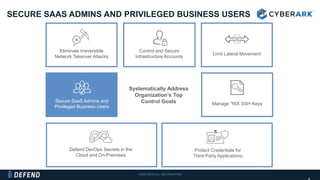
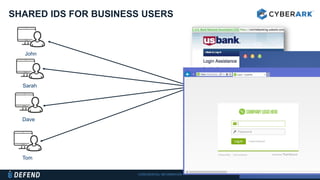
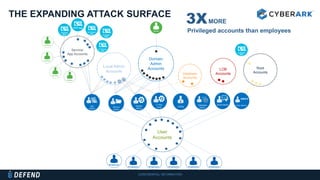
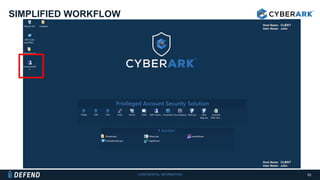
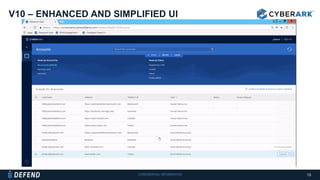
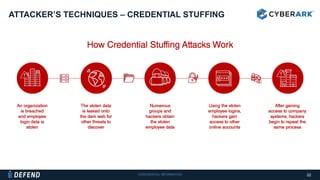
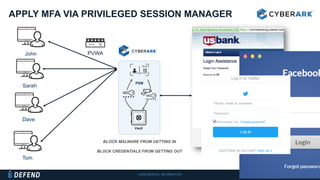
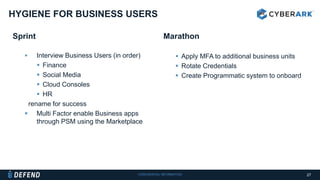
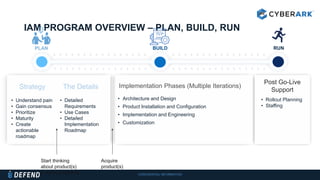
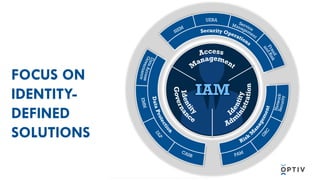
This document discusses multifactor authentication for critical business users. It begins by providing context that organizations are multifactoring access but breaches are still occurring. It then outlines how a privileged session manager and multifactor authentication can be used to securely manage privileged accounts and shared credentials. The presentation concludes by discussing how to apply these techniques to business units and maintain credential hygiene.