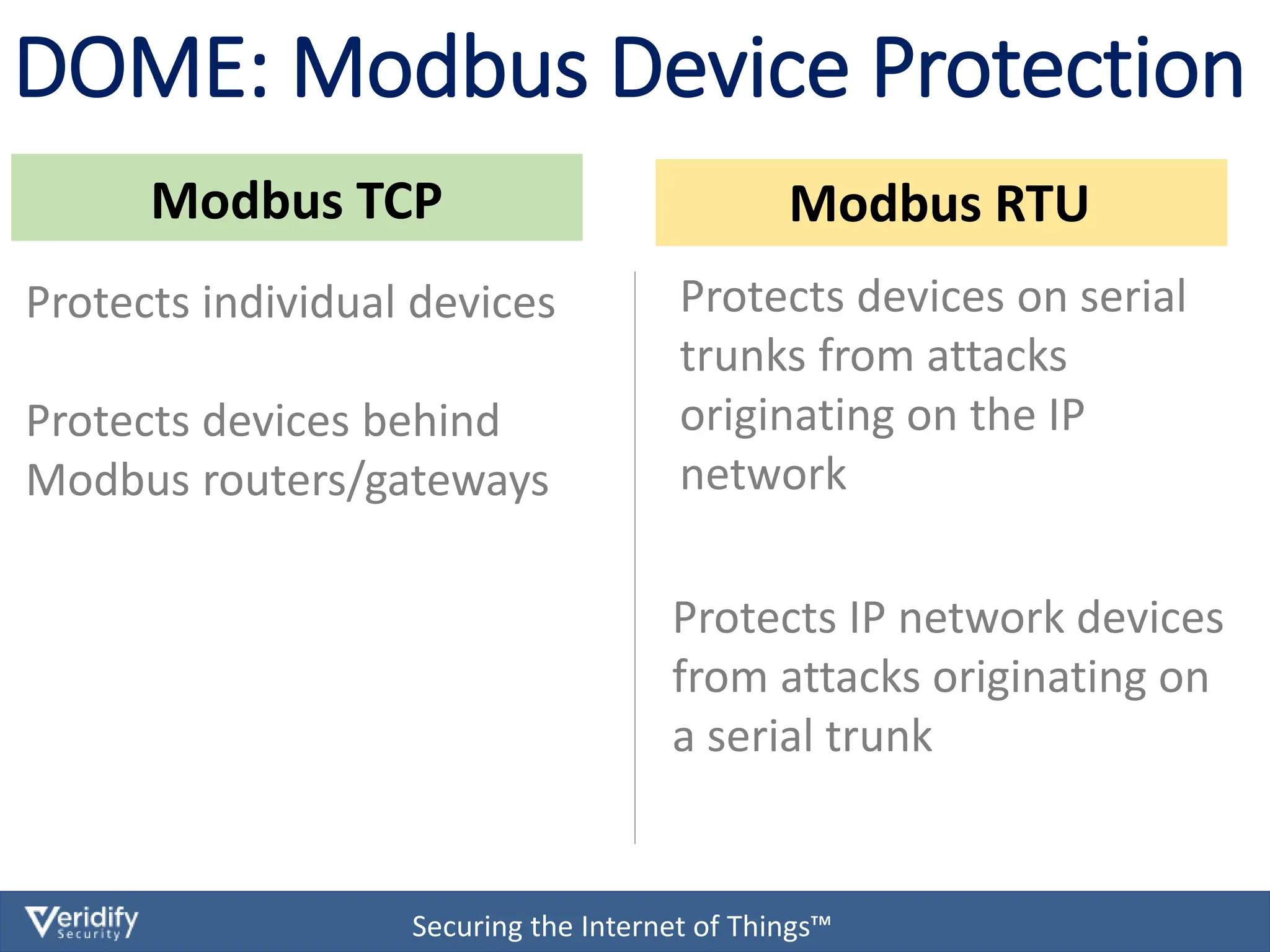
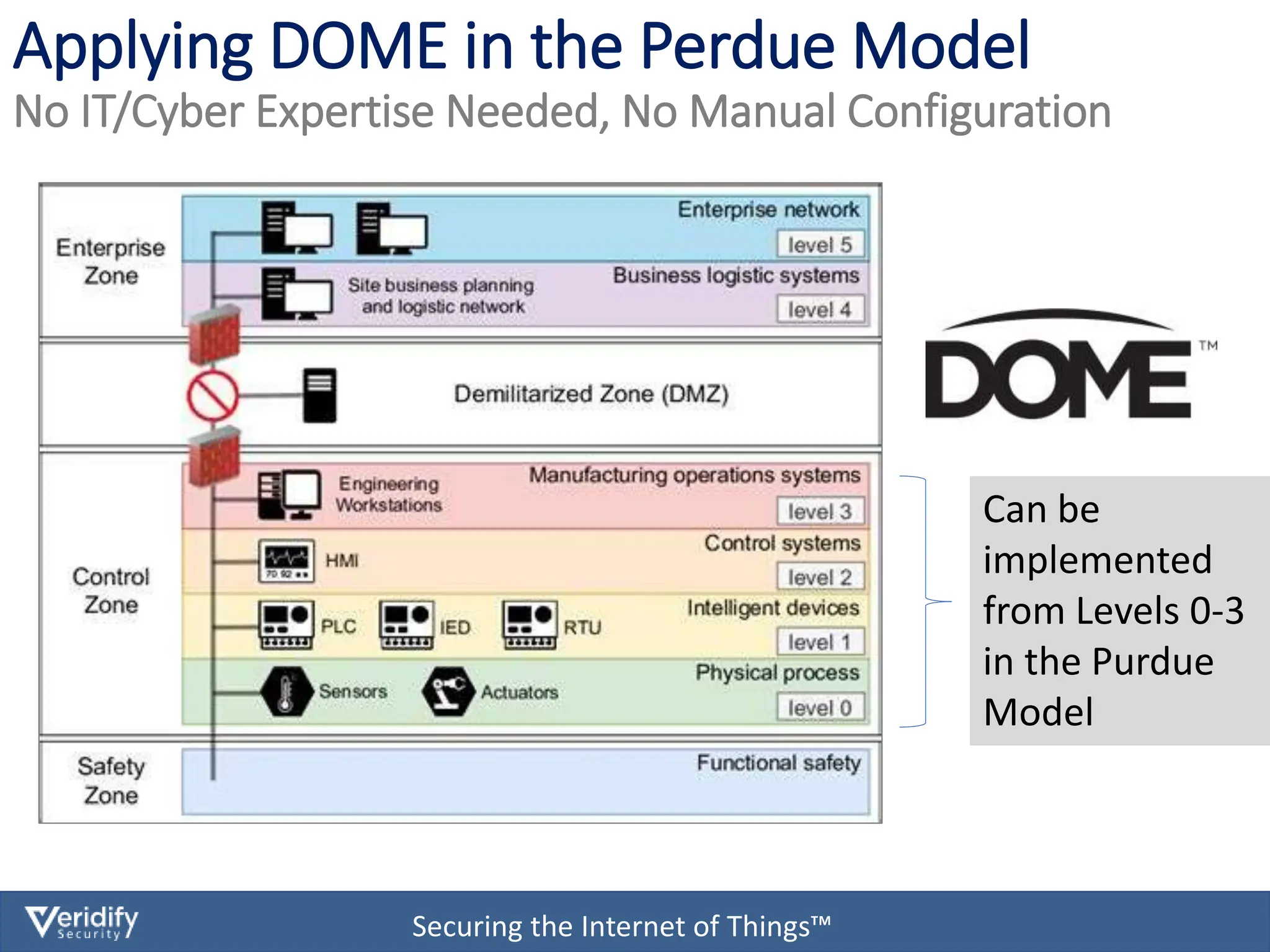
The document discusses cybersecurity challenges for Modbus in Internet of Things (IoT) environments, highlighting that the Modbus protocol was not originally designed with security in mind. It introduces a comprehensive security solution called Dome, which offers features such as authentication, data encryption, and real-time protection for devices on both IP and serial networks without needing IT expertise. Dome is designed for ease of installation, supporting rapid deployment and security management for operational technology environments.