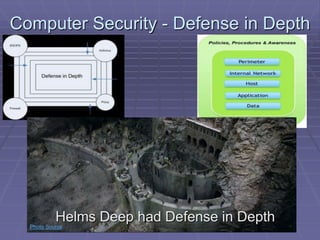
This document discusses computer security innovation and proposes a Secure Computing Infrastructure (SCIF) as a foundational solution. Some key points:
- Current computer security approaches are unsustainable and non-scalable as they do not build security in from the beginning.
- Operating systems and applications lack basic immune systems and are not written robustly, leading to vulnerabilities.
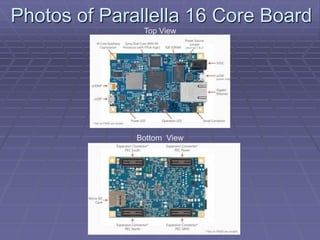
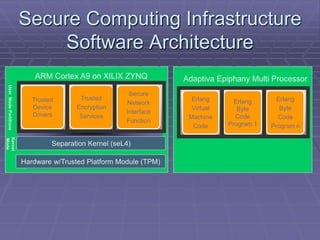
- The document proposes a SCIF that uses components like the Parallella board running seL4 microkernel with Erlang virtual machine to securely run applications and provide fault tolerance.
- A phased approach is outlined to prototype and field trial the SCIF as a more secure computing foundation.