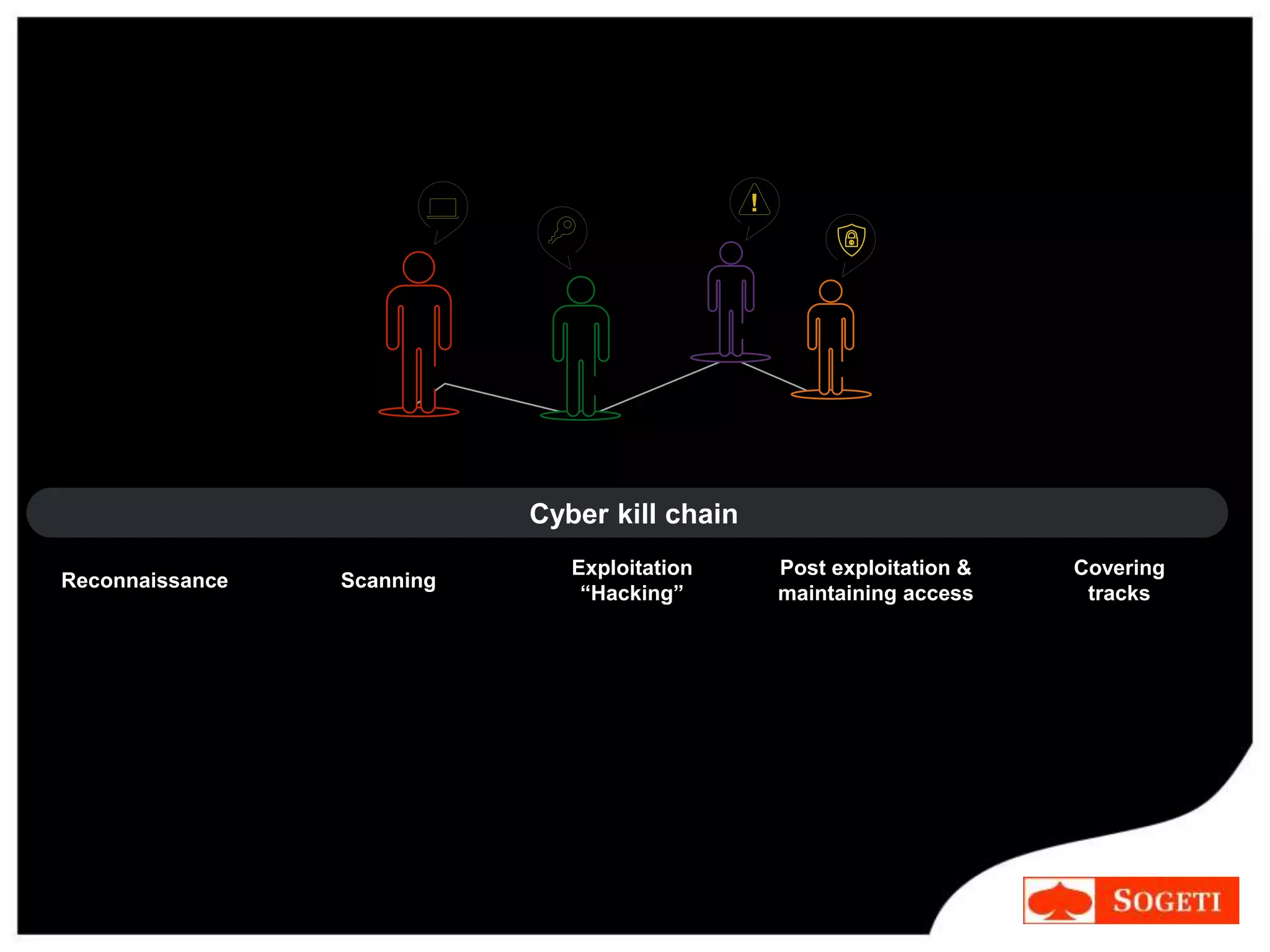
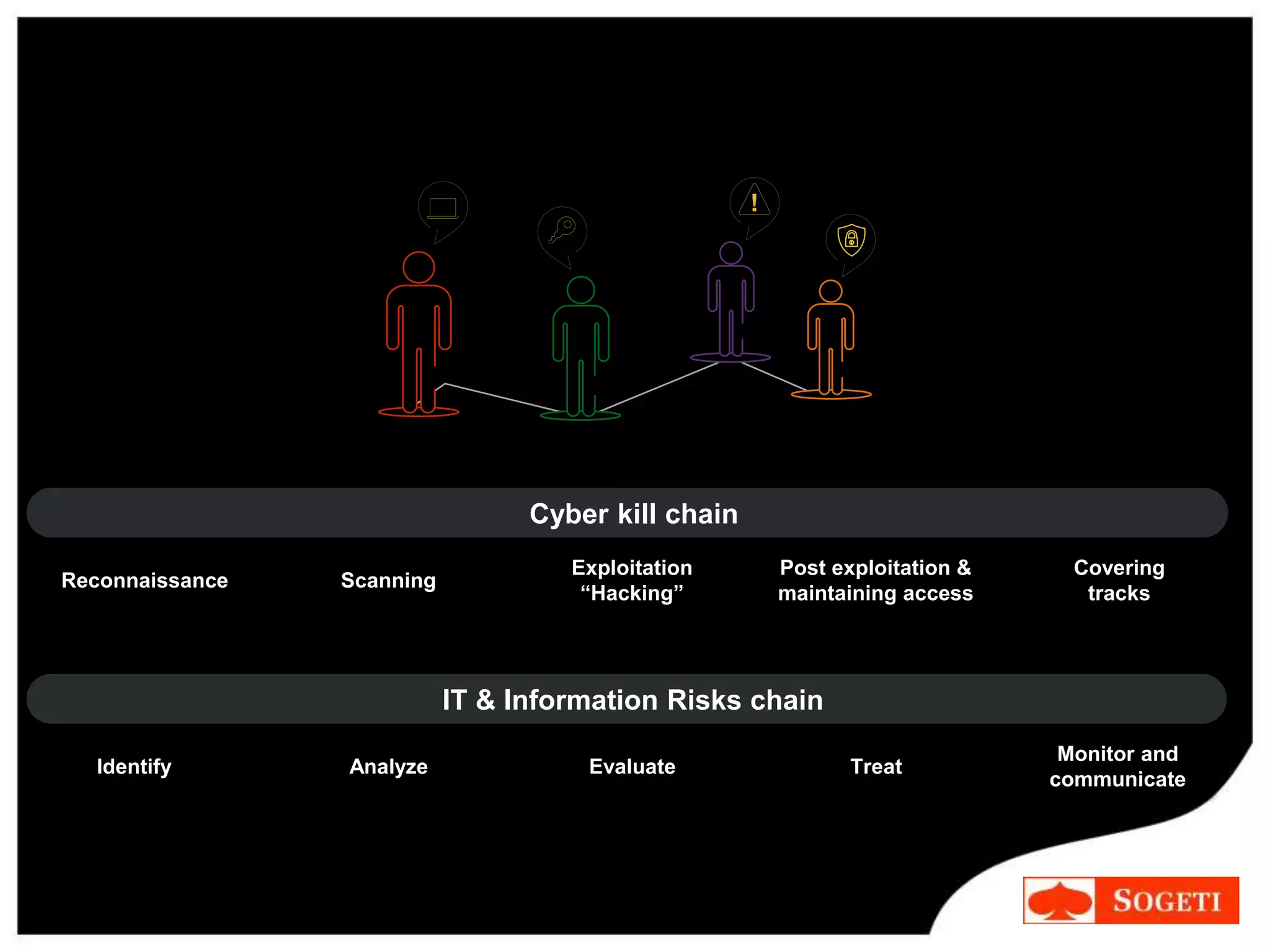
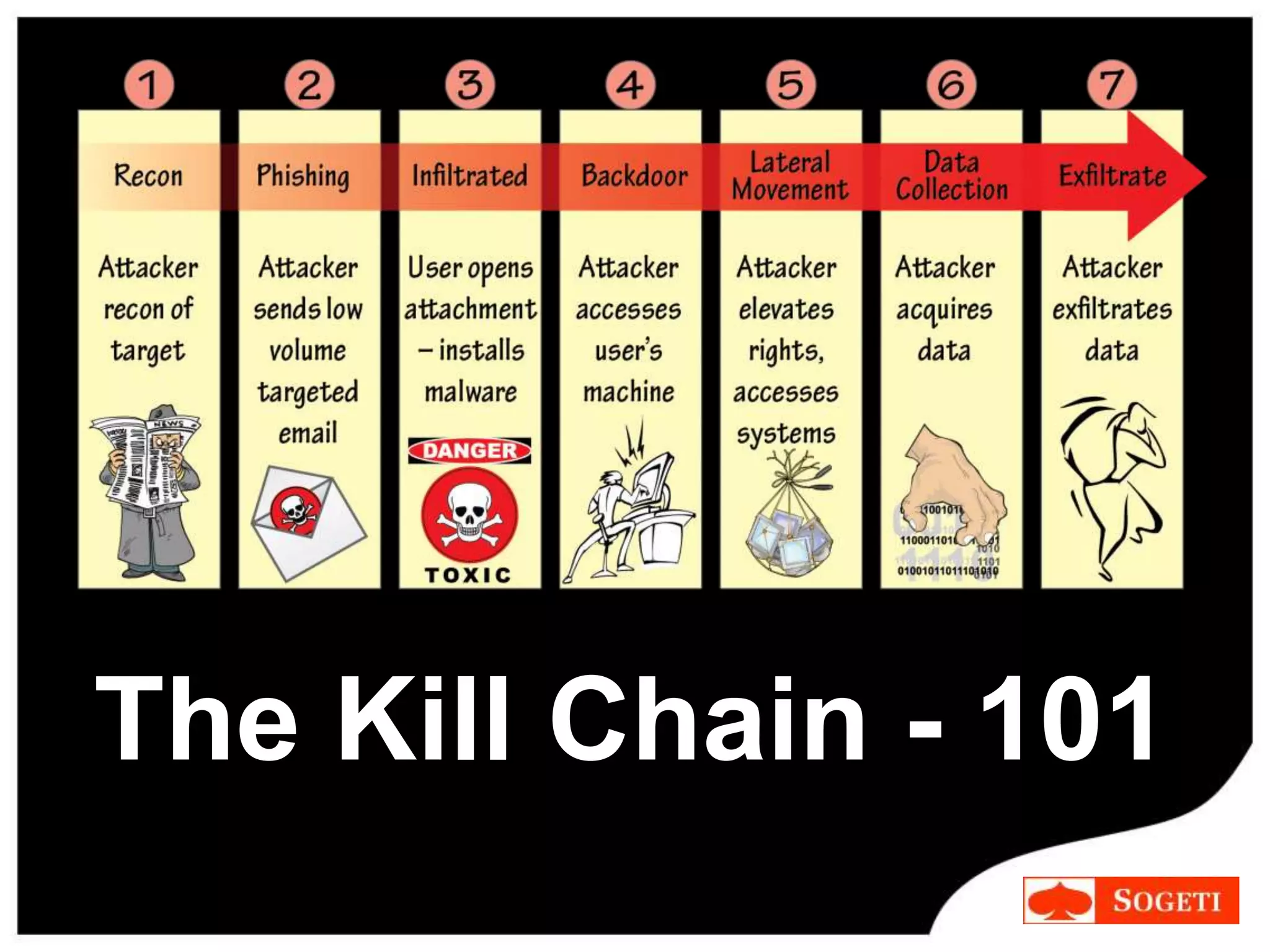
IT security focused on protecting systems, while cybersecurity is a paradigm shift that recognizes threats can come from anywhere on the internet. The cybersecurity kill chain describes the steps hackers use, from initial reconnaissance to maintaining access. While some see cyber threats as a myth, over 110 million Americans had personal data exposed in the past year, and advanced persistent threats from nation-states pose serious risks. To counter attacks, organizations should develop new approaches through education and creativity, rather than relying on fear, and aim to make security practices inherently more secure.