Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
What endpoint protection solutions are available on the market today?

What endpoint protection solutions are available on the market today?
Best Information Security Tips for Better Computing

Best Information Security Tips for Better Computing
Re solution - corona virus cyber security infographic

Re solution - corona virus cyber security infographic
Top 10 Reasons to Learn Cybersecurity | Why Cybersecurity is Important | Edureka

Top 10 Reasons to Learn Cybersecurity | Why Cybersecurity is Important | Edureka
Network Security - Defense Through Layered Information Security

Network Security - Defense Through Layered Information Security
F5 Networks- Why Legacy Security Systems are Failing

F5 Networks- Why Legacy Security Systems are Failing
Similar to Cyberdefense in depth with validy technology
Similar to Cyberdefense in depth with validy technology (20)
JS Fest 2019. Анастасия Войтова. "Defense in depth": trench warfare principle...

JS Fest 2019. Анастасия Войтова. "Defense in depth": trench warfare principle...
Fidelis - Live Demonstration of Deception Solution

Fidelis - Live Demonstration of Deception Solution
Cybersecurity Concerns You Should be Thinking About

Cybersecurity Concerns You Should be Thinking About
More from Gilles Sgro
More from Gilles Sgro (20)
Validy lettre-dpsd-colonel-bourguignon-27-dec-2006

Validy lettre-dpsd-colonel-bourguignon-27-dec-2006
Validy lettre-dpsd-colonel-bourguignon-15-fev-2007

Validy lettre-dpsd-colonel-bourguignon-15-fev-2007
Validy 171 signataires lettre au président, aux députés, aux sénateurs et à...

Validy 171 signataires lettre au président, aux députés, aux sénateurs et à...
Courrier du chef de cabinet du président de la république du 8 aout 2012

Courrier du chef de cabinet du président de la république du 8 aout 2012
Lettre recue le 9 nov 2012 du chef de cabinet du président de la république

Lettre recue le 9 nov 2012 du chef de cabinet du président de la république
Lettre recue fleur pellerin 14 sept 2012 - recu le 1 er octobre 2012

Lettre recue fleur pellerin 14 sept 2012 - recu le 1 er octobre 2012
Secrétaire général elyséee macron - lettre - 4 octobre 2012

Secrétaire général elyséee macron - lettre - 4 octobre 2012
Secrétaire général elyséee macron - note -4 octobre 2012

Secrétaire général elyséee macron - note -4 octobre 2012
Rapport senateur bockel surligné cyber defense - 19 juillet 2012

Rapport senateur bockel surligné cyber defense - 19 juillet 2012
Autorité de la concurrence retrait de la plainte - bruno lasserre - 6 mars ...

Autorité de la concurrence retrait de la plainte - bruno lasserre - 6 mars ...
Recently uploaded
Recently uploaded (20)
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
Cyberdefense in depth with validy technology
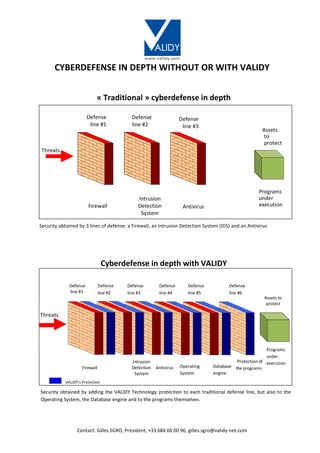
- 1. www.validy.com Contact: Gilles SGRO, President, +33 684 60 00 96, gilles.sgro@validy-net.com CYBERDEFENSE IN DEPTH WITHOUT OR WITH VALIDY « Traditional » cyberdefense in depth Defense line #1 Defense line #2 Defense line #3 Assets to protect Threats Firewall Intrusion Detection System Antivirus Programs under execution Security obtained by 3 lines of defense: a Firewall, an Intrusion Detection System (IDS) and an Antivirus Cyberdefense in depth with VALIDY Threats Defense line #1 Defense line #2 Defense line #3 Defense line #4 Defense line #5 Defense line #6 Assets to protect Firewall VALIDY’s Protection Intrusion Detection System Antivirus Operating System Database engine Protection of the programs Programs under execution Security obtained by adding the VALIDY Technology protection to each traditional defense line, but also to the Operating System, the Database engine and to the programs themselves.