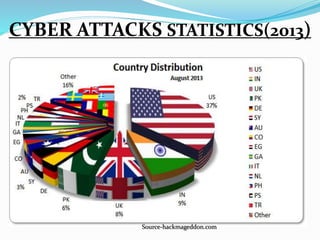
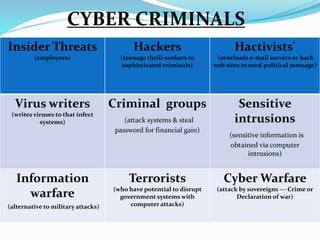
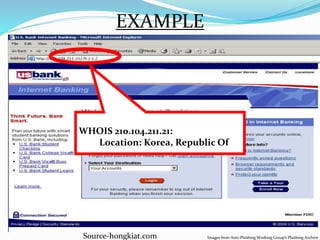
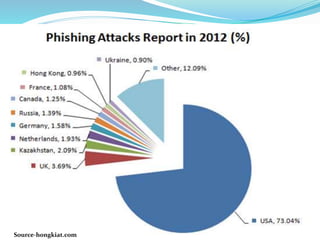
The document discusses the rise of cyber crime in India, highlighting its history and defining characteristics, such as unlawful acts involving computers. It categorizes cyber crimes into three main areas: against persons, property, and government, and also details various forms of cyber criminal activities. The document emphasizes the importance of preventive measures like strong passwords and secure networks to combat the increasing threat of cyber crime.