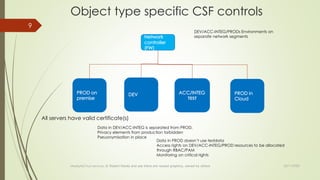
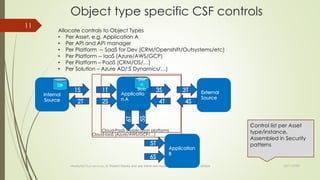
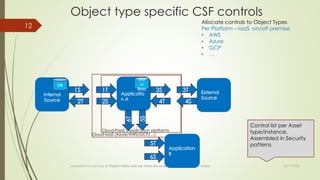
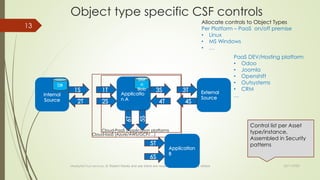
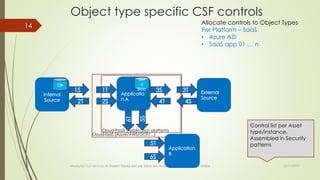
The document discusses integrating cybersecurity controls into an organization's Way of Working (WoW). It recommends defining cybersecurity goals and applying the NIST Cybersecurity Framework (CSF) and NIST Special Publication 800-53 controls. Specifically, the document suggests allocating controls to different object types like applications, platforms, and systems. It also advises converting controls into user stories and tests to integrate them into the software development lifecycle according to the WoW. The overall goal is to securely develop and operate systems using a risk-based approach aligned with the organization's processes.


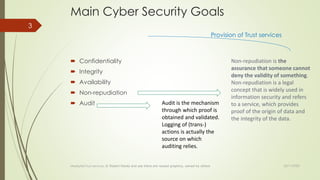

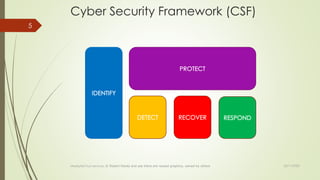
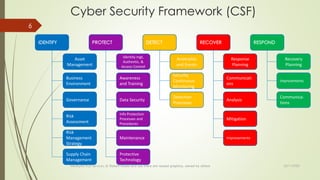

![ Target Organisation should apply CSF & NIST.SP.800-53r5.
NIST.SP.800-53r5 document has been converted into (Confluence) wiki
Which facilitates both Development and Operations, as well as Audit and
Compliance to incorporate the obligatory mechanisms
Use of capabilities and controls will evolve following the roadmap timeline.
More discussion below
23/11/2022
MediqAid Trust services; © Robert Kloots and yes there are reused graphics, owned by others
8
CSF Quality Controls, Risk & Compliance
AC-2(1) Account Management | Automated
System Account Management
Support the management of system accounts using [Assignment:
organization-defined automated mechanisms].
AC-2(2) Account Management | Automated
Temporary and Emergency Account
Management
Automatically [Selection: remove; disable] temporary and
emergency accounts after [Assignment: organization-defined time
period for each type of account].
AC-2(3) Account Management | Disable
Accounts
Disable accounts within [Assignment: organization-defined time
period] when the accounts:
(a) Have expired;
(b) Are no longer associated with a user or individual;
(c) Are in violation of organizational policy; or
(d) Have been inactive for [Assignment: organization-defined time
period].
AC-2(4) Account Management | Automated
Audit Actions
Automatically audit account creation, modification, enabling,
disabling, and removal actions.
AC-2(5) Account Management | Inactivity
Logout
Require that users log out when [Assignment: organization-
defined time period of expected inactivity or description of when
to log out].
Extract from NIST.SP.800-53r5
Identity mgt,
Authentic. &
Access Control
PROTECT](https://image.slidesharecdn.com/cyberobjecttypesandcontrols-221123174607-65915463/85/Cyber-object-types-and-controls-pdf-8-320.jpg)